6cbae072ebc008418b9f25f9abc7cc4f.ppt
- Количество слайдов: 57
 Virtual Internet Research at the Postel Center Joe Touch Postel Center Computer Networks Division USC/ISI January 2004 Joe Touch USC/ISI 1
Virtual Internet Research at the Postel Center Joe Touch Postel Center Computer Networks Division USC/ISI January 2004 Joe Touch USC/ISI 1
 Outline: ¬ VIs: definition & architecture ¬ Using VIs: ¬ X-Bone – deploying VIs ¬ Dyna. Bone – multilayer VIs for fault tolerance, security, and performance ¬ Supporting VIs: ¬ Net. FS – OS support for VIs ¬ Data. Router – app. -directed net-layer forwarding January 2004 Joe Touch USC/ISI 2
Outline: ¬ VIs: definition & architecture ¬ Using VIs: ¬ X-Bone – deploying VIs ¬ Dyna. Bone – multilayer VIs for fault tolerance, security, and performance ¬ Supporting VIs: ¬ Net. FS – OS support for VIs ¬ Data. Router – app. -directed net-layer forwarding January 2004 Joe Touch USC/ISI 2
 VI Definition ¬ VI is a network composed of: ¬ Virt. hosts, virt. routers, virt. links (tunnels) ¬ Provides at least the same services as IA ¬ In a virtual context ¬ First-principles extension ¬ More than a patch ¬ More than interim January 2004 Joe Touch USC/ISI 3
VI Definition ¬ VI is a network composed of: ¬ Virt. hosts, virt. routers, virt. links (tunnels) ¬ Provides at least the same services as IA ¬ In a virtual context ¬ First-principles extension ¬ More than a patch ¬ More than interim January 2004 Joe Touch USC/ISI 3
 Motivation ¬ Unified, consistent virtual architecture ¬ VPNs, overlay nets, peer nets ¬ Incremental deployment of new services ¬ Ongoing experiments ¬ Topology-based services ¬ DHTs, geographic forwarding [Geo. Net], string-rewriter forwarding [Data. Router] ¬ Layer-based services ¬ Contained dynamic routing, fault tolerance (FEC), security (traffic hiding), multi-algorithm [Dyna. Bone], Plutarch’s subnet composition January 2004 Joe Touch USC/ISI 4
Motivation ¬ Unified, consistent virtual architecture ¬ VPNs, overlay nets, peer nets ¬ Incremental deployment of new services ¬ Ongoing experiments ¬ Topology-based services ¬ DHTs, geographic forwarding [Geo. Net], string-rewriter forwarding [Data. Router] ¬ Layer-based services ¬ Contained dynamic routing, fault tolerance (FEC), security (traffic hiding), multi-algorithm [Dyna. Bone], Plutarch’s subnet composition January 2004 Joe Touch USC/ISI 4
 Extra Constraints ¬ Internet-like ¬ Routing (link up) vs. provisioning (link add) ¬ …one header to bind them all… (use IP, provide IP recursion) ¬ Complete E 2 E system ¬ All VNs are E 2 E ¬ VN “Turing Test” ¬ A net can’t tell it’s virtual ¬ Use existing protocols, OSs, apps. January 2004 Joe Touch USC/ISI 5
Extra Constraints ¬ Internet-like ¬ Routing (link up) vs. provisioning (link add) ¬ …one header to bind them all… (use IP, provide IP recursion) ¬ Complete E 2 E system ¬ All VNs are E 2 E ¬ VN “Turing Test” ¬ A net can’t tell it’s virtual ¬ Use existing protocols, OSs, apps. January 2004 Joe Touch USC/ISI 5
 Principles ¬ TENET 1. Internet-like ¬ VIs = VRs + VHs + tunnels ¬ Emulating the Internet ¬ TENET 2. All-Virtual ¬ Decoupled from their base network ¬ TENET 3. Recursion-as-router ¬ Some of VRs are VI networks January 2004 Joe Touch USC/ISI 6
Principles ¬ TENET 1. Internet-like ¬ VIs = VRs + VHs + tunnels ¬ Emulating the Internet ¬ TENET 2. All-Virtual ¬ Decoupled from their base network ¬ TENET 3. Recursion-as-router ¬ Some of VRs are VI networks January 2004 Joe Touch USC/ISI 6
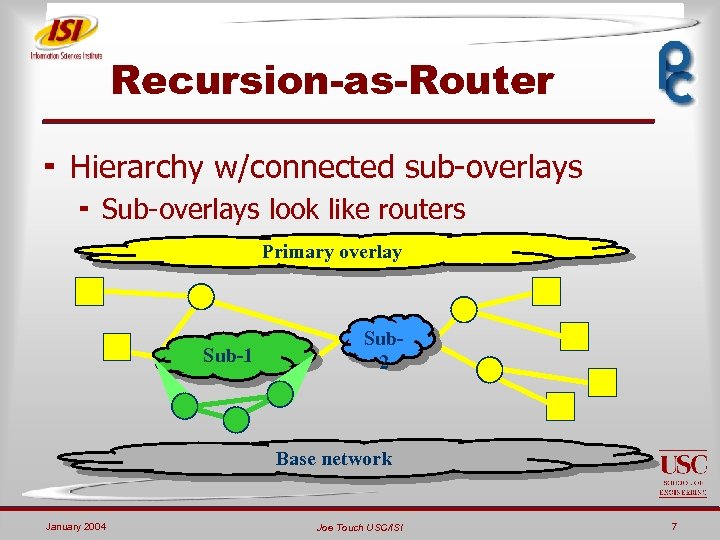 Recursion-as-Router ¬ Hierarchy w/connected sub-overlays ¬ Sub-overlays look like routers Primary overlay Sub-1 Sub 2 Base network January 2004 Joe Touch USC/ISI 7
Recursion-as-Router ¬ Hierarchy w/connected sub-overlays ¬ Sub-overlays look like routers Primary overlay Sub-1 Sub 2 Base network January 2004 Joe Touch USC/ISI 7
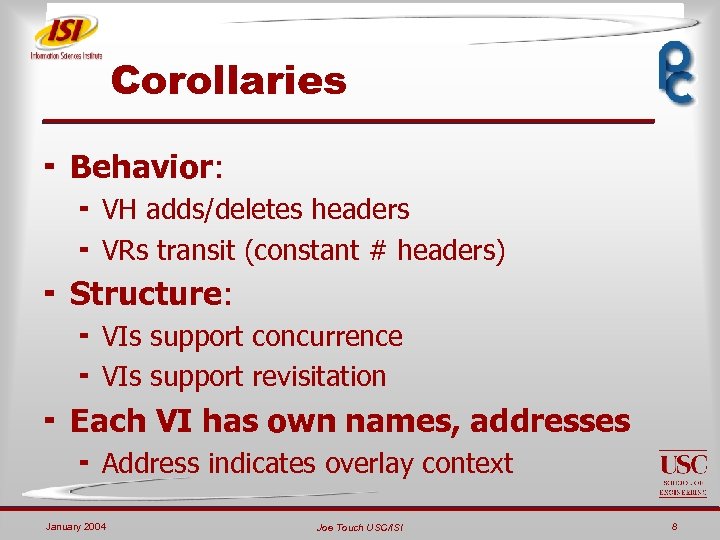 Corollaries ¬ Behavior: ¬ VH adds/deletes headers ¬ VRs transit (constant # headers) ¬ Structure: ¬ VIs support concurrence ¬ VIs support revisitation ¬ Each VI has own names, addresses ¬ Address indicates overlay context January 2004 Joe Touch USC/ISI 8
Corollaries ¬ Behavior: ¬ VH adds/deletes headers ¬ VRs transit (constant # headers) ¬ Structure: ¬ VIs support concurrence ¬ VIs support revisitation ¬ Each VI has own names, addresses ¬ Address indicates overlay context January 2004 Joe Touch USC/ISI 8
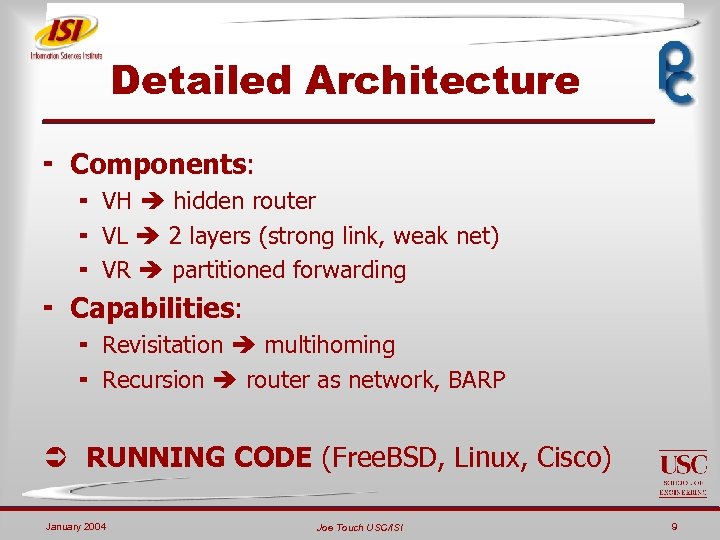 Detailed Architecture ¬ Components: ¬ VH hidden router ¬ VL 2 layers (strong link, weak net) ¬ VR partitioned forwarding ¬ Capabilities: ¬ Revisitation multihoming ¬ Recursion router as network, BARP RUNNING CODE (Free. BSD, Linux, Cisco) January 2004 Joe Touch USC/ISI 9
Detailed Architecture ¬ Components: ¬ VH hidden router ¬ VL 2 layers (strong link, weak net) ¬ VR partitioned forwarding ¬ Capabilities: ¬ Revisitation multihoming ¬ Recursion router as network, BARP RUNNING CODE (Free. BSD, Linux, Cisco) January 2004 Joe Touch USC/ISI 9
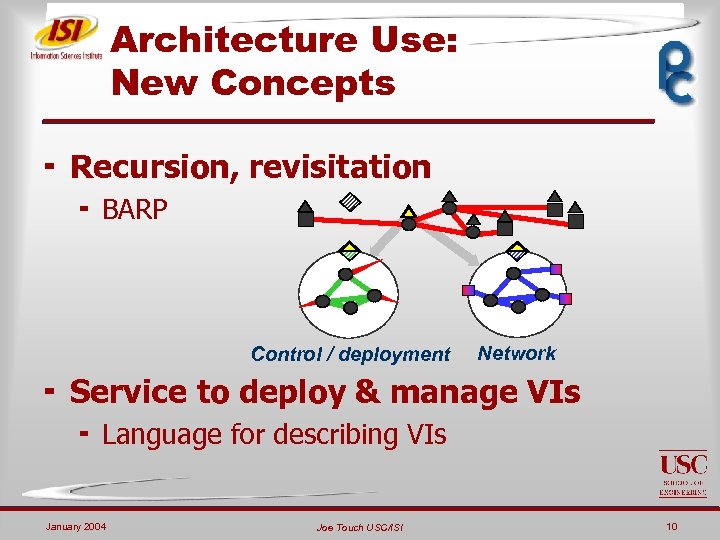 Architecture Use: New Concepts ¬ Recursion, revisitation ¬ BARP Control / deployment Network ¬ Service to deploy & manage VIs ¬ Language for describing VIs January 2004 Joe Touch USC/ISI 10
Architecture Use: New Concepts ¬ Recursion, revisitation ¬ BARP Control / deployment Network ¬ Service to deploy & manage VIs ¬ Language for describing VIs January 2004 Joe Touch USC/ISI 10
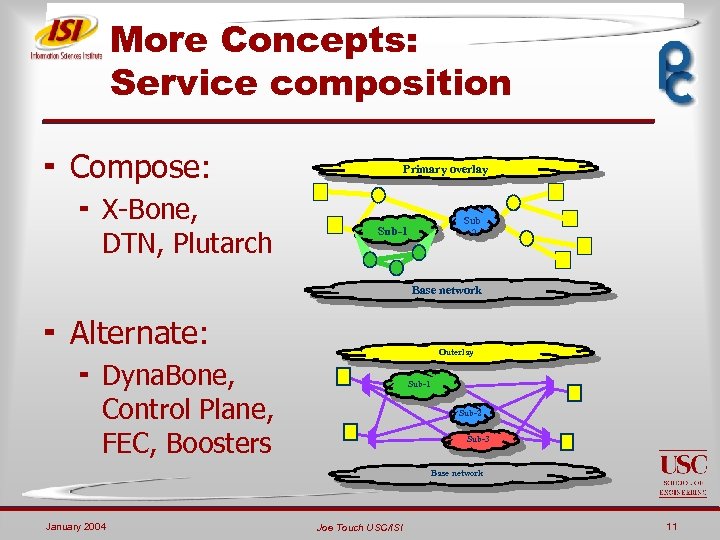 More Concepts: Service composition ¬ Compose: ¬ X-Bone, DTN, Plutarch Primary overlay Sub -2 Sub-1 Base network ¬ Alternate: Outerlay ¬ Dyna. Bone, Control Plane, FEC, Boosters Sub-1 Sub-2 Sub-3 Base network January 2004 Joe Touch USC/ISI 11
More Concepts: Service composition ¬ Compose: ¬ X-Bone, DTN, Plutarch Primary overlay Sub -2 Sub-1 Base network ¬ Alternate: Outerlay ¬ Dyna. Bone, Control Plane, FEC, Boosters Sub-1 Sub-2 Sub-3 Base network January 2004 Joe Touch USC/ISI 11
 More Architecture Uses: Correct/explain anomalies ¬ Multihoming ¬ Phantom router in all hosts ¬ Input context forwarding/binding ¬ Revisitation ¬ Two-level tunnels ¬ Input context sets ¬ IPsec tunnel mode & dynamic routing January 2004 Joe Touch USC/ISI 12
More Architecture Uses: Correct/explain anomalies ¬ Multihoming ¬ Phantom router in all hosts ¬ Input context forwarding/binding ¬ Revisitation ¬ Two-level tunnels ¬ Input context sets ¬ IPsec tunnel mode & dynamic routing January 2004 Joe Touch USC/ISI 12
 Typical Q’s ¬ Why not VPNs/Peer, etc. ? ¬ Most net-level are incremental, partial, etc. ¬ App. Level recapitulates network & won’t compose ¬ Isn’t this more complex? ¬ AS-like management encapsulation (multi-level) ¬ Can make application view simpler (per-app. networks) ¬ Isn’t this suboptimal/non-diverse? ¬ So is VM; like VM, OOB info. & direct measurements can help ¬ Layering implies increasing coarseness ¬ Wasn’t this done in (X) before? ¬ VIA is uniform, consistent, & implemented ¬ What’s so hard? ¬ See “uses” & “anomalies” January 2004 Joe Touch USC/ISI 13
Typical Q’s ¬ Why not VPNs/Peer, etc. ? ¬ Most net-level are incremental, partial, etc. ¬ App. Level recapitulates network & won’t compose ¬ Isn’t this more complex? ¬ AS-like management encapsulation (multi-level) ¬ Can make application view simpler (per-app. networks) ¬ Isn’t this suboptimal/non-diverse? ¬ So is VM; like VM, OOB info. & direct measurements can help ¬ Layering implies increasing coarseness ¬ Wasn’t this done in (X) before? ¬ VIA is uniform, consistent, & implemented ¬ What’s so hard? ¬ See “uses” & “anomalies” January 2004 Joe Touch USC/ISI 13
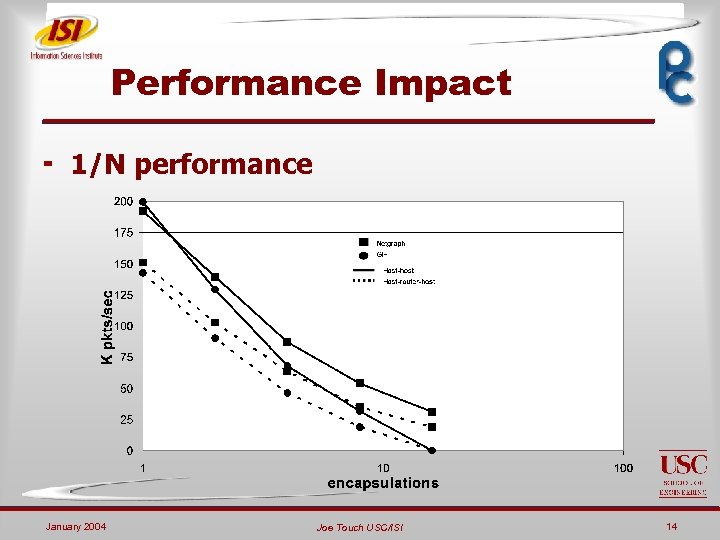 Performance Impact ¬ 1/N performance January 2004 Joe Touch USC/ISI 14
Performance Impact ¬ 1/N performance January 2004 Joe Touch USC/ISI 14
 Prior & Related Work ¬ Service/new protocols ¬ Cronus, M/6/Q/A-Bone ¬ Multi/other layer ¬ Cronus, Supranet, Morph. Net, VANs ¬ Partial ¬ VPN, VNS, RON, Detour, PPVPN, SOS ¬ Virtualization, Revistation, Recursion ¬ X-Bone, Spawning, Dyna. Bone, Net. FS, Netlab January 2004 Joe Touch USC/ISI 15
Prior & Related Work ¬ Service/new protocols ¬ Cronus, M/6/Q/A-Bone ¬ Multi/other layer ¬ Cronus, Supranet, Morph. Net, VANs ¬ Partial ¬ VPN, VNS, RON, Detour, PPVPN, SOS ¬ Virtualization, Revistation, Recursion ¬ X-Bone, Spawning, Dyna. Bone, Net. FS, Netlab January 2004 Joe Touch USC/ISI 15
 VI analogy to VM ¬ Protection ¬ For concurrency, separation ¬ Simpler configuration ¬ Run over simpler topologies ¬ Decouple from physical ¬ Emulate larger/different nets ¬ Automation ¬ Generic, external mechanism January 2004 Joe Touch USC/ISI 16
VI analogy to VM ¬ Protection ¬ For concurrency, separation ¬ Simpler configuration ¬ Run over simpler topologies ¬ Decouple from physical ¬ Emulate larger/different nets ¬ Automation ¬ Generic, external mechanism January 2004 Joe Touch USC/ISI 16
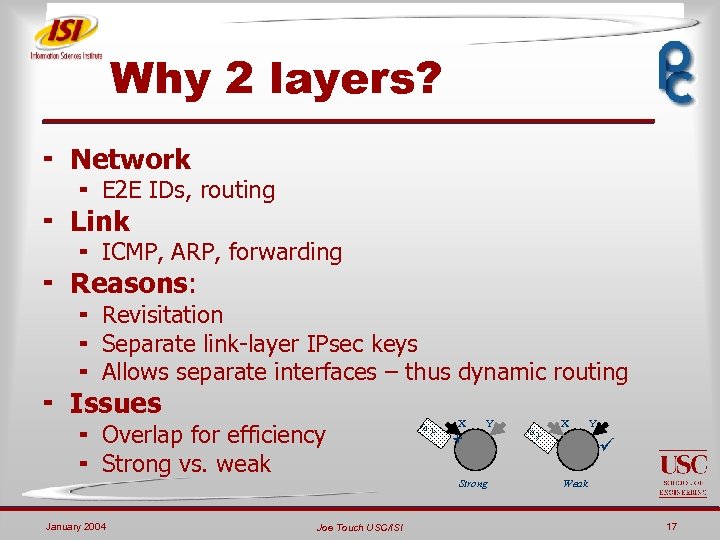 Why 2 layers? ¬ Network ¬ E 2 E IDs, routing ¬ Link ¬ ICMP, ARP, forwarding ¬ Reasons: ¬ Revisitation ¬ Separate link-layer IPsec keys ¬ Allows separate interfaces – thus dynamic routing ¬ Issues ¬ Overlap for efficiency ¬ Strong vs. weak January 2004 Joe Touch USC/ISI to Y X Y Strong to Y X Y Weak 17
Why 2 layers? ¬ Network ¬ E 2 E IDs, routing ¬ Link ¬ ICMP, ARP, forwarding ¬ Reasons: ¬ Revisitation ¬ Separate link-layer IPsec keys ¬ Allows separate interfaces – thus dynamic routing ¬ Issues ¬ Overlap for efficiency ¬ Strong vs. weak January 2004 Joe Touch USC/ISI to Y X Y Strong to Y X Y Weak 17
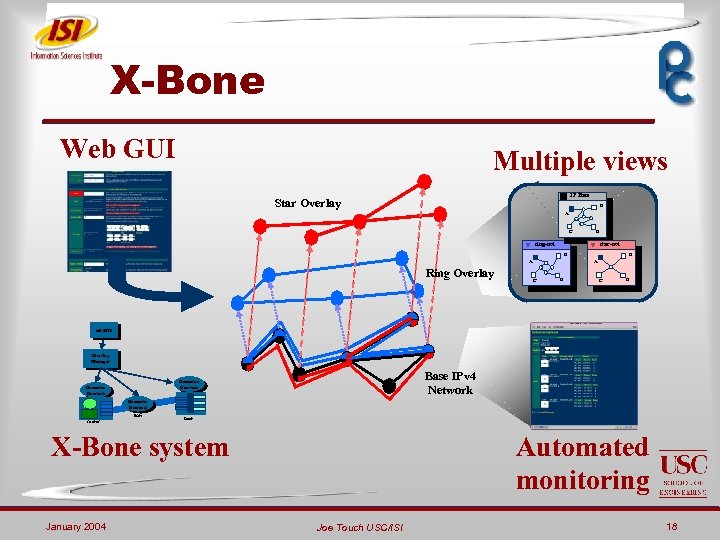 X-Bone Web GUI Multiple views IP Base Star Overlay B A C D ring-ovl star-ovl B A Ring Overlay B A C D xd GUI Overlay Manager Base IPv 4 Network Resource Daemon link router host Automated monitoring X-Bone system January 2004 Joe Touch USC/ISI 18
X-Bone Web GUI Multiple views IP Base Star Overlay B A C D ring-ovl star-ovl B A Ring Overlay B A C D xd GUI Overlay Manager Base IPv 4 Network Resource Daemon link router host Automated monitoring X-Bone system January 2004 Joe Touch USC/ISI 18
 The X-Bone is… ¬ A system for automated overlay deployment ¬ Among a closed set of trusted hosts and routers ¬ Pprovide coordination, configuration, management ¬ Many details are plug-replaceable ¬ New tricks for overlays (use of overlays) ¬ Overlays on overlays on … ¬ Fault tolerance, service deployment ¬ Member in multiple overlays, in single multiple times ¬ New tricks for old dogs (extend net arch. ) ¬ Use existing stacks and applications January 2004 Joe Touch USC/ISI 19
The X-Bone is… ¬ A system for automated overlay deployment ¬ Among a closed set of trusted hosts and routers ¬ Pprovide coordination, configuration, management ¬ Many details are plug-replaceable ¬ New tricks for overlays (use of overlays) ¬ Overlays on overlays on … ¬ Fault tolerance, service deployment ¬ Member in multiple overlays, in single multiple times ¬ New tricks for old dogs (extend net arch. ) ¬ Use existing stacks and applications January 2004 Joe Touch USC/ISI 19
 What We Don’t Do… ¬ Optimize the overlay topology ¬ ¬ We use a plug-in module (AI folk can provide) It requires network status (emerging now) Fault tolerance only via ground truth (admin. issue) X-Bone is capability more than performance (now) ¬ Non-IP overlays ¬ IP is the interoperability layer ¬ IP recurses / stacks nicely January 2004 Joe Touch USC/ISI 20
What We Don’t Do… ¬ Optimize the overlay topology ¬ ¬ We use a plug-in module (AI folk can provide) It requires network status (emerging now) Fault tolerance only via ground truth (admin. issue) X-Bone is capability more than performance (now) ¬ Non-IP overlays ¬ IP is the interoperability layer ¬ IP recurses / stacks nicely January 2004 Joe Touch USC/ISI 20
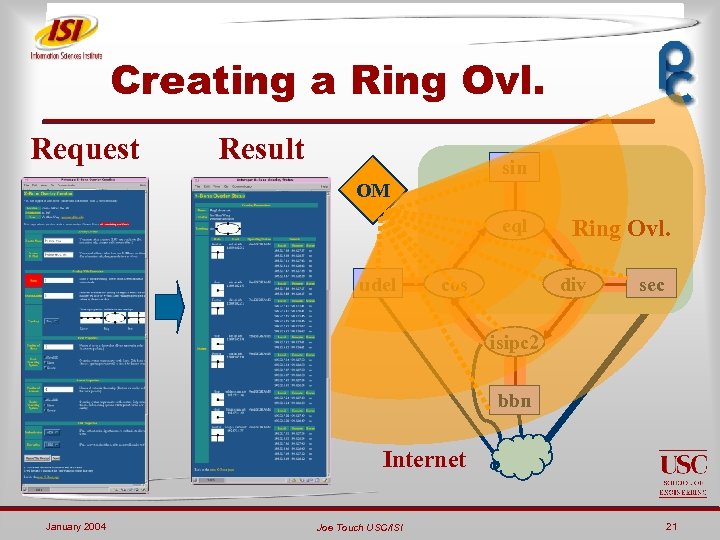 Creating a Ring Ovl. Request Result sin OM eql udel cos Ring Ovl. div sec isipc 2 bbn Internet January 2004 Joe Touch USC/ISI 21
Creating a Ring Ovl. Request Result sin OM eql udel cos Ring Ovl. div sec isipc 2 bbn Internet January 2004 Joe Touch USC/ISI 21
 Potential Uses ¬ Test new protocols ¬ Test denial-of-service solutions ¬ Deploy new services incrementally ¬ Dynamic routing, proxylets, security ¬ Increase lab & testbed utility ¬ Overlapping nets, add delay & loss ¬ Scale to 10, 000 nodes ¬ Simplify view of topology ¬ Support fault tolerance ¬ Added level of recovery January 2004 Joe Touch USC/ISI 22
Potential Uses ¬ Test new protocols ¬ Test denial-of-service solutions ¬ Deploy new services incrementally ¬ Dynamic routing, proxylets, security ¬ Increase lab & testbed utility ¬ Overlapping nets, add delay & loss ¬ Scale to 10, 000 nodes ¬ Simplify view of topology ¬ Support fault tolerance ¬ Added level of recovery January 2004 Joe Touch USC/ISI 22
 Features ¬ Secure ¬ X. 509 certs, SSL control, ACLs ¬ Resilient ¬ Heartbeats with auto-dismantle ¬ Crash recovery/restore ¬ Detects/avoids replays; idempotent actions w/rollback ¬ Overlay features ¬ Dummynet, IPsec ¬ Application deployment ¬ ABone ¬ Squid proxy system (U. Catalonia) ¬ Planet. Lab-like slice of vservers January 2004 Joe Touch USC/ISI 23
Features ¬ Secure ¬ X. 509 certs, SSL control, ACLs ¬ Resilient ¬ Heartbeats with auto-dismantle ¬ Crash recovery/restore ¬ Detects/avoids replays; idempotent actions w/rollback ¬ Overlay features ¬ Dummynet, IPsec ¬ Application deployment ¬ ABone ¬ Squid proxy system (U. Catalonia) ¬ Planet. Lab-like slice of vservers January 2004 Joe Touch USC/ISI 23
 Recent Additions ¬ In 3. 0 (1/2004): ¬ ¬ ¬ IPv 6 Dynamic DNS/DNSsec Cisco via buddy host Zebra dynamic routing User-specified topology XML-based API ¬ Coming soon ¬ Revisitation (using network stacks) ¬ Recursion January 2004 Joe Touch USC/ISI 24
Recent Additions ¬ In 3. 0 (1/2004): ¬ ¬ ¬ IPv 6 Dynamic DNS/DNSsec Cisco via buddy host Zebra dynamic routing User-specified topology XML-based API ¬ Coming soon ¬ Revisitation (using network stacks) ¬ Recursion January 2004 Joe Touch USC/ISI 24
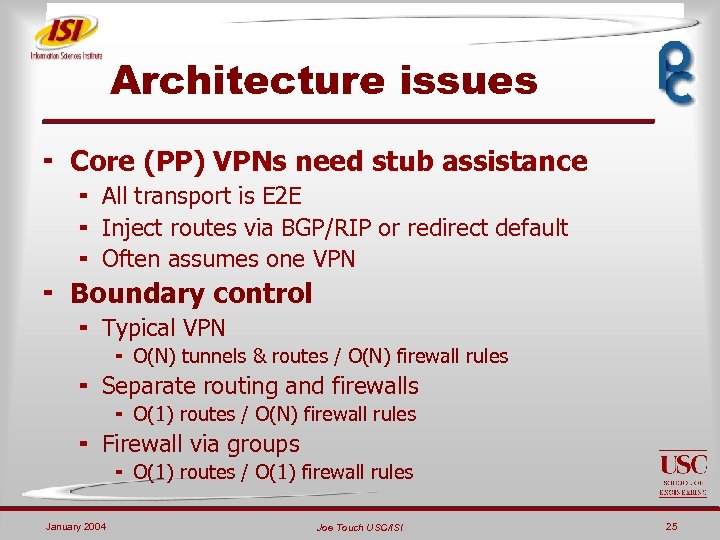 Architecture issues ¬ Core (PP) VPNs need stub assistance ¬ All transport is E 2 E ¬ Inject routes via BGP/RIP or redirect default ¬ Often assumes one VPN ¬ Boundary control ¬ Typical VPN ¬ O(N) tunnels & routes / O(N) firewall rules ¬ Separate routing and firewalls ¬ O(1) routes / O(N) firewall rules ¬ Firewall via groups ¬ O(1) routes / O(1) firewall rules January 2004 Joe Touch USC/ISI 25
Architecture issues ¬ Core (PP) VPNs need stub assistance ¬ All transport is E 2 E ¬ Inject routes via BGP/RIP or redirect default ¬ Often assumes one VPN ¬ Boundary control ¬ Typical VPN ¬ O(N) tunnels & routes / O(N) firewall rules ¬ Separate routing and firewalls ¬ O(1) routes / O(N) firewall rules ¬ Firewall via groups ¬ O(1) routes / O(1) firewall rules January 2004 Joe Touch USC/ISI 25
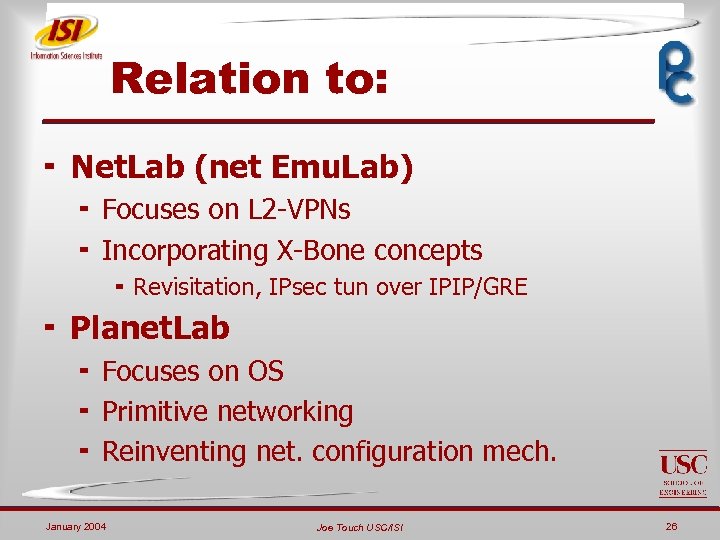 Relation to: ¬ Net. Lab (net Emu. Lab) ¬ Focuses on L 2 -VPNs ¬ Incorporating X-Bone concepts ¬ Revisitation, IPsec tun over IPIP/GRE ¬ Planet. Lab ¬ Focuses on OS ¬ Primitive networking ¬ Reinventing net. configuration mech. January 2004 Joe Touch USC/ISI 26
Relation to: ¬ Net. Lab (net Emu. Lab) ¬ Focuses on L 2 -VPNs ¬ Incorporating X-Bone concepts ¬ Revisitation, IPsec tun over IPIP/GRE ¬ Planet. Lab ¬ Focuses on OS ¬ Primitive networking ¬ Reinventing net. configuration mech. January 2004 Joe Touch USC/ISI 26
 Availability (and not)… ¬ http: //www. isi. edu/xbone ¬ Platforms ¬ ¬ Free. BSD 4. x/5. x (IPv 4/6 IPsec) Linux Red. Hat (IPv 4/IPsec only) Cisco via buddy host (IPv 4 IPsec, IPv 6) Under development/test: ¬ Net. BSD (tested only) ¬ Mac. OS X (prelim. testing) ¬ Platforms not capable of VIs: ¬ ¬ Windows 2 K/XP Linux Free. S/WAN Vxworks, Janos Planet. Lab inside vserver January 2004 Joe Touch USC/ISI 27
Availability (and not)… ¬ http: //www. isi. edu/xbone ¬ Platforms ¬ ¬ Free. BSD 4. x/5. x (IPv 4/6 IPsec) Linux Red. Hat (IPv 4/IPsec only) Cisco via buddy host (IPv 4 IPsec, IPv 6) Under development/test: ¬ Net. BSD (tested only) ¬ Mac. OS X (prelim. testing) ¬ Platforms not capable of VIs: ¬ ¬ Windows 2 K/XP Linux Free. S/WAN Vxworks, Janos Planet. Lab inside vserver January 2004 Joe Touch USC/ISI 27
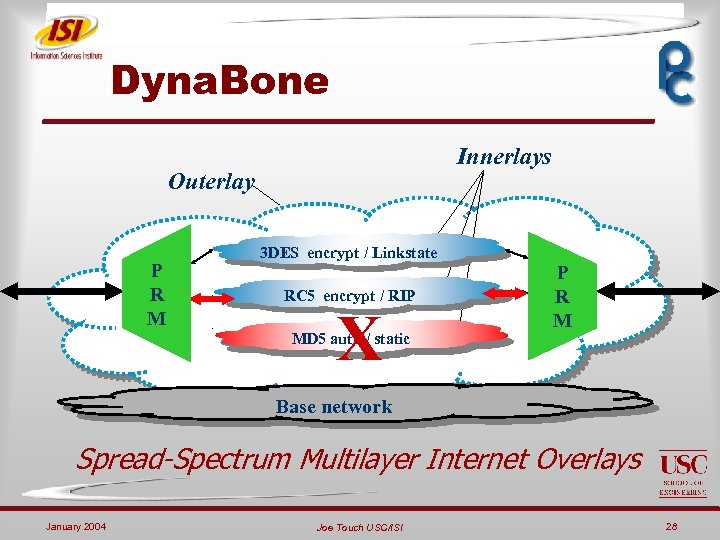 Dyna. Bone Innerlays Outerlay P R M 3 DES encrypt / Linkstate RC 5 encrypt / RIP X MD 5 auth / static P R M Base network Spread-Spectrum Multilayer Internet Overlays January 2004 Joe Touch USC/ISI 28
Dyna. Bone Innerlays Outerlay P R M 3 DES encrypt / Linkstate RC 5 encrypt / RIP X MD 5 auth / static P R M Base network Spread-Spectrum Multilayer Internet Overlays January 2004 Joe Touch USC/ISI 28
 Goals ¬ Auto platform for spread-spectrum ¬ Architecture in which to use … (see BASF) ¬ Closed-group communication ¬ E 2 E, E 2(gateway), etc. ¬ Enable multilayer defense (IP addr, SPI, decrypts) ¬ Platform for muggles ¬ Transparent to applications, protocols, OS’s ¬ Auto-deploy January 2004 Joe Touch USC/ISI 29
Goals ¬ Auto platform for spread-spectrum ¬ Architecture in which to use … (see BASF) ¬ Closed-group communication ¬ E 2 E, E 2(gateway), etc. ¬ Enable multilayer defense (IP addr, SPI, decrypts) ¬ Platform for muggles ¬ Transparent to applications, protocols, OS’s ¬ Auto-deploy January 2004 Joe Touch USC/ISI 29
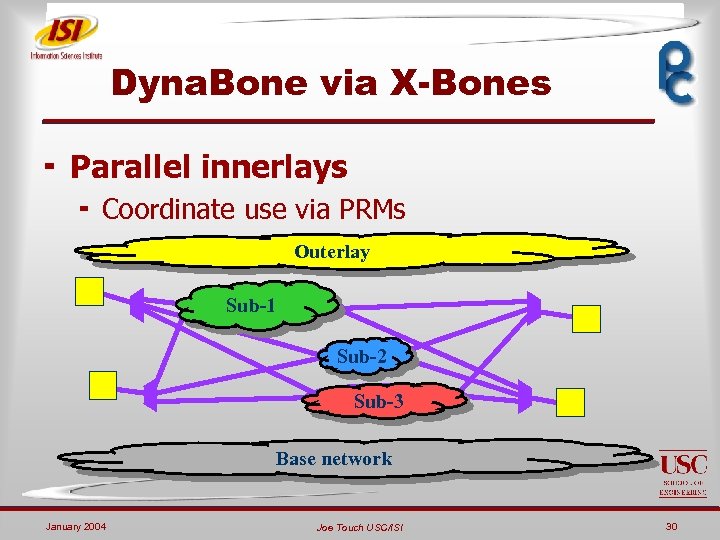 Dyna. Bone via X-Bones ¬ Parallel innerlays ¬ Coordinate use via PRMs Outerlay Sub-1 Sub-2 Sub-3 Base network January 2004 Joe Touch USC/ISI 30
Dyna. Bone via X-Bones ¬ Parallel innerlays ¬ Coordinate use via PRMs Outerlay Sub-1 Sub-2 Sub-3 Base network January 2004 Joe Touch USC/ISI 30
 Layered Overlays ¬ Innerlays ¬ A network you can gracefully disconnect ¬ Attacker-like parallelsim as a defense ¬ Outerlay ¬ Hides the Innerlays from OS, applications ¬ Allows transparent restoration ¬ Automated deployment via X-Bone ¬ User deployed, trans-AS, no new protocols ¬ Integrates heterogeneous net-level security January 2004 Joe Touch USC/ISI 31
Layered Overlays ¬ Innerlays ¬ A network you can gracefully disconnect ¬ Attacker-like parallelsim as a defense ¬ Outerlay ¬ Hides the Innerlays from OS, applications ¬ Allows transparent restoration ¬ Automated deployment via X-Bone ¬ User deployed, trans-AS, no new protocols ¬ Integrates heterogeneous net-level security January 2004 Joe Touch USC/ISI 31
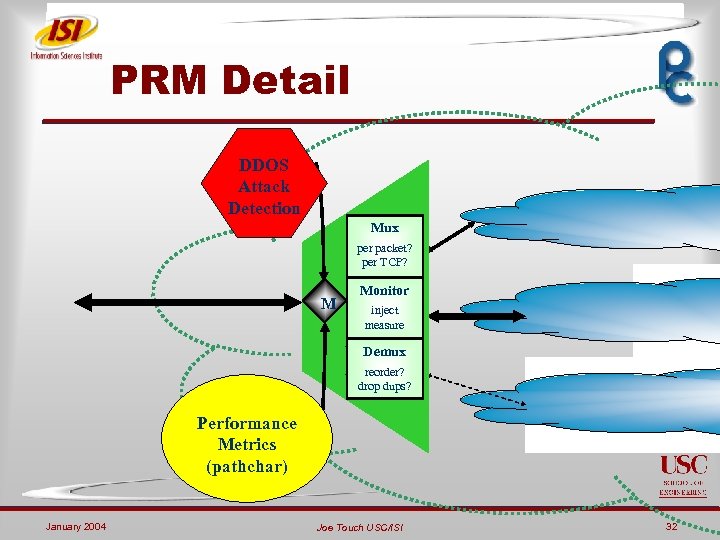 PRM Detail DDOS Attack Detection Mux P R M per packet? per TCP? M Monitor inject measure Demux reorder? drop dups? Performance Metrics (pathchar) January 2004 Joe Touch USC/ISI 32
PRM Detail DDOS Attack Detection Mux P R M per packet? per TCP? M Monitor inject measure Demux reorder? drop dups? Performance Metrics (pathchar) January 2004 Joe Touch USC/ISI 32
 Monitor & Control GUI January 2004 Joe Touch USC/ISI 33
Monitor & Control GUI January 2004 Joe Touch USC/ISI 33
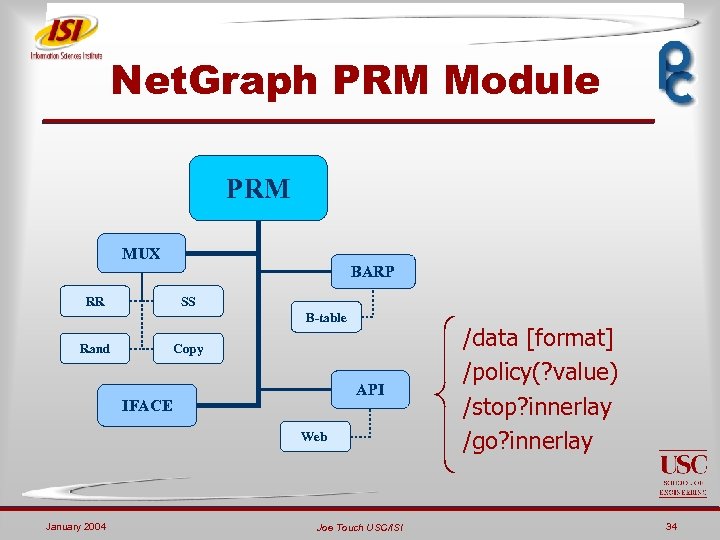 Net. Graph PRM Module PRM MUX BARP RR SS B-table Rand Copy API IFACE Web January 2004 Joe Touch USC/ISI /data [format] /policy(? value) /stop? innerlay /go? innerlay 34
Net. Graph PRM Module PRM MUX BARP RR SS B-table Rand Copy API IFACE Web January 2004 Joe Touch USC/ISI /data [format] /policy(? value) /stop? innerlay /go? innerlay 34
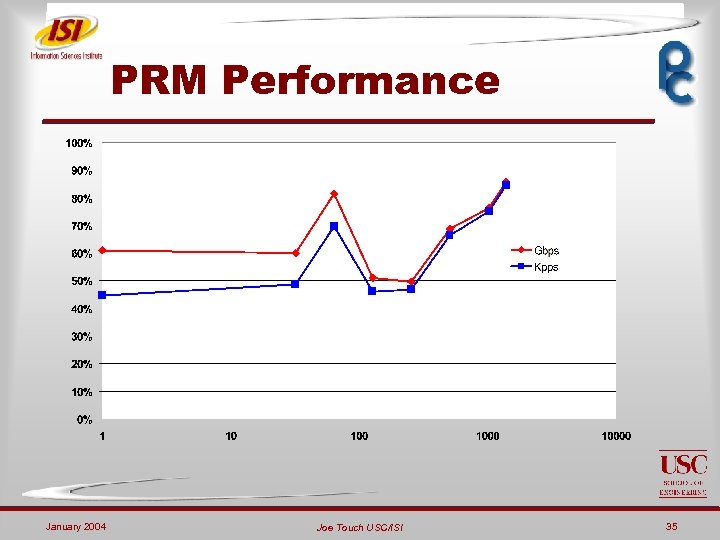 PRM Performance January 2004 Joe Touch USC/ISI 35
PRM Performance January 2004 Joe Touch USC/ISI 35
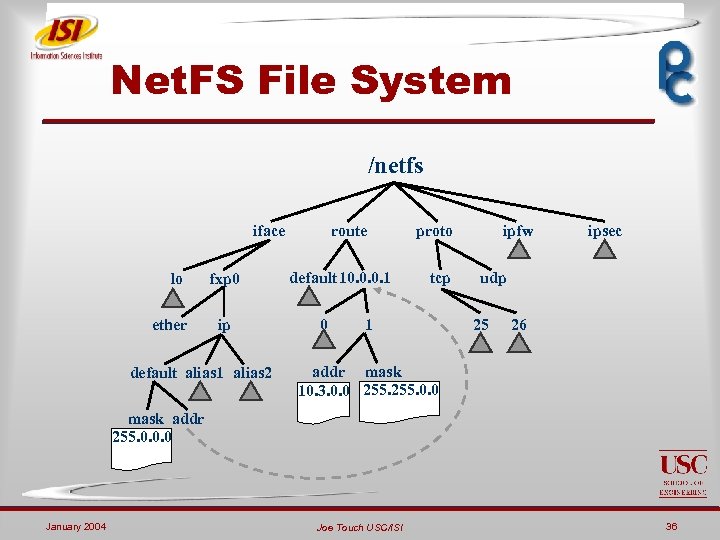 Net. FS File System /netfs iface lo ether fxp 0 ip default alias 1 alias 2 route default 10. 0. 0. 1 0 proto tcp 1 ipfw ipsec udp 25 26 addr mask 10. 3. 0. 0 255. 0. 0 mask addr 255. 0. 0. 0 January 2004 Joe Touch USC/ISI 36
Net. FS File System /netfs iface lo ether fxp 0 ip default alias 1 alias 2 route default 10. 0. 0. 1 0 proto tcp 1 ipfw ipsec udp 25 26 addr mask 10. 3. 0. 0 255. 0. 0 mask addr 255. 0. 0. 0 January 2004 Joe Touch USC/ISI 36
 Goals ¬ Simple, standard interface ¬ Across different OS’s ¬ File system API and semantics ¬ Fine-grained security ¬ User, group, world, etc. ¬ Per instance of each resource ¬ Context-dependent views ¬ Limits “ifconfig –a” response January 2004 Joe Touch USC/ISI 37
Goals ¬ Simple, standard interface ¬ Across different OS’s ¬ File system API and semantics ¬ Fine-grained security ¬ User, group, world, etc. ¬ Per instance of each resource ¬ Context-dependent views ¬ Limits “ifconfig –a” response January 2004 Joe Touch USC/ISI 37
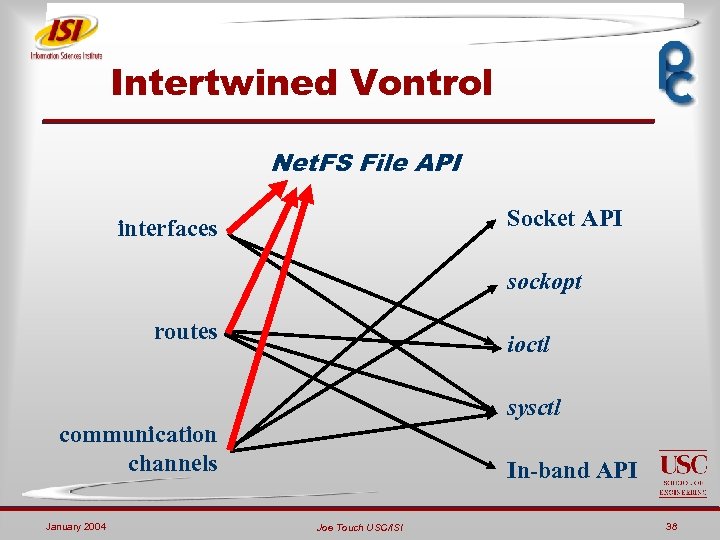 Intertwined Vontrol Net. FS File API Socket API interfaces sockopt routes ioctl sysctl communication channels January 2004 In-band API Joe Touch USC/ISI 38
Intertwined Vontrol Net. FS File API Socket API interfaces sockopt routes ioctl sysctl communication channels January 2004 In-band API Joe Touch USC/ISI 38
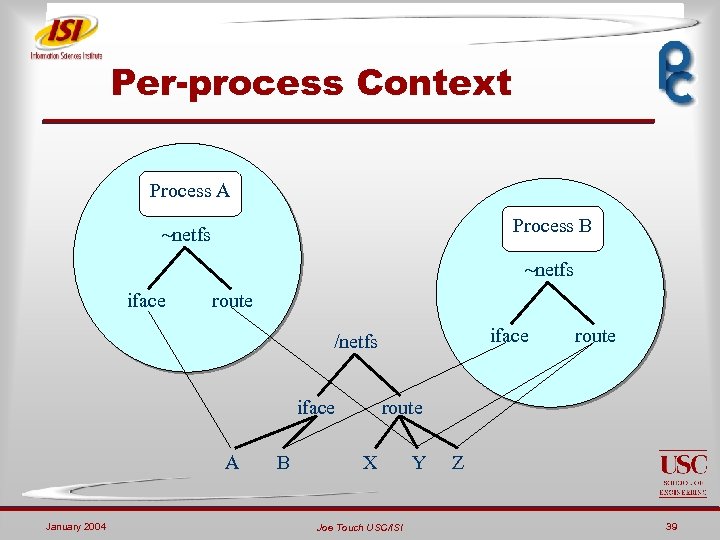 Per-process Context Process A Process B ~netfs iface route iface /netfs iface A January 2004 B route X Joe Touch USC/ISI Y Z 39
Per-process Context Process A Process B ~netfs iface route iface /netfs iface A January 2004 B route X Joe Touch USC/ISI Y Z 39
 Related Work ¬ Linux’s /procfs ¬ Processes ¬ Jail(fbsd) & vserver(linux) ¬ Limits root access to 1 IP addr per partition ¬ Plan 9’s /net ¬ Sockets ¬ Free. BSD extensions (underway) ¬ Add naming (kernel hack) to interfaces January 2004 Joe Touch USC/ISI 40
Related Work ¬ Linux’s /procfs ¬ Processes ¬ Jail(fbsd) & vserver(linux) ¬ Limits root access to 1 IP addr per partition ¬ Plan 9’s /net ¬ Sockets ¬ Free. BSD extensions (underway) ¬ Add naming (kernel hack) to interfaces January 2004 Joe Touch USC/ISI 40
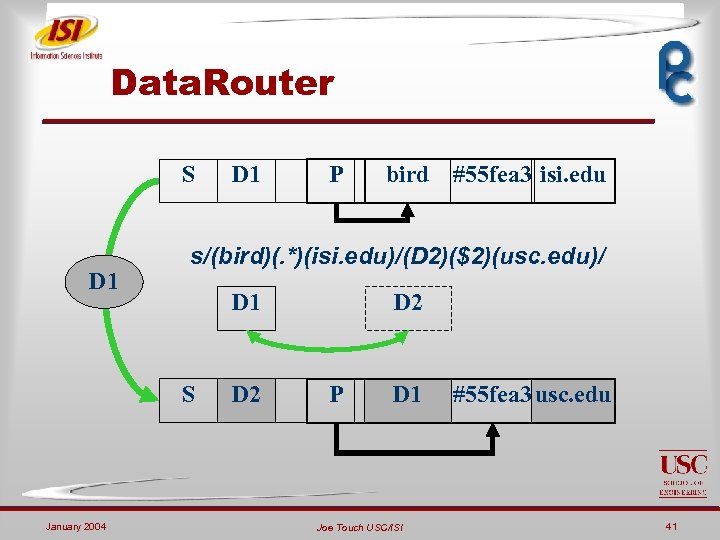 Data. Router S D 1 P bird #55 fea 3 isi. edu s/(bird)(. *)(isi. edu)/(D 2)($2)(usc. edu)/ D 1 S January 2004 D 1 D 2 P D 1 Joe Touch USC/ISI #55 fea 3 usc. edu 41
Data. Router S D 1 P bird #55 fea 3 isi. edu s/(bird)(. *)(isi. edu)/(D 2)($2)(usc. edu)/ D 1 S January 2004 D 1 D 2 P D 1 Joe Touch USC/ISI #55 fea 3 usc. edu 41
 Motivation ¬ Application-level networks are ‘bad’ ¬ Recapitulate the network layer ¬ Require additional E 2 E transport protocols ¬ Hard to compose ¬ Network-level overlays not enough ¬ Application-level info. is hidden ¬ IP forwarding is not sufficient January 2004 Joe Touch USC/ISI 42
Motivation ¬ Application-level networks are ‘bad’ ¬ Recapitulate the network layer ¬ Require additional E 2 E transport protocols ¬ Hard to compose ¬ Network-level overlays not enough ¬ Application-level info. is hidden ¬ IP forwarding is not sufficient January 2004 Joe Touch USC/ISI 42
 Goal = peer/DHT support: ¬ Useful: ¬ Supports application-directed forwarding ¬ Enables composition/integration of app. svcs. ¬ Clean: ¬ Avoids reinventing the network layer ¬ Avoids reinventing the transport layer ¬ Appropriate: ¬ Forwards fast ¬ Supports IPsec ¬ Is somewhat safe January 2004 Joe Touch USC/ISI 43
Goal = peer/DHT support: ¬ Useful: ¬ Supports application-directed forwarding ¬ Enables composition/integration of app. svcs. ¬ Clean: ¬ Avoids reinventing the network layer ¬ Avoids reinventing the transport layer ¬ Appropriate: ¬ Forwards fast ¬ Supports IPsec ¬ Is somewhat safe January 2004 Joe Touch USC/ISI 43
 Data. Router IS: ¬ Header = IP Loose Source Route ¬ Network layer option ¬ Works as an encapsulation header (ala IPsec) ¬ Entry = string ¬ Explicit application context ¬ Forwarding via string rewriting ¬ String (IP address, string’) pair January 2004 Joe Touch USC/ISI 44
Data. Router IS: ¬ Header = IP Loose Source Route ¬ Network layer option ¬ Works as an encapsulation header (ala IPsec) ¬ Entry = string ¬ Explicit application context ¬ Forwarding via string rewriting ¬ String (IP address, string’) pair January 2004 Joe Touch USC/ISI 44
 Data. Router ISN’T: ¬ Routing protocol ¬ IP doesn’t force OSPF, BGP, etc. ¬ Overlay configuration ¬ IP doesn’t force particular topology January 2004 Joe Touch USC/ISI 45
Data. Router ISN’T: ¬ Routing protocol ¬ IP doesn’t force OSPF, BGP, etc. ¬ Overlay configuration ¬ IP doesn’t force particular topology January 2004 Joe Touch USC/ISI 45
 Enabled Capabilities ¬ App. forwarding via network svc. ¬ Late-binding integration ¬ One packet: TCP/SYN w/ Google as DR ¬ Google DNS IP ¬ Anycast services ¬ First DR hop = anycast server ¬ Further hops added by appending January 2004 Joe Touch USC/ISI 46
Enabled Capabilities ¬ App. forwarding via network svc. ¬ Late-binding integration ¬ One packet: TCP/SYN w/ Google as DR ¬ Google DNS IP ¬ Anycast services ¬ First DR hop = anycast server ¬ Further hops added by appending January 2004 Joe Touch USC/ISI 46
 Quick FAQ: ¬ This is forwarding; who does routing? ¬ Application that would have done forwarding (Chord, CAN, Napster, Google, DNS) ¬ Can transport handle unbound dests? ¬ Use HIP to decouple TCP/UDP from IP ¬ What is the API? ¬ DR strings via SOCKOPT ¬ Forwarding entries via droute command ¬ Why use REs? ¬ Sufficient, efficient, complete ¬ How does it avoid breaking E 2 E? ¬ By allowing E 2 E TCP ¬ Why use a LSR IP option? ¬ Integrates w/existing ICMP, IPsec; allows ‘overlays’; transparent January 2004 Joe Touch USC/ISI 47
Quick FAQ: ¬ This is forwarding; who does routing? ¬ Application that would have done forwarding (Chord, CAN, Napster, Google, DNS) ¬ Can transport handle unbound dests? ¬ Use HIP to decouple TCP/UDP from IP ¬ What is the API? ¬ DR strings via SOCKOPT ¬ Forwarding entries via droute command ¬ Why use REs? ¬ Sufficient, efficient, complete ¬ How does it avoid breaking E 2 E? ¬ By allowing E 2 E TCP ¬ Why use a LSR IP option? ¬ Integrates w/existing ICMP, IPsec; allows ‘overlays’; transparent January 2004 Joe Touch USC/ISI 47
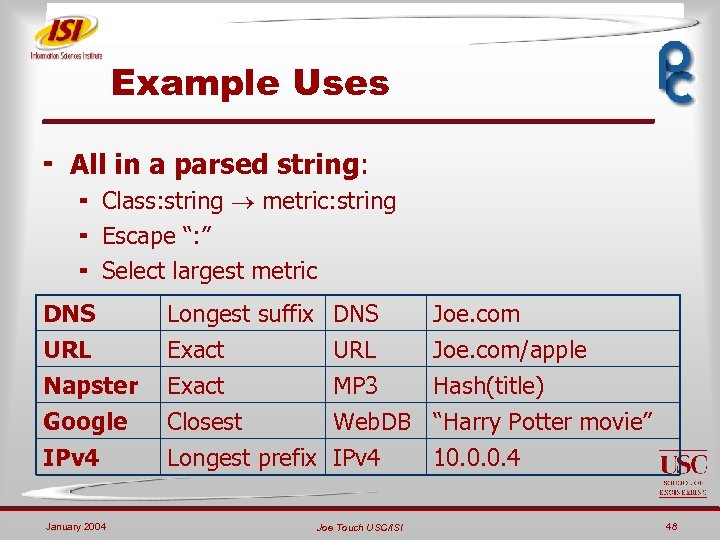 Example Uses ¬ All in a parsed string: ¬ Class: string metric: string ¬ Escape “: ” ¬ Select largest metric DNS URL Napster Google Longest suffix DNS Exact URL Exact MP 3 Closest Web. DB Joe. com/apple Hash(title) “Harry Potter movie” IPv 4 Longest prefix IPv 4 10. 0. 0. 4 January 2004 Joe Touch USC/ISI 48
Example Uses ¬ All in a parsed string: ¬ Class: string metric: string ¬ Escape “: ” ¬ Select largest metric DNS URL Napster Google Longest suffix DNS Exact URL Exact MP 3 Closest Web. DB Joe. com/apple Hash(title) “Harry Potter movie” IPv 4 Longest prefix IPv 4 10. 0. 0. 4 January 2004 Joe Touch USC/ISI 48
 Related Work ¬ Application-directed forwarding ¬ DHTs, web proxies… ¬ Google, DNS ¬ Alternate network forwarding ¬ ¬ Dbase index [Carzaniga 03] Linda [Carriero 86] Data manipilation lang. [Chandranmenon 95] Catanet, TRIAD, I 3, IPNL, Heaps, Net Ptrs… Electronic control January 2004 Joe Touch USC/ISI 49
Related Work ¬ Application-directed forwarding ¬ DHTs, web proxies… ¬ Google, DNS ¬ Alternate network forwarding ¬ ¬ Dbase index [Carzaniga 03] Linda [Carriero 86] Data manipilation lang. [Chandranmenon 95] Catanet, TRIAD, I 3, IPNL, Heaps, Net Ptrs… Electronic control January 2004 Joe Touch USC/ISI 49
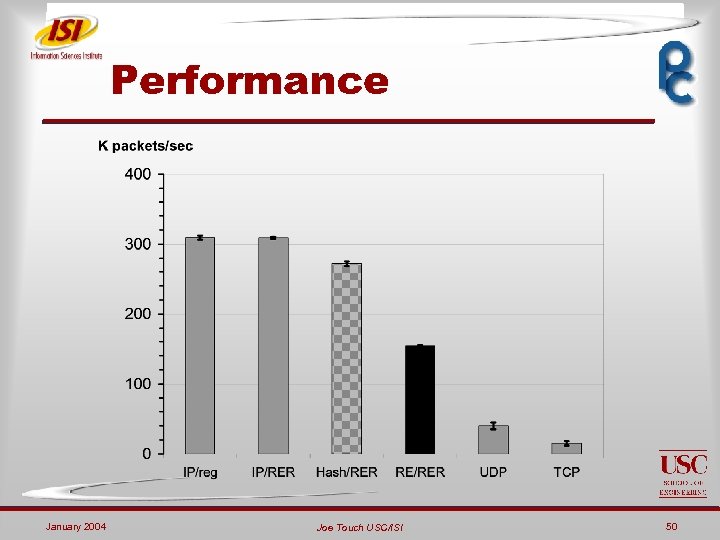 Performance January 2004 Joe Touch USC/ISI 50
Performance January 2004 Joe Touch USC/ISI 50
 Tether. Net ¬ Complete Internet IP connectivity ¬ Works behind NATs ¬ Works behind short-lease DHCP January 2004 Joe Touch USC/ISI 51
Tether. Net ¬ Complete Internet IP connectivity ¬ Works behind NATs ¬ Works behind short-lease DHCP January 2004 Joe Touch USC/ISI 51
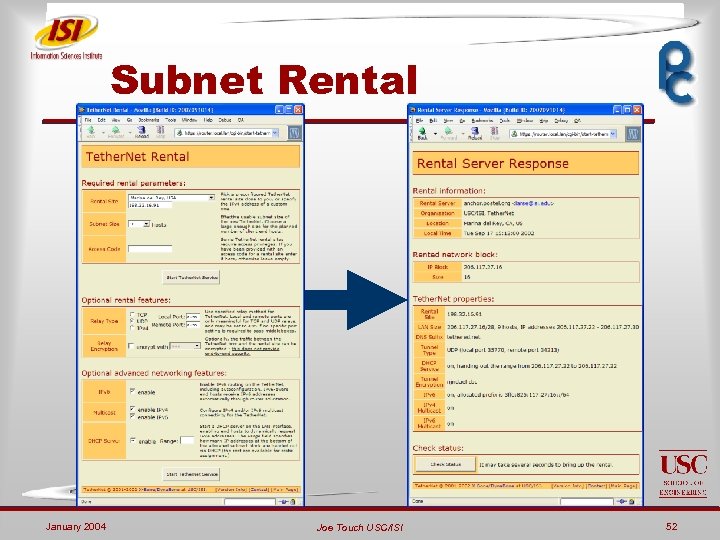 Subnet Rental January 2004 Joe Touch USC/ISI 52
Subnet Rental January 2004 Joe Touch USC/ISI 52
 Optical Internets ¬ Optical recapitulates electronic ¬ WDM = VCs ¬ Burst switching = MPLS/label switching ¬ Jump ahead to packet-based ¬ Router ¬ ¬ Queue-free architecture Forwarding via partial filters TTL decrement IP checksum ¬ LAN Protocols ¬ OCDMA MAC design January 2004 Joe Touch USC/ISI 53
Optical Internets ¬ Optical recapitulates electronic ¬ WDM = VCs ¬ Burst switching = MPLS/label switching ¬ Jump ahead to packet-based ¬ Router ¬ ¬ Queue-free architecture Forwarding via partial filters TTL decrement IP checksum ¬ LAN Protocols ¬ OCDMA MAC design January 2004 Joe Touch USC/ISI 53
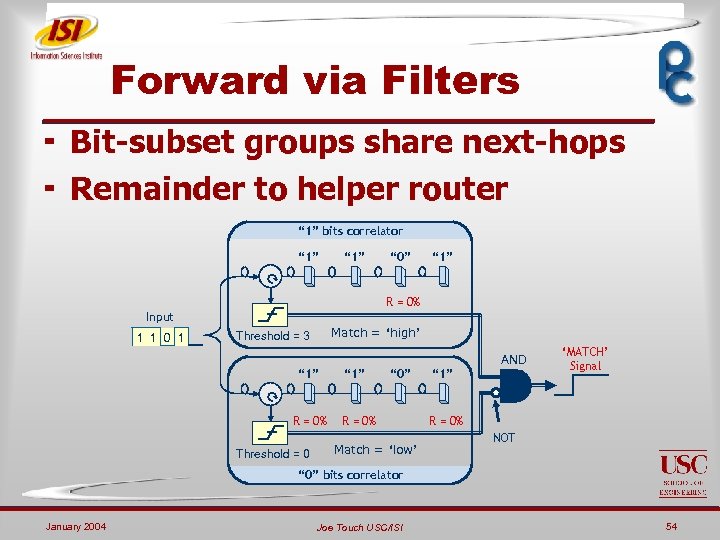 Forward via Filters ¬ Bit-subset groups share next-hops ¬ Remainder to helper router “ 1” bits correlator “ 1” “ 0” “ 1” R = 0% Input 1 1 0 1 Match = ‘high’ Threshold = 3 AND “ 1” “ 0” “ 1” ‘MATCH’ Signal R = 0% Threshold = 0 R = 0% Match = ‘low’ R = 0% NOT “ 0” bits correlator January 2004 Joe Touch USC/ISI 54
Forward via Filters ¬ Bit-subset groups share next-hops ¬ Remainder to helper router “ 1” bits correlator “ 1” “ 0” “ 1” R = 0% Input 1 1 0 1 Match = ‘high’ Threshold = 3 AND “ 1” “ 0” “ 1” ‘MATCH’ Signal R = 0% Threshold = 0 R = 0% Match = ‘low’ R = 0% NOT “ 0” bits correlator January 2004 Joe Touch USC/ISI 54
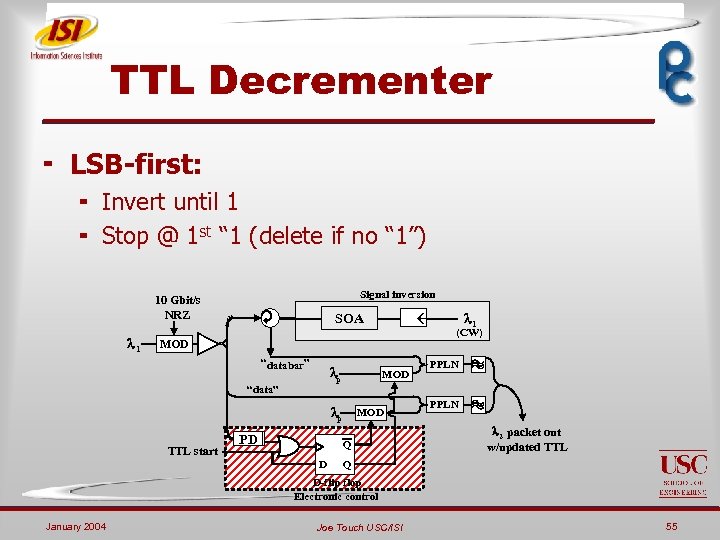 TTL Decrementer ¬ LSB-first: ¬ Invert until 1 ¬ Stop @ 1 st “ 1 (delete if no “ 1”) l 1 Signal inversion 10 Gbit/s NRZ SOA ß MOD “databar” lp “data” MOD lp TTL start PD PD MOD Q Q D D l 11 (CW) PPLN l 2 packet out w/updated TTL Q Q D-flip flop Electronic control January 2004 Joe Touch USC/ISI 55
TTL Decrementer ¬ LSB-first: ¬ Invert until 1 ¬ Stop @ 1 st “ 1 (delete if no “ 1”) l 1 Signal inversion 10 Gbit/s NRZ SOA ß MOD “databar” lp “data” MOD lp TTL start PD PD MOD Q Q D D l 11 (CW) PPLN l 2 packet out w/updated TTL Q Q D-flip flop Electronic control January 2004 Joe Touch USC/ISI 55
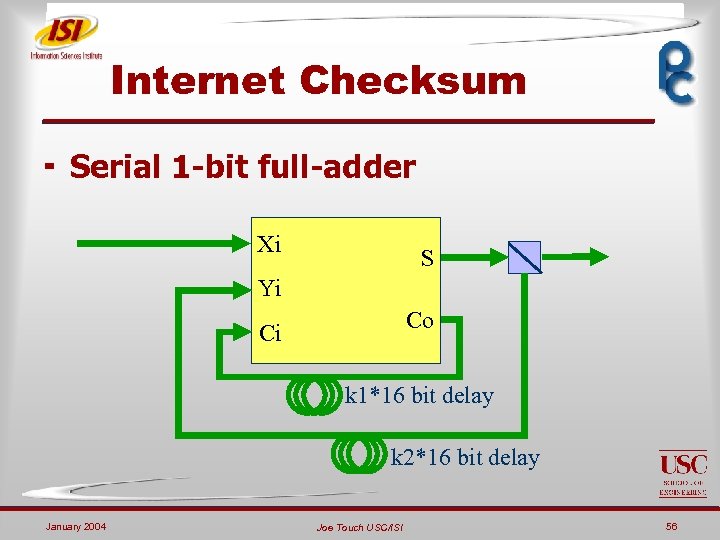 Internet Checksum ¬ Serial 1 -bit full-adder Xi S Yi Co Ci k 1*16 bit delay k 2*16 bit delay January 2004 Joe Touch USC/ISI 56
Internet Checksum ¬ Serial 1 -bit full-adder Xi S Yi Co Ci k 1*16 bit delay k 2*16 bit delay January 2004 Joe Touch USC/ISI 56
 http: //www. isi. edu/ ¬ xbone ¬ Greg Finn, Steve Hotz, Amy Hughes, Lars Eggert, Yu. Shun Wang, Nimish Kasat, Osama Dosary, Ankur Sheth, Shitanshu Shah, Wei-Chun Chou, Stephen Suryaputra, Savas Guven ¬ dynabone ¬ Venkata Pingali, Runfang Zhou ¬ netfs ¬ Josh Train ¬ (datarouter) ¬ Venkata Pingali ¬ tethernet ¬ Lars Eggert, Yu. Shun Wang ¬ pow / ocdma ¬ Joseph Bannister, Puroshutham Kamath, Michelle Hauer, Dinez Gurkin, John Mc. Geehan January 2004 Joe Touch USC/ISI 57
http: //www. isi. edu/ ¬ xbone ¬ Greg Finn, Steve Hotz, Amy Hughes, Lars Eggert, Yu. Shun Wang, Nimish Kasat, Osama Dosary, Ankur Sheth, Shitanshu Shah, Wei-Chun Chou, Stephen Suryaputra, Savas Guven ¬ dynabone ¬ Venkata Pingali, Runfang Zhou ¬ netfs ¬ Josh Train ¬ (datarouter) ¬ Venkata Pingali ¬ tethernet ¬ Lars Eggert, Yu. Shun Wang ¬ pow / ocdma ¬ Joseph Bannister, Puroshutham Kamath, Michelle Hauer, Dinez Gurkin, John Mc. Geehan January 2004 Joe Touch USC/ISI 57


