02eca4e533db7506d17e8b07e6af6810.ppt
- Количество слайдов: 87

1 Credits: Parts of the slides are based on slides created by UNIX textbook authors, Syed M. Sarwar, Robert Koretsky, Syed A. Sarwar, 2005 Addison Wesley Jozef Goetz, 2014 expanded by Jozef Goetz, 2014

Objectives n You may ignore all slides with commands started with r* n To describe networks, the Internet and internetworks and explain why they are used n To discuss briefly the TCP/IP protocol suite, IP addresses, protocol ports, and internet services and applications n To explain what the client-server software model is and how it works n To discuss various network software tools for electronic communication , remote login, file transfer, remote command execution , and status reporting 1. 2. 3. 4. n To describe briefly the secure shell n To cover the commands and primitives Jozef Goetz, 2014 2

Computer Networks and Internet works n When two or more computer hardware resources are connected they form a computer network 1. 2. 3. n Jozef Goetz, 2014 Local area Networks (LANs) Metropolitan area networks (MANs) Wide area networks (WANs) An internetwork is a network of networks 3

A brief history of the Internet 4 • ARPANET (50 s and 60 s, some universities) • NSFNET (late 70 s, all universities) • TCP/IP (invention ’ 74) became the official protocol in 1983. n n When NSFNET and the ARPANET were connected, the growth became exponential Many regional networks (Canada, Europe, the Pacific) joined up In mid-80 s people began viewing the collection of networks as the Internet The glue that holds the Internet together is the TCP/IP reference model and TCP/IP protocol stack • ANS (Advanced Networks and Service) by MERIT, MCI, and IBM took over NSFNET in 1990 as ANSNET • ANSNET sold to American Online in 1995. Jozef Goetz, 2014

The ARPANET n The original ARPANET design. IMP - Interface Message Processor Jozef Goetz, 2014 5

The ARPANET n Growth of the ARPANET (a) December 1969. (b) July 1970. (c) March 1971. (d) April 1972. (e) September 1972. Jozef Goetz, 2014 6

NSFNET n The NSFNET backbone in 1988. Jozef Goetz, 2014 7

Internet Usage n Machine is on the Internet if n n 8 it runs the TCP/IP protocol stack, has an IP address, and can send IP packets to all the other machines on the Internet Millions PC can call up an Internet service provider using a modem, be assigned a temporary (dynamic) IP address, and send IP packets to all the other hosts Jozef Goetz, 2014

Internet Usage n Traditional applications (1970 – 1990) n E-mail n News n n Remote login n n newsgroups devoted to different topics) Using telnet, Win. SCP, rlogin, ssh programs File transfer n Jozef Goetz, 2014 Using FTP programs 9

Internet Usage n Early ’ 90 s new application the WWW (World Wide Web) n n n 10 invented by physicist Tim Berbers-Lee brought millions of nonacademic users They started using the Mosaic browser (GUI) and then other browsers The ch-r of the network was changed from an academic and military playground to a public utility Jozef Goetz, 2014

Architecture of the Internet. n 11 A NAP (Network Access Point) is a room full of routers, at least one per backbone n n Overview of the Internet. n Signal is transferred to the ISP’s (Internet Service Provider) POP – Point of Present (located in the tel. switching office) and injected into the ISP’s regional network n from this point the system is fully digital and Jozef Goetz, 2014 packet switched n A LAN in the room connects all the routers, so packets can be forwarded from any backbone to any other backbone

Collection of Subnetworks 12 SNA: Systems Network Architecture -IBM's mainframe network standards The Internet is an interconnected collection of many networks. Jozef Goetz, 2014

X. 25 Networks • Developed during 70's. 1 st public data network interface between public packet-switched networks and customers. Data packet has a 3 -byte header n a 12 bit connection #, n a packet sequence #, n an acknowledgment # etc. and up to 126 bytes of data • Operate at 64 Kbps, so are very slow and becoming outdated. However there are still many of them in operation. • Connection oriented: Uses: • Switched Virtual Circuit n n established when the first packet is sent circuit remains for duration of session providing in-order delivery, and flow control. • Permanent Virtual Circuit n established by agreement between the customer and the carrier: n Jozef Goetz, 2014 Like a leased line 13

Frame Relay 14 • Takes advantage of modern high-speed reliable digital phone lines. Connection oriented. Property: In-order delivery, no error control, no flow control, akin to LAN • This allows simple protocols with work done by user computers rather than by the network. n Runs at 1. 5 Mbps with few features. • Customer leases a permanent virtual circuit between two points. n Jozef Goetz, 2014 this "virtual leased line" means that the wire is shared with other users at a great price reduction.

Broadband ISDN and ATM 15 Connection oriented. • ISDN (Integrated Services Digital Network) n offers cable, video on demand, e-mail, etc. • ATM (Asynchronous Transfer Mode) early ’ 90 s is underlying n n Mechanism inside the tel. system. Transmits in small fixed-size cells. Not synchronous. n n Jozef Goetz, 2014 Was supposed to merge voice, data, cable TV, telex, telegraph etc. into a single integrated system – it didn’t happen Alive, used by carriers for internal transport

16 (a) Computer Networks and (b) Internetworks R - routers Jozef Goetz, 2014

Why Computer Networks and Internetworks? n Sharing of computer resources n n Network as a communication medium n n inexpensive, fast, reliable Cost efficiency n n computers, printers, plotters, scanners, files and software large computing power available Less performance degradation n if one computer crashes, the remaining ones are still up Jozef Goetz, 2014 17

Network Models n n International Standards Organization’s Open System Interconnect Reference Model (ISO’s OSI 7 -Layer Reference Model) The TCP/IP 5 -layer Model n Jozef Goetz, 2014 Used in the Internet 18

Network Models with approximate mapping between the two • The first 4 layers deal with the communication between hosts. • The 5 th layer deals with the Internet services provided by various applications. • Most of the 1 st layer is handled by hardware (communication medium used, attachments of hosts to the medium). • The rest of the 1 st layer and all the 2 nd layer is handled by the (Network Interface Card) NIC card in a host. • Layers 3 and 4 are fully implemented in the operating systems kernel on most existing systems. Jozef Goetz, 2014 • The first 2 layers are network hardware specific, the others are work independently of the physical layer 19

Reference Models n n n n Protocols and networks in the TCP/IP model initially. The Application layer contains all of the higherlevel protocols – telnet - virtual terminal protocol – FTP – file transfer – SMTP – e-mail – DNS - Domain Name System – NNTP - Network News Transfer Protocol – HTTP - Hypertext Transfer Protocol Jozef Goetz, 2014 20

The TCP/IP Protocol Suite n As a user you can see the application layer in the form of applications and utilities 1. 2. 3. 4. Jozef Goetz, 2014 Web browsing, file transfer, remote login etc. 1 st -2 nd layer is handled by the Network Interface Card -NIC card 21

The TCP/IP Protocol Suite n 22 IGMP - Internet Group Management Protocol n handles multicasting ICMP - Internet Control Message Protocol n n Handles errors and control messages. Protocol is used to forward information, primarily error messages. To see if a computer is running, the `ping' program sends an echo request, which is part of ICMP. n ARP -Address Resolution Protocol is a protocol for mapping an Internet Protocol IP address to a physical machine address (MAC) that is recognized in the local network. n For example, in IP Version 4, the most common level of IP in use today, an address is 32 bits long. n In an Ethernet LAN, however, addresses for attached devices are 48 bits 1 st -2 nd layer Jozef Goetz, 2014 n RARP - Reverse Address Resolution Protocol is a protocol by which a physical machine in a LAN can request to learn its IP address from a gateway server's Address Resolution Protocol (ARP) table or cache. n A network administrator creates a table in a LAN’s gateway router that maps the physical machine (MAC addresses) into IP addresses. is handled by the Network Interface Card -NIC card

Transport Layer: The TCP and UDP n The purpose of the transport layer is to transport application data from your machine to a remote machine and vice versa n n User Datagram Protocol (UDP) is a connectionless protocol, offers the best effort delivery service Transmission Control Protocol (TCP) is a connection-oriented protocol that establish a virtual connection with the destination before transmitting data, n thus the TCP leads completely reliable, n error free n in-sequence delivery of data n Jozef Goetz, 2014 23

n n n Routing of the Application Data The Internet Protocol (IP) The network layer is responsible for routing application data to the destination host IP is responsible for transporting IP datagrams containing TCP segments or UDP datagrams to the destination host The IP is a connectionless protocol, it simply sends the application data without establishing virtual connection with the destination before transmitting data, n Jozef Goetz, 2014 thus the IP routing is the best effort and doesn’t guarantee delivery of TCP segments or UDP datagrams 24

Routing of the Application Data The Internet Protocol (IP) n n n In IPv 4 the IP address (32 bits) is divided into three fields: 1. address class, 2. network ID and 3. host ID The address class field identifies the class of the address and dictates the number of bits used in the network ID and host ID fields This scheme has 5 address classes : A, B, C, D, E Jozef Goetz, 2014 25

IPv 4 Addresses in Dotted Decimal Notation n 32 -bit binary numbers are difficult to remember IPv 4 addresses are given in dotted decimal notation (DDN) In DDN all 4 bytes of an IPv 4 address are written in their decimal equivalents and are separated by dots n Example: 192. 10. 21 Jozef Goetz, 2014 26

IP Addresses IP address formats. 127. 0. 0. 0 (or 127. x. x. x, where x is between 0 -127) is known as localhost is used to send a data packet to itself. for testing purpose. nhost ID = 1… 1 is the broadcast address in order to send a data packet to all hosts on a network n Jozef Goetz, 2014 27

IPv 4 Address Classes The sum of network IDs for class A, B, C = 2^7 + 2^14 + 2^21 = 1, 113, 664 networks The sum of hosts IDs for class A, B, C = 2^24 + 2^16 + 2^ 8 = 3, 758, 096, 400 hosts Jozef Goetz, 2014 28

IPv 4 Address Classes Prove all ranges!!! Jozef Goetz, 2014 29
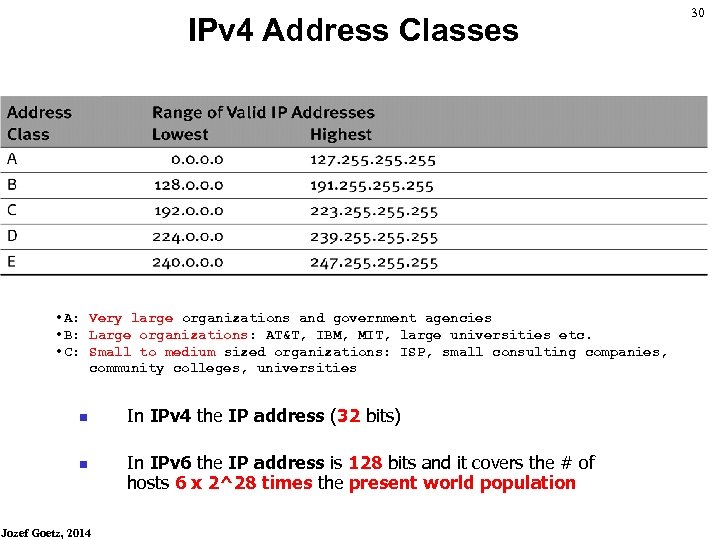
IPv 4 Address Classes • A: Very large organizations and government agencies • B: Large organizations: AT&T, IBM, MIT, large universities etc. • C: Small to medium sized organizations: ISP, small consulting companies, community colleges, universities n n Jozef Goetz, 2014 In IPv 4 the IP address (32 bits) In IPv 6 the IP address is 128 bits and it covers the # of hosts 6 x 2^28 times the present world population 30

31 IPv 4 Address Classes Figure 14. 5 An internetwork of 4 networks with one class A, one class B, and 2 class C networks connected via 4 routers class C class A class C Jozef Goetz, 2014 class B

Symbolic Names 32 Symbolic names are easier to remember n remain the same even if the numeric address changes n must be unique for a host on the Internet n Format: hostname. domain_name e. g. students. up. edu where: domain_name = organization_name. top-level_domain n organization_name is assigned by the Network Information Center e. g. laverne. edu Attaching the name of a host to a domain name with a period between them yields the Fully Qualified Domain Name (FQDN) for the host n e. g. egr. up. edu – egr is a host name at the University of Portland Jozef Goetz, 2014

33 A portion of the Internet domain name hierarchy Jozef Goetz, 2014

Top-Level Internet Domains Jozef Goetz, 2014 34

35 Jozef Goetz, 2014

The Domain Name System n Domain Name System (DNS) service translates symbolic names to equivalent IP addresses n n DNS implements a distributed database of name-to-address mappings A set of dedicated hosts run name servers that take requests from the application software n n and work together to map domain names to the corresponding IP addresses every organization runs at least 1 name server n Jozef Goetz, 2014 app uses gethostbyname() to get its IP address 36

Inverse domain n The servers that handle the inverse domain are also hierarchical. n This means the netid part of the address should be at a higher level than the subnetid part, and the subnetid part higher than the hosted part. n In this way, a server serving the whole site is at a higher level than the servers serving each subnet. n n To follow the convention of reading the domain labels from the bottom to the top, an IP address such as 132. 34. 45. 121 (a class 13: address with netid 132. 34) is read as 121. 45. 34. 132. in-addr. area. n This configuration makes the domain look inverted when compared to a generic or country domain. Jozef Goetz, 2014 37
![DNS lookup utility: host [cs 253 u@shell cs 253 u]$ host ecs. fullerton. edu DNS lookup utility: host [cs 253 u@shell cs 253 u]$ host ecs. fullerton. edu](https://present5.com/presentation/02eca4e533db7506d17e8b07e6af6810/image-38.jpg)
DNS lookup utility: host [cs 253 u@shell cs 253 u]$ host ecs. fullerton. edu has address 137. 151. 27. 1 [cs 253 u@shell cs 253 u]$ host 137. 151. 27. 151. 137. in-addr. arpa domain name pointer ecs. fullerton. edu. [cs 253 u@shell cs 253 u]$ [jgoetz ulv. edu jgoetz]$ host ulv. edu has address 192. 231. 179. 66 mail is handled (pri=5) by mxg 1. ulv. edu mail is handled (pri=5) by mxg 2. ulv. edu [jgoetz]$ host 192. 231. 179. 66 66. 179. 231. 192. IN-ADDR. ARPA domain name pointer www. ulv. edu Jozef Goetz, 2014 38

The Domain Name System #DNS service is to use a static host file /etc/hosts #a static hosts file contains the domain names and their IP addresses configured by the system admin $ cat /etc/hosts [jgoetz]$ cat /etc/hosts 127. 0. 0. 1 localhost 192. 231. 179. 91 raq 4. ulv. edu # Cobalt automated entry for eth 0 192. 231. 179. 81 loki. ulv. edu loki #Veritas Backup Server #to view IP address and other info about host’s interface to the network $ /sbin/ifconfig –a # faculty. ulv. edu has 192. 231. 179. 91 [jgoetz]$ /sbin/ifconfig -a eth 0 Link encap: Ethernet HWaddr 00: 10: E 0: 05: A 8: F 4 inet addr: 192. 231. 179. 91 Bcast: 192. 231. 179. 95 Mask: 255. 224 UP BROADCAST RUNNING MULTICAST MTU: 1500 Metric: 1 RX packets: 212947098 errors: 0 dropped: 0 overruns: 0 frame: 0 TX packets: 318162567 errors: 3 dropped: 0 overruns: 0 carrier: 3 collisions: 0 txqueuelen: 100 Interrupt: 5 Base address: 0 x 8000 eth 1 Link encap: Ethernet HWaddr 00: 10: E 0: 05: A 8: F 3 BROADCAST MULTICAST MTU: 1500 Metric: 1 RX packets: 0 errors: 0 dropped: 0 overruns: 0 frame: 0 TX packets: 0 errors: 0 dropped: 0 overruns: 0 carrier: 0 collisions: 0 txqueuelen: 100 Interrupt: 9 Base address: 0 x 8100 lo Link encap: Local Loopback inet addr: 127. 0. 0. 1 Mask: 255. 0. 0. 0 UP LOOPBACK RUNNING MTU: 3924 Metric: 1 RX packets: 1749416 errors: 0 dropped: 0 overruns: 0 frame: 0 TX packets: 1749416 errors: 0 dropped: 0 overruns: 0 carrier: 0 collisions: 0 txqueuelen: 0 $ Jozef Goetz, 2014 39
![The Domain Name System [cs 253 u@shell cs 253 u]$ cat /etc/hosts # Do The Domain Name System [cs 253 u@shell cs 253 u]$ cat /etc/hosts # Do](https://present5.com/presentation/02eca4e533db7506d17e8b07e6af6810/image-40.jpg)
The Domain Name System [cs 253 u@shell cs 253 u]$ cat /etc/hosts # Do not remove the following line, or various programs # that require network functionality will fail. 127. 0. 0. 1 localhost. localdomain localhost shell 192. 168. 3. 25 ldap. int. ecs. fullerton. edu ldap 192. 168. 3. 29 ecsmysql. ecs. fullerton. edu ecsmysql 192. 168. 3. 30 mail. ecs. fullerton. edu mail 137. 151. 28. 223 lupus. ecs. fullerton. edu lupus 192. 168. 3. 200 lupus 2. ecs. fullerton. edu lupus 2 n [jgoetz@raq 4 ~]$ host 192. 231. 179. 91 n 91. 179. 231. 192. IN-ADDR. ARPA domain name pointer FACULTY. ULV. EDU Jozef Goetz, 2014 40

The Domain Name System #lookup for the IP address of a host name: [cs 253 u@shell cs 253 u]$ nslookup ecs. fullerton. edu Server: 192. 168. 3. 26 # name server Address: 192. 168. 3. 26#53 Name: Address: ecs. fullerton. edu 137. 151. 27. 1 [jgoetz]$ nslookup ulv. edu Server: ns. ulv. edu Address: 64. 69. 149. 200 Name: ulv. edu Address: 192. 231. 179. 66 [jgoetz@raq 4 Server: Address: Name: Address: ~]$ nslookup faculty. ulv. edu ns. ulv. edu # this a name server 64. 69. 149. 200 faculty. ulv. edu 192. 231. 179. 91 #nslookup uses file /etc/resolv. conf to find the host that runs the name server and passes the request over it. Jozef Goetz, 2014 [jgoetz]$ cat /etc/resolv. conf domain ulv. edu search ulv. edu nameserver 64. 69. 149. 200 nameserver 64. 69. 154. 123 [jgoetz]$ 41

The Domain Name System n nslookup uses file /etc/resolv. conf to find the host that runs the name server and passes the request over it. n n [cs 253 u@shell cs 253 u]$ cat /etc/resolv. conf nameserver 192. 168. 3. 26 dig interacts with name servers specified in /etc/resolv. conf and display their responses – gives more info than nslookup Jozef Goetz, 2014 42
![The Domain Name System [jgoetz@raq 4 ~]$ dig faculty. ulv. edu [jgoetz]$ dig ulv. The Domain Name System [jgoetz@raq 4 ~]$ dig faculty. ulv. edu [jgoetz]$ dig ulv.](https://present5.com/presentation/02eca4e533db7506d17e8b07e6af6810/image-43.jpg)
The Domain Name System [jgoetz@raq 4 ~]$ dig faculty. ulv. edu [jgoetz]$ dig ulv. edu ; <<>> Di. G 8. 3 <<>> faculty. ulv. edu ; <<>> Di. G 8. 3 <<>> ulv. edu ; ; res options: init recurs defnam dnsrch ; ; got answer: ; ; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: ; ; ->>HEADER<<- opcode: QUERY, status: 4 ; ; flags: qr aa rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 2, NOERROR, id: 4 ADDITIONAL: 2 ; ; flags: qr aa rd ra; QUERY: 1, ANSWER: 1, ; ; QUERY SECTION: AUTHORITY: 2, ADDITIONAL: 2 ; ; faculty. ulv. edu, type = A, class = IN ; ; QUERY SECTION: ; ; ulv. edu, type = A, class = IN ; ; ANSWER SECTION: faculty. ulv. edu. 1 D IN A 192. 231. 179. 91 ; ; ANSWER SECTION: ulv. edu. 12 H IN A 192. 231. 179. 66 ; ; AUTHORITY SECTION: ulv. edu. 1 D IN NS ns. ulv. edu. ; ; AUTHORITY SECTION: ulv. edu. 1 D IN NS ns 2. ulv. edu. 12 H IN NS ns. ulv. edu. ; ; ADDITIONAL SECTION: ns. ulv. edu. 1 D IN A 64. 69. 149. 200 ; ; ADDITIONAL SECTION: ns 2. ulv. edu. 1 D IN A 64. 69. 154. 123 ns. ulv. edu. 12 H IN A 64. 69. 149. 200 ns 2. ulv. edu. 12 H IN A 64. 69. 154. 123 ; ; Total query time: 25 msec ; ; FROM: raq 4. ulv. edu to SERVER: default -- 64. 69. 149. 200 Total query time: 11 msec ; ; WHEN: Wed Nov 16 22: 25 2005 ; ; FROM: raq 4. ulv. edu to SERVER: default -; ; MSG SIZE sent: 33 rcvd: 116 64. 69. 149. 200 ; ; WHEN: Thu Nov 15 16: 21: 26 2007 ; ; MSG SIZE sent: 25 rcvd: 108 Jozef Goetz, 2014 43
![The Domain Name System dig [jgoetz]$ dig ulv. edu ecs. fullerton. edu ; <<>> The Domain Name System dig [jgoetz]$ dig ulv. edu ecs. fullerton. edu ; <<>>](https://present5.com/presentation/02eca4e533db7506d17e8b07e6af6810/image-44.jpg)
The Domain Name System dig [jgoetz]$ dig ulv. edu ecs. fullerton. edu ; <<>> Di. G 9. 2. 4 <<>> ecs. fullerton. edu ; ; global options: printcmd ; ; Got answer: ; ; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 29854 ; ; flags: qr aa rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 1, ADDITIONAL: 0 ; ; QUESTION SECTION: ; ecs. fullerton. edu. IN ; ; ANSWER SECTION: ecs. fullerton. edu. 137. 151. 27. 1 86400 ; ; AUTHORITY SECTION: ecs. fullerton. edu. 86400 ; ; ; ; IN IN Query time: 22 msec SERVER: 192. 168. 3. 26#53(192. 168. 3. 26) WHEN: Fri Mar 14 23: 54: 21 2008 MSG SIZE rcvd: 65 Jozef Goetz, 2014 A A NS ; <<>> Di. G 8. 3 <<>> ulv. edu ; ; res options: init recurs defnam dnsrch ; ; got answer: ; ; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 4 ; ; flags: qr aa rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 2, ADDITIONAL: 2 ; ; QUERY SECTION: ; ; ulv. edu, type = A, class = IN ; ; ANSWER SECTION: ulv. edu. 12 H IN A 192. 231. 179. 66 ; ; AUTHORITY SECTION: ulv. edu. 12 H IN NS ns 2. ulv. edu. ns. ulv. edu. ; ; ADDITIONAL SECTION: ns. ulv. edu. 12 H IN A ns 2. ulv. edu. 12 H IN A 64. 69. 149. 200 64. 69. 154. 123 ; ; Total query time: 11 msec ; ; FROM: raq 4. ulv. edu to SERVER: default -64. 69. 149. 200 ; ; WHEN: Thu Nov 15 16: 21: 26 2007 ; ; MSG SIZE sent: 25 rcvd: 108 44

45 Well-known Internet Services Jozef Goetz, 2014

The Client-Server Software Model n n 46 Internet services are implemented by using a paradigm in which the software for a service is partitioned into 2 parts n The part that runs on the host on which the user running the application is logged on to is called the client software n The part that’s usually starts running when a host boots is called the server software Connection-oriented client server models: n client sends a connection request to the server and n the server either rejects or accepts the request. n If server accepts the request, the client and server are said to be connected through a virtual connection Jozef Goetz, 2014

47 The Client-Server Software Model http: //faculty. ulv. edu/ Jozef Goetz, 2014
![Displaying the Names. 48 uname [OPTION]. . . DESCRIPTION Print certain system information. With Displaying the Names. 48 uname [OPTION]. . . DESCRIPTION Print certain system information. With](https://present5.com/presentation/02eca4e533db7506d17e8b07e6af6810/image-48.jpg)
Displaying the Names. 48 uname [OPTION]. . . DESCRIPTION Print certain system information. With no OPTION, same as -s. -a, --all print all information -m, --machine print the machine (hardware) type -n, --nodename print the machine's network node hostname -r, --release print the operating system release -s, --sysname print the operating system name -p, --processor print the host processor type -v print the operating system version --help display this help and exit --version output version information and exit Jozef Goetz, 2014 [jgoetz]$ uname Linux [jgoetz]$ uname -n raq 4. ulv. edu [jgoetz]$ uname -a [jgoetz. Linux raq 4. ulv. edu 2. 2. 16 C 37_V #1 Sat Apr 12 15: 06: 43 PDT 2003 i 686 unknown

Displaying the Host Name 49 $ uname -n yamsrv 1. ece. gatech. edu $ uname -a Sun. OS yamsrv 1. ece. gatech. edu 5. 8 Generic_108528 -22 sun 4 u sparc SUNW, Ultra-250 $ hostname – name of the host you are logged on to yamsrv 1. ece. gatech. edu [jgoetz]$ hostname raq 4. ulv. edu Jozef Goetz, 2014 -a, --all print all information -m, --machine print the machine (hardware) type -n, --nodename print the machine's network node hostname --help
![cpu info. [jgoetz]$ less /proc/cpuinfo [cs 253 u@shell cs 253 u]$ less /proc/cpuinfo processor cpu info. [jgoetz]$ less /proc/cpuinfo [cs 253 u@shell cs 253 u]$ less /proc/cpuinfo processor](https://present5.com/presentation/02eca4e533db7506d17e8b07e6af6810/image-50.jpg)
cpu info. [jgoetz]$ less /proc/cpuinfo [cs 253 u@shell cs 253 u]$ less /proc/cpuinfo processor : 1 vendor_id : Authentic. AMD cpu family : 15 model : 35 model name : Dual Core AMD Opteron(tm) Processor 175 stepping : 2 cpu MHz : 2211. 280 cache size : 1024 KB fdiv_bug : no hlt_bug : no f 00 f_bug : no coma_bug : no fpu : yes fpu_exception : yes cpuid level : 1 flags : fpu vme de pse tsc msr pae mce cx 8 apic sep mtrr pge mca cmov pat pse 36 clflush mmx fxsr sse 2 ht syscall nx mmxext lm 3 dnowext 3 dnow lahf_ lm pni /proc/cpuinfo (END) Jozef Goetz, 2014 50

Displaying Users on a Network $ rwho | more - remote who displays info about the user currently using machines on your network: log name, computer: terminal, date and time the user logged in Bobk upibm 7: tty. C 4 Dfrakes upibm 47: ttyp 2 Lulay upsun 17: pts/0 Oster upsun 17: pts/2 Sarwar upibm 7: ttyp 2 $ rwho -a | more Bobk upibm 7: tty. C 4 dfrakes upibm 47: ttyp 2 kent upibm 48: ttyp 0 kittyt upibm 9: ttyp 0 kuhn upsun 29: console lulay upsun 17: pts/0 oster upsun 17: pts/2 pioster upsun 20: pts/0 sarwar upibm 7: ttyp 2 sarwar upsun 29: pts/0 $ Jozef Goetz, 2014 Jul Jul Jul 26 26 26 12: 03 11: 49 10: 17 12: 28 11: 15 Jul Jul Jul 26 26 16 26 26 26 12: 03 11: 49 03: 41 07: 36 13: 11 10: 17 12: 28 09: 53 11: 15 11: 24 8: 49 1: 28 99: 59 2: 41 1: 00 51
![Displaying Users on a Network. rusers [options] [host_list] Purpose: Output: to Display the login Displaying Users on a Network. rusers [options] [host_list] Purpose: Output: to Display the login](https://present5.com/presentation/02eca4e533db7506d17e8b07e6af6810/image-52.jpg)
Displaying Users on a Network. rusers [options] [host_list] Purpose: Output: to Display the login names of the remote users logged on to all the machines on our local network Information about the users logged on the hosts on your local network in one line per machine format Commonly used options/features: -a Display all host names even if no user is using it -l Display the user information in a long format similar to that displayed by the who command Jozef Goetz, 2014 52

Displaying Users on a Network for particular machine Jozef Goetz, 2014 53
![Displaying the Status of Hosts on a Network ruptime [options] – remote uptime Purpose: Displaying the Status of Hosts on a Network ruptime [options] – remote uptime Purpose:](https://present5.com/presentation/02eca4e533db7506d17e8b07e6af6810/image-54.jpg)
Displaying the Status of Hosts on a Network ruptime [options] – remote uptime Purpose: Output: Show status of all connected machines on the local area network Status of machines including machine name, up/down status, time a machine has been up (or down) for-called machine uptime, and the number of users logged on to the machine Commonly used options/features after sorting : -l Display output after sorting it with load average -t Display output after sorting it by machine uptime -u Display output after sorting it by the number of users Jozef Goetz, 2014 54

Displaying the Status of Hosts on a Network Commonly used options/features after sorting : -l Display output after sorting it with load average -t Display output after sorting it by machine uptime -u Display output after sorting it by the number of users Jozef Goetz, 2014 55
![Testing a Network Connection ping [options] hostname Purpose: Output: Send an IP datagram to Testing a Network Connection ping [options] hostname Purpose: Output: Send an IP datagram to](https://present5.com/presentation/02eca4e533db7506d17e8b07e6af6810/image-56.jpg)
Testing a Network Connection ping [options] hostname Purpose: Output: Send an IP datagram to ‘hostname’ to test whether it is on the network (or Internet); if the host is alive it simply echoes the received datagram Message(s) indicating whether the machine is alive Commonly used options/features: -c count Send and receive ‘count’ (e. g. 3) packets -f Send 100 packets per second or as many as can be handled by the network; only the superuser can use this option -s packetsize Send ‘packetsize’ packets; the default is 56 bytes (plus an 8 byte header) Jozef Goetz, 2014 56

Testing a Network Connection Jozef Goetz, 2014 ping -c count Send and receive ‘count’ packets ping -s packetsize Send ‘packetsize’ packets; the default is 56 bytes (plus an 8 byte header); Test yahoo. com 57
![Displaying Information About Users finger [options] [user_list] Purpose: Display information about the users in Displaying Information About Users finger [options] [user_list] Purpose: Display information about the users in](https://present5.com/presentation/02eca4e533db7506d17e8b07e6af6810/image-58.jpg)
Displaying Information About Users finger [options] [user_list] Purpose: Display information about the users in the ‘user_list’; without a ‘user_list’, the command displays a short status report about all the users currently logged on to the specified hosts Output: User info extracted from the ~/. project and ~/. plan files Commonly used options/features: -m Match ‘user_list’ to login names only -s Display output in a short format [jgoetz@raq 4 ~]$ finger Jozef Login: jgoetz Name: Jozef Goetz Directory: /home/sites/site 7/users/jgoetz Shell: /bin/bash On since Wed Nov 30 21: 05 (PST) on pts/1 from 64. 69. 147. 181 No mail. No Jozef Goetz, 2014 Plan. 58
![Displaying Information About Users [jgoetz@raq 4 ~]$ finger -s Jozef Login Name Tty Idle Displaying Information About Users [jgoetz@raq 4 ~]$ finger -s Jozef Login Name Tty Idle](https://present5.com/presentation/02eca4e533db7506d17e8b07e6af6810/image-59.jpg)
Displaying Information About Users [jgoetz@raq 4 ~]$ finger -s Jozef Login Name Tty Idle Login Time Office Phone jgoetz Jozef Goetz pts/1 Nov 30 21: 05 (64. 69. 147. 181) [jgoetz@raq 4 ~]$ finger -m jgoetz Login: jgoetz Name: Jozef Goetz Directory: /home/sites/site 7/users/jgoetz Shell: /bin/bash On since Wed Nov 30 21: 05 (PST) on pts/1 from 64. 69. 147. 184 No mail. No Plan. -m -s Jozef Goetz, 2014 Match ‘user_list’ to login names only Display output in a short format 59

Displaying Information About Users -m -s Jozef Goetz, 2014 Match ‘user_list’ to login names only Display output in a short format 60
![Displaying Information About Users // if the finger server is running [jgoetz]$ finger jgoetz@ulv. Displaying Information About Users // if the finger server is running [jgoetz]$ finger jgoetz@ulv.](https://present5.com/presentation/02eca4e533db7506d17e8b07e6af6810/image-61.jpg)
Displaying Information About Users // if the finger server is running [jgoetz]$ finger jgoetz@ulv. edu [ulv. edu] finger: connect: No route to host [jgoetz]$ jozef@ulv. edu Jozef Goetz, 2014 61

Remote Login. n The telnet protocol is designed to allow you to connect to a remote computer over a network telnet [options] [host[port]] Purpose: To connect to a remote system ‘host’ via a network; the ‘host’ can be specified by its name or IP address in dotted decimal notation Commonly used options/features: -a Attempt automatic login -l Specify a user for login usage: telnet [-l user] [-a] host-name [port] e. g. titan/bin > telnet -l jgoetz -a faculty. ulv. edu Trying 192. 231. 179. 91. . . Connected to FACULTY. ULV. EDU (192. 231. 179. 91). Escape character is '^]'. Password: Last login: Wed Nov 29 13: 00: 01 from cpe-66 -74 - … telnet help //or telnet --help // to get available cmds Jozef Goetz, 2014 62

Remote Login (contd. ) $ telnet upsun 29 Trying 192. 10. 89. . . Connected to upsun 29. egr. up. edu. Escape character is ‘^]’. UNIX(r) System V Release 4. 0 (upsun 29. egr. up. edu) login: sarwar Password: ***** Last login: Sat Dec 27 05: 37 from up You have mail. DISPLAY = (‘) TERM = (vt 100) $ Jozef Goetz, 2014 63
![64 Remote Login (contd. ) [jgoetz]$ telnet -? telnet: invalid option -- ? Usage: 64 Remote Login (contd. ) [jgoetz]$ telnet -? telnet: invalid option -- ? Usage:](https://present5.com/presentation/02eca4e533db7506d17e8b07e6af6810/image-64.jpg)
64 Remote Login (contd. ) [jgoetz]$ telnet -? telnet: invalid option -- ? Usage: telnet [-8] [-E] [-L] [-S tos] [-a] [-c] [-d] [-e char] [-l user][-n tracefile] [-b hostalias ][-r] [host-name [port]] Ctrl + D close the session Jozef Goetz, 2014

Remote Login (contd. ) # reverts to the telnet client – place in the foreground Jozef Goetz, 2014 65

Using Telnet to Invoke Other Well-known Services invokes a daytime service running at port 13 Jozef Goetz, 2014 66

The rlogin Command n The rlogin command allows you to log on to a host on your local network (or remote) rlogin [options] hosts Purpose: To connect to a remote LINUX or UNIX ‘host’ via a network ; the ‘host’ can be specified by its name or IP address in the dotted decimal notation Commonly used options/features: -ec Set the escape character to ‘c’( the default is ‘~’) -l user User ‘user’ as the login name on the remote host e. g. [jgoetz]$ rlogin -l jozefg ecs. fullerton. edu: Connection refused // it is not a local network slogin [options] hosts - secure version uses strong cryptography for transmitting data Jozef Goetz, 2014 67

The rlogin Command $ rlogin upsun -l perform Password: Last login: Mon Dec 18 12: 08: 12 from upsun 21. up. edu Sun. OS Release 4. 1. 3 (UPSUN_SERVER) #5: Mon Nov 14 17: 31: 44 PST 1994 DISPLAY 5 (upx 46: 0. 0) TERM 5 (vt 100) $ whoami perform $ hostname upsun. egr. up. edu $ -ec Set the escape character to ‘c’( the default is ‘~’) -l user User ‘user’ as the login name on the remote host Jozef Goetz, 2014 68
![Remote Command Execution rsh – remote shell rsh [options] host [command] Purpose: n n Remote Command Execution rsh – remote shell rsh [options] host [command] Purpose: n n](https://present5.com/presentation/02eca4e533db7506d17e8b07e6af6810/image-69.jpg)
Remote Command Execution rsh – remote shell rsh [options] host [command] Purpose: n n To execute a command on a remote machine , ‘host’, on the same network; the rlogin command is executed if no ‘command’ is specified Commonly used options/features: -l user Use ‘user’ as the login name on the remote host ssh [options] host [command] -secure version uses strong cryptography for transmitting data Jozef Goetz, 2014 69

70 Figure 14. 8 The semantics of the rsh upsun 29 ps command n. The Jozef Goetz, 2014 same network

Figure 14. 9 The semantics of the rsh upsun 29 sort students > sorted_students command students and sorted_students are files Jozef Goetz, 2014 71

Remote Command Execution Jozef Goetz, 2014 72

Remote Command Execution • the sort cmd takes input from the students file on the local machine, (upibm 7) and the output is sent to the sorted_students file on the local machine • input from local file students and store the sorted result in a sorted_students file on the remote machine When used without arguments, the rsh reverts to the rlogin command. nit is executed if no ‘arguments’ is specified n //to log on a different network on the Internet Jozef Goetz, 2014 73
![File Transfer ftp [options] [host] n Purpose: To transfer files from or to a File Transfer ftp [options] [host] n Purpose: To transfer files from or to a](https://present5.com/presentation/02eca4e533db7506d17e8b07e6af6810/image-74.jpg)
File Transfer ftp [options] [host] n Purpose: To transfer files from or to a remote ‘host’ Commonly used options/features -d Enable debugging -i Disable prompting during transfers of multiple files -v Show all remote responses Jozef Goetz, 2014 74

File Transfer titan/jozefg > ftp -v faculty. ulv. edu // -v Show all remote responses Connected to faculty. ulv. edu. 220 Pro. FTPD 1. 2. 9 Server (Pro. FTPD) [192. 231. 179. 91] 500 AUTH not understood KERBEROS_V 4 rejected as an authentication type Name (faculty. ulv. edu: jozefg): jgoetz 331 Password required for jgoetz. Password: 230 User jgoetz logged in. Remote system type is UNIX. Using binary mode to transfer files. ftp> ls -l 200 PORT command successful 150 Opening ASCII mode data connection for file list -rw-r--r-- 1 jgoetz site 7 123392 Nov 28 21: 01 Assig. doc -rwxrwxrwx 1 jgoetz site 7 13 Oct 31 07: 22 m drwxrwsr-x 4 jgoetz site 7 4096 Jun 1 2006 web 226 Transfer complete. ftp> Jozef Goetz, 2014 75

File Transfer Jozef Goetz, 2014 76

77 Jozef Goetz, 2014
![Remote Copy rcp[options] [host: ]sfile [host: ]dfile rcp[options] [host: ]sfile [host: ]dir Purpose: To Remote Copy rcp[options] [host: ]sfile [host: ]dfile rcp[options] [host: ]sfile [host: ]dir Purpose: To](https://present5.com/presentation/02eca4e533db7506d17e8b07e6af6810/image-78.jpg)
Remote Copy rcp[options] [host: ]sfile [host: ]dfile rcp[options] [host: ]sfile [host: ]dir Purpose: To copy ‘sfile’ to ‘dfile’ source file – sfile destination file - dfile Commonly used options/features -p n -r Jozef Goetz, 2014 Attempt to preserve file modify and access times; without this option the command uses the current value of unmask to create file permissions Recursively copy files at ‘sfiles’ to ‘dir’ 78

Remote Copy (contd. ) $ rcp ~/myweb/*. html upsun 29: webmirror $ rcp ~/unixbook/Chapter[1 -9]. doc upsun 29: unixbook. backup $ rcp upsun 29: ece 446/projects/*. [c, C] ~/swprojects. backup $ rcp -rp www 1: * www 2: $ -p Attempt to preserve file modify and access times; -r Recursively copy files at ‘sfiles’ to ‘dir’ Secure version of the rcp command $ scp prog 4. c upsun 29: ~/courses/cs 213/programs/ $ scp -r upsun 21. egr. up. edu: courses. $ scp -rp www 1: * www 2: $ Jozef Goetz, 2014 79

Communication Commands n Communication Commands: n $ who 80 n // check the user name to whom you want to talk $ mesg [y|n] // permit execution $ write user [tty] - works $ talk user [tty] - shows 2 sections of the screen: sender and receiver $ biff [y|n] // notification on/off Jozef Goetz, 2014
![Interactive Chat write user [tty] talk user [tty] //-> works Purpose: to initiate interactive Interactive Chat write user [tty] talk user [tty] //-> works Purpose: to initiate interactive](https://present5.com/presentation/02eca4e533db7506d17e8b07e6af6810/image-81.jpg)
Interactive Chat write user [tty] talk user [tty] //-> works Purpose: to initiate interactive chat with ‘use’ who is logged in a ‘tty’ terminal $ talk bob [Waiting for your party to respond] Message from Talk_Daemon@upibm 7. egr. up. edu at 13: 36. . . talk: connection requested by sarwar@upibm 7. egr. up. edu. talk: respond with: talk sarwar@upibm 7. egr. up. edu $ talk sarwar@upibm 7 Jozef Goetz, 2014 81 on

82 Utility Commands (Contd) Jozef Goetz, 2014

Tracing the Route from One Site to Another Site traceroute www. yahoo. com #some administrators disable this cmd for security Jozef Goetz, 2014 83

84 Important Internet Organizations Jozef Goetz, 2014

Web Resources Jozef Goetz, 2014 85

Web Resources Jozef Goetz, 2014 86

Request For Comments (RFCs) – omit it n n Jozef Goetz, 2014 The TCP/IP standards are described in a series of documents, known as the Request for Comments RFCs are first published as the Internet Drafts and are made available to all Internet users for reviewer and feedback by placing them in known RFC repositories After the review process is complete, a draft can become a standard Some RFCs are for information only others are experimental 87
02eca4e533db7506d17e8b07e6af6810.ppt