73c112981b8c7e2caa8a102d4c50c253.ppt
- Количество слайдов: 10
 1 /10 draft-urien-tls-keygen-00. txt TLS Key Generation Pascal. Urien@telecom-paristech. fr Pascal URIEN, IETF 72 rd, Monday July 28 th Dublin, Ireland http: //www. telecom-paristech. fr
1 /10 draft-urien-tls-keygen-00. txt TLS Key Generation Pascal. Urien@telecom-paristech. fr Pascal URIEN, IETF 72 rd, Monday July 28 th Dublin, Ireland http: //www. telecom-paristech. fr
 2 /10 Summary The TLS protocol is widely deployed and used over the Internet. Binary encoding, wide adoption There is an increasing need in the Internet to set up efficient key distribution infrastructures. This draft proposes a keying infrastructure based on the TLS protocol. Differences with the draft-ietf-tls-extractor Computed keys In draft-ietf-tls-extractor-01. txt the TLS PRF function is used In draft-urien-tls-keygen-00. txt a separate KDF function is used Pushed keys The point that is not addressed by draft-ietf-tls-extractor 01. txt, is the case for which keys are pushed by server and not computed by both parties (client and server) Pascal URIEN, IETF 72 rd, Monday July 28 th Dublin, Ireland
2 /10 Summary The TLS protocol is widely deployed and used over the Internet. Binary encoding, wide adoption There is an increasing need in the Internet to set up efficient key distribution infrastructures. This draft proposes a keying infrastructure based on the TLS protocol. Differences with the draft-ietf-tls-extractor Computed keys In draft-ietf-tls-extractor-01. txt the TLS PRF function is used In draft-urien-tls-keygen-00. txt a separate KDF function is used Pushed keys The point that is not addressed by draft-ietf-tls-extractor 01. txt, is the case for which keys are pushed by server and not computed by both parties (client and server) Pascal URIEN, IETF 72 rd, Monday July 28 th Dublin, Ireland
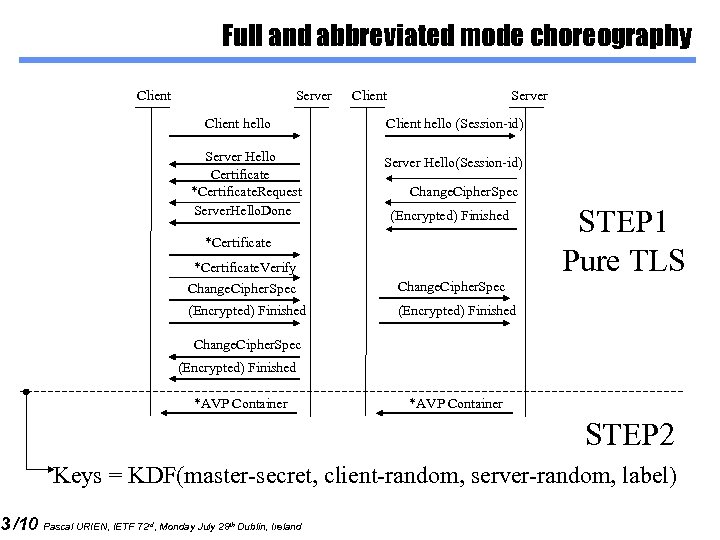 3 /10 Full and abbreviated mode choreography Client Server Client hello Server Hello Certificate *Certificate. Request Server. Hello. Done Client Server Client hello (Session-id) Server Hello(Session-id) Change. Cipher. Spec (Encrypted) Finished *Certificate. Verify Change. Cipher. Spec (Encrypted) Finished STEP 1 Pure TLS (Encrypted) Finished Change. Cipher. Spec (Encrypted) Finished *AVP Container STEP 2 Keys = KDF(master-secret, client-random, server-random, label) Pascal URIEN, IETF 72 rd, Monday July 28 th Dublin, Ireland
3 /10 Full and abbreviated mode choreography Client Server Client hello Server Hello Certificate *Certificate. Request Server. Hello. Done Client Server Client hello (Session-id) Server Hello(Session-id) Change. Cipher. Spec (Encrypted) Finished *Certificate. Verify Change. Cipher. Spec (Encrypted) Finished STEP 1 Pure TLS (Encrypted) Finished Change. Cipher. Spec (Encrypted) Finished *AVP Container STEP 2 Keys = KDF(master-secret, client-random, server-random, label) Pascal URIEN, IETF 72 rd, Monday July 28 th Dublin, Ireland
 4 /10 Full and abbreviated mode choreography What is available at the end of STEP 1. Client-random, Server-random, master-secret, negotiated cipher-suite Implicit KDF function, with an implicit label Other KDF functions MAY be negotiated via TLS-Extensions Cryptographic keys (Kc and Ki), used by encryption algorithms (Kc) and MAC procedures (Ki), are derived according to TLS specifications, but use KDF in place of the TLS PRF function. Keys = KDF(master-secret, client-random, server-random, label) What MAY be done during STEP 2. Keys MAY be sent encrypted in an AVP container A new label (for the KDF function) MAY be sent in an AVP container. Pascal URIEN, IETF 72 rd, Monday July 28 th Dublin, Ireland
4 /10 Full and abbreviated mode choreography What is available at the end of STEP 1. Client-random, Server-random, master-secret, negotiated cipher-suite Implicit KDF function, with an implicit label Other KDF functions MAY be negotiated via TLS-Extensions Cryptographic keys (Kc and Ki), used by encryption algorithms (Kc) and MAC procedures (Ki), are derived according to TLS specifications, but use KDF in place of the TLS PRF function. Keys = KDF(master-secret, client-random, server-random, label) What MAY be done during STEP 2. Keys MAY be sent encrypted in an AVP container A new label (for the KDF function) MAY be sent in an AVP container. Pascal URIEN, IETF 72 rd, Monday July 28 th Dublin, Ireland
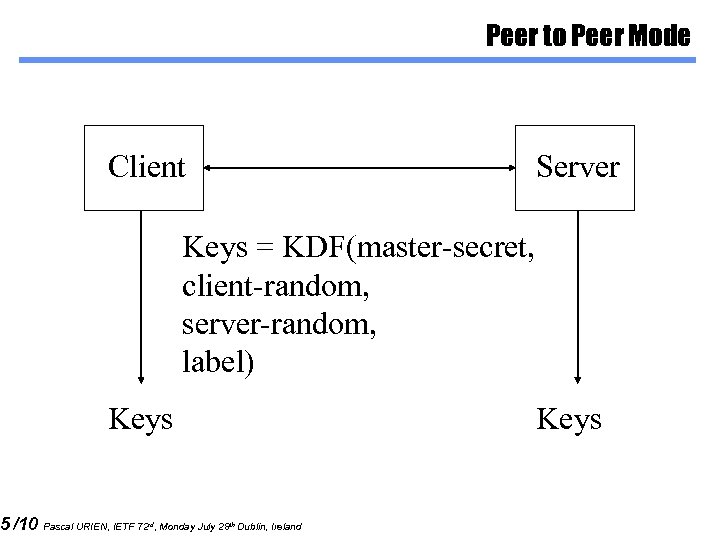 5 /10 Peer to Peer Mode Client Server Keys = KDF(master-secret, client-random, server-random, label) Keys Pascal URIEN, IETF 72 rd, Monday July 28 th Dublin, Ireland Keys
5 /10 Peer to Peer Mode Client Server Keys = KDF(master-secret, client-random, server-random, label) Keys Pascal URIEN, IETF 72 rd, Monday July 28 th Dublin, Ireland Keys
 6 /10 Distributed Mode Server Encrypted Keys Client 1 Keys are sent in AVP containers Keys Pascal URIEN, IETF 72 rd, Monday July 28 th Dublin, Ireland Encrypted Keys Client 2 Keys
6 /10 Distributed Mode Server Encrypted Keys Client 1 Keys are sent in AVP containers Keys Pascal URIEN, IETF 72 rd, Monday July 28 th Dublin, Ireland Encrypted Keys Client 2 Keys
![7 /10 AVP Container Coding (imported from TTLS] The AVP Code is four octets 7 /10 AVP Container Coding (imported from TTLS] The AVP Code is four octets](https://present5.com/presentation/73c112981b8c7e2caa8a102d4c50c253/image-7.jpg) 7 /10 AVP Container Coding (imported from TTLS] The AVP Code is four octets Combined with the Vendor-ID field if present, identifies the attribute (i. e. the container structure) uniquely. The 'V' (Vendor-Specific) bit indicates whether the Vendor-ID field is present. The 'M' (Mandatory) bit indicates whether support of the AVP is required. The 'r' bits are unused and set to 0 by the sender. The AVP Length field is three octets, and indicates the length of this AVP including the AVP Code, AVP Length, AVP Flags, Vendor-ID (if present) and Data Length is two octets and indicates the size of data without padding bytes. 0 1 2 3 4 5 6 7 8 9 0 1 +-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+ | AVP Code | +-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+ |V M r r r| AVP Length | +-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+ | Vendor-ID (opt) | +-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+ | Data Length + Data | + | | Optional padding bytes +-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+ th Pascal URIEN, IETF 72 rd, Monday July 28 Dublin, Ireland
7 /10 AVP Container Coding (imported from TTLS] The AVP Code is four octets Combined with the Vendor-ID field if present, identifies the attribute (i. e. the container structure) uniquely. The 'V' (Vendor-Specific) bit indicates whether the Vendor-ID field is present. The 'M' (Mandatory) bit indicates whether support of the AVP is required. The 'r' bits are unused and set to 0 by the sender. The AVP Length field is three octets, and indicates the length of this AVP including the AVP Code, AVP Length, AVP Flags, Vendor-ID (if present) and Data Length is two octets and indicates the size of data without padding bytes. 0 1 2 3 4 5 6 7 8 9 0 1 +-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+ | AVP Code | +-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+ |V M r r r| AVP Length | +-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+ | Vendor-ID (opt) | +-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+ | Data Length + Data | + | | Optional padding bytes +-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+ th Pascal URIEN, IETF 72 rd, Monday July 28 Dublin, Ireland
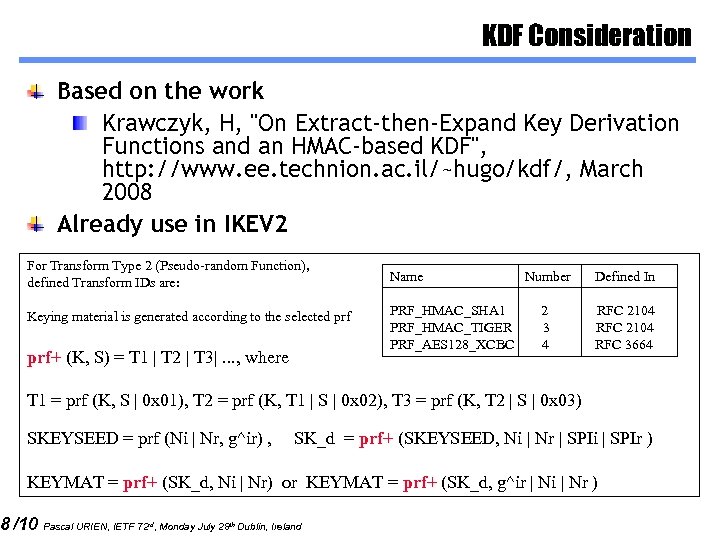 KDF Consideration Based on the work Krawczyk, H, "On Extract-then-Expand Key Derivation Functions and an HMAC-based KDF", http: //www. ee. technion. ac. il/~hugo/kdf/, March 2008 Already use in IKEV 2 For Transform Type 2 (Pseudo-random Function), defined Transform IDs are: Keying material is generated according to the selected prf+ (K, S) = T 1 | T 2 | T 3|. . . , where Name Number Defined In PRF_HMAC_SHA 1 2 RFC 2104 PRF_HMAC_TIGER 3 RFC 2104 PRF_AES 128_XCBC 4 RFC 3664 T 1 = prf (K, S | 0 x 01), T 2 = prf (K, T 1 | S | 0 x 02), T 3 = prf (K, T 2 | S | 0 x 03) SKEYSEED = prf (Ni | Nr, g^ir) , SK_d = prf+ (SKEYSEED, Ni | Nr | SPIi | SPIr ) KEYMAT = prf+ (SK_d, Ni | Nr) or KEYMAT = prf+ (SK_d, g^ir | Ni | Nr ) 8 /10 Pascal URIEN, IETF 72 rd, Monday July 28 th Dublin, Ireland
KDF Consideration Based on the work Krawczyk, H, "On Extract-then-Expand Key Derivation Functions and an HMAC-based KDF", http: //www. ee. technion. ac. il/~hugo/kdf/, March 2008 Already use in IKEV 2 For Transform Type 2 (Pseudo-random Function), defined Transform IDs are: Keying material is generated according to the selected prf+ (K, S) = T 1 | T 2 | T 3|. . . , where Name Number Defined In PRF_HMAC_SHA 1 2 RFC 2104 PRF_HMAC_TIGER 3 RFC 2104 PRF_AES 128_XCBC 4 RFC 3664 T 1 = prf (K, S | 0 x 01), T 2 = prf (K, T 1 | S | 0 x 02), T 3 = prf (K, T 2 | S | 0 x 03) SKEYSEED = prf (Ni | Nr, g^ir) , SK_d = prf+ (SKEYSEED, Ni | Nr | SPIi | SPIr ) KEYMAT = prf+ (SK_d, Ni | Nr) or KEYMAT = prf+ (SK_d, g^ir | Ni | Nr ) 8 /10 Pascal URIEN, IETF 72 rd, Monday July 28 th Dublin, Ireland
 9 /10 Proposed default KDF Notations. The first argument to a keyed function denotes the key, the value K is the key to PRF and x its input. The symbol || denotes concatenation. Given two numbers N and n the symbol N: n represents the value N written as n-bit integer. L is the length in bits, of this output value delivers by the HMAC procedure (L=160 for SHA 1) Pseudo Random Key PRK = HMAC (client-random || server-random, master-secret) Keying material, whose length in bits is D, required D/L operations. First is expressed as K(1) = HMAC(PRK, 0: L || Key. Label || 0: 32), Further operations (whose number is i) are computed according to K(i+1) = HMAC(PRK, K(i) || Key. Label || i: 32) where Key. Label is an ASCII string set to "key expansion". Pascal URIEN, IETF 72 rd, Monday July 28 th Dublin, Ireland
9 /10 Proposed default KDF Notations. The first argument to a keyed function denotes the key, the value K is the key to PRF and x its input. The symbol || denotes concatenation. Given two numbers N and n the symbol N: n represents the value N written as n-bit integer. L is the length in bits, of this output value delivers by the HMAC procedure (L=160 for SHA 1) Pseudo Random Key PRK = HMAC (client-random || server-random, master-secret) Keying material, whose length in bits is D, required D/L operations. First is expressed as K(1) = HMAC(PRK, 0: L || Key. Label || 0: 32), Further operations (whose number is i) are computed according to K(i+1) = HMAC(PRK, K(i) || Key. Label || i: 32) where Key. Label is an ASCII string set to "key expansion". Pascal URIEN, IETF 72 rd, Monday July 28 th Dublin, Ireland
 10 /10 Questions ? Pascal URIEN, IETF 72 rd, Monday July 28 th Dublin, Ireland
10 /10 Questions ? Pascal URIEN, IETF 72 rd, Monday July 28 th Dublin, Ireland


