cb7f314a69e83d005acb46273f20d7ad.ppt
- Количество слайдов: 114
 1
1
 2
2
 Use of Computer Forensics
Use of Computer Forensics
 Types of Computer Abuse
Types of Computer Abuse
 Accountants Role in Computer Forensics 5
Accountants Role in Computer Forensics 5
 Investigative Options 6
Investigative Options 6
 7
7
 8
8
 9
9
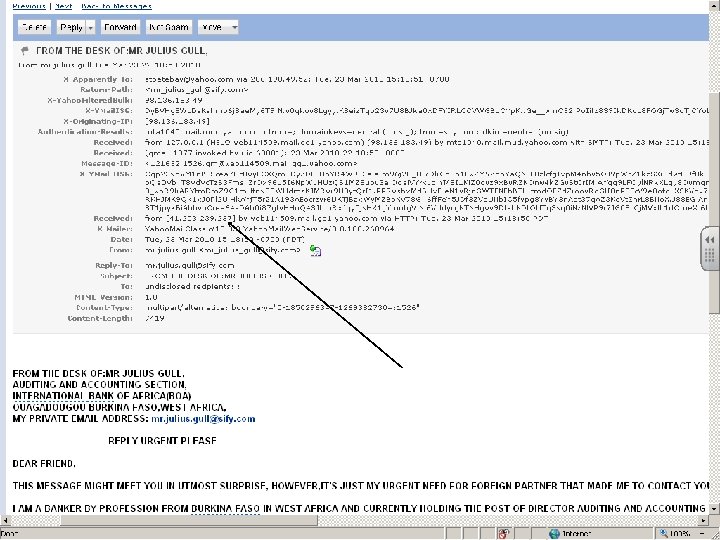
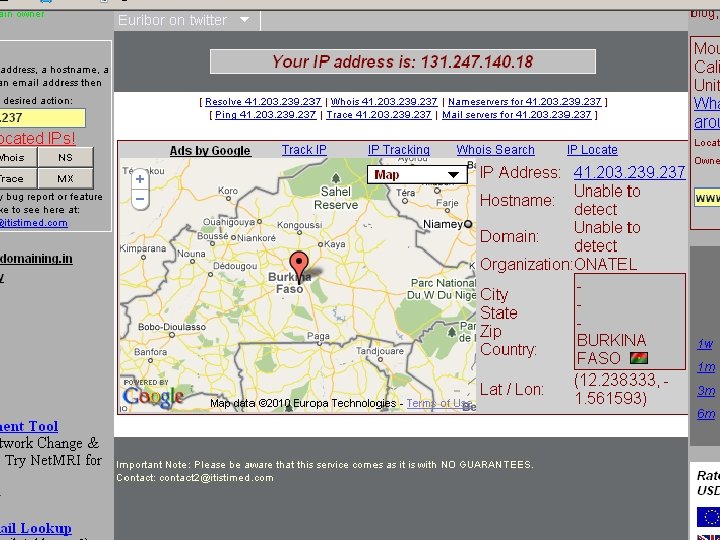
 Cyber. Crime
Cyber. Crime
 Types of Computer Crime
Types of Computer Crime
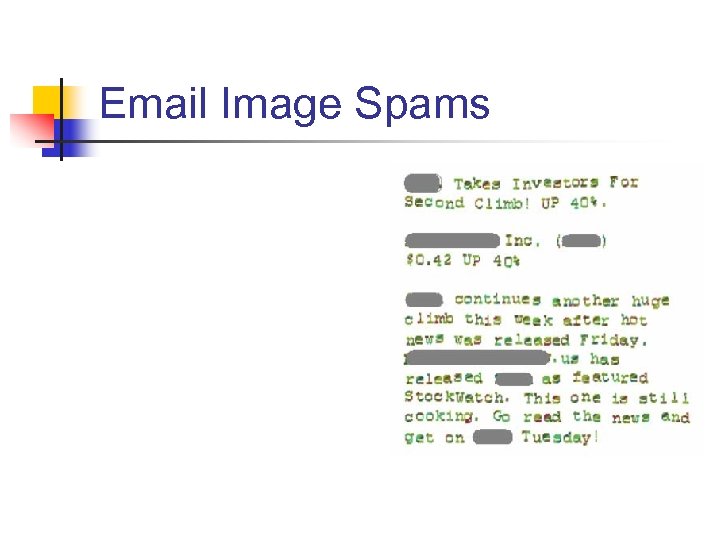 Email Image Spams
Email Image Spams
 Cyberstalking Kay Scarpetta
Cyberstalking Kay Scarpetta
 The Italian Job
The Italian Job

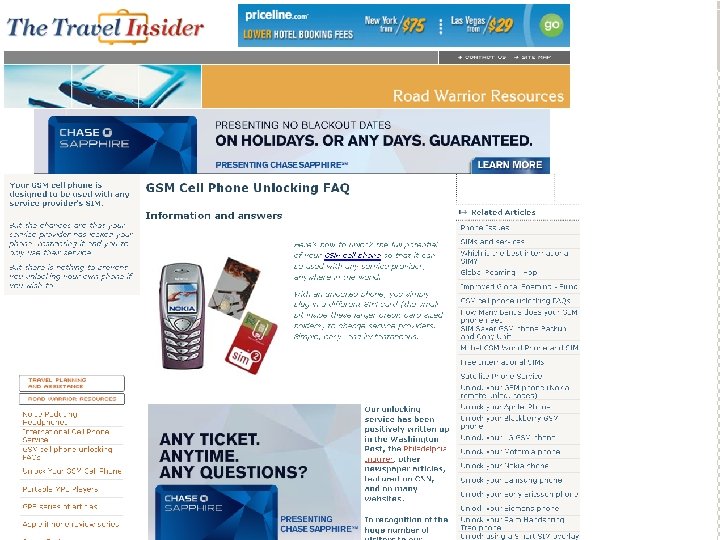
 Cell Phone Evidence 101
Cell Phone Evidence 101
 Cell Phone Seizures
Cell Phone Seizures

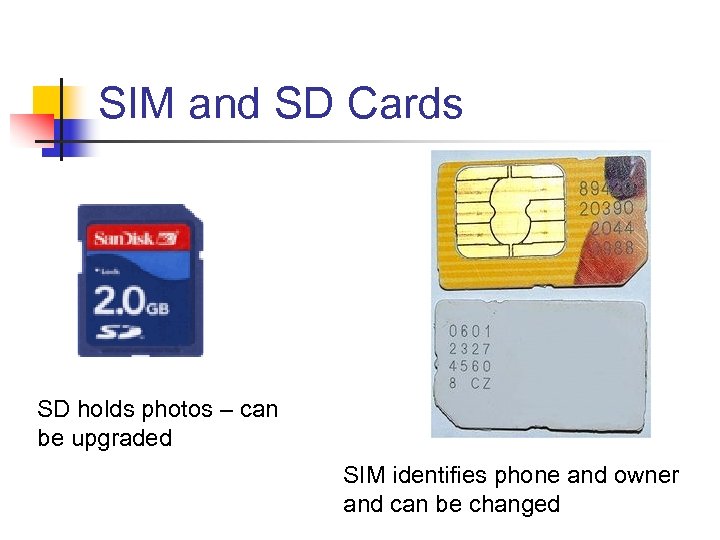 SIM and SD Cards SD holds photos – can be upgraded SIM identifies phone and owner and can be changed
SIM and SD Cards SD holds photos – can be upgraded SIM identifies phone and owner and can be changed
 Blackberry and i. Phone Remote Protection 21
Blackberry and i. Phone Remote Protection 21
 22
22
 Tools of the Trade 23
Tools of the Trade 23
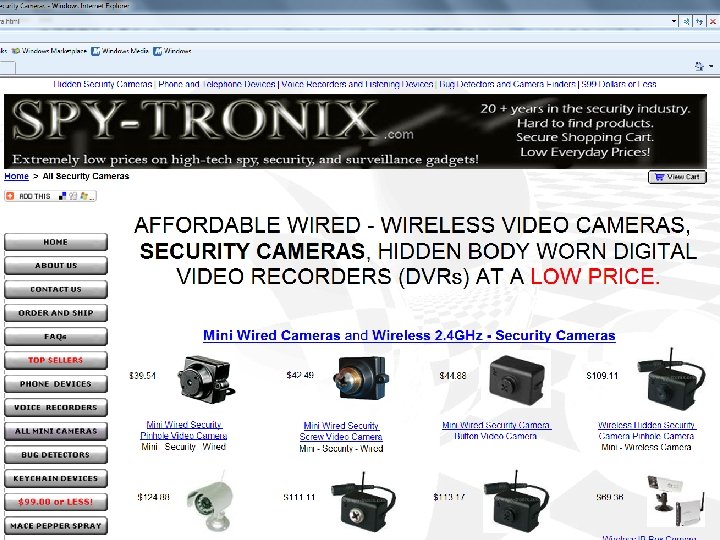
 Surveillance Tools
Surveillance Tools
 Surveillance Tools
Surveillance Tools
 Surveillance Tools
Surveillance Tools
 Anti-Surveillance Tools
Anti-Surveillance Tools
 Private Eye and Chameleon 29
Private Eye and Chameleon 29
 30
30
 31
31
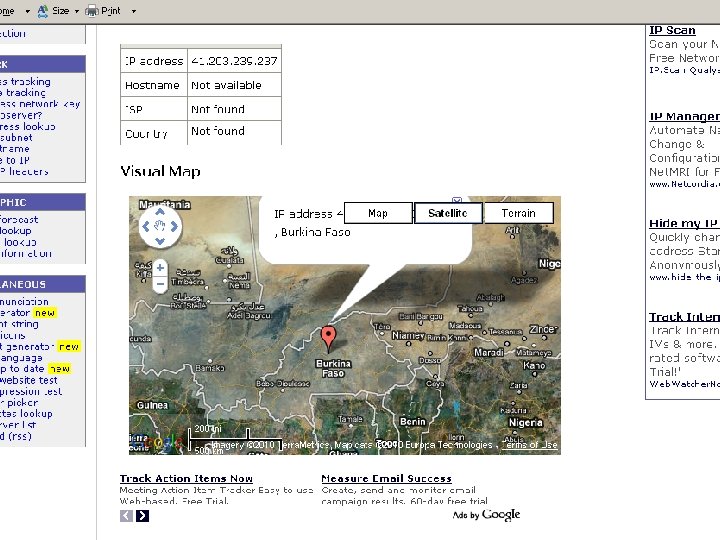 32
32
 Keyword Search and E-Discovery 33
Keyword Search and E-Discovery 33
 34
34
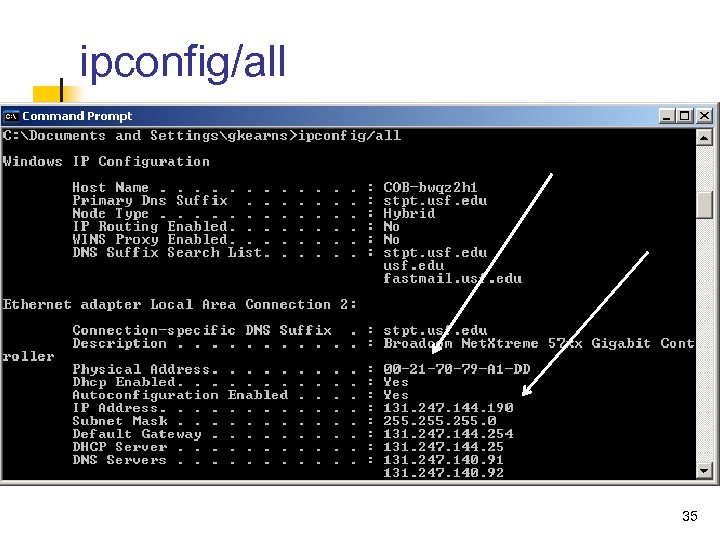 ipconfig/all 35
ipconfig/all 35
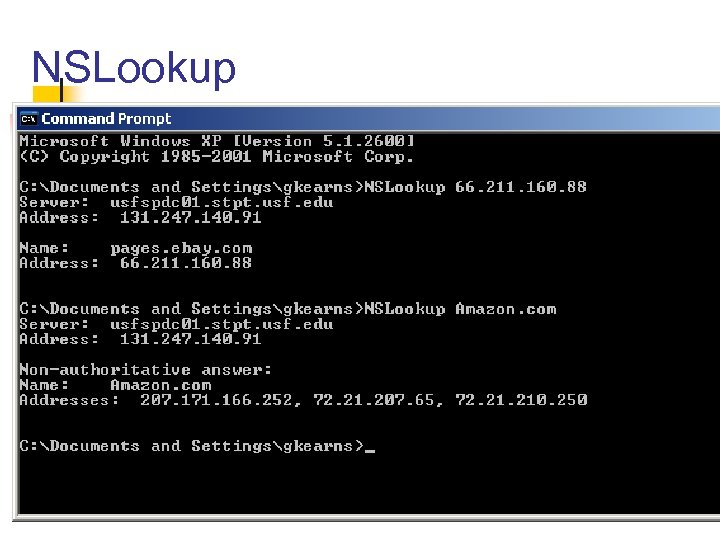 NSLookup 36
NSLookup 36
 Sedona Conference and ESI Framework 37
Sedona Conference and ESI Framework 37
 38
38
 ESI Retention Policy 39
ESI Retention Policy 39
 E-Mail Retention Policy
E-Mail Retention Policy
 Encryption 41
Encryption 41
 Encryption
Encryption
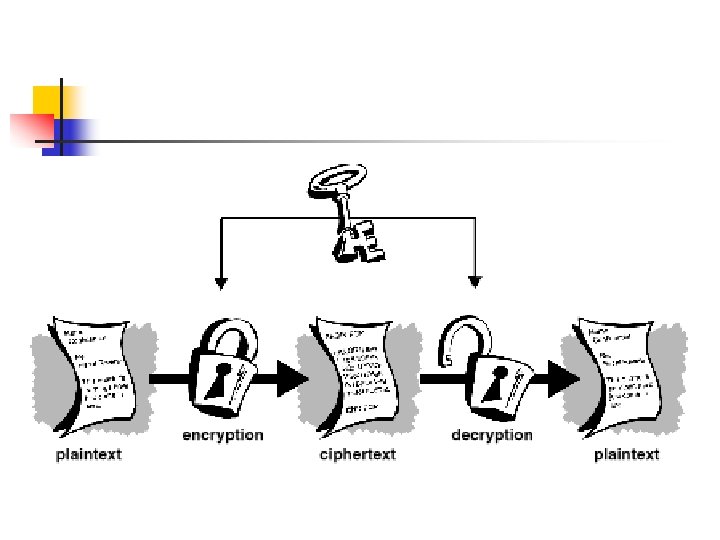
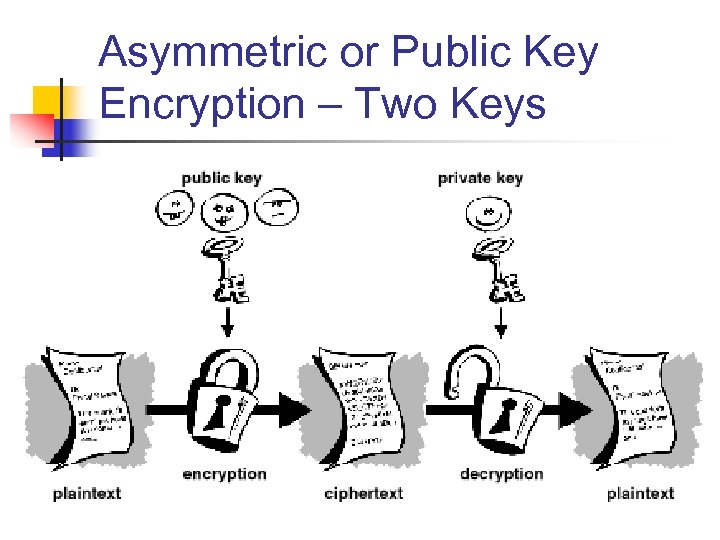 Asymmetric or Public Key Encryption – Two Keys
Asymmetric or Public Key Encryption – Two Keys
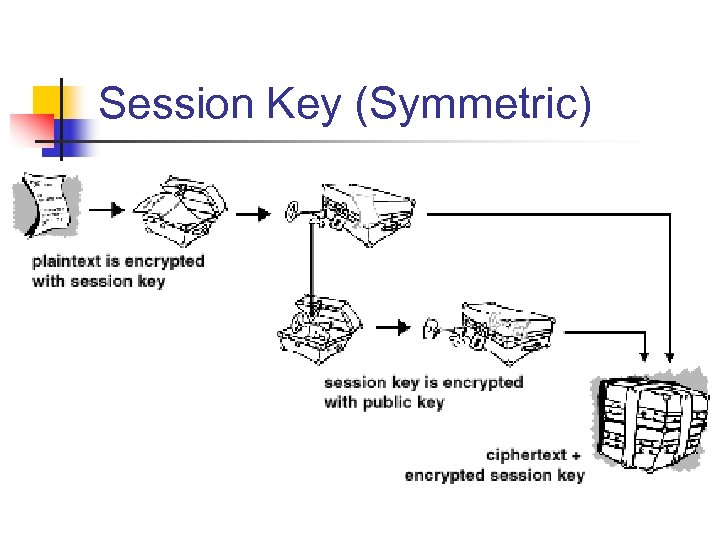 Session Key (Symmetric)
Session Key (Symmetric)
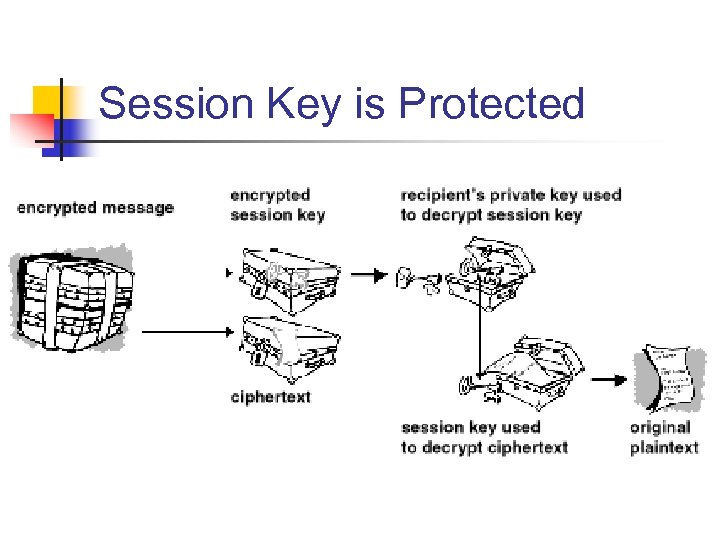 Session Key is Protected
Session Key is Protected
 Data in Transit and at Rest
Data in Transit and at Rest
 True. Crypt 49
True. Crypt 49
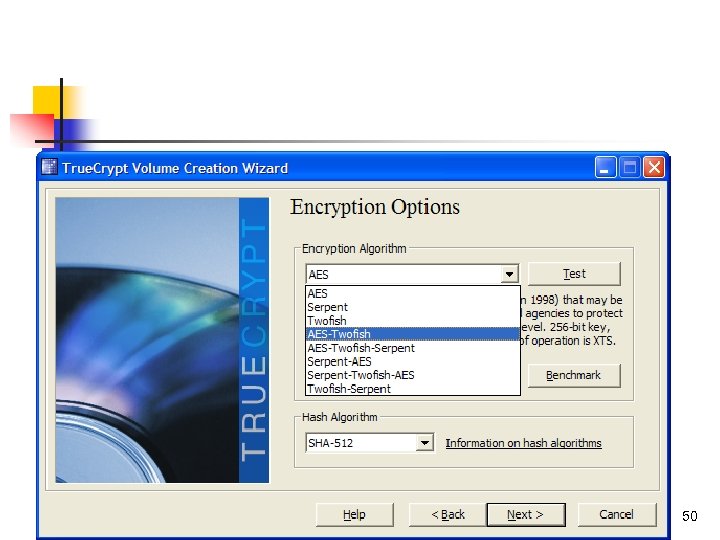 50
50
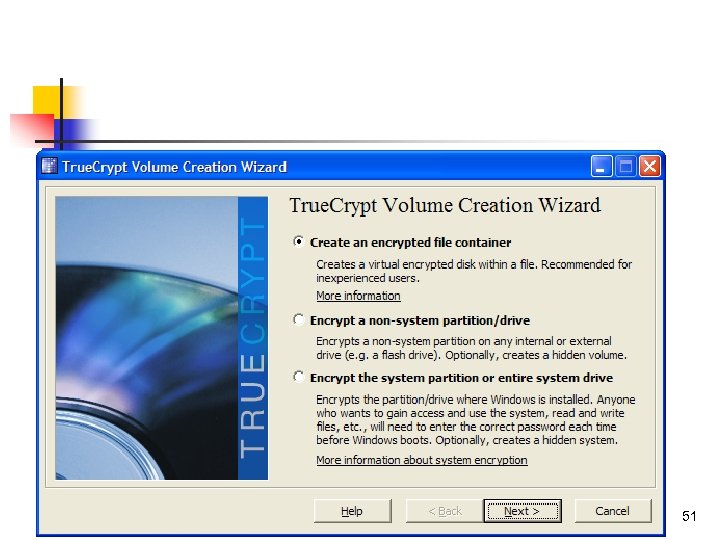 51
51
 Cost of Poor Retention Policy 52
Cost of Poor Retention Policy 52
 Redacted E-mail and Privacy 53
Redacted E-mail and Privacy 53
 IT Technologies Important to Accountants 54
IT Technologies Important to Accountants 54
 55
55
 56
56
 AICPA Top 10 Technology Initiatives 57
AICPA Top 10 Technology Initiatives 57

 Federal Rules of Evidence and Digital Data
Federal Rules of Evidence and Digital Data
 Reinterpretation of FRE
Reinterpretation of FRE
 Daubert Standards 61
Daubert Standards 61
 New Federal Rules of Civil Procedure 62
New Federal Rules of Civil Procedure 62
 Audit Command Language ACL 63
Audit Command Language ACL 63
 64
64
 65 65
65 65
 66
66
 67 67
67 67
 Cleansing Data
Cleansing Data


 71 71
71 71
 72 72
72 72
 73 73
73 73
 74 74
74 74
 75 75
75 75
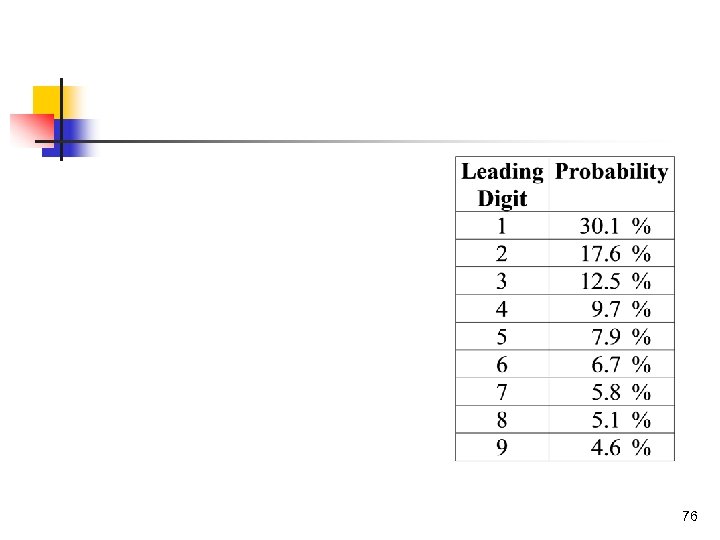 76
76
 Small Business Owner Example
Small Business Owner Example
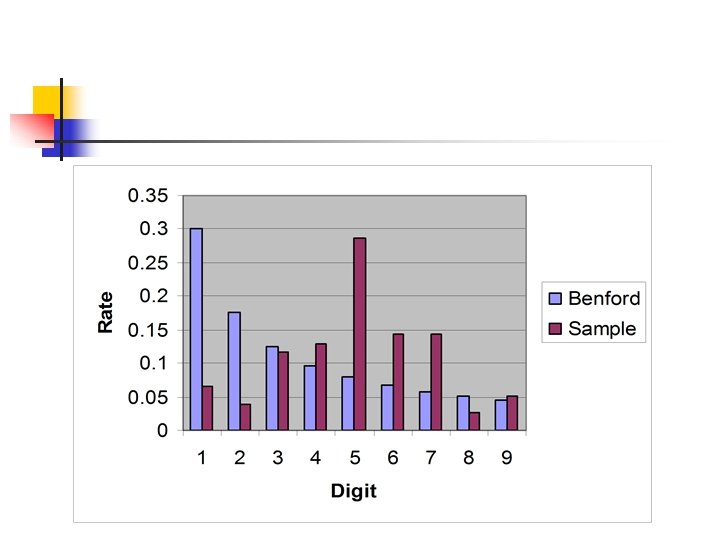
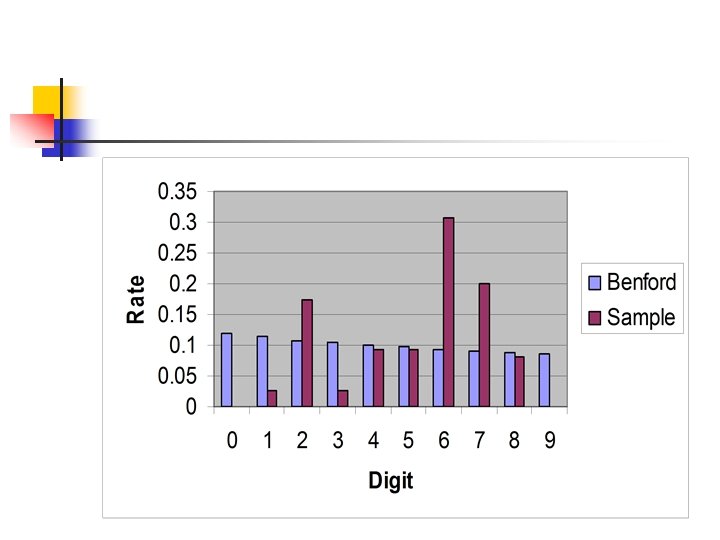



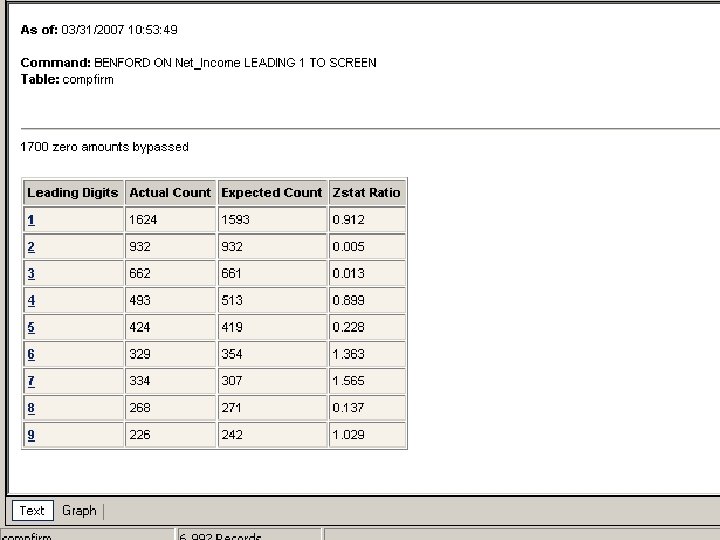 83 83
83 83

 85
85
 86
86
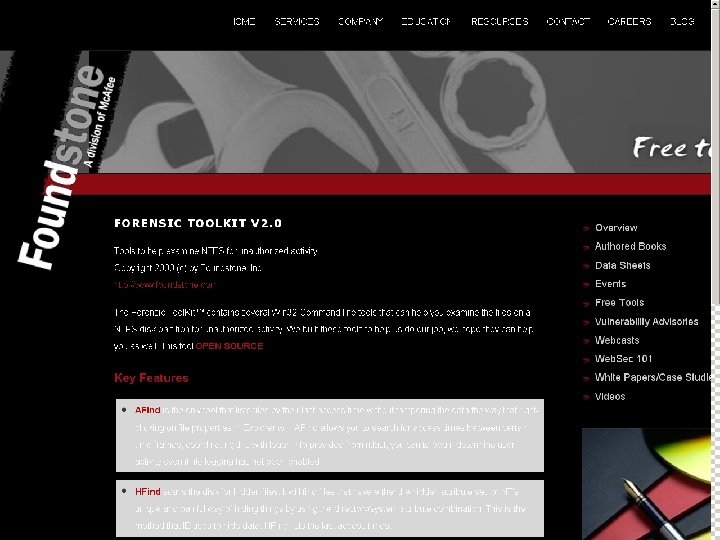 87
87
 Rainbow Tables www. accessdata. com Rainbow Tables are precomputed, brute-force attacks. A brute-force attack is an attempt to recover a cryptographic key or password by trying every possible combination until the correct one is found. With a Rainbow Table, you can decrypt 40 bit encrypted files in seconds or minutes rather than days or weeks.
Rainbow Tables www. accessdata. com Rainbow Tables are precomputed, brute-force attacks. A brute-force attack is an attempt to recover a cryptographic key or password by trying every possible combination until the correct one is found. With a Rainbow Table, you can decrypt 40 bit encrypted files in seconds or minutes rather than days or weeks.
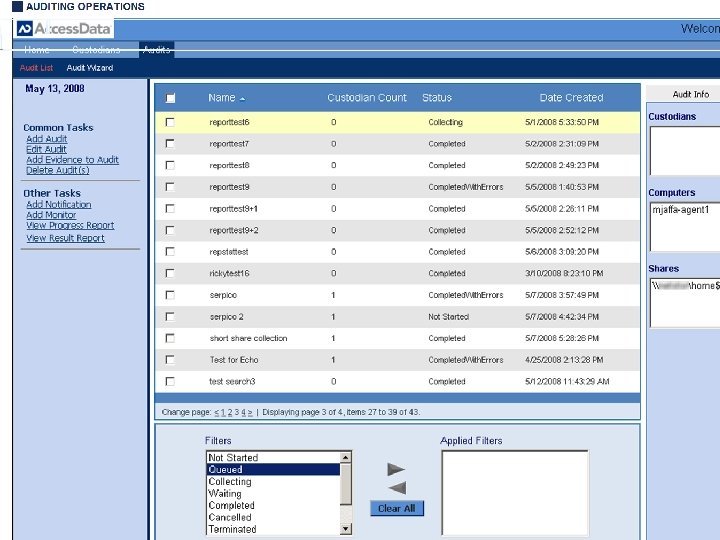
 Beware the Unmanaged IM and Email 90
Beware the Unmanaged IM and Email 90
 Beware the Unmanaged IM and Email Over 10, 000 U. S. laws and regulations apply to Instant Messaging and Email Retention!
Beware the Unmanaged IM and Email Over 10, 000 U. S. laws and regulations apply to Instant Messaging and Email Retention!
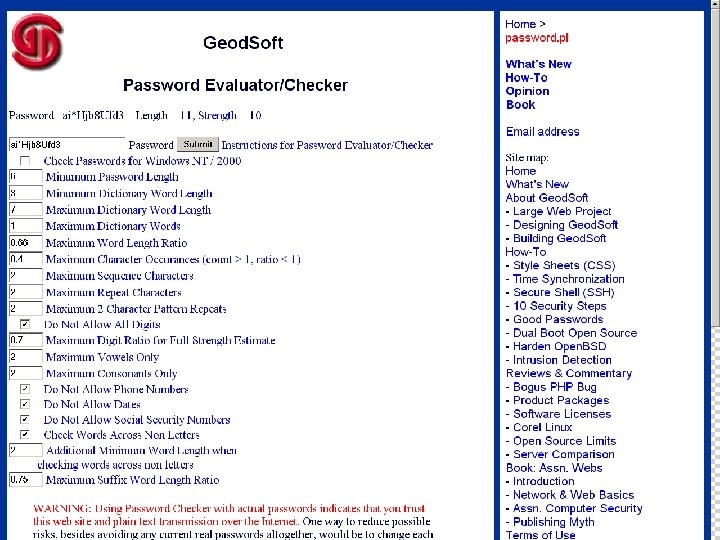 92
92
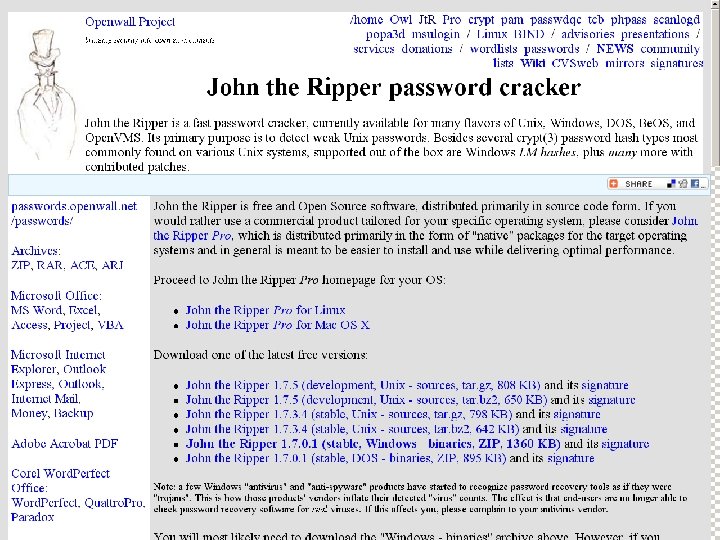 93
93
 94
94
 www. crackpassword. com 95
www. crackpassword. com 95
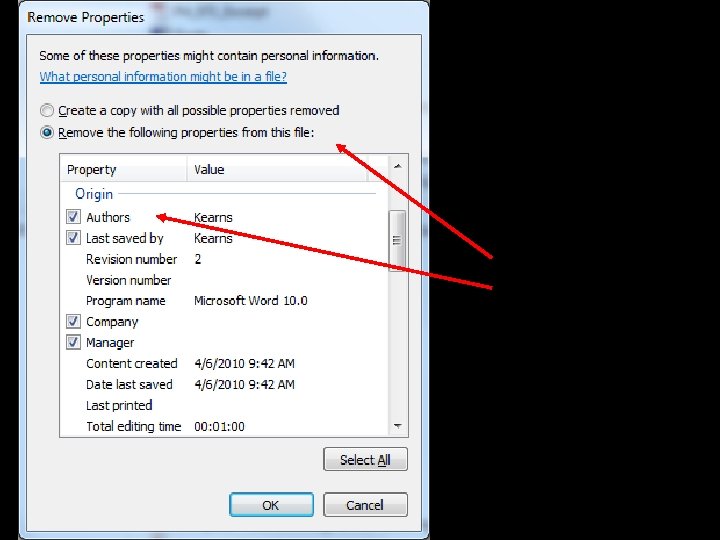
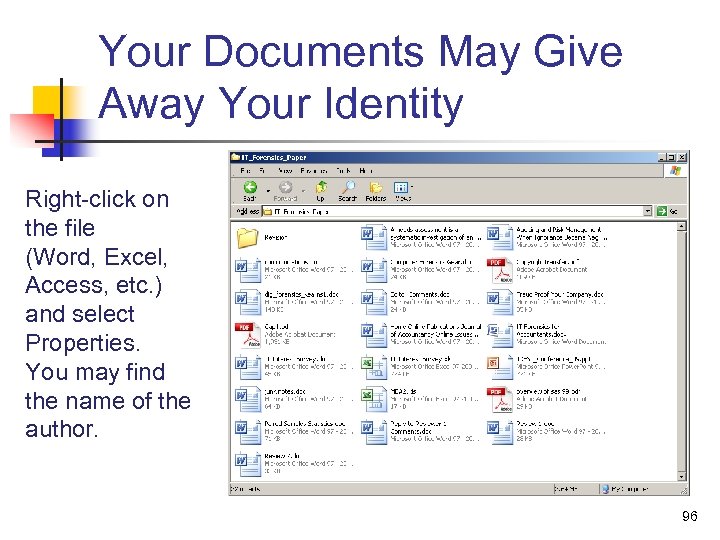 Your Documents May Give Away Your Identity Right-click on the file (Word, Excel, Access, etc. ) and select Properties. You may find the name of the author. 96
Your Documents May Give Away Your Identity Right-click on the file (Word, Excel, Access, etc. ) and select Properties. You may find the name of the author. 96
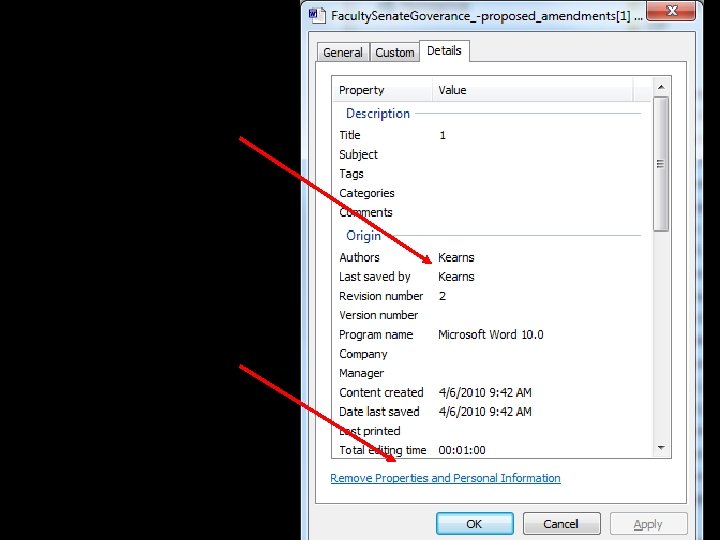
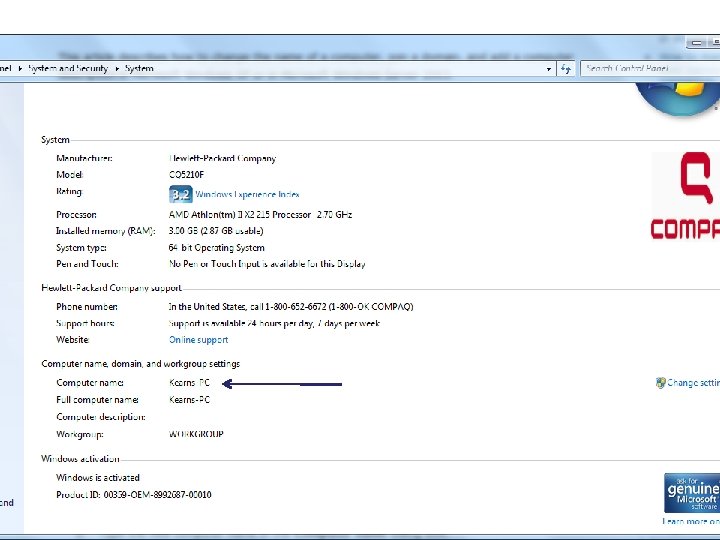
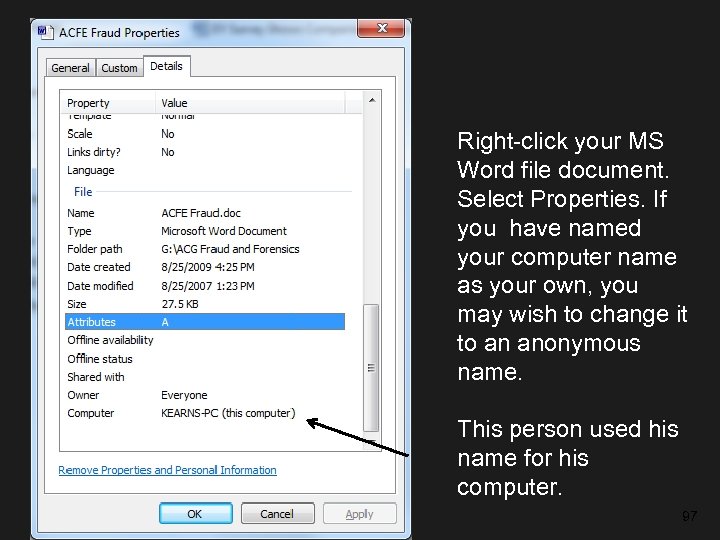 Right-click your MS Word file document. Select Properties. If you have named your computer name as your own, you may wish to change it to an anonymous name. This person used his name for his computer. 97
Right-click your MS Word file document. Select Properties. If you have named your computer name as your own, you may wish to change it to an anonymous name. This person used his name for his computer. 97
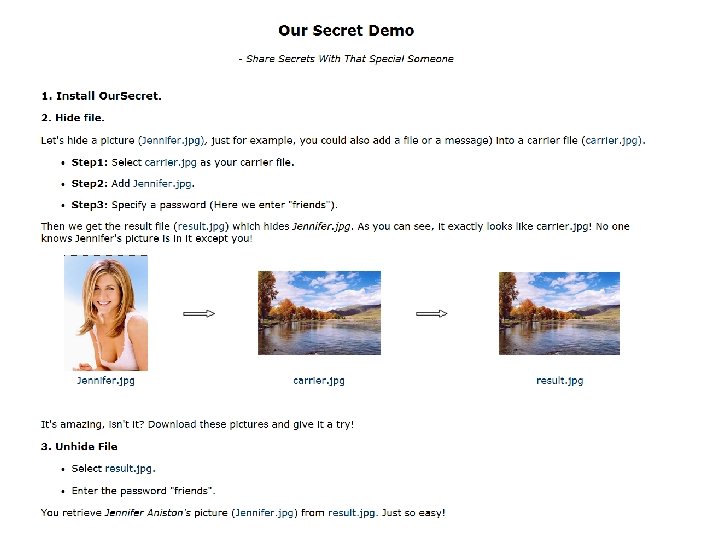
 Virtual Credit Cards
Virtual Credit Cards
 102
102
 105
105
 106
106
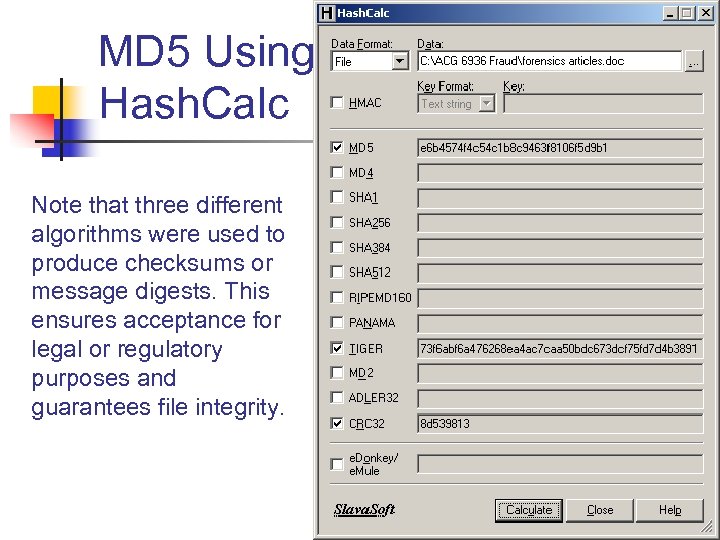 MD 5 Using Hash. Calc Note that three different algorithms were used to produce checksums or message digests. This ensures acceptance for legal or regulatory purposes and guarantees file integrity. 107
MD 5 Using Hash. Calc Note that three different algorithms were used to produce checksums or message digests. This ensures acceptance for legal or regulatory purposes and guarantees file integrity. 107
 108
108
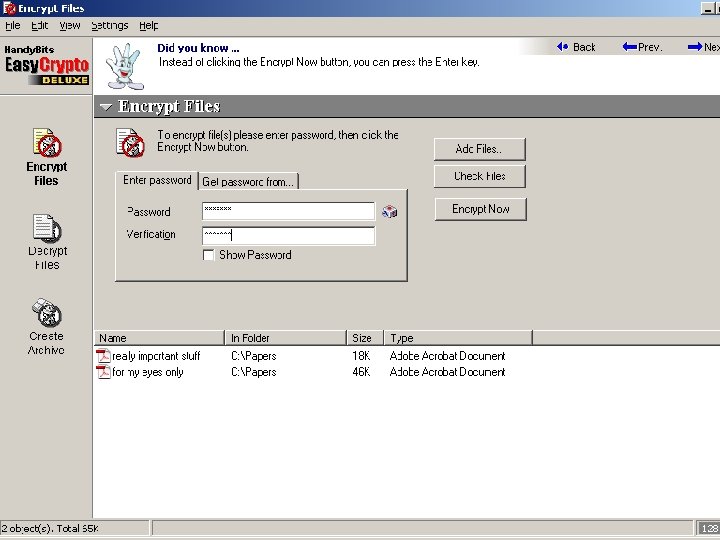 109
109
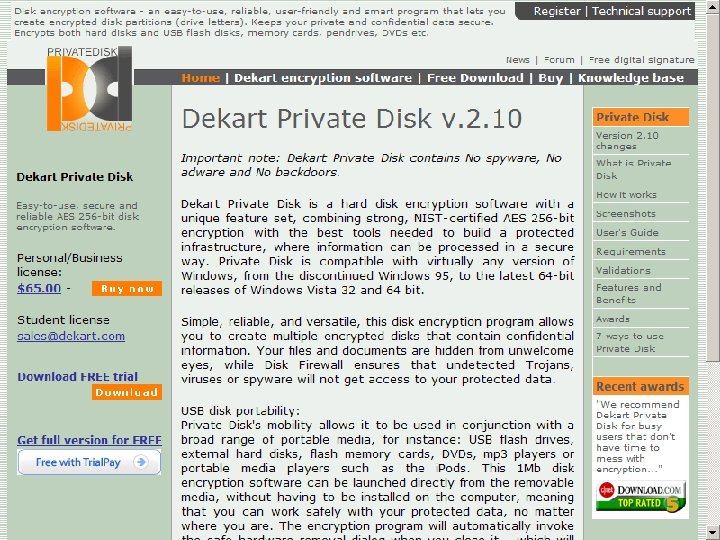 110
110
 111
111
 112
112
 113
113
 114
114


