3a2b2540863b2e35f9cf7ec4cc14854f.ppt
- Количество слайдов: 19
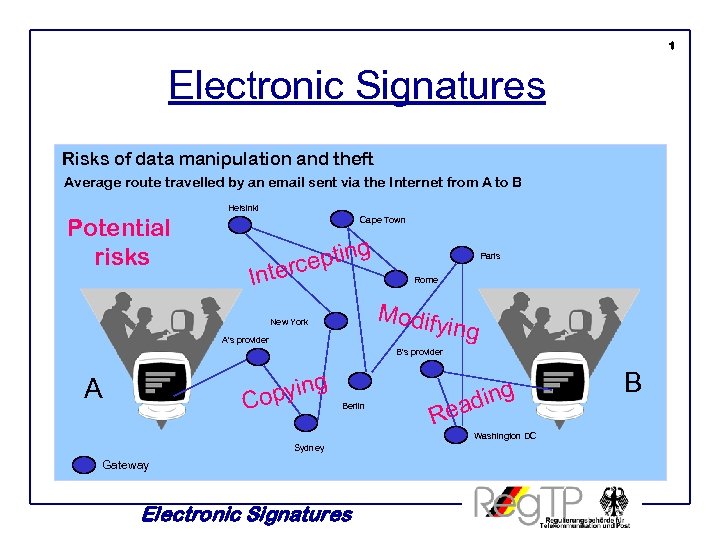 1 Electronic Signatures Risks of data manipulation and theft Average route travelled by an email sent via the Internet from A to B Helsinki Potential risks Cape Town g eptin c Inter Paris Rome Modif ying New York A's provider B's provider pying Co A Berlin ding a Re Washington DC Sydney Gateway Electronic Signatures B
1 Electronic Signatures Risks of data manipulation and theft Average route travelled by an email sent via the Internet from A to B Helsinki Potential risks Cape Town g eptin c Inter Paris Rome Modif ying New York A's provider B's provider pying Co A Berlin ding a Re Washington DC Sydney Gateway Electronic Signatures B
 Areas of application for electronic signatures Communicating with public authorities • eg individuals completing, signing, encrypting and emailing electronic tax returns • eg building contractors signing, encrypting and emailing electronic bids in response to invitations to tender Communicating with judicial bodies • eg lawyers writing, signing, encrypting (safeguarding clients' secrets) and emailing electronic claims and actions to the competent courts Communicating in the private sector • eg customers communicating with companies, for instance for banking purposes • eg strangers communicating via the Internet • eg signing emails Anywhere legally binding declarations of will require a signature and where – trustworthy communications, – reliable identification, and – integrity of electronic data are a key factor, can legally compliant electronic signatures be used. Electronic Signatures 2
Areas of application for electronic signatures Communicating with public authorities • eg individuals completing, signing, encrypting and emailing electronic tax returns • eg building contractors signing, encrypting and emailing electronic bids in response to invitations to tender Communicating with judicial bodies • eg lawyers writing, signing, encrypting (safeguarding clients' secrets) and emailing electronic claims and actions to the competent courts Communicating in the private sector • eg customers communicating with companies, for instance for banking purposes • eg strangers communicating via the Internet • eg signing emails Anywhere legally binding declarations of will require a signature and where – trustworthy communications, – reliable identification, and – integrity of electronic data are a key factor, can legally compliant electronic signatures be used. Electronic Signatures 2
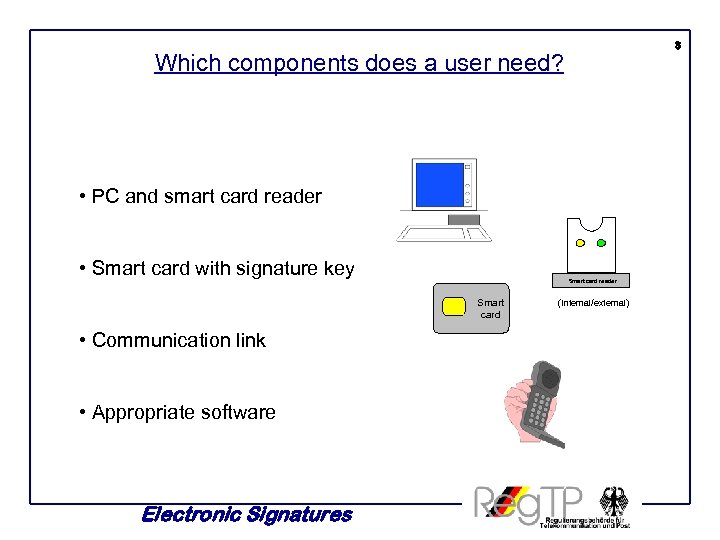 3 Which components does a user need? • PC and smart card reader • Smart card with signature key Smart card reader Smart card • Communication link • Appropriate software Electronic Signatures (Internal/external)
3 Which components does a user need? • PC and smart card reader • Smart card with signature key Smart card reader Smart card • Communication link • Appropriate software Electronic Signatures (Internal/external)
 What does an electronic signature do? An electronic signature is the electronic equivalent of a handwritten signature; in other words, it can be used to • reliably verify that an electronic document has not been modified, • reliably identify the person who has signed an electronic document, and • INTEGRITY IDENTITY verify both the INTEGRITY of an electronic document and the IDENTITY of the person VERIFIABILITY who has signed it on a long term basis. Electronic signatures cannot ensure the confidentiality of electronic documents. Electronic Signatures 4
What does an electronic signature do? An electronic signature is the electronic equivalent of a handwritten signature; in other words, it can be used to • reliably verify that an electronic document has not been modified, • reliably identify the person who has signed an electronic document, and • INTEGRITY IDENTITY verify both the INTEGRITY of an electronic document and the IDENTITY of the person VERIFIABILITY who has signed it on a long term basis. Electronic signatures cannot ensure the confidentiality of electronic documents. Electronic Signatures 4
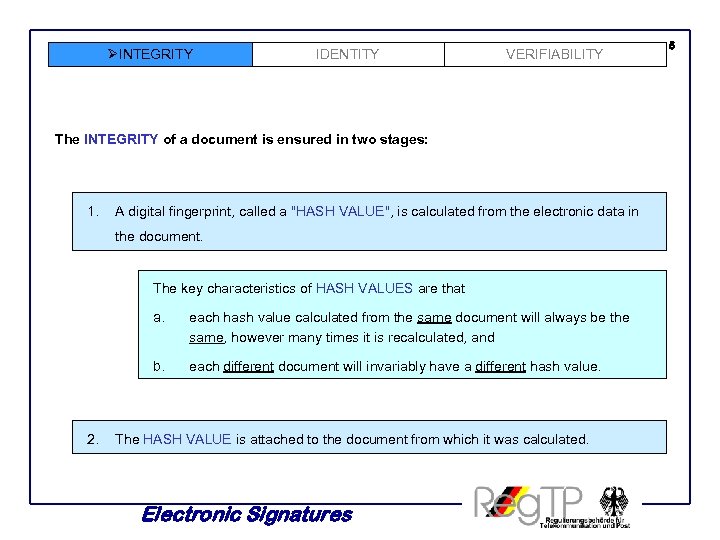 ØINTEGRITY IDENTITY VERIFIABILITY The INTEGRITY of a document is ensured in two stages: 1. A digital fingerprint, called a "HASH VALUE", is calculated from the electronic data in the document. The key characteristics of HASH VALUES are that a. b. 2. each hash value calculated from the same document will always be the same, however many times it is recalculated, and each different document will invariably have a different hash value. The HASH VALUE is attached to the document from which it was calculated. Electronic Signatures 5
ØINTEGRITY IDENTITY VERIFIABILITY The INTEGRITY of a document is ensured in two stages: 1. A digital fingerprint, called a "HASH VALUE", is calculated from the electronic data in the document. The key characteristics of HASH VALUES are that a. b. 2. each hash value calculated from the same document will always be the same, however many times it is recalculated, and each different document will invariably have a different hash value. The HASH VALUE is attached to the document from which it was calculated. Electronic Signatures 5
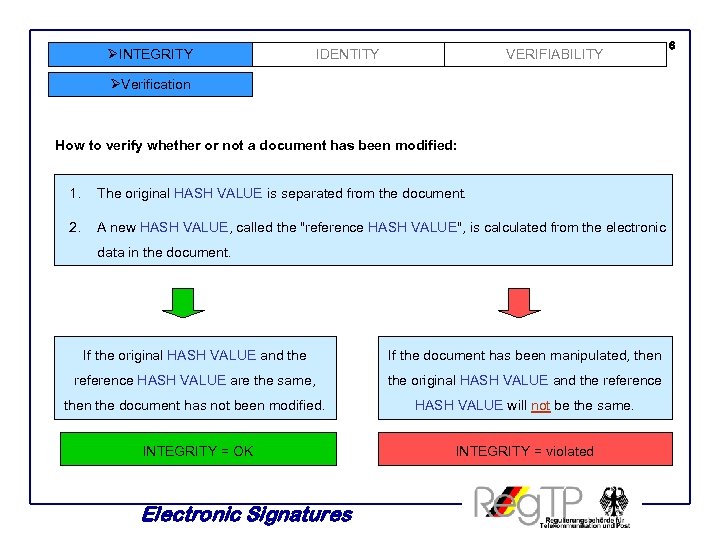 ØINTEGRITY IDENTITY VERIFIABILITY ØVerification How to verify whether or not a document has been modified: 1. The original HASH VALUE is separated from the document. 2. A new HASH VALUE, called the "reference HASH VALUE", is calculated from the electronic data in the document. If the original HASH VALUE and the If the document has been manipulated, then reference HASH VALUE are the same, the original HASH VALUE and the reference then the document has not been modified. HASH VALUE will not be the same. INTEGRITY = OK INTEGRITY = violated Electronic Signatures 6
ØINTEGRITY IDENTITY VERIFIABILITY ØVerification How to verify whether or not a document has been modified: 1. The original HASH VALUE is separated from the document. 2. A new HASH VALUE, called the "reference HASH VALUE", is calculated from the electronic data in the document. If the original HASH VALUE and the If the document has been manipulated, then reference HASH VALUE are the same, the original HASH VALUE and the reference then the document has not been modified. HASH VALUE will not be the same. INTEGRITY = OK INTEGRITY = violated Electronic Signatures 6
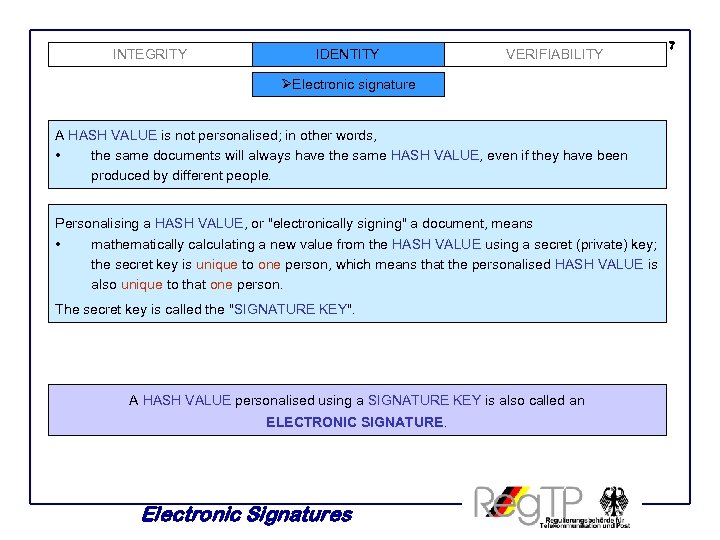 INTEGRITY IDENTITY VERIFIABILITY ØElectronic signature A HASH VALUE is not personalised; in other words, • the same documents will always have the same HASH VALUE, even if they have been produced by different people. Personalising a HASH VALUE, or "electronically signing" a document, means • mathematically calculating a new value from the HASH VALUE using a secret (private) key; the secret key is unique to one person, which means that the personalised HASH VALUE is also unique to that one person. The secret key is called the "SIGNATURE KEY". A HASH VALUE personalised using a SIGNATURE KEY is also called an ELECTRONIC SIGNATURE. Electronic Signatures 7
INTEGRITY IDENTITY VERIFIABILITY ØElectronic signature A HASH VALUE is not personalised; in other words, • the same documents will always have the same HASH VALUE, even if they have been produced by different people. Personalising a HASH VALUE, or "electronically signing" a document, means • mathematically calculating a new value from the HASH VALUE using a secret (private) key; the secret key is unique to one person, which means that the personalised HASH VALUE is also unique to that one person. The secret key is called the "SIGNATURE KEY". A HASH VALUE personalised using a SIGNATURE KEY is also called an ELECTRONIC SIGNATURE. Electronic Signatures 7
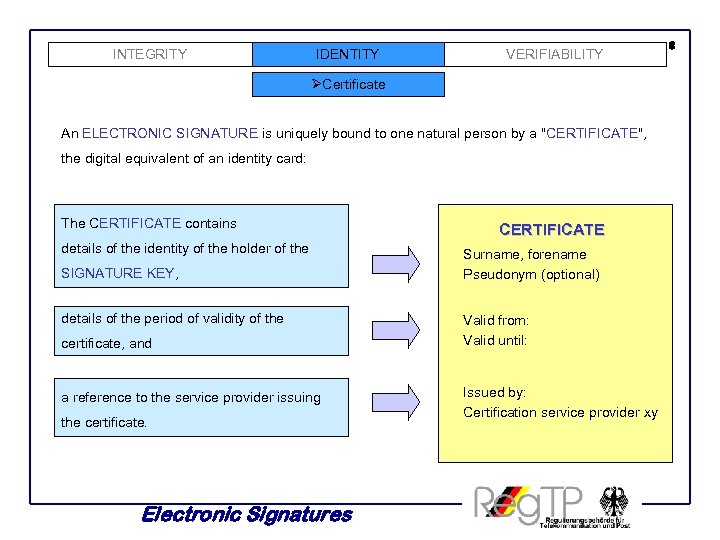 INTEGRITY IDENTITY VERIFIABILITY ØCertificate An ELECTRONIC SIGNATURE is uniquely bound to one natural person by a "CERTIFICATE", the digital equivalent of an identity card: The CERTIFICATE contains details of the identity of the holder of the SIGNATURE KEY, details of the period of validity of the certificate, and a reference to the service provider issuing the certificate. Electronic Signatures CERTIFICATE Surname, forename Pseudonym (optional) Valid from: Valid until: Issued by: Certification service provider xy 8
INTEGRITY IDENTITY VERIFIABILITY ØCertificate An ELECTRONIC SIGNATURE is uniquely bound to one natural person by a "CERTIFICATE", the digital equivalent of an identity card: The CERTIFICATE contains details of the identity of the holder of the SIGNATURE KEY, details of the period of validity of the certificate, and a reference to the service provider issuing the certificate. Electronic Signatures CERTIFICATE Surname, forename Pseudonym (optional) Valid from: Valid until: Issued by: Certification service provider xy 8
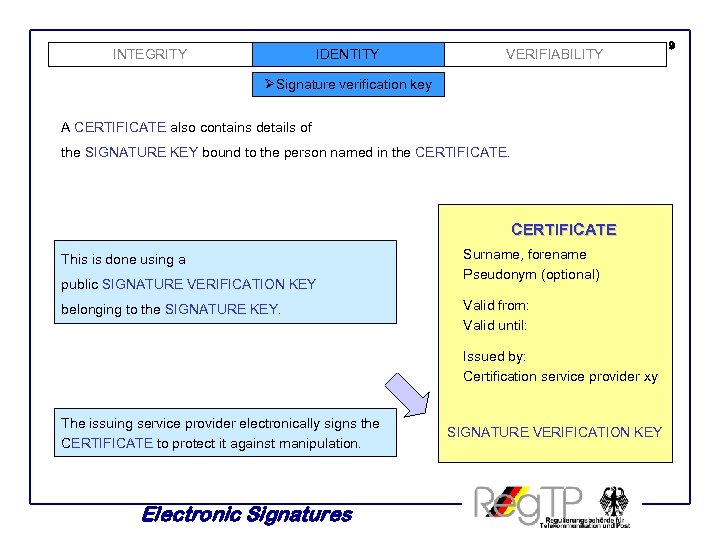 INTEGRITY IDENTITY VERIFIABILITY ØSignature verification key A CERTIFICATE also contains details of the SIGNATURE KEY bound to the person named in the CERTIFICATE This is done using a public SIGNATURE VERIFICATION KEY belonging to the SIGNATURE KEY. Surname, forename Pseudonym (optional) Valid from: Valid until: Issued by: Certification service provider xy The issuing service provider electronically signs the CERTIFICATE to protect it against manipulation. Electronic Signatures SIGNATURE VERIFICATION KEY 9
INTEGRITY IDENTITY VERIFIABILITY ØSignature verification key A CERTIFICATE also contains details of the SIGNATURE KEY bound to the person named in the CERTIFICATE This is done using a public SIGNATURE VERIFICATION KEY belonging to the SIGNATURE KEY. Surname, forename Pseudonym (optional) Valid from: Valid until: Issued by: Certification service provider xy The issuing service provider electronically signs the CERTIFICATE to protect it against manipulation. Electronic Signatures SIGNATURE VERIFICATION KEY 9
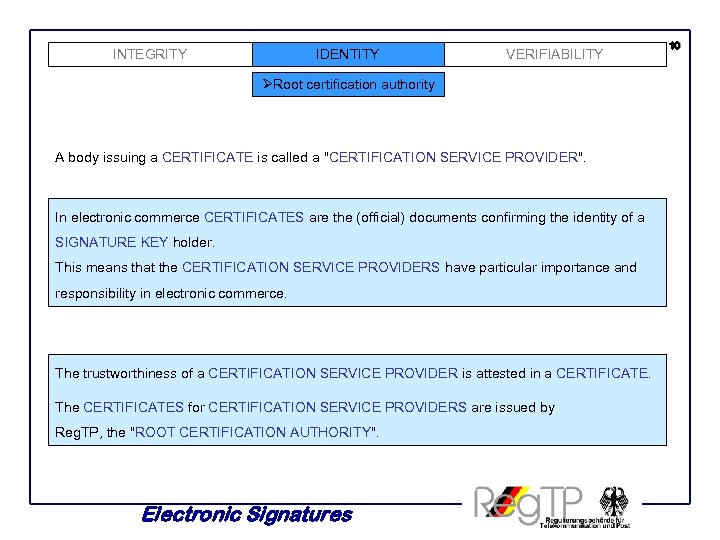 INTEGRITY IDENTITY VERIFIABILITY ØRoot certification authority A body issuing a CERTIFICATE is called a "CERTIFICATION SERVICE PROVIDER". In electronic commerce CERTIFICATES are the (official) documents confirming the identity of a SIGNATURE KEY holder. This means that the CERTIFICATION SERVICE PROVIDERS have particular importance and responsibility in electronic commerce. The trustworthiness of a CERTIFICATION SERVICE PROVIDER is attested in a CERTIFICATE. The CERTIFICATES for CERTIFICATION SERVICE PROVIDERS are issued by Reg. TP, the "ROOT CERTIFICATION AUTHORITY". Electronic Signatures 10
INTEGRITY IDENTITY VERIFIABILITY ØRoot certification authority A body issuing a CERTIFICATE is called a "CERTIFICATION SERVICE PROVIDER". In electronic commerce CERTIFICATES are the (official) documents confirming the identity of a SIGNATURE KEY holder. This means that the CERTIFICATION SERVICE PROVIDERS have particular importance and responsibility in electronic commerce. The trustworthiness of a CERTIFICATION SERVICE PROVIDER is attested in a CERTIFICATE. The CERTIFICATES for CERTIFICATION SERVICE PROVIDERS are issued by Reg. TP, the "ROOT CERTIFICATION AUTHORITY". Electronic Signatures 10
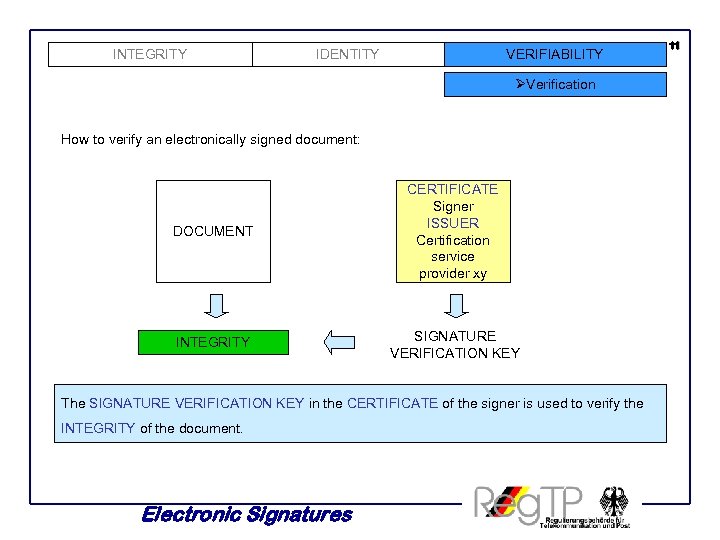 INTEGRITY IDENTITY VERIFIABILITY ØVerification How to verify an electronically signed document: DOCUMENT CERTIFICATE Signer ISSUER Certification service provider xy INTEGRITY SIGNATURE VERIFICATION KEY The SIGNATURE VERIFICATION KEY in the CERTIFICATE of the signer is used to verify the INTEGRITY of the document. Electronic Signatures 11
INTEGRITY IDENTITY VERIFIABILITY ØVerification How to verify an electronically signed document: DOCUMENT CERTIFICATE Signer ISSUER Certification service provider xy INTEGRITY SIGNATURE VERIFICATION KEY The SIGNATURE VERIFICATION KEY in the CERTIFICATE of the signer is used to verify the INTEGRITY of the document. Electronic Signatures 11
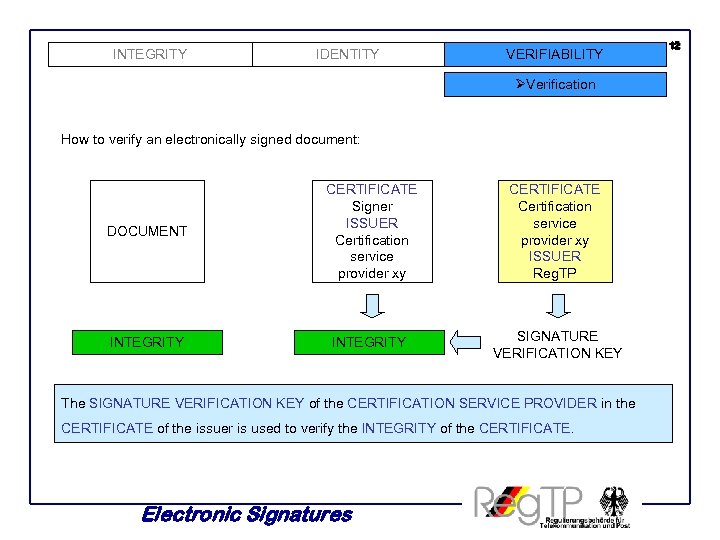 INTEGRITY IDENTITY VERIFIABILITY ØVerification How to verify an electronically signed document: DOCUMENT CERTIFICATE Signer ISSUER Certification service provider xy CERTIFICATE Certification service provider xy ISSUER Reg. TP INTEGRITY SIGNATURE VERIFICATION KEY The SIGNATURE VERIFICATION KEY of the CERTIFICATION SERVICE PROVIDER in the CERTIFICATE of the issuer is used to verify the INTEGRITY of the CERTIFICATE. Electronic Signatures 12
INTEGRITY IDENTITY VERIFIABILITY ØVerification How to verify an electronically signed document: DOCUMENT CERTIFICATE Signer ISSUER Certification service provider xy CERTIFICATE Certification service provider xy ISSUER Reg. TP INTEGRITY SIGNATURE VERIFICATION KEY The SIGNATURE VERIFICATION KEY of the CERTIFICATION SERVICE PROVIDER in the CERTIFICATE of the issuer is used to verify the INTEGRITY of the CERTIFICATE. Electronic Signatures 12
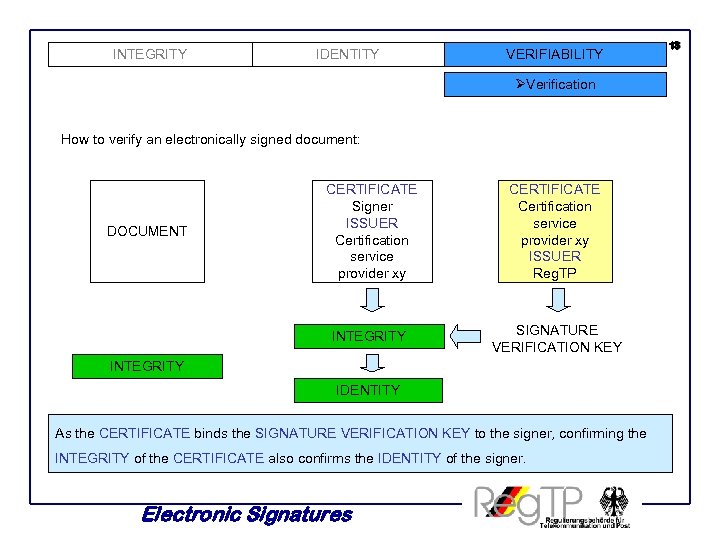 INTEGRITY IDENTITY VERIFIABILITY ØVerification How to verify an electronically signed document: CERTIFICATE Certification service provider xy ISSUER Reg. TP INTEGRITY DOCUMENT CERTIFICATE Signer ISSUER Certification service provider xy SIGNATURE VERIFICATION KEY INTEGRITY IDENTITY As the CERTIFICATE binds the SIGNATURE VERIFICATION KEY to the signer, confirming the INTEGRITY of the CERTIFICATE also confirms the IDENTITY of the signer. Electronic Signatures 13
INTEGRITY IDENTITY VERIFIABILITY ØVerification How to verify an electronically signed document: CERTIFICATE Certification service provider xy ISSUER Reg. TP INTEGRITY DOCUMENT CERTIFICATE Signer ISSUER Certification service provider xy SIGNATURE VERIFICATION KEY INTEGRITY IDENTITY As the CERTIFICATE binds the SIGNATURE VERIFICATION KEY to the signer, confirming the INTEGRITY of the CERTIFICATE also confirms the IDENTITY of the signer. Electronic Signatures 13
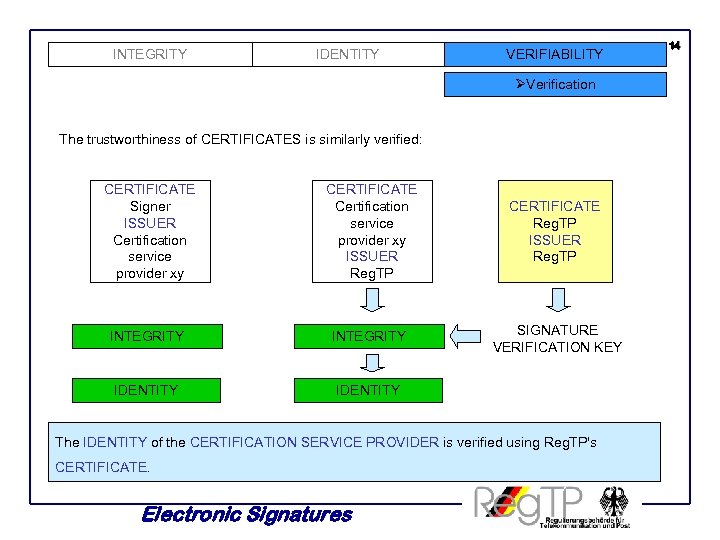 INTEGRITY IDENTITY VERIFIABILITY ØVerification The trustworthiness of CERTIFICATES is similarly verified: CERTIFICATE Signer ISSUER Certification service provider xy CERTIFICATE Certification service provider xy ISSUER Reg. TP CERTIFICATE Reg. TP ISSUER Reg. TP INTEGRITY SIGNATURE VERIFICATION KEY IDENTITY The IDENTITY of the CERTIFICATION SERVICE PROVIDER is verified using Reg. TP's CERTIFICATE. Electronic Signatures 14
INTEGRITY IDENTITY VERIFIABILITY ØVerification The trustworthiness of CERTIFICATES is similarly verified: CERTIFICATE Signer ISSUER Certification service provider xy CERTIFICATE Certification service provider xy ISSUER Reg. TP CERTIFICATE Reg. TP ISSUER Reg. TP INTEGRITY SIGNATURE VERIFICATION KEY IDENTITY The IDENTITY of the CERTIFICATION SERVICE PROVIDER is verified using Reg. TP's CERTIFICATE. Electronic Signatures 14
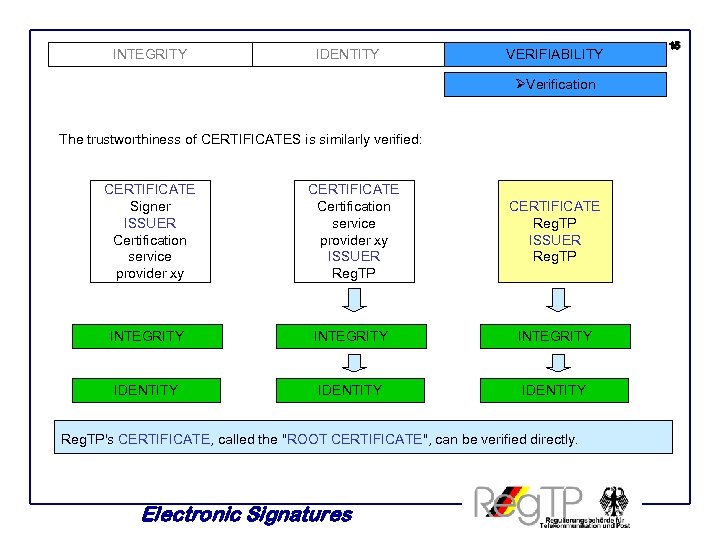 INTEGRITY IDENTITY VERIFIABILITY ØVerification The trustworthiness of CERTIFICATES is similarly verified: CERTIFICATE Signer ISSUER Certification service provider xy CERTIFICATE Certification service provider xy ISSUER Reg. TP CERTIFICATE Reg. TP ISSUER Reg. TP INTEGRITY IDENTITY Reg. TP's CERTIFICATE, called the "ROOT CERTIFICATE", can be verified directly. Electronic Signatures 15
INTEGRITY IDENTITY VERIFIABILITY ØVerification The trustworthiness of CERTIFICATES is similarly verified: CERTIFICATE Signer ISSUER Certification service provider xy CERTIFICATE Certification service provider xy ISSUER Reg. TP CERTIFICATE Reg. TP ISSUER Reg. TP INTEGRITY IDENTITY Reg. TP's CERTIFICATE, called the "ROOT CERTIFICATE", can be verified directly. Electronic Signatures 15
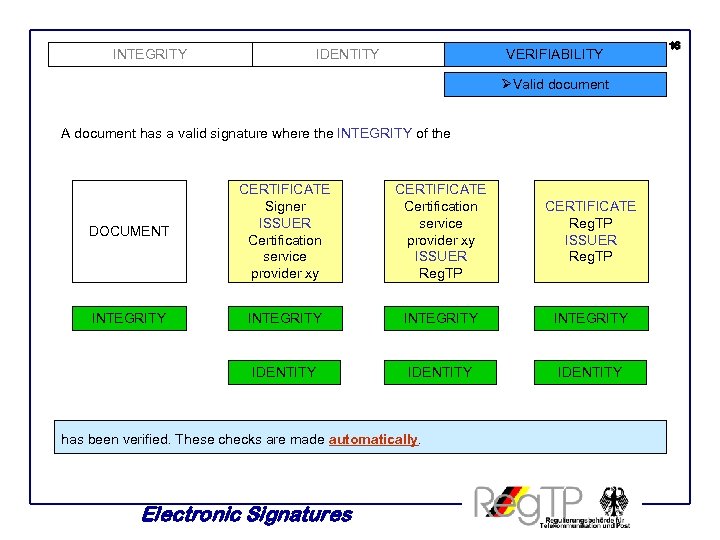 INTEGRITY IDENTITY VERIFIABILITY ØValid document A document has a valid signature where the INTEGRITY of the DOCUMENT CERTIFICATE Signer ISSUER Certification service provider xy CERTIFICATE Certification service provider xy ISSUER Reg. TP CERTIFICATE Reg. TP ISSUER Reg. TP INTEGRITY IDENTITY has been verified. These checks are made automatically. Electronic Signatures 16
INTEGRITY IDENTITY VERIFIABILITY ØValid document A document has a valid signature where the INTEGRITY of the DOCUMENT CERTIFICATE Signer ISSUER Certification service provider xy CERTIFICATE Certification service provider xy ISSUER Reg. TP CERTIFICATE Reg. TP ISSUER Reg. TP INTEGRITY IDENTITY has been verified. These checks are made automatically. Electronic Signatures 16
 INTEGRITY IDENTITY VERIFIABILITY ØTrust centre directory service A list is kept of all the CERTIFICATES needed to verify an electronically signed document. A list, called a "CERTIFICATE REVOCATION LIST", is also kept of all the CERTIFICATES that have been revoked. A CERTIFICATE can be revoked if, for instance, the SIGNATURE KEY of the holder identified in the CERTIFICATE has been stolen. As soon as a CERTIFICATE has been revoked, it cannot be used to create a valid electronic signature. The list of CERTIFICATES and the CERTIFICATE REVOCATION LIST together form the DIRECTORY SERVICE. The DIRECTORY SERVICE is available to anyone at any time (24 hours a day) for information for validity checks. The DIRECTORY SERVICE and the technical components used by a CERTIFICATION SERVICE PROVIDER to produce certificates are located in a particularly secure environment, called a "TRUST CENTRE". Electronic Signatures 17
INTEGRITY IDENTITY VERIFIABILITY ØTrust centre directory service A list is kept of all the CERTIFICATES needed to verify an electronically signed document. A list, called a "CERTIFICATE REVOCATION LIST", is also kept of all the CERTIFICATES that have been revoked. A CERTIFICATE can be revoked if, for instance, the SIGNATURE KEY of the holder identified in the CERTIFICATE has been stolen. As soon as a CERTIFICATE has been revoked, it cannot be used to create a valid electronic signature. The list of CERTIFICATES and the CERTIFICATE REVOCATION LIST together form the DIRECTORY SERVICE. The DIRECTORY SERVICE is available to anyone at any time (24 hours a day) for information for validity checks. The DIRECTORY SERVICE and the technical components used by a CERTIFICATION SERVICE PROVIDER to produce certificates are located in a particularly secure environment, called a "TRUST CENTRE". Electronic Signatures 17
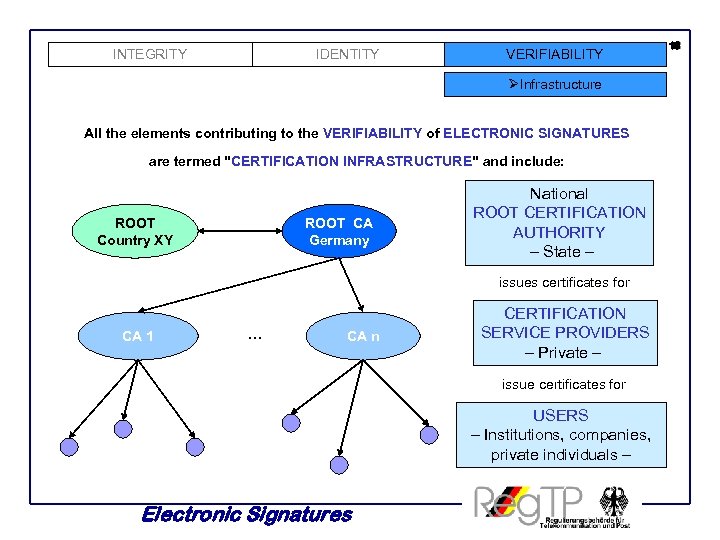 INTEGRITY IDENTITY VERIFIABILITY ØInfrastructure All the elements contributing to the VERIFIABILITY of ELECTRONIC SIGNATURES are termed "CERTIFICATION INFRASTRUCTURE" and include: ROOT Country XY ROOT CA Germany National ROOT CERTIFICATION AUTHORITY – State – issues certificates for CA 1 . . . CA n CERTIFICATION SERVICE PROVIDERS – Private – issue certificates for USERS – Institutions, companies, private individuals – Electronic Signatures 18
INTEGRITY IDENTITY VERIFIABILITY ØInfrastructure All the elements contributing to the VERIFIABILITY of ELECTRONIC SIGNATURES are termed "CERTIFICATION INFRASTRUCTURE" and include: ROOT Country XY ROOT CA Germany National ROOT CERTIFICATION AUTHORITY – State – issues certificates for CA 1 . . . CA n CERTIFICATION SERVICE PROVIDERS – Private – issue certificates for USERS – Institutions, companies, private individuals – Electronic Signatures 18
 INTEGRITY IDENTITY VERIFIABILITY ØLong term signatures In order to create the equivalent of handwritten signatures, electronically signed documents must remain VERIFIABLE over long periods of time (decades): This means that the DIRECTORY SERVICE of each CERTIFICATION SERVICE PROVIDER must operate reliably over a period of years and must be interoperable with other DIRECTORY SERVICES in the same INFRASTRUCTURE. In addition, all the procedures and technical components used must have been comprehensively verified in order to guarantee a high level of security for electronically signed documents on a long term basis. The new Electronic Signatures Act takes full account of these special circumstances by creating a framework that ensures the security of electronic signatures. Reg. TP's TRUST CENTRE was the first to meet the stringent security requirements of the Act. It forms the core of Germany's CERTIFICATION INFRASTRUCTURE for electronic signatures. Electronic Signatures 19
INTEGRITY IDENTITY VERIFIABILITY ØLong term signatures In order to create the equivalent of handwritten signatures, electronically signed documents must remain VERIFIABLE over long periods of time (decades): This means that the DIRECTORY SERVICE of each CERTIFICATION SERVICE PROVIDER must operate reliably over a period of years and must be interoperable with other DIRECTORY SERVICES in the same INFRASTRUCTURE. In addition, all the procedures and technical components used must have been comprehensively verified in order to guarantee a high level of security for electronically signed documents on a long term basis. The new Electronic Signatures Act takes full account of these special circumstances by creating a framework that ensures the security of electronic signatures. Reg. TP's TRUST CENTRE was the first to meet the stringent security requirements of the Act. It forms the core of Germany's CERTIFICATION INFRASTRUCTURE for electronic signatures. Electronic Signatures 19


