b46a64ea19e0de98c742d49db6eaa1c3.ppt
- Количество слайдов: 13
 1 Adaptive Intrusion Detection and Mitigation Systems for Wi. MAX Networks Yan Chen Northwestern Lab for Internet and Security Technology (LIST) Dept. of Computer Science Northwestern University http: //list. cs. northwestern. edu Motorola Liaisons Gregory W. Cox, Z. Judy Fu, Philip R. Roberts Motorola Labs
1 Adaptive Intrusion Detection and Mitigation Systems for Wi. MAX Networks Yan Chen Northwestern Lab for Internet and Security Technology (LIST) Dept. of Computer Science Northwestern University http: //list. cs. northwestern. edu Motorola Liaisons Gregory W. Cox, Z. Judy Fu, Philip R. Roberts Motorola Labs
 Battling Hackers is a Growth Industry! 2 --Wall Street Journal (11/10/2004) • The past decade has seen an explosion in the concern for the security of information • Denial of service (Do. S) attacks – Cost $1. 2 billion in 2000 • Viruses and worms faster and more powerful – Cause over $28 billion in economic losses in 2003, growing to over $75 billion in economic losses by 2007.
Battling Hackers is a Growth Industry! 2 --Wall Street Journal (11/10/2004) • The past decade has seen an explosion in the concern for the security of information • Denial of service (Do. S) attacks – Cost $1. 2 billion in 2000 • Viruses and worms faster and more powerful – Cause over $28 billion in economic losses in 2003, growing to over $75 billion in economic losses by 2007.
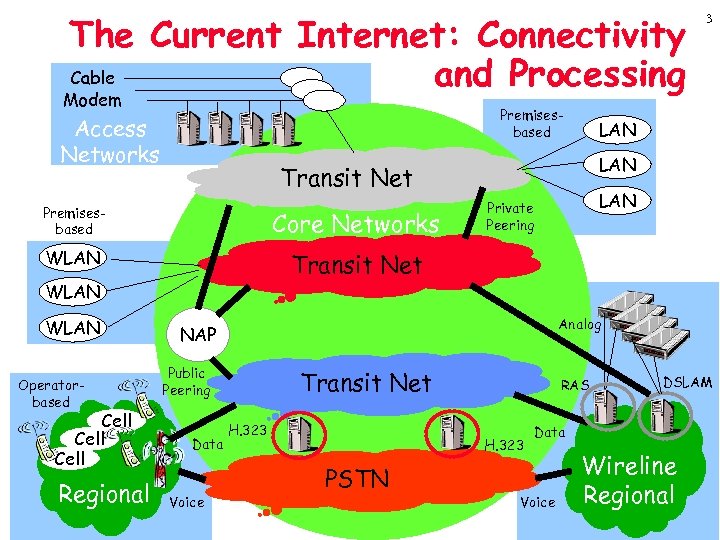 The Current Internet: Connectivity Cable and Processing Modem Premisesbased Access Networks LAN Transit Net Premisesbased Core Networks WLAN 3 LAN Private Peering Transit Net WLAN Operatorbased Cell Regional Analog NAP Public Peering Data Voice Transit Net H. 323 RAS H. 323 PSTN DSLAM Data Voice Wireline Regional
The Current Internet: Connectivity Cable and Processing Modem Premisesbased Access Networks LAN Transit Net Premisesbased Core Networks WLAN 3 LAN Private Peering Transit Net WLAN Operatorbased Cell Regional Analog NAP Public Peering Data Voice Transit Net H. 323 RAS H. 323 PSTN DSLAM Data Voice Wireline Regional
 Motivation 4 • Viruses/worms moving into the wireless world … – 6 new viruses, including Cabir and Skulls, with 30 variants targeting mobile devices • IEEE 802. 16 Wi. MAX networks emerging – Predicted multi-billion dollar industry – No existing research/product tailored towards 802. 16 anomaly/intrusion detection and mitigation • 802. 16 IDS development can potentially lead to critical gain in market share – All major WLAN vendors integrated IDS into products • Strategically important to lead in Wi. MAX product portfolio with security & trouble shooting capability – Simply buy off-the-shelf IDSes blind to their limitations
Motivation 4 • Viruses/worms moving into the wireless world … – 6 new viruses, including Cabir and Skulls, with 30 variants targeting mobile devices • IEEE 802. 16 Wi. MAX networks emerging – Predicted multi-billion dollar industry – No existing research/product tailored towards 802. 16 anomaly/intrusion detection and mitigation • 802. 16 IDS development can potentially lead to critical gain in market share – All major WLAN vendors integrated IDS into products • Strategically important to lead in Wi. MAX product portfolio with security & trouble shooting capability – Simply buy off-the-shelf IDSes blind to their limitations
 Existing Intrusion Detection Systems (IDS) Insufficient • Mostly host-based and not scalable to high-speed networks – Slammer worm infected 75, 000 machines in < 10 mins – Host-based schemes inefficient and user dependent » Have to install IDS on all user machines ! • Mostly signature-based – Cannot recognize unknown anomalies/intrusions – New viruses/worms, polymorphism 5
Existing Intrusion Detection Systems (IDS) Insufficient • Mostly host-based and not scalable to high-speed networks – Slammer worm infected 75, 000 machines in < 10 mins – Host-based schemes inefficient and user dependent » Have to install IDS on all user machines ! • Mostly signature-based – Cannot recognize unknown anomalies/intrusions – New viruses/worms, polymorphism 5
 Current IDS Insufficient (II) • Statistical detection – Hard to adapt to traffic pattern changes – Unscalable for flow-level detection » IDS vulnerable to Do. S attacks » Wi. MAX, up to 134 Mbps, 10 min traffic may take 4 GB memory – Overall traffic based: inaccurate, high false positives » Existing high-speed IDS here • Cannot differentiate malicious events with unintentional anomalies – Anomalies can be caused by network element faults – E. g. , signal interference of wireless network 6
Current IDS Insufficient (II) • Statistical detection – Hard to adapt to traffic pattern changes – Unscalable for flow-level detection » IDS vulnerable to Do. S attacks » Wi. MAX, up to 134 Mbps, 10 min traffic may take 4 GB memory – Overall traffic based: inaccurate, high false positives » Existing high-speed IDS here • Cannot differentiate malicious events with unintentional anomalies – Anomalies can be caused by network element faults – E. g. , signal interference of wireless network 6
 Adaptive Intrusion Detection System for Wireless Networks (WAIDM) • Online traffic recording and analysis for highspeed Wi. MAX networks – Leverage sketches for data streaming computation – Record millions of flows (GB traffic) in a few Kilobytes • Online flow-level intrusion detection & mitigation – Leverage statistical learning theory (SLT) adaptively learn the traffic pattern changes » Successfully detected flow-level SYN flooding and various port scans with NU, LBL and Fermi network traces – Flow-level mitigation of attacks – Combine with 802. 16 specific signature-based detection » Automatic polymorphic worm signature generation 7
Adaptive Intrusion Detection System for Wireless Networks (WAIDM) • Online traffic recording and analysis for highspeed Wi. MAX networks – Leverage sketches for data streaming computation – Record millions of flows (GB traffic) in a few Kilobytes • Online flow-level intrusion detection & mitigation – Leverage statistical learning theory (SLT) adaptively learn the traffic pattern changes » Successfully detected flow-level SYN flooding and various port scans with NU, LBL and Fermi network traces – Flow-level mitigation of attacks – Combine with 802. 16 specific signature-based detection » Automatic polymorphic worm signature generation 7
 WAIDM Systems (II) • Anomaly diagnosis for false positive reduction – Use statistics from MIB of base station to understand the wireless network status » E. g. , busy vs. idle wireless networks, with different level of interferences, etc. » Successfully experimented with 802. 11 networks – Root cause analysis for diagnose link failures, routing misconfiguration, etc. – Useful for managing and trouble-shooting the Wi. MAX networks 8
WAIDM Systems (II) • Anomaly diagnosis for false positive reduction – Use statistics from MIB of base station to understand the wireless network status » E. g. , busy vs. idle wireless networks, with different level of interferences, etc. » Successfully experimented with 802. 11 networks – Root cause analysis for diagnose link failures, routing misconfiguration, etc. – Useful for managing and trouble-shooting the Wi. MAX networks 8
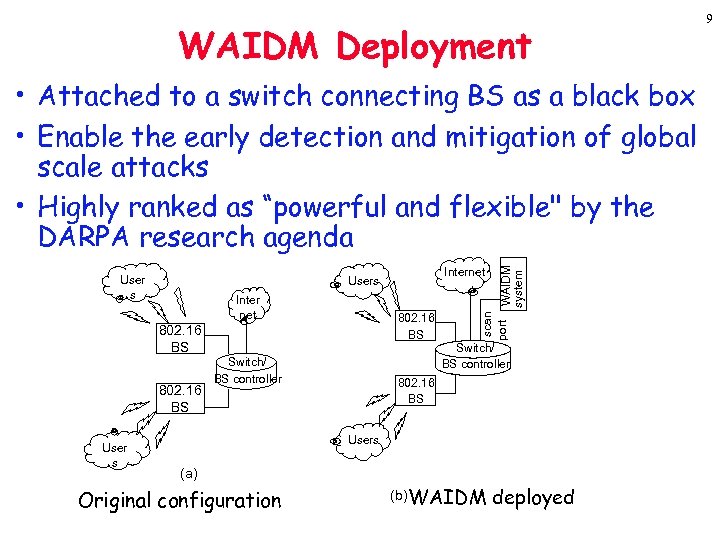 WAIDM Deployment User s 802. 16 BS User s Internet Users Inter net Switch/ BS controller scan port WAIDM system • Attached to a switch connecting BS as a black box • Enable the early detection and mitigation of global scale attacks • Highly ranked as “powerful and flexible" by the DARPA research agenda Switch/ BS controller 802. 16 BS Users (a) Original configuration (b) WAIDM deployed 9
WAIDM Deployment User s 802. 16 BS User s Internet Users Inter net Switch/ BS controller scan port WAIDM system • Attached to a switch connecting BS as a black box • Enable the early detection and mitigation of global scale attacks • Highly ranked as “powerful and flexible" by the DARPA research agenda Switch/ BS controller 802. 16 BS Users (a) Original configuration (b) WAIDM deployed 9
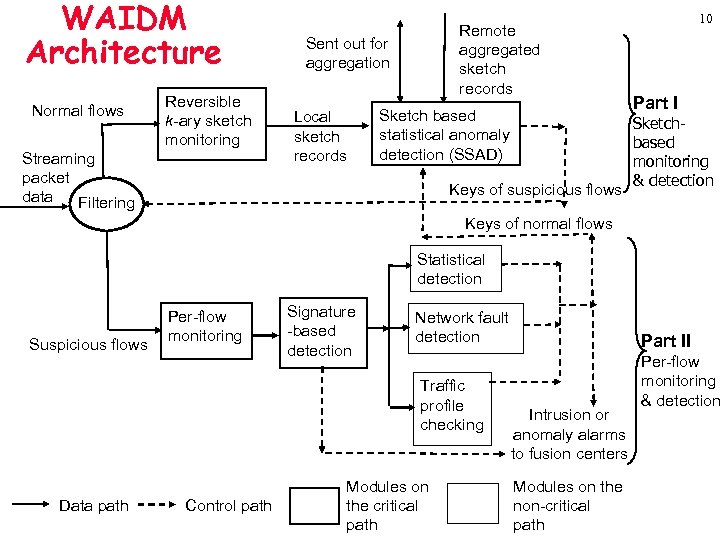 WAIDM Architecture Normal flows Reversible k-ary sketch monitoring Streaming packet data Filtering Remote aggregated sketch records Sent out for aggregation Local sketch records Sketch based statistical anomaly detection (SSAD) Keys of suspicious flows 10 Part I Sketchbased monitoring & detection Keys of normal flows Statistical detection Suspicious flows Per-flow monitoring Signature -based detection Network fault detection Traffic profile checking Data path Control path Modules on the critical path Part II Intrusion or anomaly alarms to fusion centers Modules on the non-critical path Per-flow monitoring & detection
WAIDM Architecture Normal flows Reversible k-ary sketch monitoring Streaming packet data Filtering Remote aggregated sketch records Sent out for aggregation Local sketch records Sketch based statistical anomaly detection (SSAD) Keys of suspicious flows 10 Part I Sketchbased monitoring & detection Keys of normal flows Statistical detection Suspicious flows Per-flow monitoring Signature -based detection Network fault detection Traffic profile checking Data path Control path Modules on the critical path Part II Intrusion or anomaly alarms to fusion centers Modules on the non-critical path Per-flow monitoring & detection
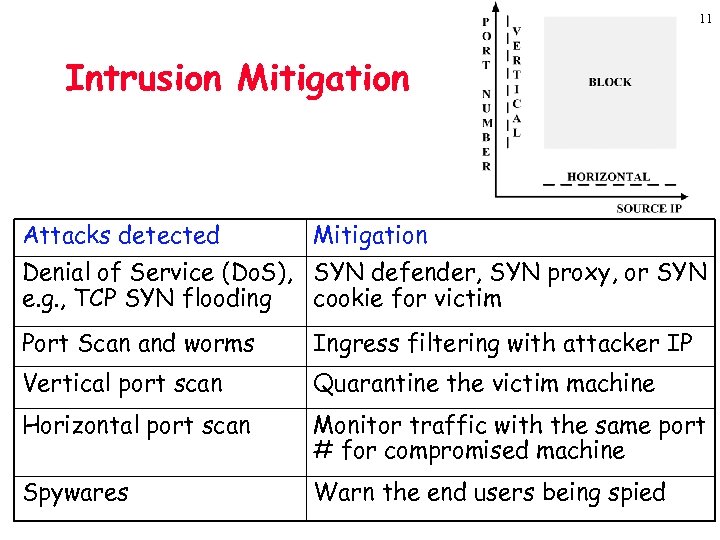 11 Intrusion Mitigation Attacks detected Mitigation Denial of Service (Do. S), SYN defender, SYN proxy, or SYN e. g. , TCP SYN flooding cookie for victim Port Scan and worms Ingress filtering with attacker IP Vertical port scan Quarantine the victim machine Horizontal port scan Monitor traffic with the same port # for compromised machine Spywares Warn the end users being spied
11 Intrusion Mitigation Attacks detected Mitigation Denial of Service (Do. S), SYN defender, SYN proxy, or SYN e. g. , TCP SYN flooding cookie for victim Port Scan and worms Ingress filtering with attacker IP Vertical port scan Quarantine the victim machine Horizontal port scan Monitor traffic with the same port # for compromised machine Spywares Warn the end users being spied
 Evaluation of Sketch-based Detection 12 • Evaluated with NU traces (536 M flows, 3. 5 TB traffic) • Scalable and efficient – For the worst case traffic, all 40 byte packets: » 16 Gbps on a single FPGA board » 526 Mbps on a Pentium-IV 2. 4 GHz PC – Only less than 10 MB memory used • Accurate – 19 SYN flooding, 1784 horizontal scans and 29 vertical scans detected in one-day NU traces – Validation » All flooding and vertical scan, and top 10 and bottom 10 for horizontal scans » Both well-known and new worms found (new confirmed in DShield) • Patent filed
Evaluation of Sketch-based Detection 12 • Evaluated with NU traces (536 M flows, 3. 5 TB traffic) • Scalable and efficient – For the worst case traffic, all 40 byte packets: » 16 Gbps on a single FPGA board » 526 Mbps on a Pentium-IV 2. 4 GHz PC – Only less than 10 MB memory used • Accurate – 19 SYN flooding, 1784 horizontal scans and 29 vertical scans detected in one-day NU traces – Validation » All flooding and vertical scan, and top 10 and bottom 10 for horizontal scans » Both well-known and new worms found (new confirmed in DShield) • Patent filed
 Research methodology Combination of theory, synthetic/real trace driven simulation, and real-world implementation and deployment 13
Research methodology Combination of theory, synthetic/real trace driven simulation, and real-world implementation and deployment 13


