37784a2e40d1f0c8e782ebf2f942c089.ppt
- Количество слайдов: 62

臺灣學術網路竹苗區域網路中心 89年網際網路教育訓練及 推廣研習課程 網路系統安全 交 通 大 學 計 算 機 與網路中 心 陳昌盛

課程概要 • • • 網路系統安全入門簡介 網路攻擊 電腦病毒 網路認證機制 入侵偵測/攻擊防治 案例 HCRC’ 2000 網路系統訓練課程 – 網路系統安全

0. 1 從何處取得網路安全的相關資訊 ? • 關於網路系統安全的網站 – http: //www. cert. org/ – http: //www. cert. org. tw • Newsgroups: – comp. security. misc, comp. security. unix, . . . • 技術報導網站 (PC Magazine) – http: //www. zdnet. com • 一般資訊定義 – http: //www. whatis. com

1. 網路系統安全入門 • • 封包觀測程式 網路入侵攻擊 電腦病毒偵測 存取管制 安全傳送系統 電腦編碼系統 數位認證 數位簽章

Network Packet 觀測程式 • Net. Xray (Windows) • Tcp_dump 程式 (Unix)

存取管制 (Access Control) • 防火牆 (Firewall) – Packet filter • 代理伺服系統 (Proxy Server) – Application gateway • 個別系統設 ACL

Secure Communication • Secure Telnet/FTP program suites – SNP (Secure Network Programs) – SSH • Secure HTTP communication – SSL/TLS – SET – CA 第三者認證 – digital signature 數位簽章

編碼系統 • 加密解密方式 – Public-key • RSA, PGP – Private Key • DES

編碼系統 (續) • • • Kerberose (Unix) MD 5 ( Message-Digest) Digital Signature 數位簽章 Digital Certificate 數位認證 CA 認證單位

2. 1 常見的網路攻擊型態 • Denial-of-Service – ping ( system bug ) – SPAM E-mail/Net. News, –. . . • Intrusion (電腦與網路入侵) – Trojan Horse ( BO, Net. Bus, . . . ) – computer virus, worm • Information Theft – Trojan Horse ( BO, Net. Bus, … 遙控程式)

幾種常見的網路攻擊模式 • Script kiddies (半桶水的小伙子最喜歡的把戲) • Web Vandals – 透過有問題的 CGI, … – 蓋掉某網站的網頁 • Internal Intruders – password cracker • Serious Attacker – 透過 DNS 蒐集資料 – 利用程式全面掃描 – 入侵有問題的系統

2. 2 Server Software Bug • 成因: – degisn bug - Buffer overflow 問題 • cases: – BIND, sendmail, imap, … – http: //www. cert. org • 因應之道: – 勤作 system patch – upgrade 到最新的版本 ( 通常情況)

DNS/BIND Security 問題 • BIND 最新的正式版本 8. 2. 2 -P 5 – 8. 2. 3 T 5 b, beta test version • BIND/named Security issues – Buffer overflow 與 CNAME bug 等嚴重問題 – 參考 CERT 相關網頁報告 ( CERT Advisory ) – http: //www. cert. org • Upgrade 到最新版本

2. 3 denial of service (Do. S) attack的定義 • On the Internet, a denial of service (Do. S) attack is an incident in which a user or organization is deprived of the services of a resource they would normally expect to have. • Typically, the loss of service is the inability of a particular network service, such as e-mail, to be available or the temporary loss of all network connectivity and services. • In the worst cases, for example, a Web site accessed by millions of people can occasionally be forced to temporarily cease operation. .
![denial of service (Do. S) attack [2] • A denial of service attack can denial of service (Do. S) attack [2] • A denial of service attack can](https://present5.com/presentation/37784a2e40d1f0c8e782ebf2f942c089/image-15.jpg)
denial of service (Do. S) attack [2] • A denial of service attack can also destroy programming and files in a computer system • Although usually intentional and malicious, a denial of service attack can sometimes happen accidentally. • A denial of service attack is a type of security breach to a computer system that does not usually result in theft of information or other security loss. – However, these attacks can cost the target person or company a great deal of time and money.

Do. S 意外案例- WINS 與 DNS • WINS 設定不當, 導致大量消耗可用頻寬 – 實例, 過去 TANet 竹苗區網某一學校, 曾經發生 • http: //www. edu. tw (MOECC newsletter, 參考 8801 -8806 期 ) – 儘量避免使用 • 啟動 Negative Caching 功能 – 自我保護 – 避免拖累網路大環境 • 請Upgrade 到最新版本 ( BIND 8. x 以後) – 內建 Negative Caching

SPAM Mail & DNS • SPAM Mail <=> UCE/UBE (不請自來) • UCE = Unsolicited Commercial E-mail • UBE = Unsolicited Bulk E-Mail • UCE/UBE 散佈途徑 – 名單收錄 • www homepage, USENET news articles • account password files on individual servers • 其他不當途徑 ( program bug, 招募會員活動, …) – 找尋管理較鬆散的 mail relay • Domain Zone scanning ( DNS) • URL scanning (web pages )

DDo. S 攻擊 • • Client ( 主控系統) Host (助攻系統) Broadcasters(放大系統) Target(目標網路/站)


2. 4 Firewall 的定義與用途 • A firewall is a set of related programs, located at a network gateway server, that protects the resources of a private network from users from other networks. (The term also implies the security policy that is used with the programs. ) • An enterprise with an intranet that allows its workers access to the wider Internet installs a firewall to prevent outsiders from accessing its own private data resources and for controlling what outside resources its own users have access to.

Firewall 的定義與用途(2) • Basically, a firewall, working closely with a router program, filters all network packets to determine whether to forward them toward their destination. • A firewall also includes or works with a proxy server that makes network requests on behalf of workstation users. • A firewall is often installed in a specially designated computer separate from the rest of the network so that no incoming request can get directly at private network resources.
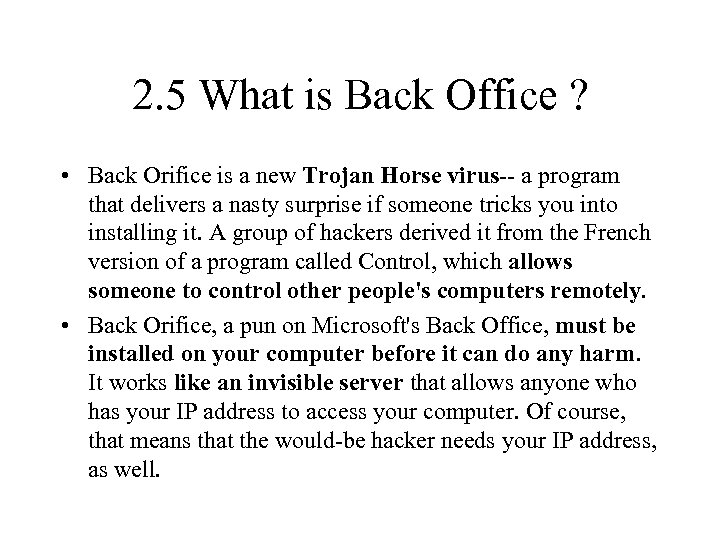
2. 5 What is Back Office ? • Back Orifice is a new Trojan Horse virus-- a program that delivers a nasty surprise if someone tricks you into installing it. A group of hackers derived it from the French version of a program called Control, which allows someone to control other people's computers remotely. • Back Orifice, a pun on Microsoft's Back Office, must be installed on your computer before it can do any harm. It works like an invisible server that allows anyone who has your IP address to access your computer. Of course, that means that the would-be hacker needs your IP address, as well.

3. 電腦病毒概念簡介 • • 什麼是 “電腦病毒” ? 電腦病毒的傳染途徑. 電腦病毒的簡單分類. 如何防範電腦病毒.

virus 的基本定義 is a piece of programming code usually disguised as something else that causes some unexpected and, for the victim, usually undesirable event and which is often designed so that it is automatically spread to other computer users. • Viruses can be transmitted by sending them as attachments to an e-mail note, by downloading infected programming from other sites, or be present on a diskette or CD. • A virus – The source of the e-mail note, downloaded file, or diskette you've received is often unaware of the virus.

3. 1電腦病毒入侵的途徑 • 三大途徑 – 經由軟碟磁片或抽取可攜式硬碟 – 經由網際網路的下載區 – 經由 e-mail 的夾帶檔 (attachment)

3. 2電腦病毒感染的癥候 • • 不正常的訊息, 顯示在電腦螢幕上 不定期, 出現不正常的聲響或音樂 系統上可用的記憶體, 突然變少 硬碟的名稱, 突然變掉了

Virus 感染後的影響 • Some viruses wreak their effect as soon as their code is executed; other viruses lie dormant until circumstances cause their code to be executed by the computer. • Some viruses are playful in intent and effect ("Happy Birthday, Ludwig!") and some can be quite harmful, erasing data or causing your hard disk to require reformatting.

3. 3 電腦病毒的分類 • 電腦病毒大略可分成 4 類 – 磁片開機磁區 (boot sector) 病毒 – 檔案或程式 (file or program)病毒 – 巨集 (macro)病毒 – 多種混合型 (multipartite)病毒

3. 4其他惡意程式 • worm – 會自我複製, 但不一定會傳染給其他程式 – 近期知名例子, 經由 MS-Outlook 這個 e-mail 系統的 address book 散播 • Melissa, ILOVEYOU • Trojan horse (特洛伊木馬) 程式 – 平時隱藏在某一些看起來無害的程式中, 等到某一 些特殊情況, 再起來作怪. • 以上這兩類, 不論 Unix 或一般的 Windows 都有

Trojan Horse Programs • In computers, a Trojan horse is a program in which malicious or harmful code is contained inside apparently harmless programming or data in such a way that it can get control and do its chosen form of damage, such as ruining the file allocation table on your hard disk. – In one celebrated case, a Trojan horse was a program that was supposed to find and destroy computer viruses. – A Trojan horse can be considered a virus if it is widely redistributed.

4. 網路認證機制 • • • 認證單位- CA (Certification Authority) 數位電子證書 ( digital certificate) 數位簽章 (digital signature) SSL/TLS SET 安全電子交易

SSL (Secure Sockets Layer) • SSL (Secure Sockets Layer) is a program layer created by Netscape for managing the security of message transmissions in a network. • Netscape's idea is that the programming for keeping your messages confidential ought to be contained in a program layer between an application (such as your Web browser or HTTP) and the Internet's TCP/IP layers. – The "sockets" part of the term refers to the sockets method of passing data back and forth between a client and a server program in a network or between program layers in the same computer.
![SSL (Secure Sockets Layer) [2] • Netscape's SSL uses the public-and-private key encryption system SSL (Secure Sockets Layer) [2] • Netscape's SSL uses the public-and-private key encryption system](https://present5.com/presentation/37784a2e40d1f0c8e782ebf2f942c089/image-33.jpg)
SSL (Secure Sockets Layer) [2] • Netscape's SSL uses the public-and-private key encryption system from RSA, which also includes the use of a digital certificate. • Netscape has offered SSL as a proposed standard protocol to the World Wide Web Consortium (W 3 C) and the Internet Engineering Task Force (IETF) as a standard security approach for Web browsers and servers.

CA (certificate authority) • A CA is an authority in a network that issues and manages security credentials and public keys for message encryption and decryption. • As part of a public key infrastructure (PKI), a CA checks with a registration authority (RA) to verify information provided by the requestor of a digital certificate. If the RA verifies the requestor's information, the CA can then issue a certificate. • Depending on the public key infrastructure implementation, the certificate includes the owner's public key, the expiration date of the certificate, the owner's name, and other information about the public key owner.

SET-Secure Electronic Transaction • Short for Secure Electronic Transaction, a new standard that will enable secure credit card transactions on the Internet. SET has been endorsed by virtually all the major players in the electronic commerce arena, including Microsoft, Netscape, Visa, and Mastercard. • By employing digital signatures, SET will enable merchants to verify that buyers are who they claim to be. And it will protect buyers by providing a mechanism for their credit card number to be transferred directly to the credit card issuer for verification and billing without the merchant being able to see the number.

SSL 的運作機制 • SSL 是設計來讓 www 用戶, 與想要連線的www server, 透過加密的方式, 真正達到溝通交換資 料的方式. – 必須確保, 用戶的瀏覽程式(browser), 是真正的連到 想要連的 www server (而不是其他冒充的 server. ) – 加密, 以確保資料不至於外洩給不相干的第三者.

SSL 的運作流程如下 • 當用戶的 瀏覽程式, 初次使用 SSL, 連上某 secure www server 時, – 該 server 必須提示, 其經由第三者( CA 提供者)發出的認證, 以 供查驗. • 接著, 用戶的瀏覽程式, 必須檢查該認證是否合乎底下 三條件. – 該認證, 是否由信譽卓著的認證機構發出. – 該認證, 應該還在有效期間. – 該認證, 的確是發給你正在連的 www server. • 上述檢查, 必須完全合格, 否則用戶的瀏覽程式, 必須發 出警告訊息, 通知使用者.

認證漏洞的案例 • Netscape 4. 7. 3 以前的版本, 被發現在某一些特殊的情況 下, 會發生 SSL 認證有漏洞. ==> upgrade 到 4. 7. 3 – 2000/5/12 , CERT-2000 -08 號報告. • IE 5. 0 也有類似的問題 – 2000/06/CERT Advisory CA-2000 -10 Inconsistent Warning Messages in Internet Explorer • http: //www. cert. org

5. 入侵偵測與攻擊防治 • • 系統入侵偵測 病毒防治 Anti-SPAM & Anti-virus mail 問題處理與追蹤

5. 1. Generic Access Control Issues • 分層負責 – Router ACL – DNS server ACL – 個別 server 的 ACL • SMTP - sendmail • http proxy - squid • NNTP - inn

5. 1. 1 DNS 設定與入侵嘗試 • 特定對象的入侵 – buffer overflow 等系統問題 • 尋找不特定的入侵對象 – forward & reverse domain zone scanning • DNS zone transfer 設限 – 阻擋不特定的目標搜索

5. 1. 2 DNS server 設限 • BIND 8. x /etc/named. conf 的相關片段 options { directory /var/named; allow-transfer { none; // 原則上, 阻擋所有 不相干的 zone transfer }; allow-query { Trusted-IP}; // 僅允許鄰近地區的使用者 }; // 省略 zone “nctu. edu. tw” { type master ; file “Zone-NCTU” ; allow-query { any; }; allow-transfer { 140. 113. 1. 1; 140. 113. 6. 2; // 允許 slave/secondary server }; }; zone “ 113. 140. in-addr. arpa” { ….

Do. S Network Attack via DNS • DNS 放大攻擊 ( DNS ACL) – 假造 IP 封包 ( Router ACL) – http: //dnsrd. nctu. edu. tw/Tech/cert. html • 紓緩之道 – 個別 DNS 設限 – http: //dnsrd. nctu. edu. tw/Named-Conf/named. conf-c
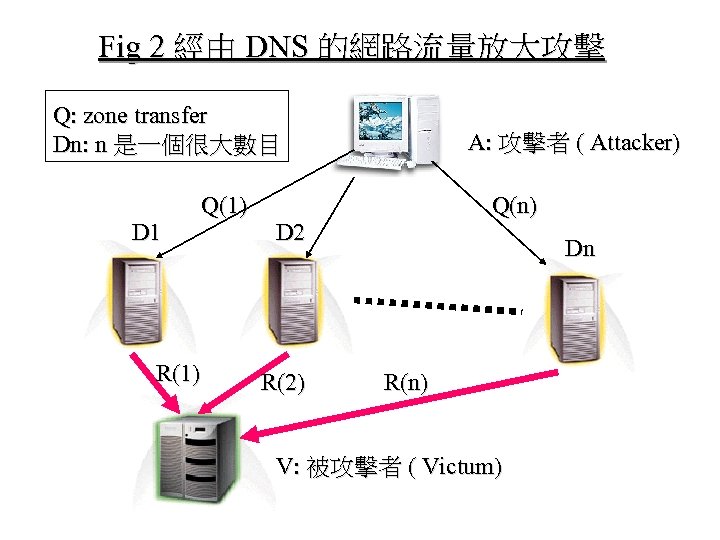
Fig 2 經由 DNS 的網路流量放大攻擊 Q: zone transfer Dn: n 是一個很大數目 D 1 R(1) Q(1) A: 攻擊者 ( Attacker) Q(n) D 2 R(2) Dn R(n) V: 被攻擊者 ( Victum)

5. 1. 3 Free. BSD 的 firewall - IPfilter • ipfw show 00100 1057 62180 deny tcp from 210. 209. 33. 176 to 163. 28. 64. 246 25 00200 1488 65232 deny tcp from 210. 209. 33. 188 to 163. 28. 64. 246 25 65535 2387573165 1175186687077 allow ip from any to any • ipfw add deny tcp from 210. 59. 168. 2

5. 1. 4 Unix 系統上-簡易的 firewall • tcp_wrapper – telnet, ftp, … – block mail spam • hosts. allow+host. deny

/etc/hosts. allow in. rlogind: 140. 113. 1. , 140. 113. 6. : severity local 3. info: allow in. ftpd: 140. 113. 1. 1, KNOWN@140. 113. 4. 120: severityocal 3. info: allow in. telnetd: 140. 113. 1. , KNOWN@140. 113. 4. 120: severity local 3. info: allow imapd: 140. 113. 1. , . ras. nctu. edu. tw: severity local 3. info: allow # Deny all Without FQDN sendmail: ALL EXCEPT KNOWN: deny sendmail: allow

5. 2 Anti-SPAM & Anti-virus Mail • SPAM Mail 防治 • Mail Server 端, 進行掃毒 – Cf. 用戶端掃毒 (安裝 anti-virus 軟體 ) • Mail Server 進行 SPAM-mail 防治 – Cf. 用戶端, anti-spam mail ( 使用過濾程式)

5. 2. 1 Anti SPAM Mail & DNS ACL • SMTP server upgrade/patch – 限定 mail relaying 對象 • DNS 設ACL – 可相當程度阻擋不特定的 relay 嘗試 • 系統管理人員介入 – 聯絡相關系統的管理人員 – rbl 建立 (Real-time Block List )

5. 2. 3 Mail Server 端掃毒 • Sendmail 與電腦病毒防治 – 配合 procmail , 掃描信件的 header • 可局部對付 iloveyou 之類的 script 型態的 worm/virus • procmail 是 delivery agent, 可適度進行 filtering • 使用 queuing mode, 搭配掃毒軟體, 進行 病毒掃描偵測任務
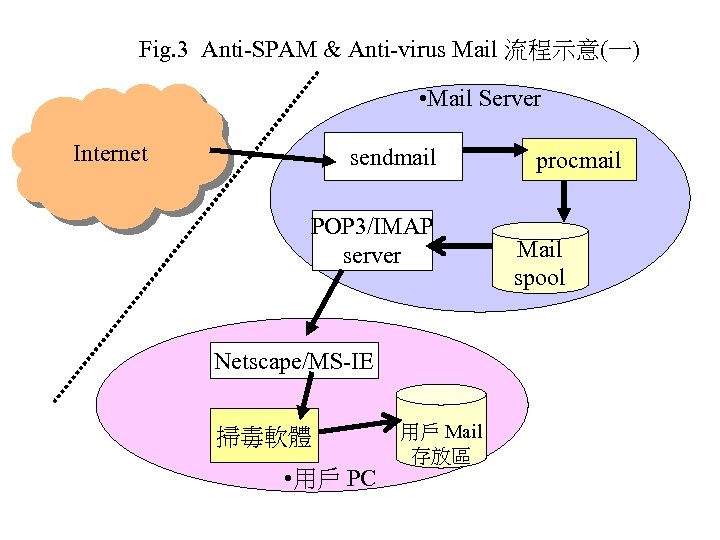
Fig. 3 Anti-SPAM & Anti-virus Mail 流程示意(一) • Mail Server Internet sendmail POP 3/IMAP server Netscape/MS-IE 掃毒軟體 • 用戶 PC 用戶 Mail 存放區 procmail Mail spool
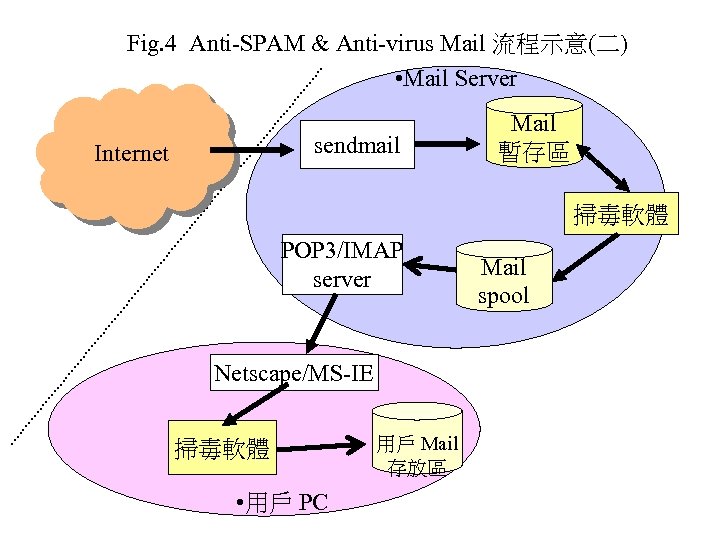
Fig. 4 Anti-SPAM & Anti-virus Mail 流程示意(二) • Mail Server sendmail Internet Mail 暫存區 掃毒軟體 POP 3/IMAP server Netscape/MS-IE 掃毒軟體 • 用戶 PC 用戶 Mail 存放區 Mail spool

5. 3 如何因應 BO 之類的程式攻擊 Basically, Back Orifice serves as a reminder to use safe computing practices: -- Don't run programs from sources you don't trust. -- Keep your anti-virus program definitions up-to-date. -- Run anti-virus scans regularly, preferably daily.

5. 3. 1 安裝入侵偵測程式 • 入侵偵測程式(Intrusion Detection System) – Zone. Alarm ( Free, 個人) • http: //www. zonealarm. com – Black. ICE defender • http: //www. networkice. com – At. Guard – NIS( Norton Internet Security) –. . .

5. 3. 2 安裝防毒軟體 • 常見防毒軟體 – Symantec Anti-virus (Norton) – Mc. Afee – PC-Cillin [ Trend Micro ; 趨勢科技 ] –. . .

6. 問題處理與追蹤 • Security 問題回報及反應 – 向相關單位報備及追蹤問題 – 向相關 CERT 報備及追蹤問題 • 各單位聯絡 e-mail address (Internet 慣例) – postmaster@your-domain-zone – abuse@your-organization, security@your-organization • 例如, postmaster@nctu. edu. tw, abuse@seed. net. tw • 案例剖析 (Case Study)

6. 1 Case Study • mbox@xyz. com. tw 轉到 德國某公司 – 本地公司設定錯誤 – 回報到該公司, 該國的 CERT, 以及TWNIC • 網路攻擊的中途站(1999. 08) – TANet 竹苗區網某校的 DNS server 被入侵 – 參考 http: //dnsrd. nctu. edu. tw

6. 2. 1 DNS & Mail - 烏龍事件 • 前幾年, 有德國X公司反應, 持續不斷接收到, 許多應該是寄往台灣 Y公司的 e-mail, 卻一直被轉往該公司. 因為收信的帳號不存在, 系 統於是一直產生, user 不在的退信, 持續往系統管理信箱塞, 信件越 累積越多, 導致server performance 大受影響. 由於該公司並無台灣 分公司, 也找不出合理的解釋, 於是開始擔心有台灣的競爭對手, 想 癱瘓他們網路的正常運作, 接下來只好採取正式的防衛行動, 透過 正式的 CERT 向相關單位反應, . . . • 成因 – 舊版 BIND/named 有 bug – 系統管理人員觀念不夠清楚 – 系統管理人員輸入資料時, IP address 打錯
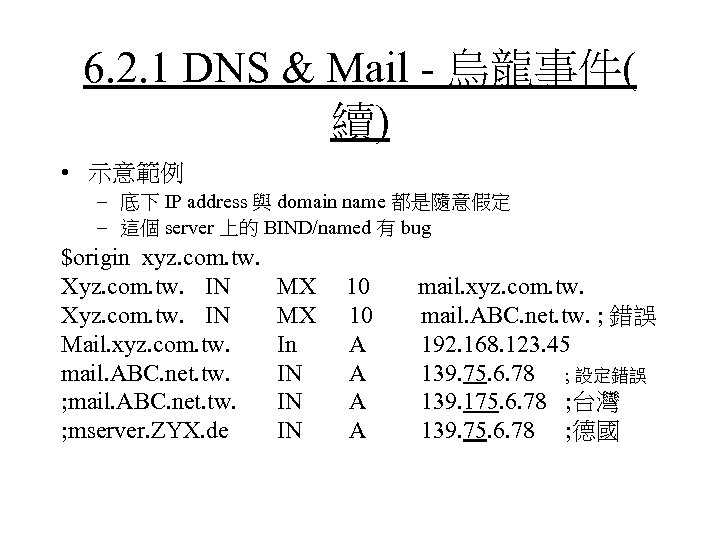
6. 2. 1 DNS & Mail - 烏龍事件( 續) • 示意範例 – 底下 IP address 與 domain name 都是隨意假定 – 這個 server 上的 BIND/named 有 bug $origin xyz. com. tw. Xyz. com. tw. IN Mail. xyz. com. tw. mail. ABC. net. tw. ; mserver. ZYX. de MX MX In IN IN IN 10 10 A A mail. xyz. com. tw. mail. ABC. net. tw. ; 錯誤 192. 168. 123. 45 139. 75. 6. 78 ; 設定錯誤 139. 175. 6. 78 ; 台灣 139. 75. 6. 78 ; 德國

6. 2. 2 竹苗區網 DNS server 入侵事件 • 某校在區網的網域, 登錄有兩個 DNS server – 不過, 從一開始, 就只有建立一個 server • 該 server-A 有 security hole, 被外來者闖入 – 入侵者, 持續透過該 server-A, 嘗試入侵國外網站 – 網域上層, 持續收到國外不同地方轉來的抱怨與求 助 e-mail • 電話通知該校管理者處理. – 後來轉維護廠家 程師. – 將近一週, 仍無改善. – 區網接手, 協助處理. • 設 tcp_wrapper, 擋掉不明來源的連線.

6. 3 相關系統管理 • 結論 – 各單位, 最好設立兩段式 Mail 組合系統 – 重要 server 勤作 security patch – DNS 設 ACL, 限制 zone transfer – 委外廠商維護能力, 意願與合約

參考資料 • Bruce, Stewart, “How to protect Against Computer Viruses”, . . . – http: //www. zdnet. com • Why Firewalls Are Not Enough – http: //www. networkice. com/html/wp_firewalls. html • Bradley Shimmin, “Deconstructing Denial of Service Attacks” – http: //www. zdnet. com
37784a2e40d1f0c8e782ebf2f942c089.ppt