b73f3b13843c7ca3cff15b9afb4b3c8a.ppt
- Количество слайдов: 162

憑證管理中心 建置與維運之實務原理 主要摘自 : 中華電信研究院歐崇明博士簡報,張光耀補充 修正 1

大綱 l PKI簡介與技術基本原理 l PKI之相關子系統功能 n n CA, RA (RAO), repository, end-entity, relying party, subscriber Certificate Policy (CP) Certification Practice Statement (CPS) X. 509 Certificate Fields l CA建置維運相關技術標準與 n n CA實際建置維運 MOICA建置維運之 CPS GCA系統之實際建置過程 憑證及電子簽章之驗證 作 秘密分享 (Secret Sharing)及忘了憑證 IC卡 login 密碼的處理 l GPKI服務推動後之議題探討 PKI: 公開金鑰基礎建設( Public Key Infrastructure) CP: Certificate Policy CPS: Certificate Practice Statement CA: 憑證機構( Certification Authority)RA: Registration authority 2

PKI簡介 與 技術基本原理 3

Schedule for PKI Environment Planning n n n Find out the business needs CP and CPS Determine hierarchy of CAs Establish the procedures for certificate applications, issuing and renewal Establish the CA management plan 4

PKI commercial needs n Purpose for PKI n n Usability of PKI n n Intranet, extranet or cooperation between enterprises 7 x 24 or available for specific area Legal responsibility for PKI n Guarantee, denial and other exclusive agreement 5

On the internet, nobody knows you’re a dog. By Peter Steiner on page 61 of July 5, 1993 issue of the New Yorker 6
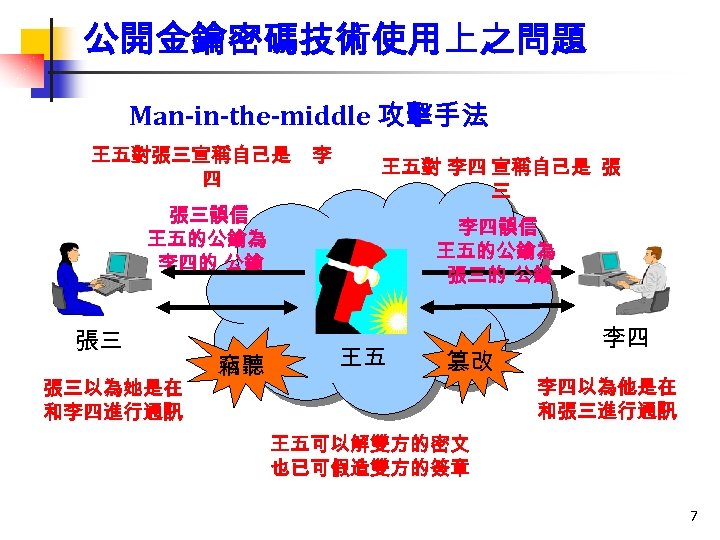
公開金鑰密碼技術使用上之問題 Man-in-the-middle 攻擊手法 王五對張三宣稱自己是 四 張三誤信 王五的公鑰為 李四的 公鑰 李 王五對 李四 宣稱自己是 張 三 Internet 張三 張三以為她是在 和李四進行通訊 竊聽 王五 李四誤信 王五的公鑰為 張三的 公鑰 篡改 李四 李四以為他是在 和張三進行通訊 王五可以解雙方的密文 也已可假造雙方的簽章 7
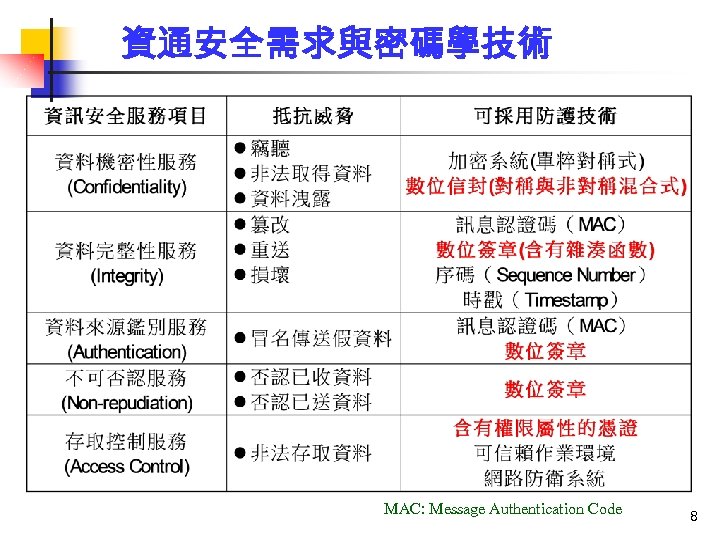
資通安全需求與密碼學技術 MAC: Message Authentication Code 8

密碼系統的分類 n 對稱式密碼系統 加密金鑰=解密金鑰 u DES, 3 DES, IDEA, AES u n 非對稱式密碼系統 又稱公開金鑰密碼系統 u 加密金鑰 ≠ 解密金鑰 u 由一對相關的密碼鑰匙組成,兩個密碼 鑰匙均可用作加密和解密 u RSA, El. Gamal, ECC u 9
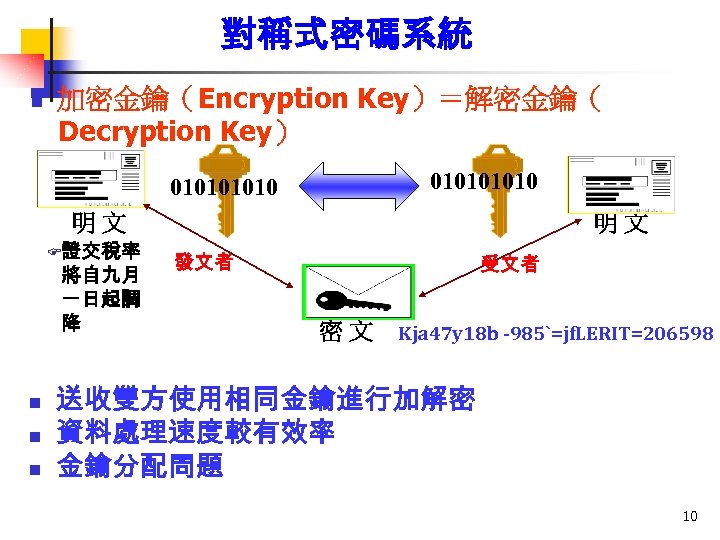
對稱式密碼系統 n 加密金鑰(Encryption Key)=解密金鑰( Decryption Key) 010101010 明文 F證交稅率 將自九月 一日起調 降 n n n 明文 發文者 受文者 密文 Kja 47 y 18 b -985`=jf. LERIT=206598 送收雙方使用相同金鑰進行加解密 資料處理速度較有效率 金鑰分配問題 10
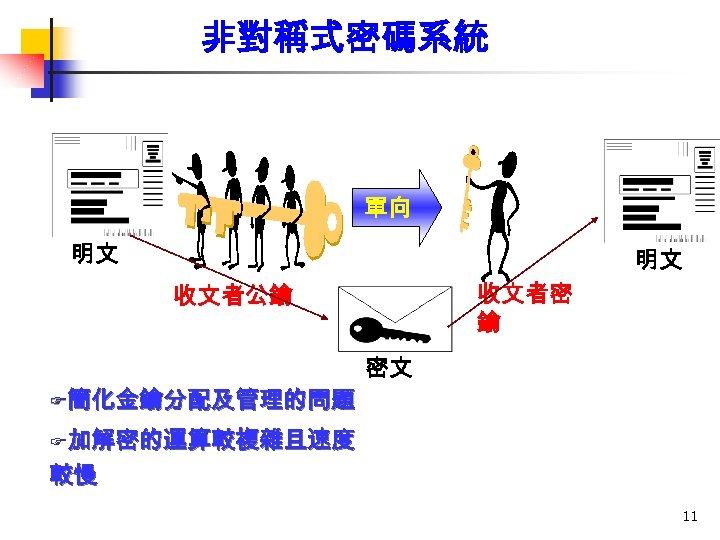
非對稱式密碼系統 單向 明文 明文 收文者密 鑰 收文者公鑰 F簡化金鑰分配及管理的問題 密文 F加解密的運算較複雜且速度 較慢 11
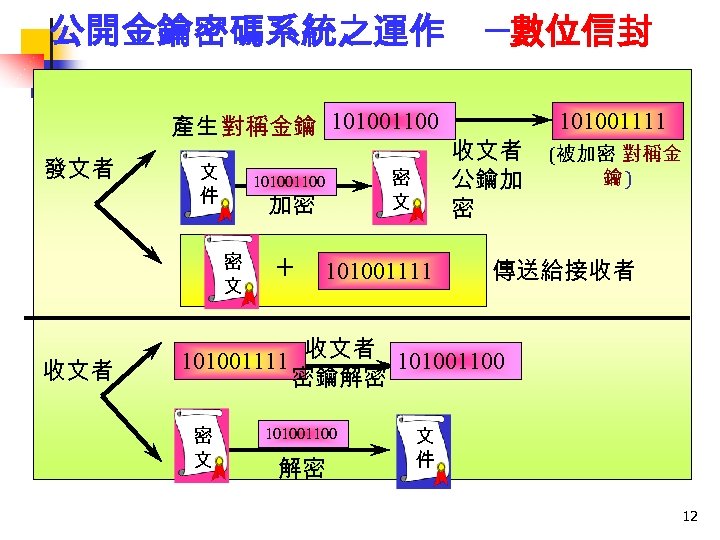
公開金鑰密碼系統之運作 產生 對稱金鑰 101001100 發文者 文 件 加密 密 文 收文者 密 文 101001100 + 101001111 ─數位信封 收文者 公鑰加 密 101001111 (被加密 對稱金 鑰) 傳送給接收者 101001111 收文者 101001100 密鑰解密 密 文 101001100 解密 文 件 12
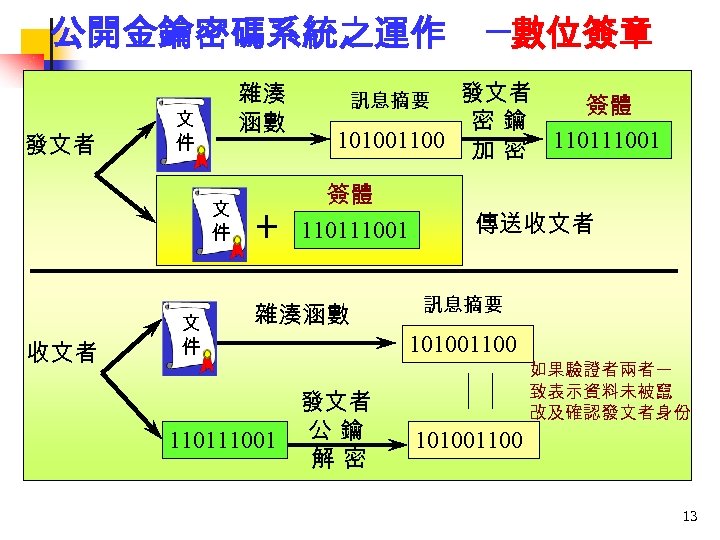
公開金鑰密碼系統之運作 發文者 雜湊 涵數 文 件 收文者 文 件 + ─數位簽章 發文者 簽體 密鑰 101001100 加 密 110111001 訊息摘要 簽體 110111001 雜湊涵數 發文者 110111001 公 鑰 解密 傳送收文者 訊息摘要 101001100 如果驗證者兩者一 致表示資料未被竄 改及確認發文者身份 101001100 13
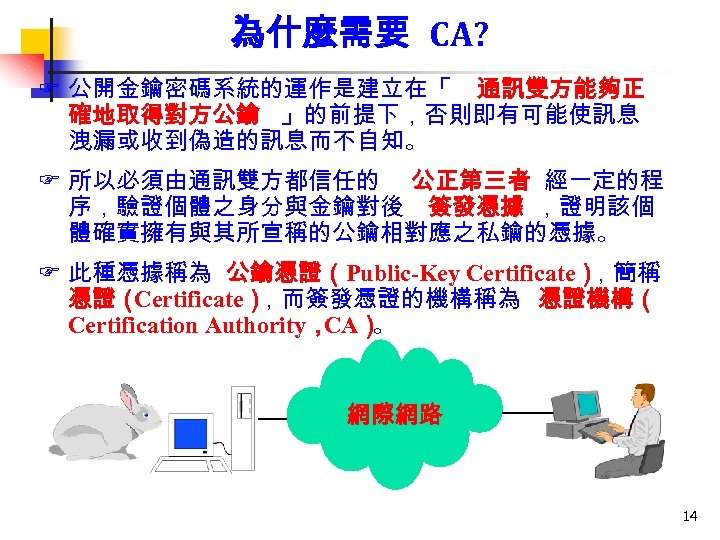
為什麼需要 CA? F 公開金鑰密碼系統的運作是建立在「 通訊雙方能夠正 確地取得對方公鑰 」的前提下,否則即有可能使訊息 洩漏或收到偽造的訊息而不自知。 F 所以必須由通訊雙方都信任的 公正第三者 經一定的程 序,驗證個體之身分與金鑰對後 簽發憑據 ,證明該個 體確實擁有與其所宣稱的公鑰相對應之私鑰的憑據。 F 此種憑據稱為 公鑰憑證(Public-Key Certificate) ,簡稱 憑證( Certificate) ,而簽發憑證的機構稱為 憑證機構( Certification Authority, CA) 。 網際網路 14
l 台灣政府開始發展 CA之狀況 Ø 需求提出、規畫案、建置、應用服 務、推廣. . . l 1999年資訊月傑出資訊應用產品獎 Ø 書面資料準備、複賽資料準備、複 賽過程 (現場展示、簡報環境、設備、 時間掌控. . . )、得獎(至 2005年有 2次獲 獎 ). . . 15
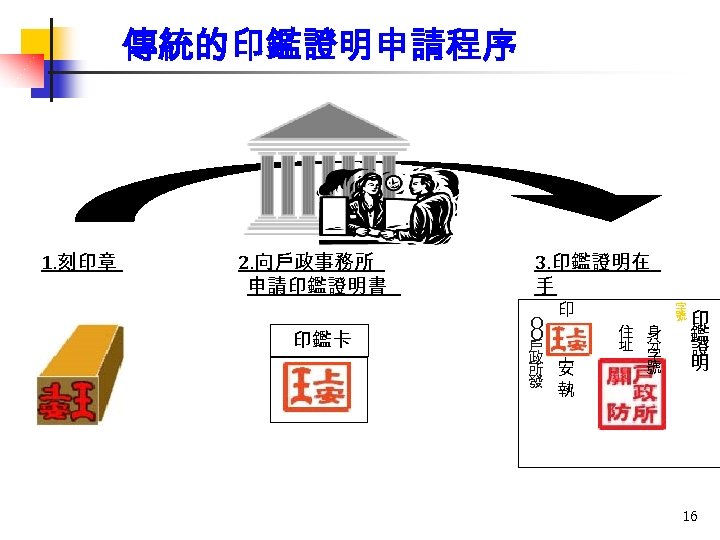
傳統的印鑑證明申請程序 1. 刻印章 2. 向戶政事務所 申請印鑑證明書 印鑑卡 3. 印鑑證明在 手 印 O O 戶 王 政 上 所 安 發 執 住 址 身 分 字 號 印 鑑 證 明 16
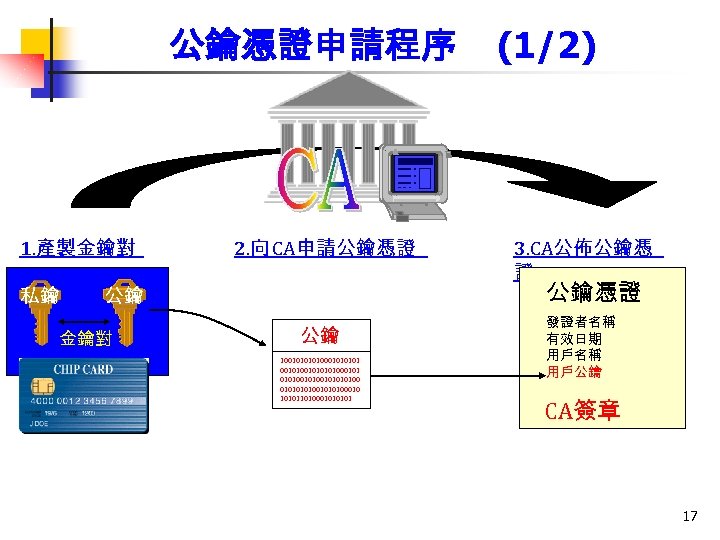
公鑰憑證申請程序 1. 產製金鑰對 私鑰 2. 向 CA申請公鑰憑證 3. CA公佈公鑰憑 證 公鑰憑證 公鑰 金鑰對 (1/2) 公鑰 100101000101010100010100101001010100010 10101101000101 發證者名稱 有效日期 用戶名稱 用戶公鑰 …… CA簽章 17
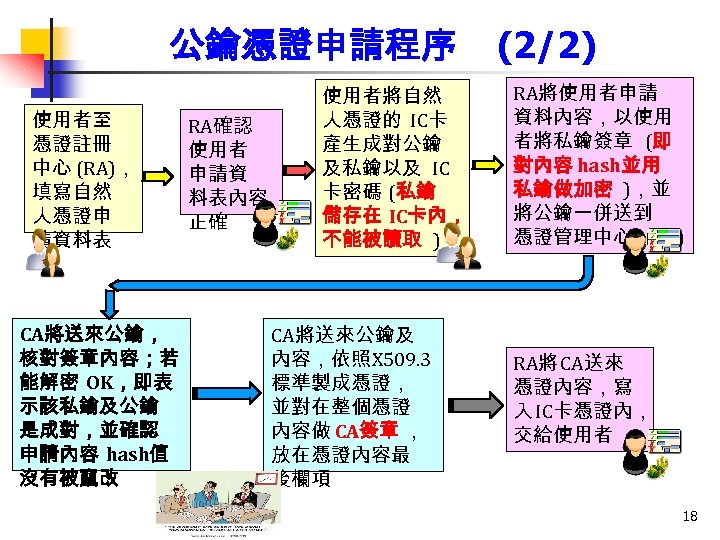
公鑰憑證申請程序 使用者至 憑證註冊 中心 (RA), 填寫自然 人憑證申 請資料表 CA將送來公鑰, 核對簽章內容;若 能解密 OK,即表 示該私鑰及公鑰 是成對,並確認 申請內容 hash值 沒有被竄改 RA確認 使用者 申請資 料表內容 正確 使用者將自然 人憑證的 IC卡 產生成對公鑰 及私鑰以及 IC 卡密碼 (私鑰 儲存在 IC卡內, 不能被讀取 ) CA將送來公鑰及 內容,依照X 509. 3 標準製成憑證, 並對在整個憑證 內容做 CA簽章 , 放在憑證內容最 後欄項 (2/2) RA將使用者申請 資料內容,以使用 者將私鑰簽章 (即 對內容 hash並用 私鑰做加密 ),並 將公鑰一併送到 憑證管理中心 (CA) RA將 CA送來 憑證內容,寫 入 IC卡憑證內, 交給使用者 18
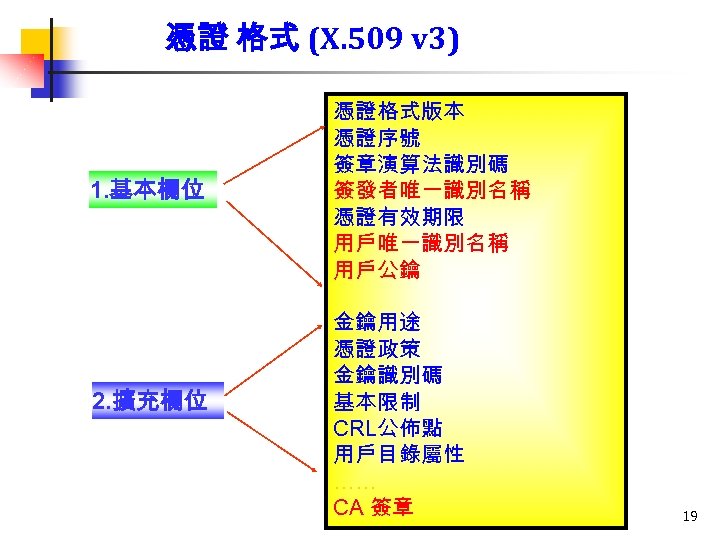
憑證 格式 (X. 509 v 3) 1. 基本欄位 2. 擴充欄位 憑證格式版本 憑證序號 簽章演算法識別碼 簽發者唯一識別名稱 憑證有效期限 用戶唯一識別名稱 用戶公鑰 金鑰用途 憑證政策 金鑰識別碼 基本限制 CRL公佈點 用戶目錄屬性 …… CA 簽章 19
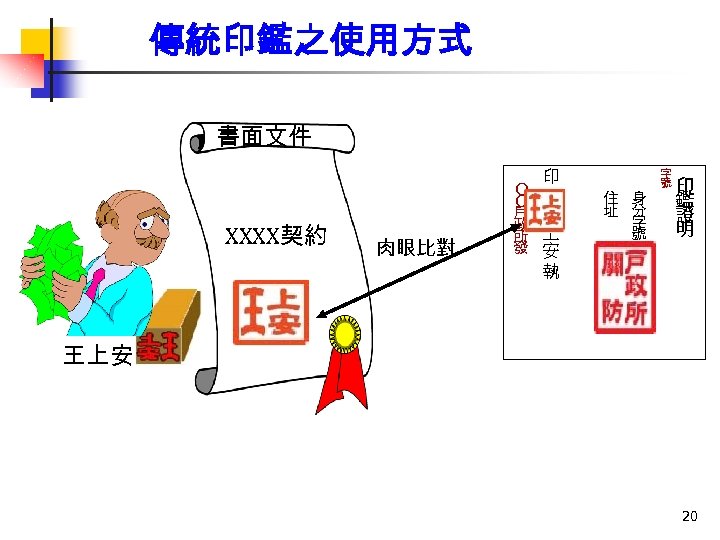
傳統印鑑之使用方式 書面文件 印 XXXX契約 祥李 印大 肉眼比對 O O 戶 王 政 所 上 發 安 住 址 身 分 字 號 印 鑑 證 明 執 王上安 20
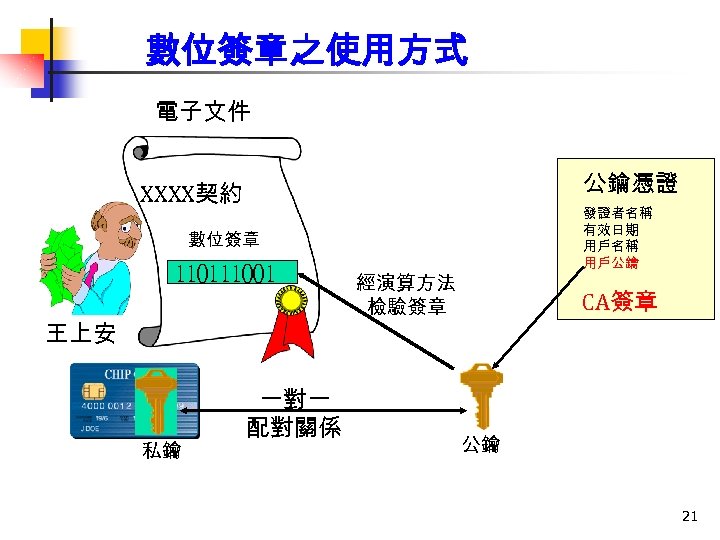
數位簽章之使用方式 電子文件 公鑰憑證 XXXX契約 數位簽章 祥李 110111001 印大 X 509 王上安 私鑰 一對一 配對關係 發證者名稱 有效日期 用戶名稱 用戶公鑰 …… 經演算方法 檢驗簽章 CA簽章 公鑰 21
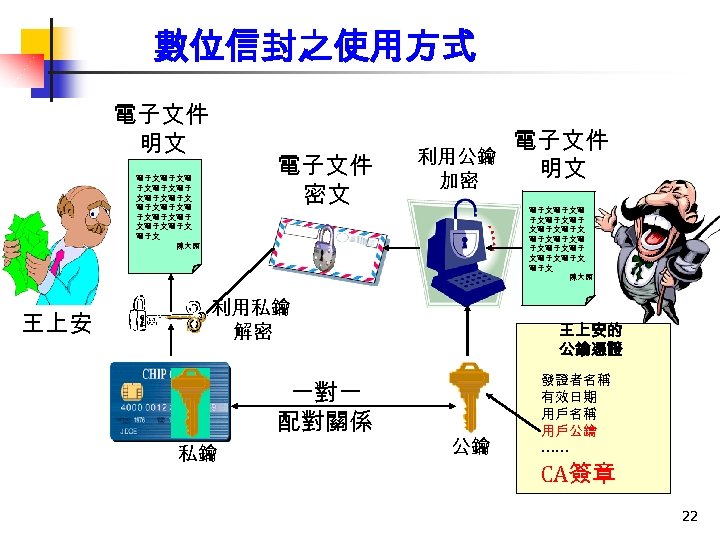
數位信封之使用方式 電子文件 明文 電子文件 密文 電子文電子文電子 文電子文電子文 電子文 陳大頭 王上安 利用公鑰 加密 電子文電子文電子 文電子文電子文 電子文 陳大頭 利用私鑰 解密 一對一 配對關係 私鑰 電子文件 明文 王上安的 公鑰憑證 公鑰 發證者名稱 有效日期 用戶名稱 用戶公鑰 …… CA簽章 22

什麼是 PKI? (1/2) n n n 雖然有完美的數學理論或是長久的實務驗證讓我們相信 公開金鑰密碼系統的各種演算法的安全性,然而 如果無 法確保「通訊雙方能夠正確地取得對方公開金鑰」這個前 提,則光有完美的密碼演算法是沒有用的 。 因此,除了密碼演算法的實作之外, 在實務上還需要建置 一些管理機制、設施、或服務等,以確保「通訊雙方能夠 正確地取得對方公開金鑰」這個前提可以實現 。 What is PKI? n 一言以蔽之,所謂「公開金鑰基礎建設( Public Key Infrastructure, PKI)」是一種支持公開金鑰密碼系統正 常運作的 Infrastructure,而所謂Infrastructure包含設備、 設施、服務、人員、法律、政策、規範等 美國NIST TWG-98 -59 23

什麼是 PKI? (2/2) n 觀念澄清:CA是公開金鑰基礎建設之核心,但 而是 PKI CA。 n 狹義的公開金鑰基礎建設 管理服務 。 n n PKI≠CA, 是指建置憑證機構提供 憑證 廣義的公開金鑰基礎建設 則是涵蓋 任何有助於公開金 鑰密碼系統運作的機制或設施 ,甚至於相關管理措施 或法規制度 都可以算是公開金鑰基礎建設的一環。 除了憑證機構提供的憑證管理服務之外,常見的其他 PKI服務有 憑證路徑建構服務 ( Certification Path Construction Service)、 憑證路徑驗證服務 ( Certification Path Validation Service)、 數位時戳服務 ( Digital Timestamp Service )、 資料驗證服務 ( Data Validation and Certification Service)等。 24
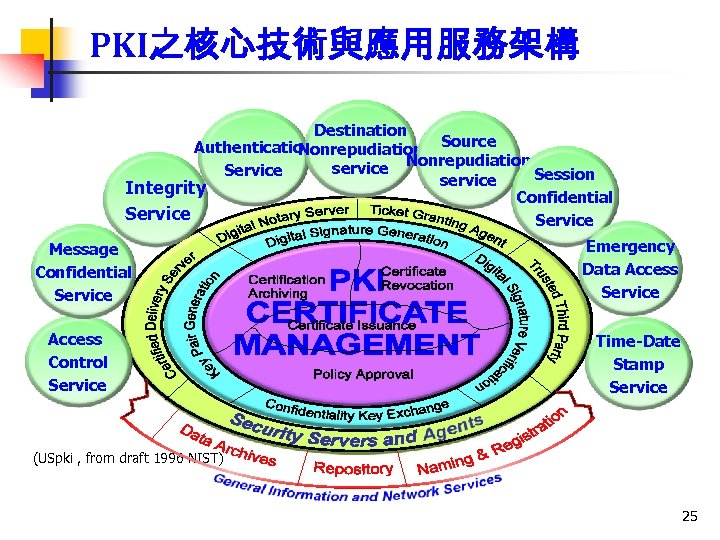
PKI之核心技術與應用服務架構 Destination Authentication Nonrepudiation Source service Nonrepudiation Session Service service Integrity Confidential Service Message Confidential Service Access Control Service Emergency Data Access Service Time-Date Stamp Service (USpki , from draft 1996 NIST) 25
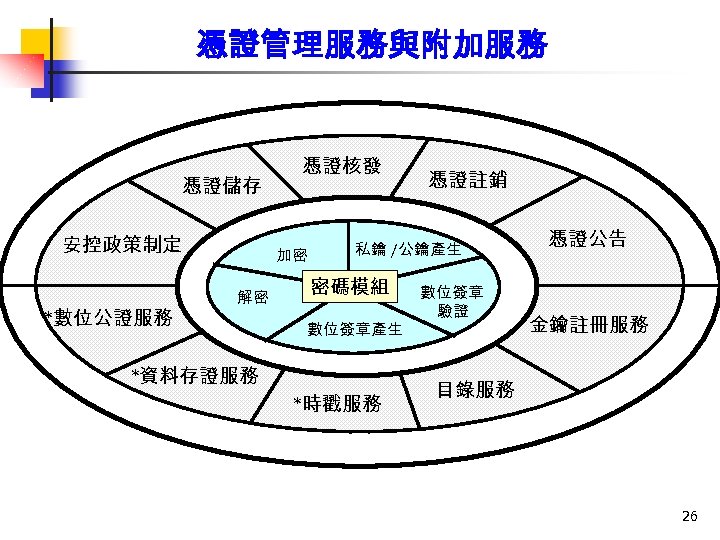
憑證管理服務與附加服務 憑證管理服務 憑證儲存 安控政策制定 *數位公證服務 憑證核發 加密 解密 憑證註銷 私鑰 /公鑰產生 密碼模組 數位簽章產生 *資料存證服務 *時戳服務 數位簽章 驗證 憑證公告 金鑰註冊服務 目錄服務 附加服務 26
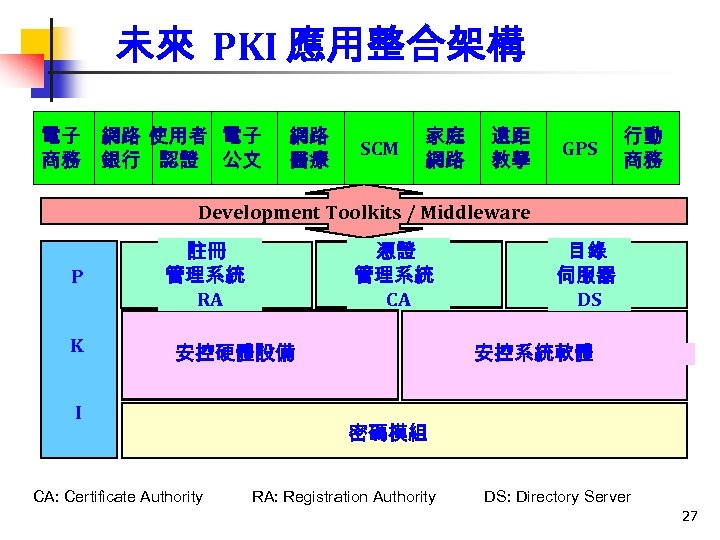
未來 PKI 應用整合架構 電子 網路 使用者 電子 商務 銀行 認證 公文 網路 醫療 SCM 家庭 網路 遠距 教學 GPS 行動 商務 Development Toolkits / Middleware P K 註冊 管理系統 RA 憑證 管理系統 CA 安控硬體設備 I CA: Certificate Authority 目錄 伺服器 DS 安控系統軟體 密碼模組 RA: Registration Authority DS: Directory Server 27
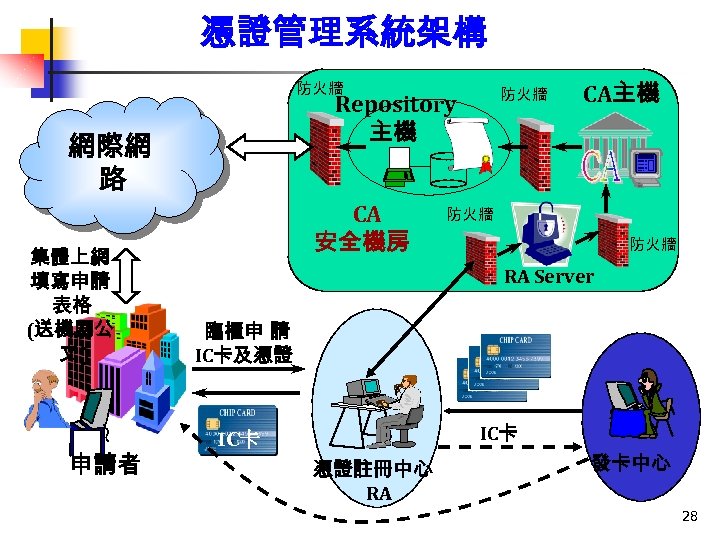
憑證管理系統架構 防火牆 網際網 路 集體上網 填寫申請 表格 (送機關公 文) 申請者 防火牆 Repository 主機 CA 安全機房 CA主機 防火牆 RA Server 臨櫃申 請 IC卡及憑證 IC卡 憑證註冊中心 RA 發卡中心 28
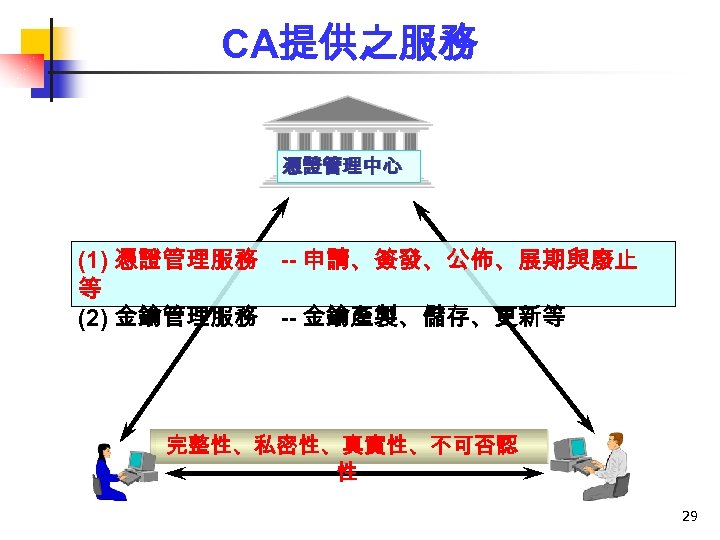
CA提供之服務 憑證管理中心 (1) 憑證管理服務 -- 申請、簽發、公佈、展期與廢止 等 (2) 金鑰管理服務 -- 金鑰產製、儲存、更新等 完整性、私密性、真實性、不可否認 性 29

PKI 之 相關子系統功能 30
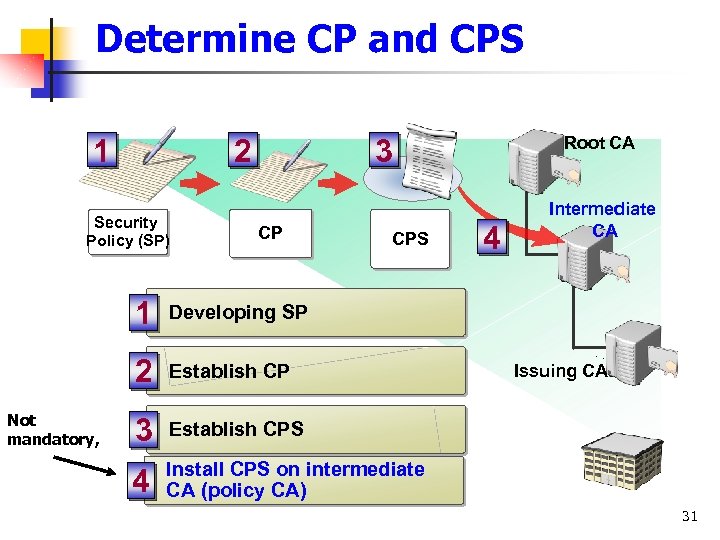
Determine CP and CPS 2 1 Security Policy (SP) 3 CP CPS 1 Not mandatory, Establish CP 3 Establish CPS 4 4 Intermediate CA Developing SP 2 Root CA Install CPS on intermediate CA (policy CA) Issuing CA 31
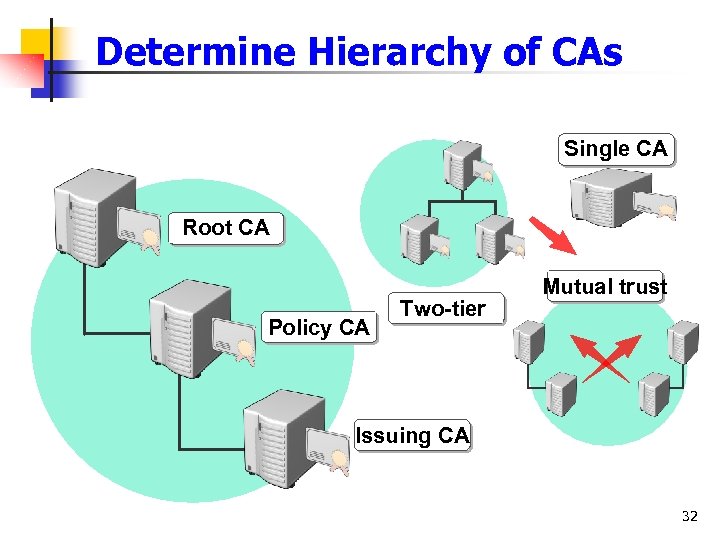
Determine Hierarchy of CAs Single CA Root CA Policy CA Two-tier Mutual trust Issuing CA 32
Planning by certificate applications Root CA Issuing CA S/MIME EFS IPSec/VPN 33
Planning by Area Root CA Issuing CA China Taiwan Your Country 34
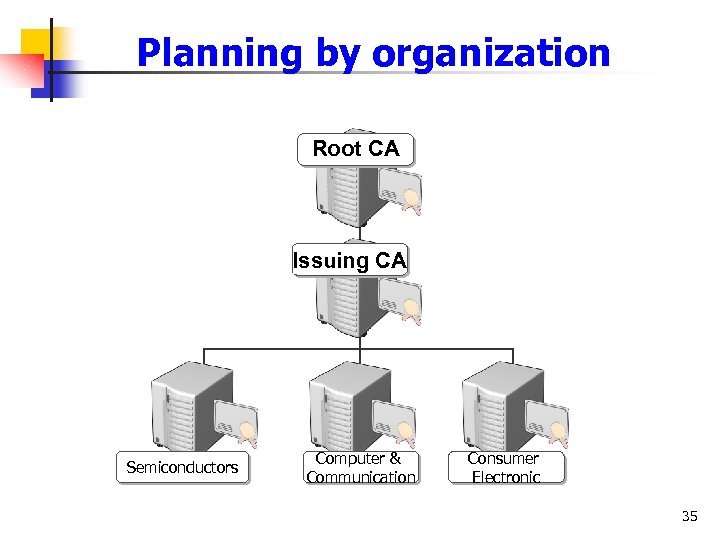
Planning by organization Root CA Issuing CA Semiconductors Computer & Communication Consumer Electronic 35
Choices of CA’s scale n n n Number of CAs depends on PKI hierarchy Multiple CAs can promote usability Reduction of unnecessary CAs may simplify key management and key recovery Efficiency of CAs will not be PKI’s primary consideration Size of a certificate is around 16 ~ 32 k 36
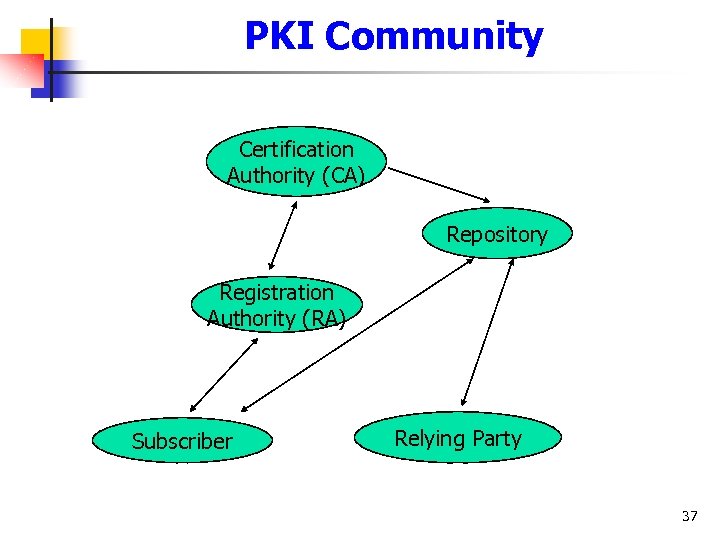
PKI Community Certification Authority (CA) Repository Registration Authority (RA) Subscriber Relying Party 37
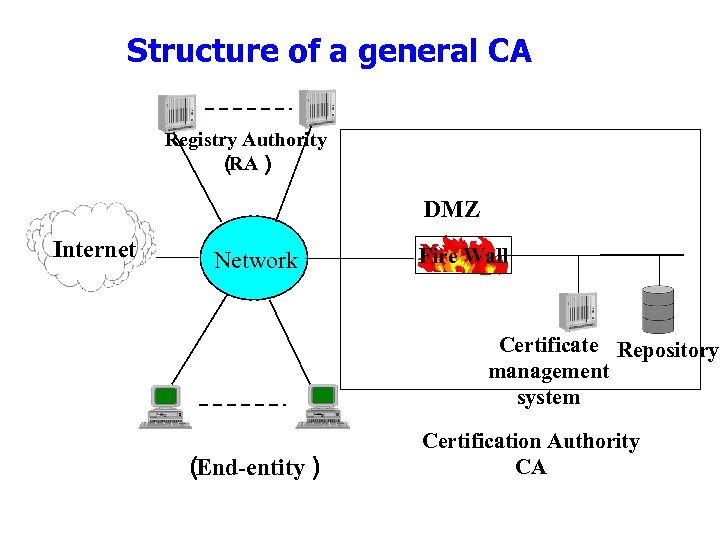
Structure of a general CA Registry Authority ( RA) DMZ Internet Network Fire Wall Certificate Repository management system ( End-entity) Certification Authority CA
End-entity n a public-key certificate (certificate) binds a public key held by an entity to a set of information that identifies the entity associated with use of the corresponding private key. n n n such as person, organization, account, device, or site this entity is known as the "subject" or "subscriber" of the certificate. Other types of certificates bind public keys to attributes of an entity other than the entity's identity, such as a role, a title, or creditworthiness information. 39

Relying party n n In summary, a relying party is an entity that uses a public key in a certificate (for signature verification and/or encryption). The degree to which a relying party can trust the binding embodied in a certificate depends on several factors. n n n the practices followed by the certification authority (CA) in authenticating the subject; the CA's operating policy, procedures, and security controls; the scope of the subscriber's responsibilities 40
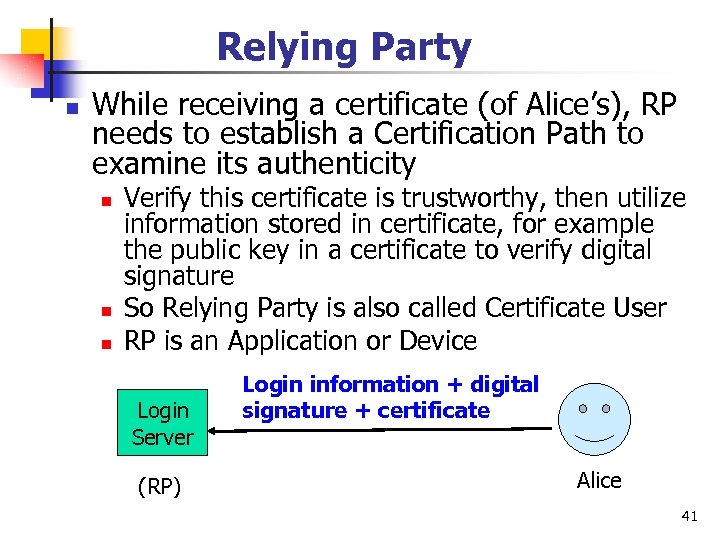
Relying Party n While receiving a certificate (of Alice’s), RP needs to establish a Certification Path to examine its authenticity n n n Verify this certificate is trustworthy, then utilize information stored in certificate, for example the public key in a certificate to verify digital signature So Relying Party is also called Certificate User RP is an Application or Device Login Server (RP) Login information + digital signature + certificate Alice 41

Repository n centralized database storing the following information n n Other tasks by repository n n n Public key certificate, CRL, Cross Certificate Pair (CCR) Related electronic forms for downloading CP and CPS publishing Updated information Tools downloading Q&A The repository publishes those information via Directory Server n n In general, some WWW website is the front end of the server end-entity may use browser to download the above information 42
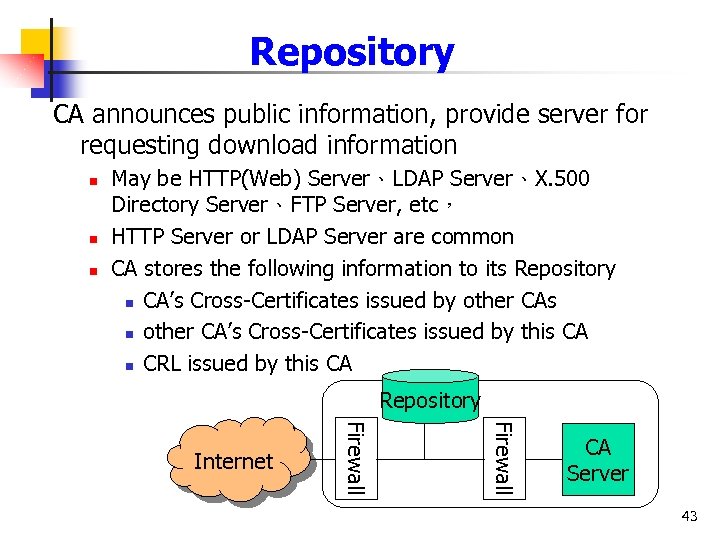
Repository CA announces public information, provide server for requesting download information n May be HTTP(Web) Server、LDAP Server、X. 500 Directory Server、FTP Server, etc, HTTP Server or LDAP Server are common CA stores the following information to its Repository n CA’s Cross-Certificates issued by other CAs n other CA’s Cross-Certificates issued by this CA n CRL issued by this CA Repository Firewall Internet CA Server 43

Certificate, Relying party n n n A certificate is used by a "certificate user" or "relying party" n rely upon the accuracy of the binding between the subject public key distributed via that certificate and the identity and/or other attributes of the subject contained in that certificate. A relying party is frequently an entity that verifies a digital signature from the certificate's subject n where the digital signature is associated with an email, web form, electronic document, or other data. Other examples of relying parties n a sender of encrypted email to the subscriber, n a user of a web browser relying on a server certificate during a secure sockets layer (SSL) session 44

Registration authority (RA) n n An entity that is responsible for identification and authentication of certificate subjects RA does not sign or issue certificates n n (i. e. , an RA is delegated certain tasks on behalf of a CA). RA operator (RAO) is an interface between subscribers and RA. n Usually residing at some counters, called RA counter (RAC). 45

What is a CP ? n n n A named set of rules that indicates the applicability of a certificate to a particular community and/or class of application with common security requirements. For example, a particular certificate policy might indicate applicability of a type of certificate to the authentication of electronic data interchange transactions for the trading of goods within a given price range. 46
Certificate Policy Examples n n International Air Transport Association (IATA) undertakes to define some certificate policies for use throughout the airline industry Two CPs might be defined n IATA General-Purpose CP n IATA Commercial-Grade CP. The IATA General-Purpose CP could be used by industry personnel n protecting routine information (e. g. , casual electronic mail) n authenticating connections from World Wide Web browsers to servers. The IATA Commercial-Grade CP could be used to protect financial transactions or binding contractual exchanges between airlines 47

Assurance Level: What CP has defined n n What is assurance? n Refer to statements and conduct of a CA to provide and maintain a specified level of service n Refer to the quality and security provided by a PKI, its certificates, and other designated data items, services and products Four levels of assurance n Rudimentary: The applicant may apply for a certificate via internet (e. g. , an e-mail) and the private key may exist in software/hardware n Basic: The applicant may apply in person via a trusted network n Medium: The applicant must appear in person before RA with proper identification information n High: The applicant must appear in person before RA with proper validation and the private key must exist in hardware 48

What is a CPS n Certificate Practice Statement n n n A more detailed description of the practices followed by a CA in issuing and otherwise managing certificates According to n n n published by or referenced by the CA. the American Bar Association Information Security Committee's Digital Signature Guidelines Information Security Committee's PKI Assessment Guidelines (PAG) a CPS is a statement of the practices which a certification authority employs in issuing certificates. 49

CPS and CA Operation Practice n n n In general, CPSs also describe practices relating to all certificate lifecycle services n issuance, management, revocation, and renewal or rekeying CPSs provide details concerning other business, legal, and technical matters. The terms contained in a CP or CPS may or may not be binding upon a PKI's participants as a contract. A CP or CPS may itself purport to be a contract. More commonly, however, an agreement may incorporate a CP or CPS by reference and therefore attempt to bind the parties of the agreement to some or all of its terms. 50
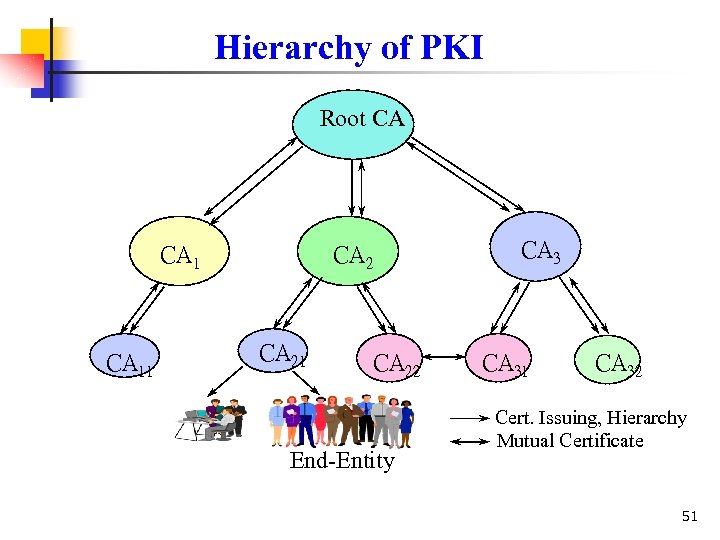
Hierarchy of PKI Root CA CA 11 CA 3 CA 21 CA 22 End-Entity CA 31 CA 32 Cert. Issuing, Hierarchy Mutual Certificate 51
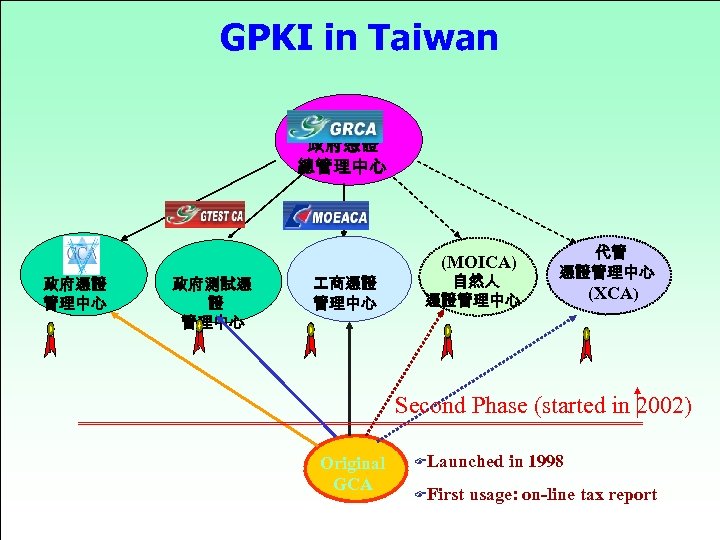
GPKI in Taiwan 政府憑證 總管理中心 (MOICA) 政府憑證 管理中心 政府測試憑 證 管理中心 商憑證 管理中心 自然人 憑證管理中心 代管 憑證管理中心 (XCA) Second Phase (started in 2002) Original GCA FLaunched FFirst in 1998 usage: on-line tax report

MOICA-CPS n n n We introduce MOICA-CPS to compare with RFC 3647 n Blue color to emphasize n Due to the time constraint, we point out important parts of MOICA-CPS MOI= Ministry of Interior The certificate issued by MOICA is called Citizen Digital Certificate 53
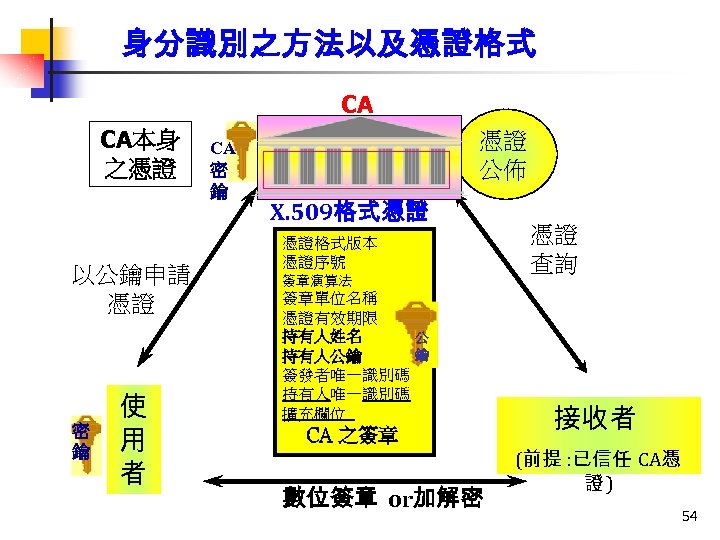
身分識別之方法以及憑證格式 CA CA本身 之憑證 以公鑰申請 憑證 密 鑰 使 用 者 CA 密 鑰 憑證 公佈 X. 509格式憑證 憑證格式版本 憑證序號 簽章演算法 簽章單位名稱 憑證有效期限 持有人姓名 公 鑰 持有人公鑰 簽發者唯一識別碼 持有人唯一識別碼 擴充欄位 CA 之簽章 數位簽章 or加解密 憑證 查詢 接收者 (前提 : 已信任 CA憑 證) 54
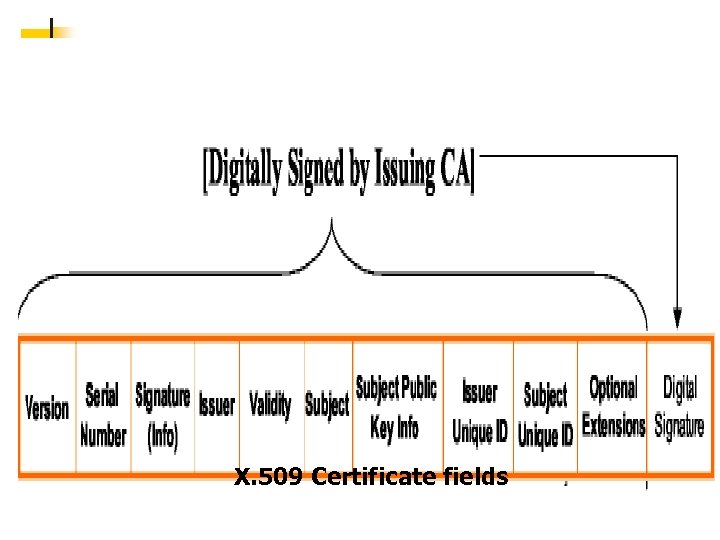
X. 509 Certificate fields 55
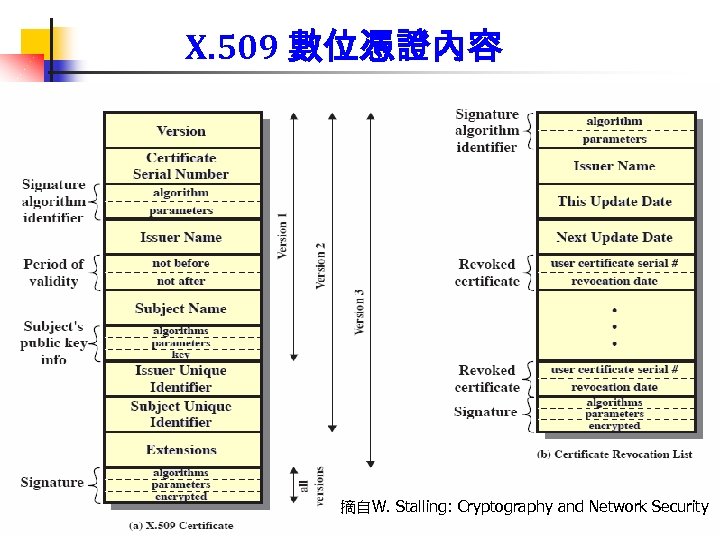
X. 509 數位憑證內容 56 摘自W. Stalling: Cryptography and Network Security 56
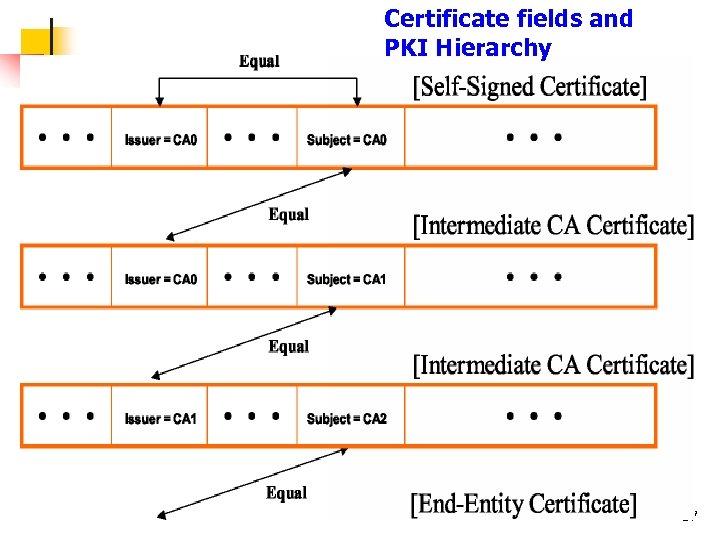
Certificate fields and PKI Hierarchy 57

CA建置維運相關技術標 準 與 實際建置維運 n (Based on RFC 3647 Examplified by MOICA-CPS) RFC 3647 : Internet X. 509 Public Key Infrastructure Certificate Policy and Certification Practices Framework 58

CPS structures (RFC 3647) n CPS consists of 8 chapters, according to RFC 3647 1. Introduction; 2. General Provisions; 3. Identification and Authentication; 4. Operational Requirements; 5. Physical, Procedural, and Personnel Security Controls; 6. Technical Security Controls; 7. Certificate and CRL Profile; and 8. Specification Administration. 憑證格式之標準為 X. 509 v 3 RFC 3280 : Internet X. 509 Public Key Infrastructure Certificate and Certificate Revocation List (CRL) Profile CPS :Certification Practice Statement 59

1 INTRODUCTION n n 1. 1 Overview n provides a general introduction to the specification. 1. 2 Identification n provides any applicable names or other identifiers, including ASN. 1 object identifiers, for the set of provisions. 1. 3 Community and Applicability n describes the types of entities that issue certificates or that are certified as subject CAs, the types of entities that perform RA functions. 1. 4 Contact Details n name and mailing address of the authority that is responsible for the registration, maintenance, and interpretation of this certificate policy or CPS. n name, electronic mail address, telephone number, and fax number of a contact person. 60

2. GENERAL PROVISIONS n n This component specifies any applicable presumptions on a range of legal and general practices topics. This component contains the following subcomponents: n Obligations n Liability n Financial Responsibility n Interpretation and Enforcement n Fees n Publication and Repositories n Compliance Audit n Confidentiality n Intellectual Property Rights. 61

2. 1 Responsibilities and obligations (MOICA-CPS) n n n n 2. 1. 1 Responsibilities of the Ministry of the Interior Certification Authority 2. 1. 2 Responsibilities of the registration authority 2. 1. 3 Responsibilities of the registration authority counter 2. 1. 4 Responsibilities of the card management authority 2. 1. 5 Obligation of the subscribers 2. 1. 6 Obligation of the relying parties 2. 1. 7 Obligation of the repository service 62

2. 2 Legal responsibility (MOICA-CPS) n n n 2. 2. 1 Responsibility of the Ministry of the Interior Certification Authority 2. 2. 2 Responsibility of the registration authority 2. 2. 3 Responsibility of the card management center 63

2. 3 Financial responsibility n n This operation of the authority shall be maintained by this Ministry that will compile budget and insurance is not conducted with insurance company. However, the audit authority shall conduct financial and accounting audit on our Ministry n other financial responsibility shall be processed based on the provision of related laws and regulations. 64

2. 4 Interpretation and execution (MOICA -CPS) n n n 2. 4. 1 Applicable law n Due to the execution of certificate issue and management operation requirement, for the explanation and legality of related agreements signed by this authority, it shall be processed according to the provision of related laws and regulations. 2. 4. 2 Divisible, existence and continuance, merger and public announcement notice n If any one chapter or section of this standard is incorrect or invalid, the other chapters and sections will still remain valid. 2. 4. 3 Dispute processing procedure n If there is dispute between the subscriber and this authority, both parties shall base on the principle of trust to conduct negotiation and discussion. n If the negotiation fails and litigation is required, the Taiwan Taipei District Court shall be the first trial jurisdictional court. 65

2. 5 Fees n n n 2. 5. 1 Certificate issue and exhibition fee 2. 5. 2 Certificate inquiry fee 2. 5. 3 Certificate revocation and status inquiry fee 2. 5. 4 Other service fee 2. 5. 5 Refund request provision n When the certification applying party applies for the certificate based on the provision of section 4. 2. 2 and if processing cannot be conducted based on provision, for the prepaid IC card handling fee, such party can present refund application at the counter. n It is required to deduct handling fee from the refund (20% handling fee of the IC card). For related provision, please go to website to inquire : http: //moica. nat. gov. tw/. 66

2. 6 Announcement and repository n n n 2. 6. 1 Information announcement by the Ministry of the Interior Certification Authority Certification policy 2. 6. 2 Announcement frequency 2. 6. 3 Access control n n n The mainframe of this authority is established inside the firewall and the outside cannot be connected on line with this mainframe directly. The depository mainframe shall be controlled and managed through the firewall system and will be directly connected to the database of the mainframe of this authority to retrieve certificate information or download certificate. 2. 6. 4 Repository n If normal operation cannot be conducted, within two working days, normal operation will be restored. The website of the repository is: http: //moica. nat. gov. tw. 67

2. 7 Audit method n n n 2. 7. 1 Audit frequency 2. 7. 2 Audit personnel identity and qualification 2. 7. 3 Relationship between the audit personnel and the party to be audited 2. 7. 4 Auditing area 2. 7. 5 Response method on the audit result 68

2. 8 Confidentiality Policy n addresses the following: n Types of information that must be kept confidential by CA or RA; n Types of information that are not considered confidential; n Who is entitled to be informed of reasons for revocation and suspension of certificates; Policy on release of information to law enforcement officials; n Information that can be revealed as part of civil discovery; Conditions upon which CA or RA may disclose upon owner's request; and n Any other circumstances under which confidential information may be disclosed. 69

3. Identification and Authentication 70

3. Identification and Authentication n n This component describes n the procedures used to authenticate a certificate applicant to a CA or RA prior to certificate issuance. n how parties requesting rekey or revocation are authenticated. n addresses naming practices, including name ownership recognition and name dispute resolution. This component has the following subcomponents: n Initial Registration; n Routine Rekey; n Rekey After Revocation; and n Revocation Request. 71
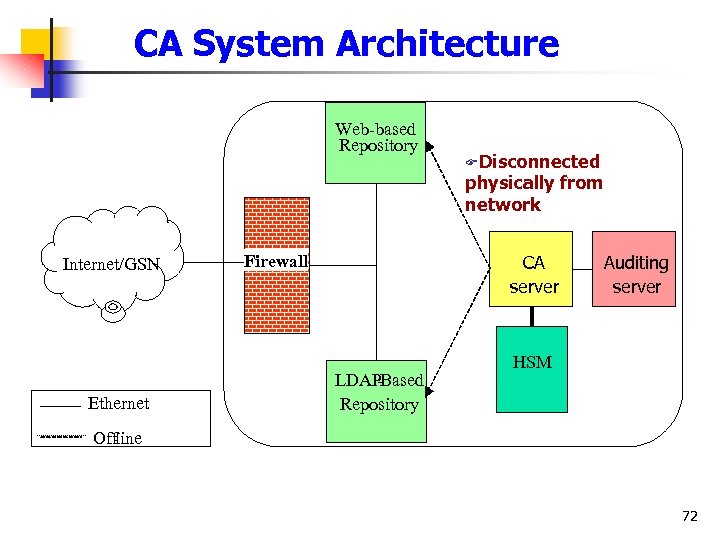
CA System Architecture Web-based Repository FDisconnected physically from network Internet/GSN Ethernet Firewall CA server LDAP -Based Repository Auditing server HSM Offline - 72
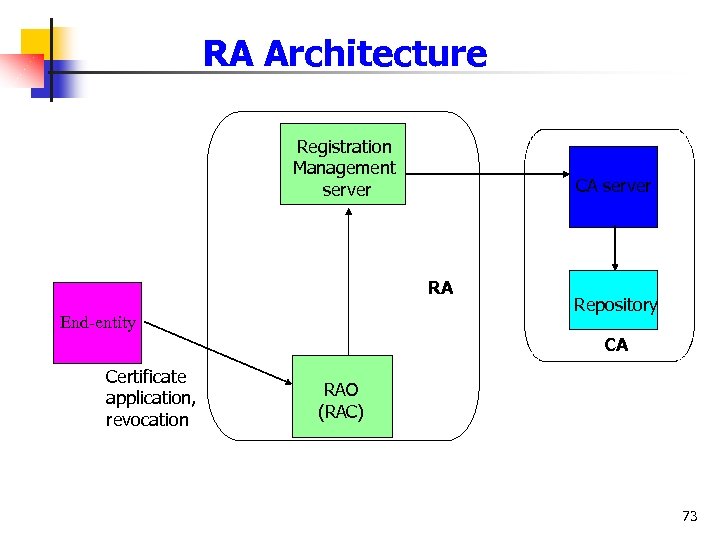
RA Architecture Registration Management server CA server RA End-entity Repository CA Certificate application, revocation RAO (RAC) 73
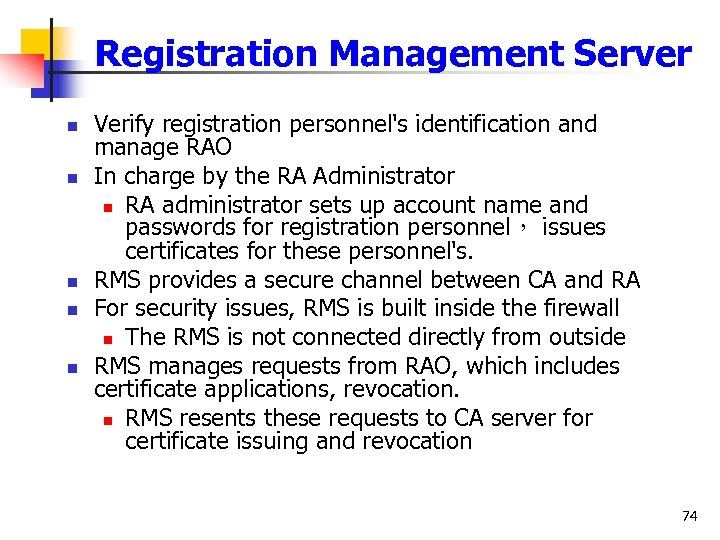
Registration Management Server n n n Verify registration personnel's identification and manage RAO In charge by the RA Administrator n RA administrator sets up account name and passwords for registration personnel, issues certificates for these personnel's. RMS provides a secure channel between CA and RA For security issues, RMS is built inside the firewall n The RMS is not connected directly from outside RMS manages requests from RAO, which includes certificate applications, revocation. n RMS resents these requests to CA server for certificate issuing and revocation 74

3. 1 Initial Registration n This subcomponent includes the following elements n Types of names assigned to the subject ; n Whether names have to be meaningful or not ; n Rules for interpreting various name forms; n Whether names have to be unique; n How name claim disputes are resolved; n Recognition, authentication, and role of trademarks; n If and how the subject must prove possession of the companion private key for the registered public key; n Authentication requirements for organizational identity of subject (CA, RA, or end entity); 75

3. 2 Routine Rekey n n This subcomponent describes the identification and authentication procedures for routine rekey for each subject type (CA, RA, and entity). 3. 3 Rekey After Revocation -- No Key Compromise n This subcomponent describes the identification and authentication procedures for rekey for each subject type (CA, RA, and entity) after the subject certificate has been revoked. 76

3. 2 Certificate key replacement or extension n n 3. 2. 1 Certificate key replacement n Certificate key replacement means the issue of a new certificate that has similar characteristics and guarantee etc. as the old certificate. n For the new certificate, except that it has new and different public key (compared with the new one, different private key) and different serial. Number, it may be assigned with different validity time limit. n If the utilization period of private key of the subscriber is due and is required to replace the key, the subscriber should reapply for certificate with this authority. 3. 2. 2 Certificate extension n extension on the issued certificate is not permitted in order to maintain the safety of the key. 77

3. 3 Certificate revocation key replacement n n If the private key of the subscriber needs to be replaced due to certificate revocation, it is required to reapply for certificate with this authority. The registration authority counter will base on the provision of section 3. 1 to conduct identification and authentication on the subscriber reapplying for the certificate. 78

3. 4 Certificate revocation The authentication procedure of the certificate revocation application is similar to the provision of section 3. 1. 3. 5 Certificate content alteration (Section added) n The authentication procedure of the certificate content alteration application is similar to the provision of section 3. 1. n 79

4. OPERATIONAL REQUIREMENTS 80

What is operational requirements ? n This component is used to specify requirements imposed upon issuing CA, subject CAs, RAs, or end entities with respect to various operational activities: n Certificate Application; n Certificate Issuance; n Certificate Acceptance; n Certificate Suspension and Revocation; n Security Audit Procedures; n Records Archival; n Key Changeover; n Compromise and Disaster Recovery n CA Termination. 81
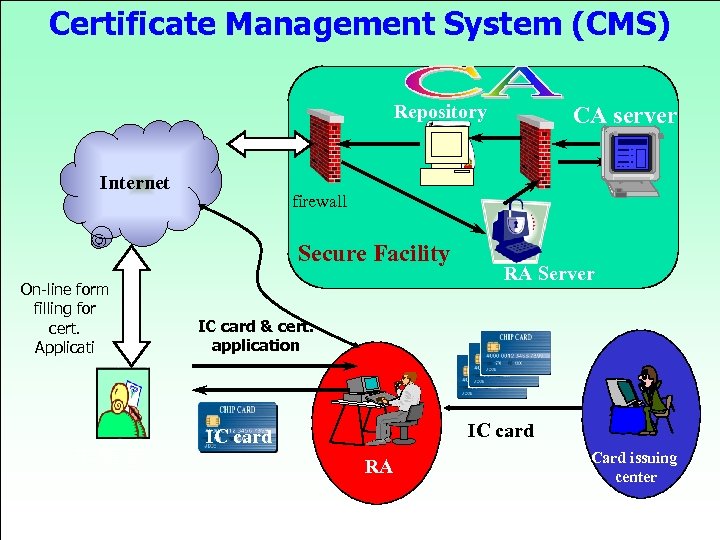
Certificate Management System (CMS) Repository Internet firewall Secure Facility On-line form filling for cert. Applicati 申請者 CA server RA Server IC card & cert. application IC card RA Card issuing center 82

4. 1~4. 3 How to get a Certificate l l l 4. 2 Certificate Application n to state requirements regarding subject enrollment and request for certificate issuance. 4. 2 Certificate Issuance n to state requirements regarding issuance of a certificate and notification to the applicant of such issuance. 4. 3 Certificate Acceptance n to state requirements regarding acceptance of an issued certificate and for consequent publication of certificates. 83

4. 4 Certificate temporary suspension and revocation n n n 4. 4. 1 Cause of certificate revocation 4. 4. 2 Certificate revocation applying person 4. 4. 3 Certificate revocation procedure 4. 4. 4 Certificate revocation application processing period 4. 4. 5 Cause of temporary suspension of certificate 4. 4. 6 Certificate temporary suspension applicant 4. 4. 7 Certificate temporary suspension procedure 4. 4. 8 Certificate temporary suspension processing period and suspension period 4. 4. 9 Certificate revocation list issue frequency 4. 4. 10 Certificate revocation list examination rules 4. 4. 11 On-line certification status inquiry service 4. 4. 12 On-line certification status inquiry provision 4. 4. 13 Other revocation announcement form 4. 4. 14 Other revocation form announcement inspection provision 4. 4. 15 Other special provision when the key is compromised 84

4. 4. 1 Cause of certificate revocation n Under the following conditions, the subscriber shall present certificate revocation application with the registration authority counter: n When there is doubt or confirmation that the private key is being compromised. n There is major alteration on the information recorded in the certificate that can affect its reliability. n n For example, the name of the subscriber has been altered. Utilization of the certificate is no longer required. 85

4. 5 Security Audit Procedures n n describe event logging and audit systems Purpose: maintaining a secure environment. n n n n Types of events recorded; Frequency with which audit logs are processed or audited; Period for which audit logs are kept; Protection of audit logs: n Who can view audit logs; Protection against modification of audit log; Protection against deletion of audit log. Audit log back up procedures; Whether the audit log accumulation system is internal or external to the entity; Whether the subject who caused an audit event to occur is notified of the audit action; Vulnerability assessments. 86
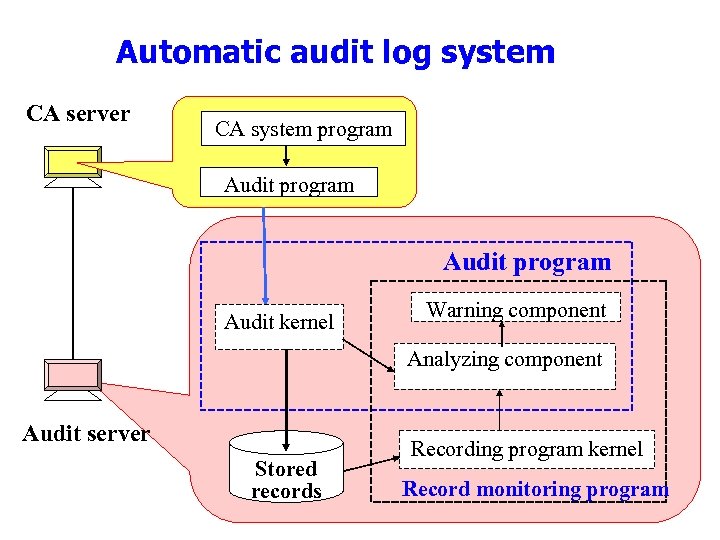
Automatic audit log system CA server CA system program Audit kernel Warning component Analyzing component Audit server Stored records Recording program kernel Record monitoring program
Audit Log and Security Audit procedures n Audit server records Audit Trails from CA server. n n n According to security policy, CA server transfers auditable events to audit server for auditor’s inspection. Every security related event is produced as an audit log. Audit logs can be produced automatically, if needed, but not necessarily. Every audit log is kept for auditing. Audit logs are protected by digital signatures Archived audit logs are encrypted. 88

4. 5 Safety audit procedure n n n n 4. 5. 1 Recorded event category 4. 5. 2 Record file processing frequency 4. 5. 3 Audit log file custodian period 4. 5. 4 Audit log file protection 4. 5. 5 Audit log file back up procedure 4. 5. 6 Safety audit system 4. 5. 7 Advice on the incident 4. 5. 8 Weak point evaluation 89

4. 6 Records Archival n to describe general records archival (or records retention) policies, including the following: n Types of events recorded; n Retention period for archive; n Protection of archive: n Who can view the archive; n Protection against modification of archive; and Protection against deletion of archive. n Archive backup procedures; n Requirements for time-stamping of records; n Whether the archive collection system is internal or external; n Procedures to obtain and verify archive information. 90

4. 7 Key replacement n Private key of this authority will be replaced periodically based on the provision of section 6. 3. 2. Two months before the certificate is due, this authority will replace the key pair used to issue certificate. n n After the key pair is replaced, the authority will apply for new certificate with the government certificate management center. Private key of the subscriber has to be replaced periodically based on the provision of section 6. 3. 2. n If the utilization period of the private key of the subscriber is expired and replacement of key is required, it is necessary to apply for new certificate with this authority based on the provision of section 4. 1. 91

4. 8 Recovery procedure when the key is being compromised or during disaster (1) n 4. 8. 1 Computer resource, software or information damage recovery procedure n n This authority stipulates the recovery procedure of computer resource, software and when information is being damaged and at the same time, exercise will be conducted every year. If the computer equipment of this authority is being damaged or cannot be operated but the signature key of this authority has not yet been destroyed, then it is a priority to recover the operation of the repository of this authority and rebuild the ability of certificate issue and management as soon as possible. 92

4. 8 Recovery procedure when the key is being compromised or during disaster (2) n n n 4. 8. 2 Recovery procedure for the revocation of signature key certificate of the Ministry of the Interior Certification Authority 4. 8. 3 Recovery procedure when the signature key certificate of the Ministry of the Interior Certification Authority is compromised 4. 8. 4 Recovery work after the disaster of safety facilities of the Ministry of the Interior Certification Authority 93

5. PHYSICAL, PROCEDURAL, AND PERSONNEL SECURITY CONTROLS 94

5. PHYSICAL, PROCEDURAL, AND PERSONNEL SECURITY CONTROLS n n This component describes non-technical security controls used by the issuing CA to perform securely the functions of key generation, subject authentication, certificate issuance, certificate revocation, audit, and archival. This component can also be used to define non-technical security controls on repository, subject CAs, RAs, and entities. The nontechnical security controls for the subject CAs, RAs, and entities could be the same, similar, or very different. These non-technical security controls are critical to trusting the certificates since lack of security may compromise CA operations resulting n n for example, in the creation of certificates or CRLs with erroneous information or the compromise of the CA private key. This component consists of three subcomponents: n Physical Security Controls; n Procedural Controls; and n Personnel Security Controls. 95
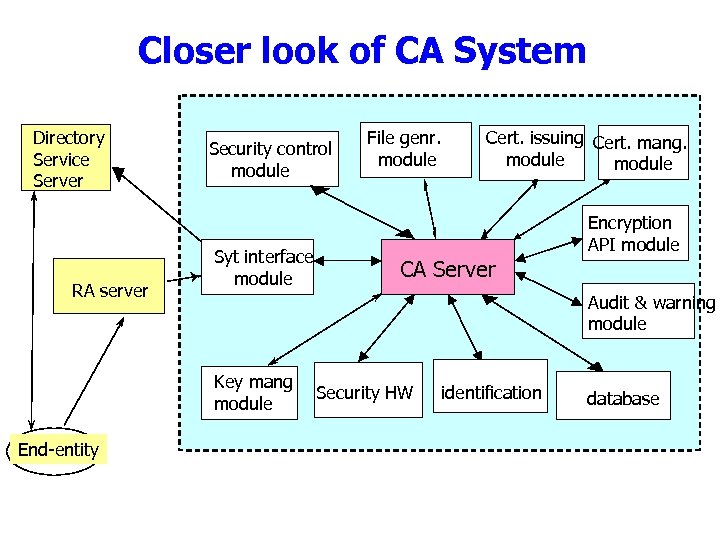
Closer look of CA System Directory Service Server RA server Security control module Syt interface module Cert. issuing Cert. mang. module Encryption API module CA Server Audit & warning module Key mang module End-entity File genr. module Security HW identification database

5. 1 Physical Security Controls n n The physical controls on the facility housing the entity systems are described. Topics addressed may include: n Site location and construction; n Physical access; n Power and air conditioning; n Water exposures; n Fire prevention and protection; n Media storage; n Waste disposal; n Off-site backup. 97

5. 1 Substance control n n n n 5. 1. 1 Substance location and structure 5. 1. 2 Substance access 5. 1. 3 Power and ventilation 5. 1. 4 Flood prevention and protection 5. 1. 5 Fire prevention and protection 5. 1. 6 Media storage 5. 1. 7 Waste handling 5. 1. 8 Different place backup 98

CA Facility security n n n Secure & reliable facility n Secure facility CHT Data Comm. Company (CHT-D) n Independent space Entrance control n Security personnel located at the Building entrance and each floor n For highly secure area: additional fingerprint check for gate entrance Theft-preventing system n authorized magnet card to open the machines n Infra-red detection for invasion n Video-surveillance system 99

CA Facility security n n n Disaster-preventing system n Fire detection and alert n Fire prevention and fire-fighting apparatus n Static electricity prevention Air condition facility n centralized AC and constant temperature control n Temperature abnormality alert system Electricity n 7 -day nonstop electricity providing system 100

5. 2 Procedure control (1) n n to specify various trusted roles in the execution of related operation number of people required for each job the identification and authentication of each role 5. 2. 1 Trusted role n This authority has five different types of trusted roles that are n Administrator n Officer n Auditor n operation n controller 101

5. 2 Procedure control (2) n 5. 2. 2 Role allocation n n The three types of trusted roles including the administrator, officer and auditor cannot be undertaken concurrently. However, they can be operator concurrently. The controller cannot take up other four types of roles concurrently. Any one type of trusted role is not permitted to execute selfaudit function. 5. 2. 3 Number of persons required for each mission n n Administrator : at least to be undertaken by three qualified persons. Officer: at least to be undertaken by three qualified persons. Auditor: at least to be undertaken by two qualified persons. Operator: at least to be undertaken by two qualified persons. Controller: at least to be undertaken by three qualified persons. 102

5. 3 Personnel control n n n n 5. 3. 1 Family background, qualification, experience and safety requirement 5. 3. 2 Family background examination procedure 5. 3. 3 Education training requirement 5. 3. 4 Personnel re-education training requirement and frequency 5. 3. 5 Work transfer frequency and sequence 5. 3. 6 Suppression of unauthorized action 5. 3. 7 Personnel employment provision 5. 3. 8 Provided documentary information 103

6. TECHNICAL SECURITY CONTROLS 104

6. TECHNICAL SECURITY CONTROLS n This component has the following subcomponents: n n n n Key Pair Generation and Installation; Private Key Protection; Other Aspects of Key Pair Management; Activation Data; Computer Security Controls; Life-Cycle Security Controls; Network Security Controls; and Cryptographic Module Engineering Controls. 105

6. 1 Key Pair Generation and Installation n n n n Who generates the entity public, private key pair? How is the private key provided securely to the entity? How is the entity's public key provided securely to the certificate issuer? If the entity is a CA (issuing or subject) how is the entity's public key provided securely to the users? 5. What are the key sizes? 6. Who generates the public key parameters? 7. quality of the parameters during key generation? 8. key generation performed in hardware or software? 9. purposes the key be used, or for what purposes should usage of the key be restricted 106
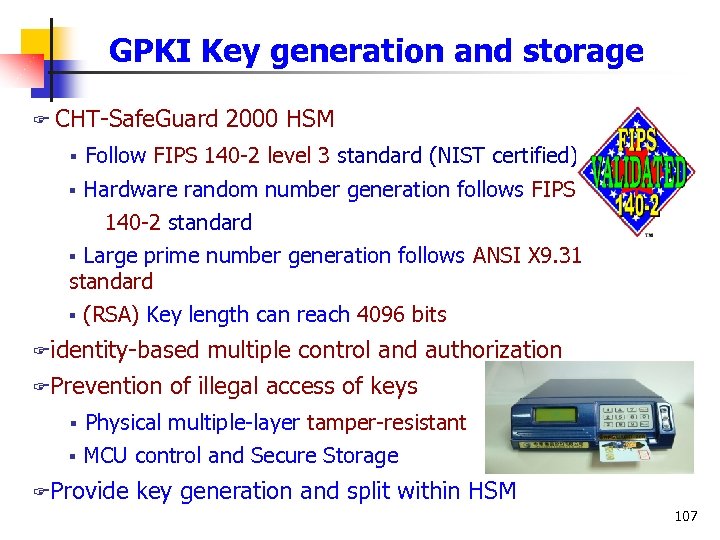
GPKI Key generation and storage F CHT-Safe. Guard 2000 HSM § Follow FIPS 140 -2 level 3 standard (NIST certified) § Hardware random number generation follows FIPS 140 -2 standard § Large prime number generation follows ANSI X 9. 31 standard § (RSA) Key length can reach 4096 bits Fidentity-based multiple control and authorization FPrevention of illegal access of keys § Physical multiple-layer tamper-resistant § MCU control and Secure Storage FProvide key generation and split within HSM 107
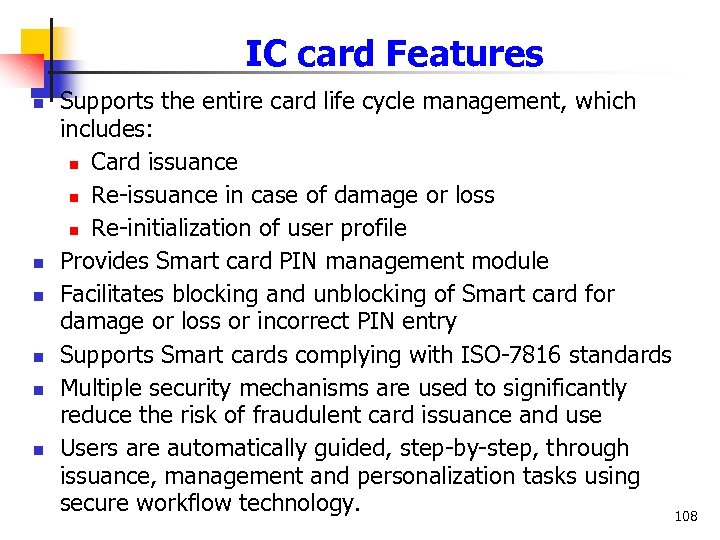
IC card Features n n n Supports the entire card life cycle management, which includes: n Card issuance n Re-issuance in case of damage or loss n Re-initialization of user profile Provides Smart card PIN management module Facilitates blocking and unblocking of Smart card for damage or loss or incorrect PIN entry Supports Smart cards complying with ISO-7816 standards Multiple security mechanisms are used to significantly reduce the risk of fraudulent card issuance and use Users are automatically guided, step-by-step, through issuance, management and personalization tasks using secure workflow technology. 108

6. 1 Key pair production and installation n 6. 1. 1 Key pair production n Based on section 6. 2. 1, this authority will produce key pair within the software cryptographic module and will adopt true random number generator and RSA key calculation method. After the production of private key within the hardware cryptographic module, it will be stored there all along and will not be leaked out. n For the production of the key of this authority, under witness by the Electronic Certification Steering Group Member of this Ministry and related personnel, it will be conducted by multiple person safety control system. n The token utilized by the subscriber is IC card. For its key pair, after the card management center has driven the IC with the safety control system, it will be produced on its own within the IC card. 109

6. 1 Key pair production and installation (2) n n n n 6. 1. 2 Safety transmission of private key to subscriber n After this authority has issued the certificate, the RAO will hand over the IC card stored with the private key to the subscriber. 6. 1. 3 Safety transmission of public key to the Ministry of Interior Certification Authority 6. 1. 4 Safety transmission of public key of the Ministry of Interior Certification Authority to relying parties 6. 1. 5 Key length n This authority utilizes 2048 bits RSA key and SHA-1 mixed function calculation method to issue certificate and subscribers utilizes 1024 bits RSA key. 6. 1. 6 Key parameter production 6. 1. 7 Key parameter quality inspection 6. 1. 8 Key produced through software or hardware 6. 1. 9 Key utilization purpose 110

6. 2 Private key protection n 6. 2. 1 Key module standard n n n 6. 2. 2 Key separate possession control and management by multiple persons n n In order to conform to the provision of certification policy section 6. 2. 1 assurance level 3, this authority utilizes safety level 3 standalone hardware cryptographic module. The subscriber utilizes safety level 2 IC card hardware cryptographic module. The multiple person control adopts Secret Sharing m-out-of-n . 6. 2. 3 Private key escrow n n The signature private key of this authority cannot be escrowed. this authority is not responsible for keeping the signature private key of subscriber. 111

6. 2 Private key protection (2) n n n 6. 2. 4 Private key back up n The multiple person control method of key separate holding in section 6. 2. 2 is utilized to make back up of private key and the IC card with high safety and is utilized as the storage media of secret separate holding. 6. 2. 5 Private key archive n This signature secret key of this authority cannot be archived. n This authority will not conduct archive on the signature private key of subscribers. 6. 2. 6 Input of private key to cryptographic module 6. 2. 7 Private key activation method n The activation of the RSA private key of this authority is based on the m-out-of-n control IC card group to conduct control. 6. 2. 8 Private key suspension method 6. 2. 9 Private key destruction method 112

6. 3 Other Aspects of Key Pair Management n n Is the public key archived? If so, who is the archival agent and what are the security controls on the archival system? The archival system should provide integrity controls other than digital signatures n n n the archival period may be greater than the cryptanalysis period for the key archive requires tamper protection, which is not provided by digital signatures. What are the usage periods, or active lifetimes, for the public and the private key respectively? 113

6. 3 Other provision of management on subscriber’s key n n n 6. 3. 1 Archive of public key n This authority will conduct archive of certificates and will execute safety control of archive system based on the provision of section 4. 6 and will not conduct archive of public key separately. 6. 3. 2 Utilization time limit of public key and private key n 6. 3. 3. 1 Utilization time limit of the public key and private key of the Ministry of the Interior Certification Authority n The key length of the public and private key is RSA 2048 bits. n The maximum utilization time limit of public key certificate is twenty years; ten years for private key 6. 3. 3. 2 Utilization time limit of the public key and private key of subscriber n The key length of the public key and private key of subscribe is RSA 1024 bits. n The maximum utilization time limit of public key certificate is five years and five years for private key. 114
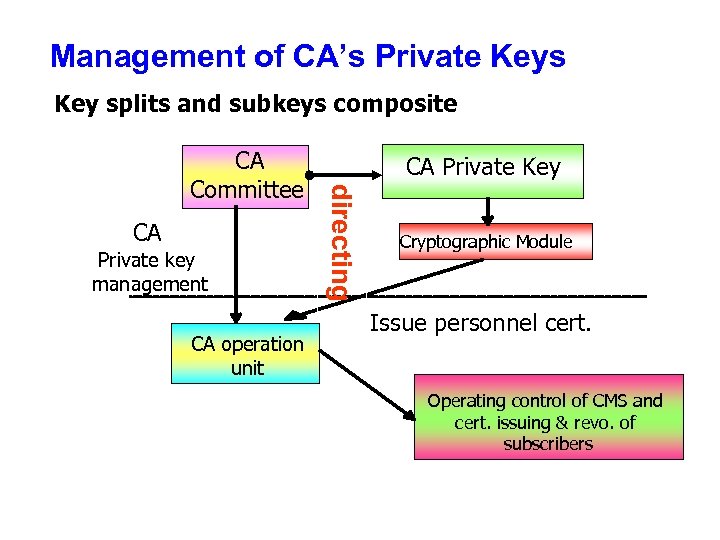
Management of CA’s Private Keys Key splits and subkeys composite CA Private key management CA operation unit CA Private Key directing CA Committee Cryptographic Module Issue personnel cert. Operating control of CMS and cert. issuing & revo. of subscribers

6. 4 Activation Data n n n Activation data refers to data values other than keys that are required to operate cryptographic modules and that need to be protected. Such consideration potentially needs to address the entire life-cycle of the activation data from generation through archival and destruction. For each of the entity types (issuing CA, repository, subject CA, RA, and entity), all of the questions listed in 6. 1 through 6. 3 potentially need to be answered with respect to activation data rather than with respect to keys. 116

6. 5 Computer Security Controls n n describe computer security controls such as n use of the trusted computing base concept, n discretionary access control, labels, mandatory access controls, object reuse, audit, n identification and authentication, trusted path, security testing, and penetration testing. n Product assurance may also be addressed. A computer security rating for computer systems may be required. n The rating could be based on the Trusted System Evaluation Criteria (TCSEC), Canadian Trusted Products Evaluation Criteria, European Information Technology Security Evaluation Criteria (ITSEC), or the Common Criteria. 117

6. 5 Computer software and hardware safety control measures n n 6. 5. 1 Specific computer safety technology requirement n Possesses identity authentication log in. n Provides discretionary access control. n Provides safety audit ability. n Restraints on various types of certification service and trusted role access control. n Possesses identification and authentication of trusted role and identity. n Possesses safe and reliable channels of trusted role and related identity role. n Possesses procedure integrity and safety control protection. 6. 5. 2 Computer safety rating n This authority adopts safety strength and computer operation system equivalent to TCSEC. 118

6. 6 Life Cycle Security Controls n This subcomponent can also address life-cycle security ratings based on n the Trusted Software Development Methodology (TSDM) level IV and V, independent life-cycle security controls audit the Software Engineering Institute's Capability Maturity Model (SEI-CMM). 6. 7 Network Security Controls n This subcomponent addresses network security related controls, including firewalls. 119

6. 8 Cryptographic Module Engineering Controls n n addresses the following aspects of a cryptographic module: n identification of the cryptographic module boundary, n input/output n roles and services n finite state machine n physical security n software security n operating system security n Algorithm compliance n electromagnetic compatibility n self tests. Requirements may be expressed through reference to a standard such as U. S. FIPS 140 -2 (or FIPS-140 -3). 120

7. CERTIFICATE AND CRL PROFILES 8. SPECIFICATION ADMINISTRATION 121

7 CERTIFICATE AND CRL PROFILES n n n This component is used to specify the X. 509 certificate format and, the CRL format. This includes information on profiles, versions, and extensions used. This component has two subcomponents: n Certificate Profile n CRL Profile. 122
7. 1 Certificate Profile n This subcomponent addresses such topics as the following (potentially by reference to a separate profile definition, such as the PKIX Part I profile): n Version number(s) supported; n Certificate extensions populated and their criticality; n Cryptographic algorithm object identifiers; n Name forms used for the CA, RA, and entity names; n Name constraints used and the name forms used in the name constraints; n Applicable certificate policy Object Identifier(s); n Usage of the policy constraints extension; n Policy qualifiers syntax and semantics; and n Processing semantics for the critical certificate policy extension. 123

7. 2 CRL Profile n This subcomponent addresses such topics as the following: n Version numbers supported for CRLs; n CRL and CRL entry extensions populated and their criticality. 124

8. SPECIFICATION ADMINISTRATION n n This component is used to specify how this particular certificate policy definition or CPS will be maintained. It contains the following subcomponents: n n n Specification Change Procedures; Publication and Notification Procedures; and CPS Approval Procedures. 125

Important Issue with CA Operation: Certificate validation 126
Public Key Certificate Verification n n Public Key Certificate n Bind a public key to the owner’s identity information n Digitally signed and certified by a trusted certificate authority(CA) Certificates Revocation n Compromising of the key or abuse of the owner n n n Certificates Revocation List (CRL) Online Certificate Status Protocol (OCSP) Certificate verification n Applications need to verify the certificate status n OCSP and CRL are two mechanisms 127
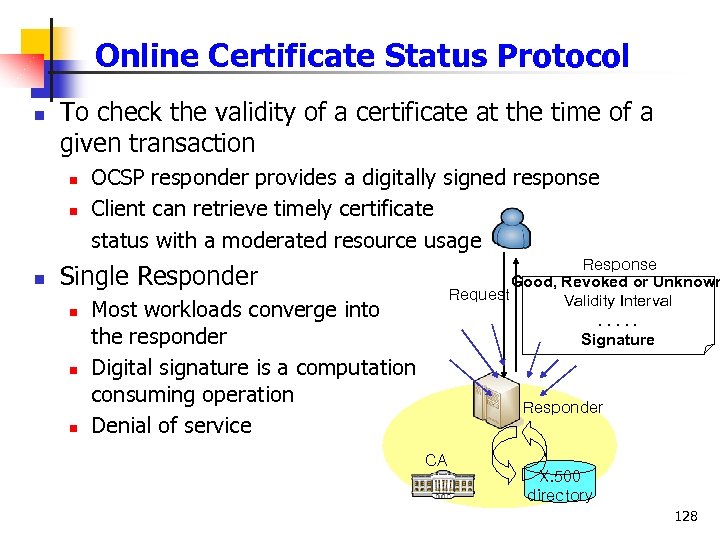
Online Certificate Status Protocol n To check the validity of a certificate at the time of a given transaction n OCSP responder provides a digitally signed response Client can retrieve timely certificate status with a moderated resource usage Response Good, Revoked or Unknown Request Validity Interval. . . Signature Single Responder n n n Most workloads converge into the responder Digital signature is a computation consuming operation Denial of service Responder CA X. 500 directory 128
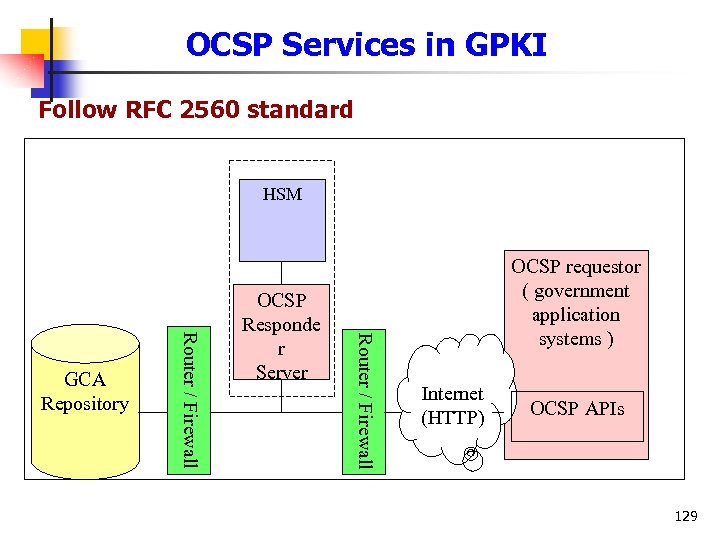
OCSP Services in GPKI Follow RFC 2560 standard HSM Router / Firewall GCA Repository OCSP Responde r Server OCSP requestor ( government application systems ) Internet (HTTP) OCSP APIs 129

憑證之驗證 作 1. 驗證憑證是否由可信賴之 CA所簽發 Ø 驗證憑證的 CA簽章是否正確 2. 檢查憑證是否仍在有效期限內。 3. 檢查憑證是否已被註銷。 (CRL或 OCSP) Ø CRL: Certificate Revocation List(定期發佈 ) Ø OCSP: Online Certificate Status Protocol(隨時查 詢) 130
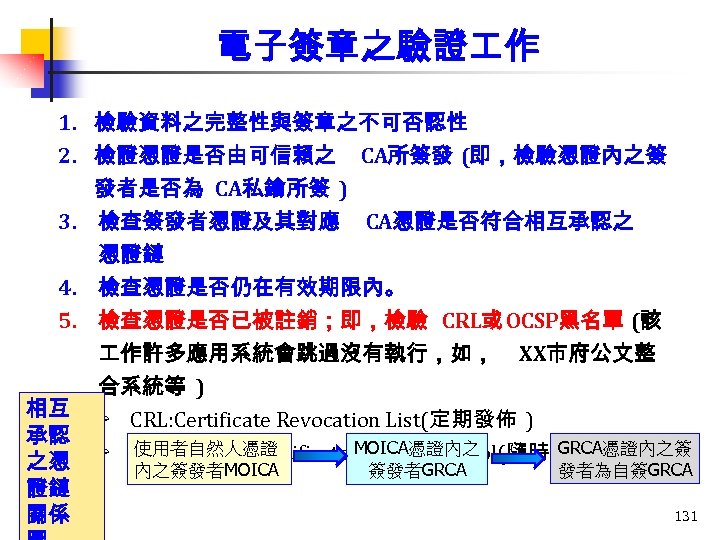
電子簽章之驗證 作 1. 檢驗資料之完整性與簽章之不可否認性 2. 檢證憑證是否由可信賴之 CA所簽發 (即,檢驗憑證內之簽 發者是否為 CA私鑰所簽 ) 3. 檢查簽發者憑證及其對應 CA憑證是否符合相互承認之 憑證鏈 4. 檢查憑證是否仍在有效期限內。 5. 檢查憑證是否已被註銷;即,檢驗 CRL或 OCSP黑名單 (該 作許多應用系統會跳過沒有執行,如, XX市府公文整 合系統等 ) 相互 Ø CRL: Certificate Revocation List(定期發佈 ) 承認 使用者自然人憑證 GRCA憑證內之簽 Ø OCSP: Online Certificate MOICA憑證內之 Status Protocol(隨時查詢 ) 之憑 證鏈 關係 內之簽發者MOICA 簽發者GRCA 發者為自簽GRCA 131

資訊技術安全評估共同準則 l「資訊技術安全評估準則」 (ITSEC, Information Technology Security Evaluation Criteria) : 1991年英、美、 法、德這些國家共同公佈。 l「資訊技術安全評估共通準則」 (CCITSE, Common Criteria for Information Technology Security Evaluation) : 1995年美國、加拿大、英國、法國、德國、及荷蘭制訂。 l國際標準組織 (ISO)於 1998年根據 CCITSE 修 訂 為 ISO/IEC 15408的資訊安全技術國際標準 ;即俗稱的 Common Criteria(共通準則) 。 132
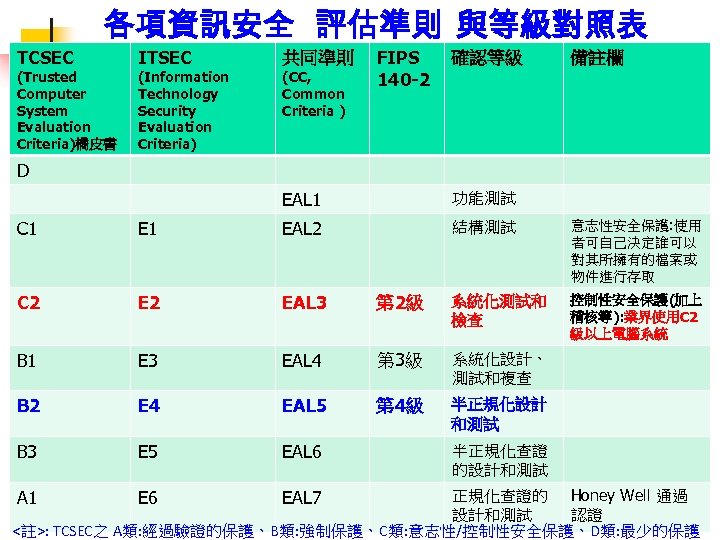
各項資訊安全 評估準則 與等級對照表 TCSEC (Trusted Computer System Evaluation Criteria)橘皮書 ITSEC (Information Technology Security Evaluation Criteria) 共同準則 (CC, Common Criteria ) FIPS 140 -2 確認等級 備註欄 D EAL 1 功能測試 結構測試 意志性安全保護: 使用 者可自己決定誰可以 對其所擁有的檔案或 物件進行存取 控制性安全保護(加上 稽核等): 業界使用C 2 級以上電腦系統 C 1 EAL 2 C 2 EAL 3 第 2級 系統化測試和 檢查 B 1 E 3 EAL 4 第 3級 系統化設計、 測試和複查 B 2 E 4 EAL 5 第 4級 半正規化設計 和測試 B 3 E 5 EAL 6 半正規化查證 的設計和測試 正規化查證的 Honey Well 通過 設計和測試 認證 133 <註>: TCSEC之 A類: 經過驗證的保護、B類: 強制保護、C類: 意志性/控制性安全保護、D類: 最少的保護 A 1 E 6 EAL 7

GCA系統 之 實際建置過程 134
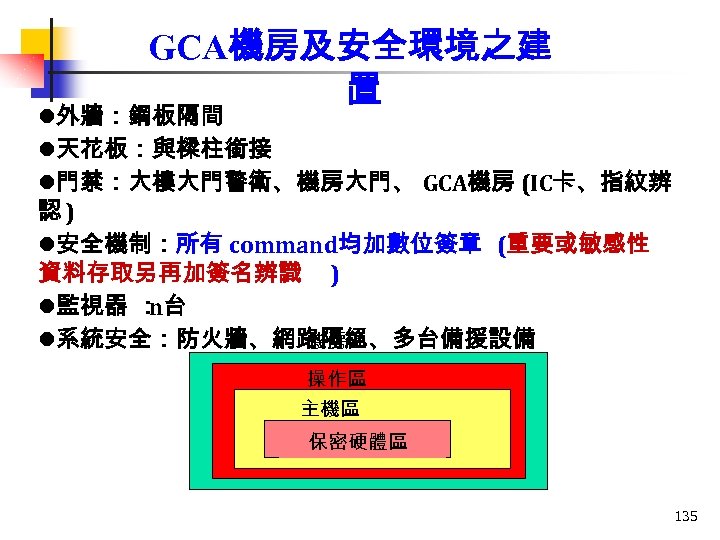
GCA機房及安全環境之建 置 l外牆:鋼板隔間 l天花板:與樑柱銜接 l門禁:大樓大門警衛、機房大門、 GCA機房 (IC卡、指紋辨 認) l安全機制:所有 command均加數位簽章 (重要或敏感性 資料存取另再加簽名辨識 ) l監視器 : n台 機房區 l系統安全:防火牆、網路隔絕、多台備援設備 操作區 主機區 保密硬體區 135
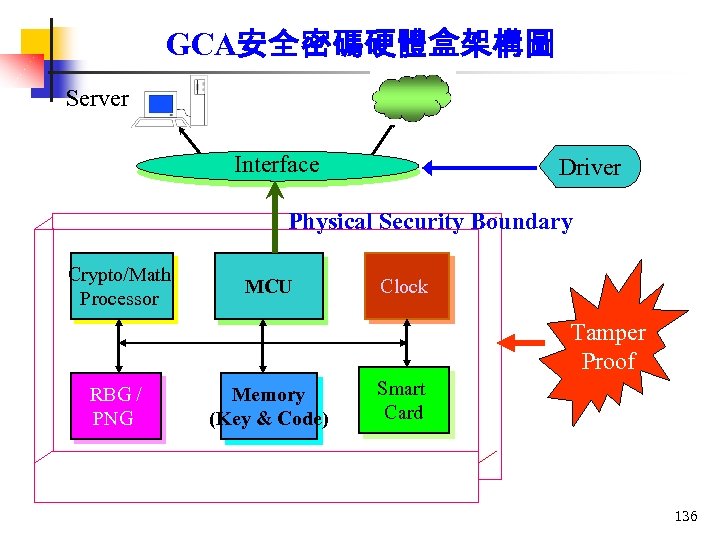
GCA安全密碼硬體盒架構圖 Server VPN Interface Driver Physical Security Boundary Crypto/Math Processor MCU Clock Tamper Proof RBG / PNG Memory (Key & Code) Smart Card 136

GCA之啟用程序 (1/2) l多位安全專家及上級 指導委員進行監督及驗證 l確認整體軟 /硬體環境及整體程序是正確 l啟動並證明系統亂數 ”種子 ”是夠安全且強韌 (strong) n 在確認 strong prime number後,要執行 random number generation時,需再確認是否符合 NIST Special Publication 800 -90 A所述 ”Recommendation for Random Number Generation Using Deterministic Random Bit Generators”(2016/5/18更新版 ) l產生 GCA公開金鑰 l. GCA公開金鑰儲存在 ”密碼硬體盒 ” (此密碼硬體盒通過國際 FIP 140 -2 level 3安全認證 ) l進行 GCA公開金鑰密碼分享 (將 GCA公開金鑰 ”切 ”成 n份 , 其中只 要有 m份 (m<=n)即可組合成原 GCA公開金鑰 ) = 此用於緊急狀況 137

GCA之啟用程序 (2/2) l確認 GCA公開金鑰組合正確 l進行 GCA簽發第一張憑證給 GCA「 自己 」 公開金鑰 l清除主機所有運算程式, 並證實產生 GCA公開金鑰之主 機沒有 Backdoor或其他程式;同時證實 GCA公開金鑰沒有 暗藏 ”某處 ” l進行簽發維運人員公開金鑰及 IC卡憑證 l維運人員進行簽發使用者公開金鑰及憑證 l再次確認整體系統及 ”密碼硬體盒 ”之運作與防護符合安 全程序 l正式啟用 138

電子化政府公開金鑰基礎建設之功能 • 憑證管理 —公開金鑰格式 —憑證產製 —憑證公佈 —憑證廢止清冊 —憑證簽發 —用戶管理 • 命名 • 金鑰管理功能 —金鑰及憑證之備援管理 —金鑰復原管理 —憑證廢止金鑰管理 • 稽核及示警 139

政府憑證管理中心 CA主體功能 A. 初始啟用憑證管理中心 (指導委員會 ) B. 簽發憑證的簽署作業 , C. 廢止憑證的簽署作業 (營運操作 ) D. 簽證單元硬體損壞的回復作業 (指導委員會 ) E. 金鑰回復身分識別卡遺失的重發卡作業 (指導委員會 ) F. 金鑰回復身分識別卡密碼遺失的密碼重設作業 (營運操作 ) G. 金鑰回復身分識別卡保管人員異動的更改作業 (監督操作 ) H. 金鑰回復身分識別卡密碼的修改作業 (營運操作 ) I. 安控人員身份識別卡遺失的重發卡作業 (營運操作 ) J. 安控人員身份識別卡密碼遺失的密碼重設作業 (營運操作 ) K. 安控人員異動的更改作業 (監督操作 ) L. 安控人員身份識別卡密碼的修改作業 (營運操作 ) M. 操作紀錄的驗證作業 , N. 憑證資料庫的查詢作業 (一般操作 ) O. 憑證資料庫的維護作業 (營運操作 ) P. 簽署憑證的統計報表作業 (一般操作 ) Q. 憑證註冊管理中心憑證核發作業 (營運操作 ) 140
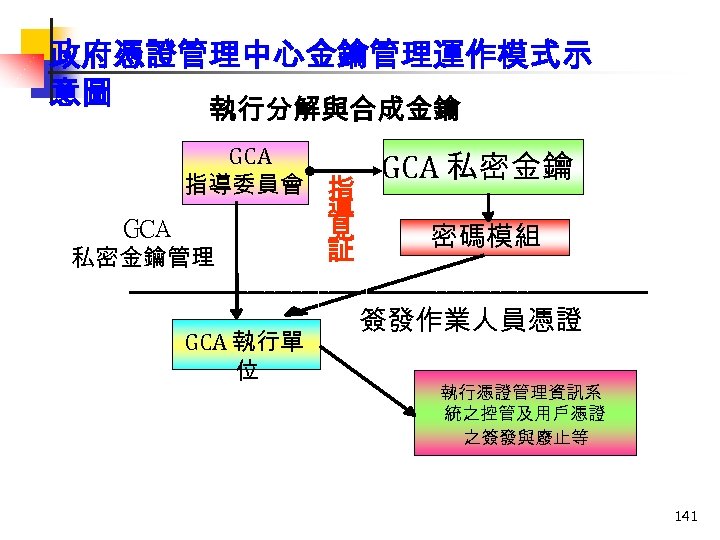
政府憑證管理中心金鑰管理運作模式示 意圖 執行分解與合成金鑰 GCA 指導委員會 指 GCA 私密金鑰管理 GCA 執行單 位 導 見 証 GCA 私密金鑰 密碼模組 簽發作業人員憑證 執行憑證管理資訊系 統之控管及用戶憑證 之簽發與廢止等 141

秘密分享 (Secret Sharing) -- 1/5 • CA Master Key(主金鑰 )使用秘密分享金鑰管理方 法 • 一般秘密分享方法 – 分割方法 (Split Schema) – 門檻方法 (Threshhold Schema) • La. Grange 多項式差入法 – 方法簡易、安全性高 142

秘密分享 (Secret Sharing) – 2/5 實務作法:如要求 7人中,只要其中任何 4人即 可組合回原來 Key(可猜出其為 a. X 3+b. X 2…多項 式 ),其秘密分享機制如下 : 在每人之 IC卡內儲存三個重要參數 1. 卡片 ID編號 (屬於 7張卡片中,第幾個卡片編號 ) 2. 座標及 f(0)的值 3. 大於 4096 bits一個正整數 (即 Mod(N)之 N值 ) 細部說明 :請參考 資訊安全基本概念導入 -密碼學概論 附件: DES、 橢圓曲線密碼系統、秘密分享 143

秘密分享 (Secret Sharing) 如何還原 – 3/5 實務作法:秘密分享 產生 過程 1. HSM 產生 random number Y=f(X)=a. X 3+b. X 2+c. X+d之 a, b, c, d 4 個很大質數 2. 取 7個座標值當成秘密分享 7個人,另帶入 f(0)取得 d值 (d值是提供 HSM做資料 AES 256 bit加密之 master key) 3. 為安全起見,將 HSM a, b, c, d 刪除 (以免需再產生另一 key 來加密,而這把 key又該如何安全儲存等議題 …) 144
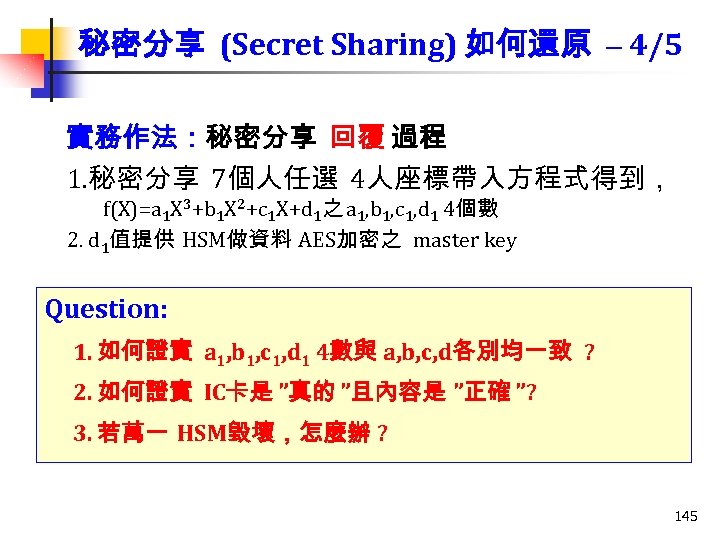
秘密分享 (Secret Sharing) 如何還原 – 4/5 實務作法:秘密分享 回覆 過程 1. 秘密分享 7個人任選 4人座標帶入方程式得到, f(X)=a 1 X 3+b 1 X 2+c 1 X+d 1之 a 1, b 1, c 1, d 1 4個數 2. d 1值提供 HSM做資料 AES加密之 master key Question: 1. 如何證實 a 1, b 1, c 1, d 1 4數與 a, b, c, d各別均一致 ? 2. 如何證實 IC卡是 ”真的 ”且內容是 ”正確 ”? 3. 若萬一 HSM毀壞,怎麼辦 ? 145

秘密分享 (Secret Sharing) 如何還原 – 5/5 實務上之解法 : 1. 不易證實 a 1, b 1, c 1, d 1 與 a, b, c, d各別均一致,且 HSM會有毀 壞狀況;可用證實 IC卡是 ”真的 ”且內容是 ”正確 ”方式 2. (1) IC卡 ID號碼與卡片表面標籤要 ”一致 ”; (2) ID號碼與每一 HSM做一 Group對應 (本 7張 IC卡針對 GCA Group), ID號碼前頭以 ”GCA”為主; (3)每張 IC卡以 8字元以上 PIN code保護; (4) IC卡內部格式特別設計與一般 IC卡不一樣 3. 若萬一 HSM毀壞,與證實 IC卡是 ”真的 ”且內容是 ”正確 ” 方式一樣 146
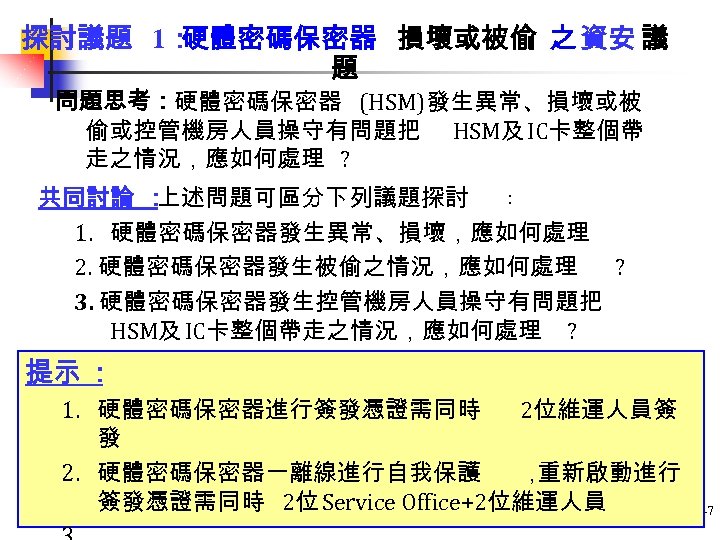
探討議題 1: 硬體密碼保密器 損壞或被偷 之 資安 議 題 問題思考:硬體密碼保密器 (HSM)發生異常、損壞或被 偷或控管機房人員操守有問題把 HSM及 IC卡整個帶 走之情況,應如何處理 ? 共同討論 : 上述問題可區分下列議題探討 : 1. 硬體密碼保密器發生異常、損壞,應如何處理 2. 硬體密碼保密器發生被偷之情況,應如何處理 ? 3. 硬體密碼保密器發生控管機房人員操守有問題把 HSM及 IC卡整個帶走之情況,應如何處理 ? 提示 : 1. 硬體密碼保密器進行簽發憑證需同時 2位維運人員簽 發 2. 硬體密碼保密器一離線進行自我保護 , 重新啟動進行 簽發憑證需同時 2位 Service Office+2位維運人員 147

如何建置可信賴的 CA之安全性及公信 力 擬申請驗證的 CA必須 = 提出其 憑證政策及憑證作業準則 (CPS) 至主管機構(經濟部商業司)進行審核通 過 148

電子化政府憑證管理中心之營運管理 l l l 憑證政策及憑證作業準則 客戶服務管理規章及要點 機房安全措施 設施裝備及週邊 組織及人力配置 經營管理作業 (CPS) 149
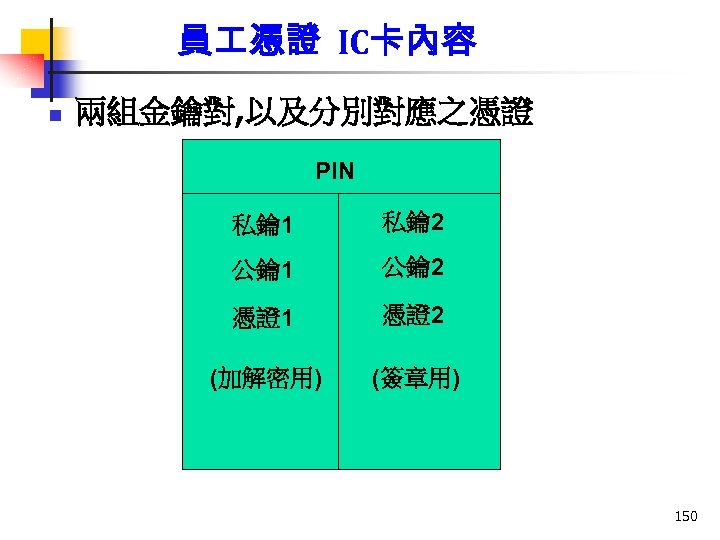
員 憑證 IC卡內容 n 兩組金鑰對, 以及分別對應之憑證 PIN 私鑰 1 私鑰 2 公鑰 1 公鑰 2 憑證1 憑證2 (加解密用) (簽章用) 150

有關個人憑證與主機 SSL憑證之 議題 個人憑證與主機 SSL憑證之間運作關係為何 ? 1. 主機公鑰及私鑰,在其主機先產生後,將公鑰及基本主機資料送 CA(若是採用 Verisign CA,則送到美國 Verisign公司 )簽發主機憑證, 送到註冊窗口,註冊窗口再將此憑證送給主機申請者。 2. 使用者 (client)與主機之憑證關係,只有在使用者 browser 使用 ”https: //. . . ”時,若主機未申請國際認證過之 CA,則browser 會發出 無法確認此主機憑證警訊 l個人憑證與主機 SSL憑證之間的關係,可以是單向及雙向認證; n 單向認證 : 如一般 client使用 ”https: //. . . ”時, browser會核對 CA list,該主機是否在國際認證過之 CA名單內,若是則順利 進行。 n 雙向認證 : 如一般 client使用 ”https: //. . . ”時, browser會核對 CA list,該主機是否在國際認證過之 CA名單內,若是則順利 進行;同時,主機端也會要求 client 插入憑證卡,進行該憑證 卡是否為在國際認證過之 CA名單內 (主機會從該 CA所簽發 CRL,核對該client是否仍為有效的憑證 ),若是則順利進行。 此種 雙向認證最常用於較高安全性之 SSL VPN服務。 <註 > :除非有特別應用軟體之要求,否則 client是不需再安裝其他憑證相關 151
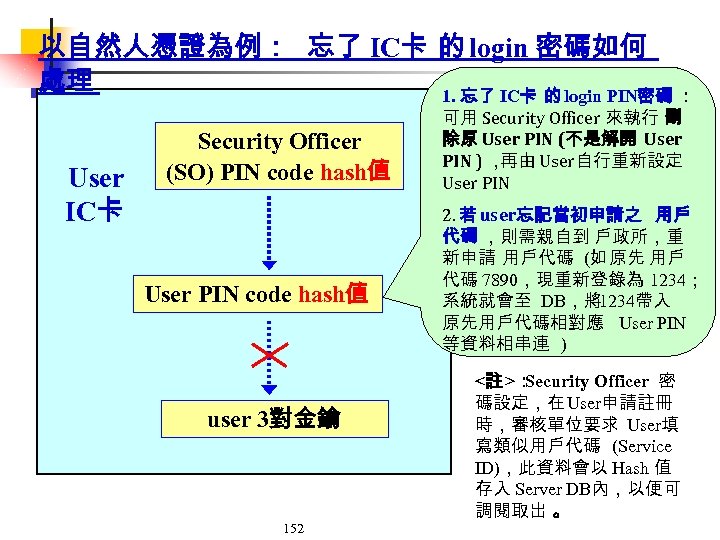
以自然人憑證為例: 忘了 IC卡 的 login 密碼如何 處理 1. 忘了 IC卡 的 login PIN密碼 : User IC卡 Security Officer (SO) PIN code hash值 User PIN code hash值 user 3對金鑰 152 可用 Security Officer 來執行 刪 除原 User PIN (不是解開 User PIN ) , 再由 User自行重新設定 User PIN 2. 若 user忘記當初申請之 用戶 代碼 ,則需親自到 戶政所,重 新申請 用戶代碼 (如 原先 用戶 代碼 7890,現重新登錄為 1234; 系統就會至 DB,將1234帶入 原先用戶代碼相對應 User PIN 等資料相串連 ) <註 >: Security Officer 密 碼設定,在 User申請註冊 時,審核單位要求 User填 寫類似用戶代碼 (Service ID),此資料會以 Hash 值 存入 Server DB內,以便可 調閱取出 。

深入探討 : 系統整體發展性 電子化政府電子認證服務 整體規劃 153

PKI與 PMI之區別? 電子化政府電子認證體系區分為「公開 金鑰基礎建設( Public Key Infrastructure, PKI)」與「授權管基礎建設( Privilege Management Infrastructure, PMI)」,分別 提供公鑰憑證服務與屬性憑證服務,以 達到憑證應用的完整性及多樣性。 154

實體證照制度之概觀 n 證照的區分與性質: n 身分證照:識別「與生俱來之身分」的證明文件: n n … 資格證照:由「身分證照」延伸出來的資格證明: n n 身分證、法人登記證、非法人團體登記證 駕照、畢業證書、技師執照、所有權狀、聘書、 委託書、營業執照、統一發票購票證、財力證 明、履約保證書、員 識別證、會員證 … 混合證照:兼具「身分證照」與「資格證照」性質之 證照 n 身分識別與授權 (Authentication vs. Authorization) n Source of Authority (SOA) and Delegation 155

X. 509 2000之電子證照架構 n 電子證照的區分與性質: n n Public-Key Certificate:身分識別憑證,由Certificate Authority(CA)簽發,記載憑證簽發對象 (Subject)的 Identity By Nature, Subject的 Public Key,並含強制性 含 (mandatory)及 低變動性 (long-term)的識別資料,如名稱、 身分證字號、統一編號等 Attribute Certificate:授權憑證,由 Attribute Authority(AA) 簽發,記載憑證簽發對象 (Subject)的 Privilege By Application,含選擇性 (optional)及 變動性 (short-term)的 授權資料, 但 不含 Public Key, 例如學位、職位、技師 資格、營業項目、資本額、履約能力等 <註 >: Attribute Certificate不含 Public Key : 可用 key. Identifier(取 CA Publish Key Hash value )或用 CA+Serial Number來識別是誰簽發 憑證 (此在 Key extension內註明 , 此為 option;另 usage 如加密或 key 簽章等應用,此為必要性 ) 156

公鑰憑證與屬性憑證的搭配 n 公鑰憑證的功能: (身分證 +印鑑證明 ) n n n 數位簽章與身分認證 (Authentication) 建立安全通訊管道 (Secure Channel) 屬性憑證的功能 : (執照 ) n 做為資格審驗 (Authorization)的依據 157
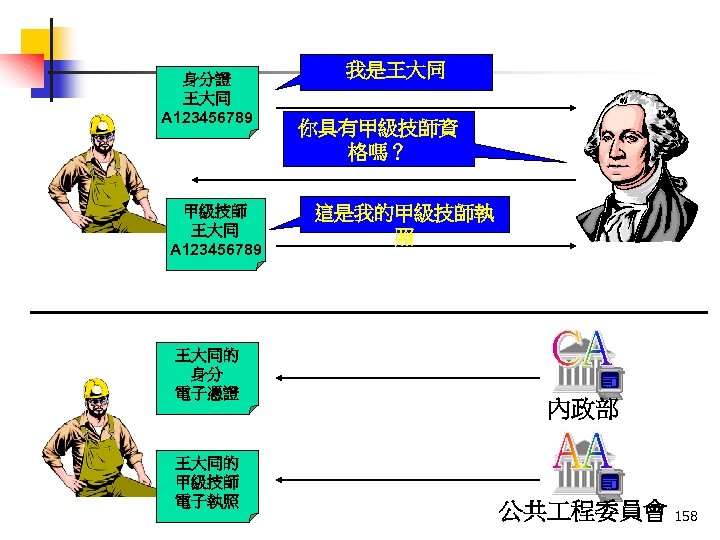
身分證 王大同 A 123456789 甲級技師 王大同 A 123456789 王大同的 身分 電子憑證 王大同的 甲級技師 電子執照 我是王大同 你具有甲級技師資 格嗎? 這是我的甲級技師執 照 內政部 公共 程委員會 158

身分識別憑證與授權憑證分離的優點 n n 尊重 Source of Authority,權責分明; 避免因變動性資料之變更而需要時常重新申請 公鑰憑證 (Public-Key Certificate)的問題; 同一個 Entity,只要由SOA發出必要之公鑰憑證 即可,不必每個應用系統都發專用的公鑰憑證, 可避免金鑰管理問題; (理想狀況是一個 Entity 只要一張公鑰憑證,但可視需要申請多張屬性 憑證。) 公鑰憑證與屬性憑證各司其職,可應付應用系 統多樣性需求。 (憑證瘦身 ) 159

GPKI服務推動後 之議題 - 資安營運面探討 160
GPKI服務推動後之議題探討 (1/2) 深入探討 : 憑證應用發展策略 我國憑證應用發展策略暨國際應用趨勢 深入探討 : 系統後續維護 -功能提升 GPKI換金鑰與換卡 Action Plan 深入探討 : 系統推廣普及性 通過 Web. Trust認證及整合微軟 IE系統 161

GPKI服務推動後之議題探討 (2/2) 深入探討 : 系統應用與推展服務 PKI技術於電子化政府之應用服務 深入探討 : 系統功能完整性 我國時戳之政策及應用 深入探討 : 系統研發前瞻性 先進電子簽章格式技術 (暫不授課 ) 162
b73f3b13843c7ca3cff15b9afb4b3c8a.ppt