00fa26f4899ab2bd2f14c950919d1f23.ppt
- Количество слайдов: 21
 Workshop on Logical Foundations of an Adaptive Security Infrastructure (WOLFASI) A sub-workshop of the LICS Foundations of Computer Security (FCS'04) Workshop, LICS '04 July 12 -13, 2004 Turku, Finland On Comparing the Expressing Power of Access Control Model Frameworks Elisa Bertino Barbara Catania Purdue University bertino@cerias. purdue. edu DISI Università degli Studi di Genova catania@disi. unige. it Elena Ferrari Paolo Perlasca DSCFM Università degli Studi dell’Insubria Elena. Ferrari@uninsubria. it DICO Università degli Studi di Milano perlasca@dico. unimi. it
Workshop on Logical Foundations of an Adaptive Security Infrastructure (WOLFASI) A sub-workshop of the LICS Foundations of Computer Security (FCS'04) Workshop, LICS '04 July 12 -13, 2004 Turku, Finland On Comparing the Expressing Power of Access Control Model Frameworks Elisa Bertino Barbara Catania Purdue University bertino@cerias. purdue. edu DISI Università degli Studi di Genova catania@disi. unige. it Elena Ferrari Paolo Perlasca DSCFM Università degli Studi dell’Insubria Elena. Ferrari@uninsubria. it DICO Università degli Studi di Milano perlasca@dico. unimi. it
 Summary • ASI and policy framework • Frameworks comparison • Conclusions and future work
Summary • ASI and policy framework • Frameworks comparison • Conclusions and future work
 ASI • Adaptive Security Infrastructure (ASI) – Collect information about security environments – Analyze the collected data – Perform efficient compensating actions according to security relevant detected events • ASI strictly depends on the underlying security policy
ASI • Adaptive Security Infrastructure (ASI) – Collect information about security environments – Analyze the collected data – Perform efficient compensating actions according to security relevant detected events • ASI strictly depends on the underlying security policy
 Security Policy Issues • How formally representing the semantics of security policies ? • In distributed environments – Compensating actions • can involve different environments and • must agree with the respective underlying security policies
Security Policy Issues • How formally representing the semantics of security policies ? • In distributed environments – Compensating actions • can involve different environments and • must agree with the respective underlying security policies
 Framework • Strategy: framework for representation, analysis, and usage of security policies • Useful in – – Performing security analysis Identifying strategies Producing compensating actions Representing in a uniform way the heterogeneity of the access control policies and formalisms • We focus on one of the most relevant classes of security policies: access control policies
Framework • Strategy: framework for representation, analysis, and usage of security policies • Useful in – – Performing security analysis Identifying strategies Producing compensating actions Representing in a uniform way the heterogeneity of the access control policies and formalisms • We focus on one of the most relevant classes of security policies: access control policies
 Access Control (AC) Policies • An access control policy determines the operations and rights that subjects can exercise on the protected objects • Access control policies can be specified through authorization rules – Rules able to establish for each subject s which actions such subject can perform on which object of the system
Access Control (AC) Policies • An access control policy determines the operations and rights that subjects can exercise on the protected objects • Access control policies can be specified through authorization rules – Rules able to establish for each subject s which actions such subject can perform on which object of the system
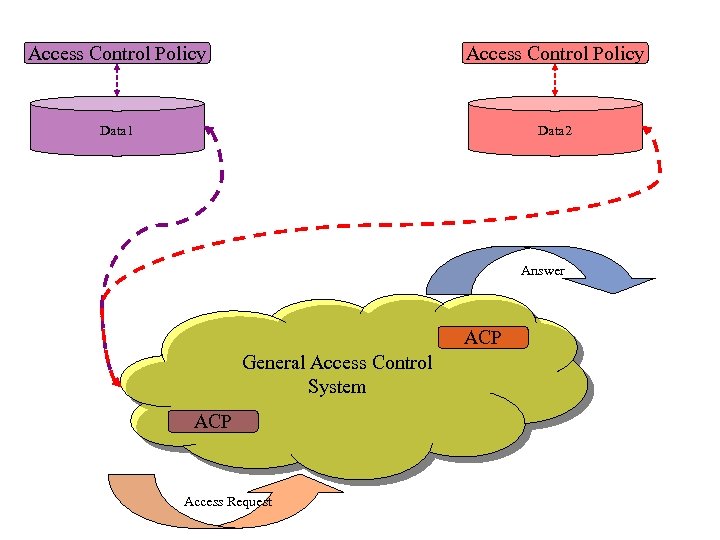 Access Control Policy Data 1 Data 2 Answer ACP General Access Control System ACP Access Request
Access Control Policy Data 1 Data 2 Answer ACP General Access Control System ACP Access Request
 Which AC framework ? • A variety of access control frameworks have been so far defined • Each framework provides a formalism for specifying access control policies and a semantics for computing authorizations • Different frameworks support the representation of different sets of policies • No comparison of the expressive power of the proposed frameworks has been investigated
Which AC framework ? • A variety of access control frameworks have been so far defined • Each framework provides a formalism for specifying access control policies and a semantics for computing authorizations • Different frameworks support the representation of different sets of policies • No comparison of the expressive power of the proposed frameworks has been investigated
 LAMP • LAMP is based on the C-Datalog language • C-Datalog supports: – classical object-oriented concepts, such as classes, objects and inheritance (used to represent subjects, objects, privileges, sessions, …) – typical logic-based concepts, such as deductive rules (used to represent authorization and constraint rules) • Each instance of an ACM is a logical program composed of C-Datalog rules defined against a CDatalog schema
LAMP • LAMP is based on the C-Datalog language • C-Datalog supports: – classical object-oriented concepts, such as classes, objects and inheritance (used to represent subjects, objects, privileges, sessions, …) – typical logic-based concepts, such as deductive rules (used to represent authorization and constraint rules) • Each instance of an ACM is a logical program composed of C-Datalog rules defined against a CDatalog schema
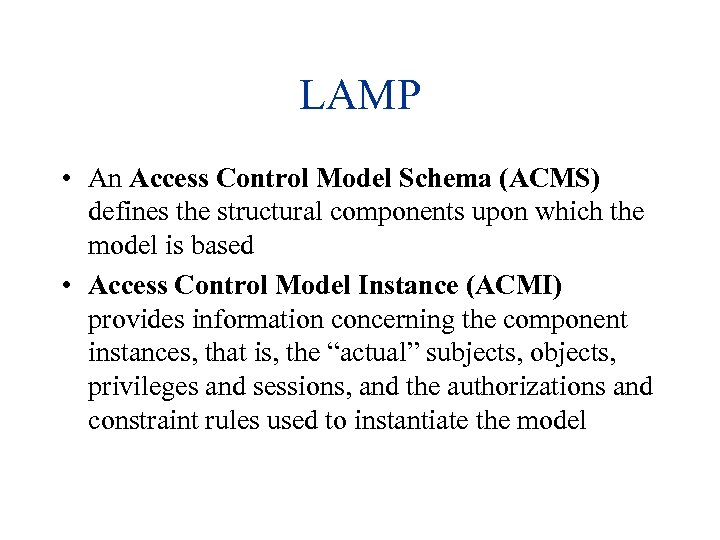 LAMP • An Access Control Model Schema (ACMS) defines the structural components upon which the model is based • Access Control Model Instance (ACMI) provides information concerning the component instances, that is, the “actual” subjects, objects, privileges and sessions, and the authorizations and constraint rules used to instantiate the model
LAMP • An Access Control Model Schema (ACMS) defines the structural components upon which the model is based • Access Control Model Instance (ACMI) provides information concerning the component instances, that is, the “actual” subjects, objects, privileges and sessions, and the authorizations and constraint rules used to instantiate the model
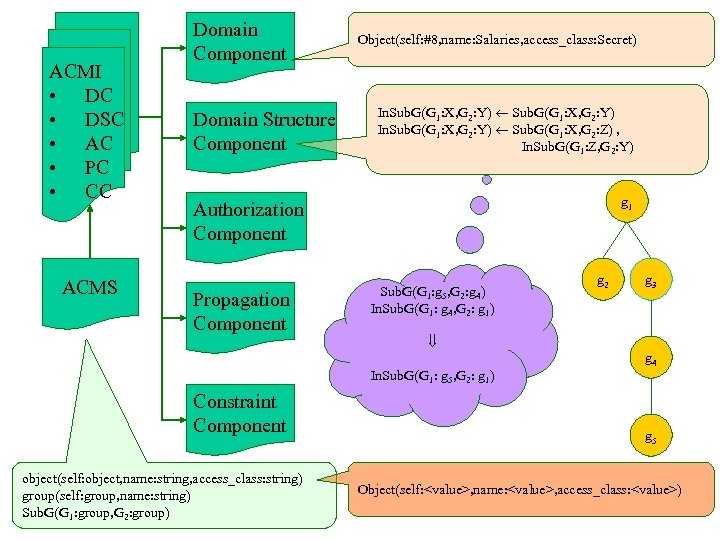 ACMI • DC • DSC • AC • PC • CC ACMS Domain Component Domain Structure Component Object(self: #8, name: Salaries, access_class: Secret) In. Sub. G(G 1: X, G 2: Y) ¬ Sub. G(G 1: X, G 2: Y) In. Sub. G(G 1: X, G 2: Y) ¬ Sub. G(G 1: X, G 2: Z) , In. Sub. G(G 1: Z, G 2: Y) g 1 Authorization Component Propagation Component Sub. G(G 1: g 5, G 2: g 4) In. Sub. G(G 1: g 4, G 2: g 1) ß In. Sub. G(G 1: g 5, G 2: g 1) Constraint Component object(self: object, name: string, access_class: string) group(self: group, name: string) Sub. G(G 1: group, G 2: group) g 2 g 3 g 4 g 5 Object(self:
ACMI • DC • DSC • AC • PC • CC ACMS Domain Component Domain Structure Component Object(self: #8, name: Salaries, access_class: Secret) In. Sub. G(G 1: X, G 2: Y) ¬ Sub. G(G 1: X, G 2: Y) In. Sub. G(G 1: X, G 2: Y) ¬ Sub. G(G 1: X, G 2: Z) , In. Sub. G(G 1: Z, G 2: Y) g 1 Authorization Component Propagation Component Sub. G(G 1: g 5, G 2: g 4) In. Sub. G(G 1: g 4, G 2: g 1) ß In. Sub. G(G 1: g 5, G 2: g 1) Constraint Component object(self: object, name: string, access_class: string) group(self: group, name: string) Sub. G(G 1: group, G 2: group) g 2 g 3 g 4 g 5 Object(self:
 Jajodia et al. • Jajodia et al. framework represents access control models by stratified logic programs constructed over a given logical language • The basic elements used to represent an ACM are: – OTH, UGH, RH, A, Rel – Authorizations (o, s,
Jajodia et al. • Jajodia et al. framework represents access control models by stratified logic programs constructed over a given logical language • The basic elements used to represent an ACM are: – OTH, UGH, RH, A, Rel – Authorizations (o, s,
 Jajodia et al. • An AS is a set of stratified rules satisfying some syntactic restrictions • Authorizations are specified through predicates: – cando(o, s,
Jajodia et al. • An AS is a set of stratified rules satisfying some syntactic restrictions • Authorizations are specified through predicates: – cando(o, s,
 RBAC • NIST RBAC is defined by four levels of increasing complexity • Roles are powerful and easy to use • SSD and DSD constraints • Policy free
RBAC • NIST RBAC is defined by four levels of increasing complexity • Roles are powerful and easy to use • SSD and DSD constraints • Policy free
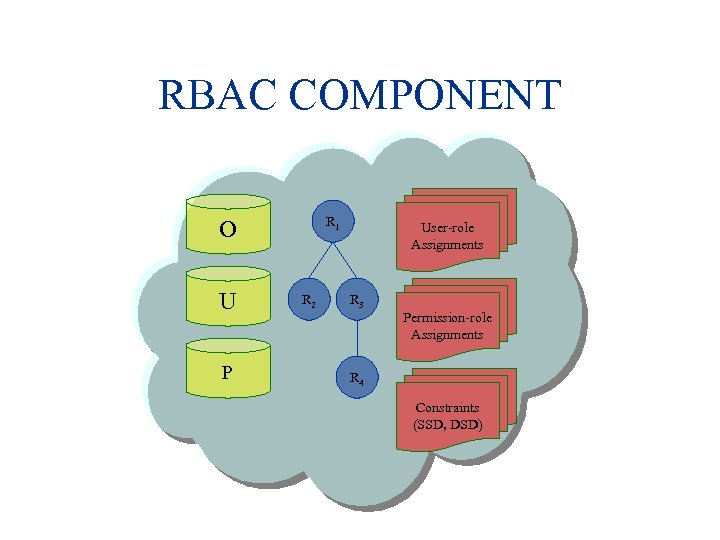 RBAC COMPONENT R 1 O U P R 2 User-role Assignments R 3 Permission-role Assignments R 4 Constraints (SSD, DSD)
RBAC COMPONENT R 1 O U P R 2 User-role Assignments R 3 Permission-role Assignments R 4 Constraints (SSD, DSD)
 Result • All the ACMs that can be represented by the Jajodia et al. framework can be represented by the Lamp framework • All the ACMs that can be represented by the four NIST levels can be represented by the Lamp framework
Result • All the ACMs that can be represented by the Jajodia et al. framework can be represented by the Lamp framework • All the ACMs that can be represented by the four NIST levels can be represented by the Lamp framework
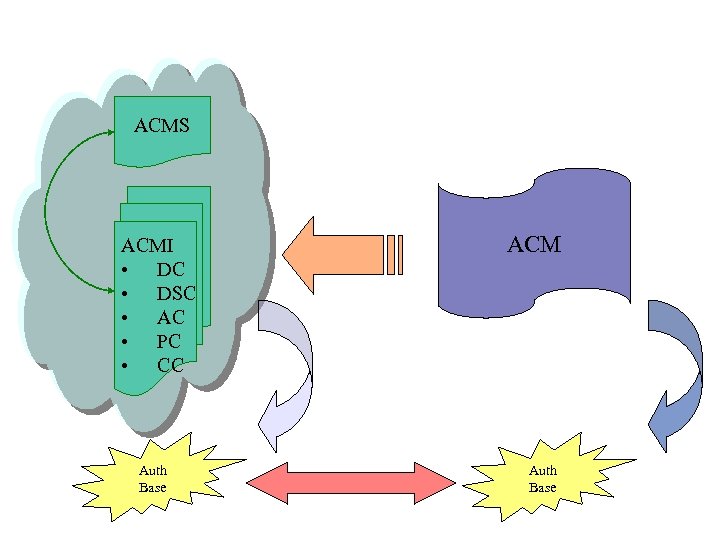 ACMS ACMI • DC • DSC • AC • PC • CC Auth Base ACM Auth Base
ACMS ACMI • DC • DSC • AC • PC • CC Auth Base ACM Auth Base
 Result • The set of the ACMs that can be represented by LAMP is greater than the one representable by the Jajodia et al. framework • Locally stratified logic programs generates a unique set of authorizations vs more general formalism supporting the generation of more than one set of consistent authorizations
Result • The set of the ACMs that can be represented by LAMP is greater than the one representable by the Jajodia et al. framework • Locally stratified logic programs generates a unique set of authorizations vs more general formalism supporting the generation of more than one set of consistent authorizations
 Result • The set of the ACMs that can be represented by LAMP is greater than the one representable by the NIST framework • SSD and DSD constraints vs broader set of constraints (conditioned separation of duty depending on specific values of basic elements)
Result • The set of the ACMs that can be represented by LAMP is greater than the one representable by the NIST framework • SSD and DSD constraints vs broader set of constraints (conditioned separation of duty depending on specific values of basic elements)
 Conclusions • Given a distributed system based on ASI our analysis will help in the selection of a specific ac framework for such environment
Conclusions • Given a distributed system based on ASI our analysis will help in the selection of a specific ac framework for such environment
 Future work • Definition of new dimensions and comparison according to them – Mapping complexity – Spatial complexity – Temporal complexity • Development of a set of tools for specifying and analyzing ac policies using LAMP as a core system
Future work • Definition of new dimensions and comparison according to them – Mapping complexity – Spatial complexity – Temporal complexity • Development of a set of tools for specifying and analyzing ac policies using LAMP as a core system


