 1
1
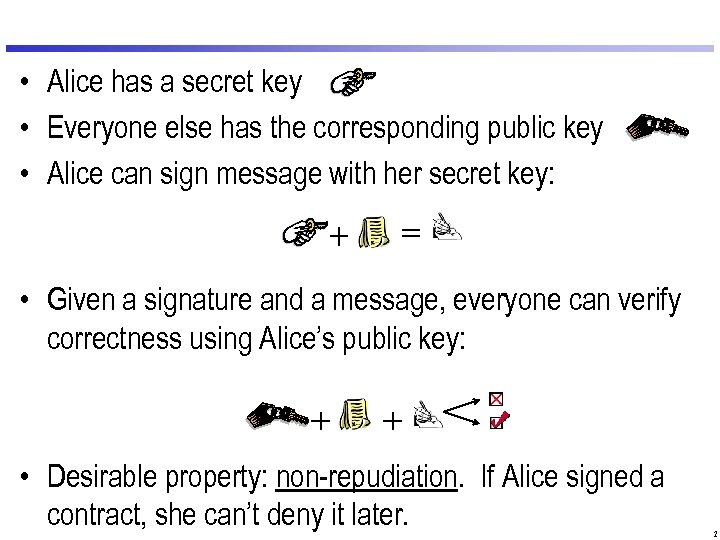 • Alice has a secret key • Everyone else has the corresponding public key • Alice can sign message with her secret key: • Given a signature and a message, everyone can verify correctness using Alice’s public key: • Desirable property: non-repudiation. If Alice signed a contract, she can’t deny it later. 2
• Alice has a secret key • Everyone else has the corresponding public key • Alice can sign message with her secret key: • Given a signature and a message, everyone can verify correctness using Alice’s public key: • Desirable property: non-repudiation. If Alice signed a contract, she can’t deny it later. 2
 3
3
 • Can’t tell when a signature was really generated – Not even if you include current time into the document! 4
• Can’t tell when a signature was really generated – Not even if you include current time into the document! 4
 5
5
 6
6
 7
7
 8
8
 9
9
 10
10
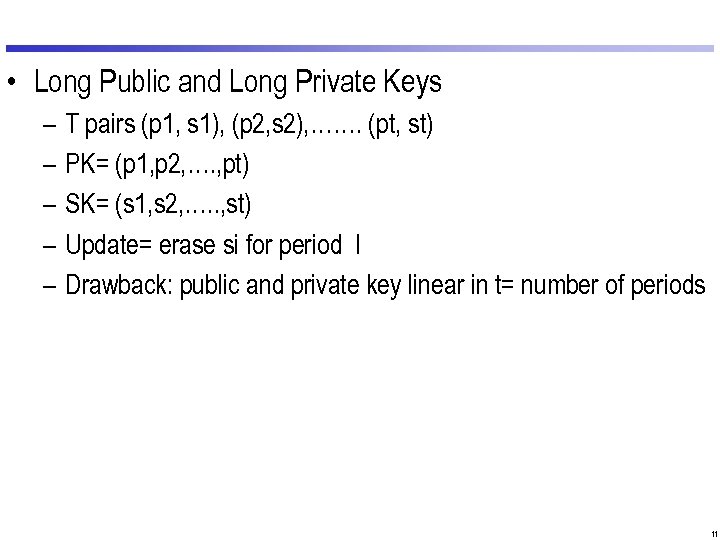 • Long Public and Long Private Keys – – – T pairs (p 1, s 1), (p 2, s 2), ……. (pt, st) PK= (p 1, p 2, …. , pt) SK= (s 1, s 2, …. . , st) Update= erase si for period I Drawback: public and private key linear in t= number of periods 11
• Long Public and Long Private Keys – – – T pairs (p 1, s 1), (p 2, s 2), ……. (pt, st) PK= (p 1, p 2, …. , pt) SK= (s 1, s 2, …. . , st) Update= erase si for period I Drawback: public and private key linear in t= number of periods 11
 • • • T pairs as above and an additonal pair (p, s) Sig(j)=SIG( j || pj) with key s, j =1, …, t [A “certificate”] Public key now = p (only) Secret key = (sj, SIG(j)) j=1, . . , t [Still linear] The public key p is like a CA key and a signature will include the period, the certificate, the message, signature on the message with period’s secret key 12
• • • T pairs as above and an additonal pair (p, s) Sig(j)=SIG( j || pj) with key s, j =1, …, t [A “certificate”] Public key now = p (only) Secret key = (sj, SIG(j)) j=1, . . , t [Still linear] The public key p is like a CA key and a signature will include the period, the certificate, the message, signature on the message with period’s secret key 12
 • • Have (p, s) In period j get (pj, sj) and Let Cert(j)= sig_s[j-1] (j || pj) A signature is the entire certificate chain + signature, it is of the form: (j, sig_sj(m), p 1, Cert(1), …pj, Cert(j)) • Think about it as a tree of degree one and length t for t periods • (signer memory still linear in t) 13
• • Have (p, s) In period j get (pj, sj) and Let Cert(j)= sig_s[j-1] (j || pj) A signature is the entire certificate chain + signature, it is of the form: (j, sig_sj(m), p 1, Cert(1), …pj, Cert(j)) • Think about it as a tree of degree one and length t for t periods • (signer memory still linear in t) 13
![Have future keys derived from a forward secure pseudorandom generator [Kra] • Pseudorandom generators Have future keys derived from a forward secure pseudorandom generator [Kra] • Pseudorandom generators](https://present5.com/presentation/dc20e501df2a9b903922ba400e7e30db/image-14.jpg) Have future keys derived from a forward secure pseudorandom generator [Kra] • Pseudorandom generators which are forward secure are easy: replace the seed with an iteration of the function. 14
Have future keys derived from a forward secure pseudorandom generator [Kra] • Pseudorandom generators which are forward secure are easy: replace the seed with an iteration of the function. 14
 15
15
 16
16
 17
17