5115254dd428729daec3b8a5ab0e7010.ppt
- Количество слайдов: 35
 The phone in the cloud Utilizing resources hosted anywhere Claes Nilsson
The phone in the cloud Utilizing resources hosted anywhere Claes Nilsson
 “Software as a Service” “Cloud Computing” ……. . 2
“Software as a Service” “Cloud Computing” ……. . 2
 What about “The Phone as a Service” ……………. GPS Camera Calendar 3 Messaging
What about “The Phone as a Service” ……………. GPS Camera Calendar 3 Messaging
 Let us combine this……. . 4
Let us combine this……. . 4
 So, we all agree that… 5
So, we all agree that… 5
 The Web is THE application execution platform 6
The Web is THE application execution platform 6
 and that …. 7
and that …. 7
 Mobile Devices must be full citizens of the Cloud 8
Mobile Devices must be full citizens of the Cloud 8
 and that…. 9
and that…. 9
 Web Applications must be able to consistently utilize Cloud Resources as well as Local Device Resources 10
Web Applications must be able to consistently utilize Cloud Resources as well as Local Device Resources 10
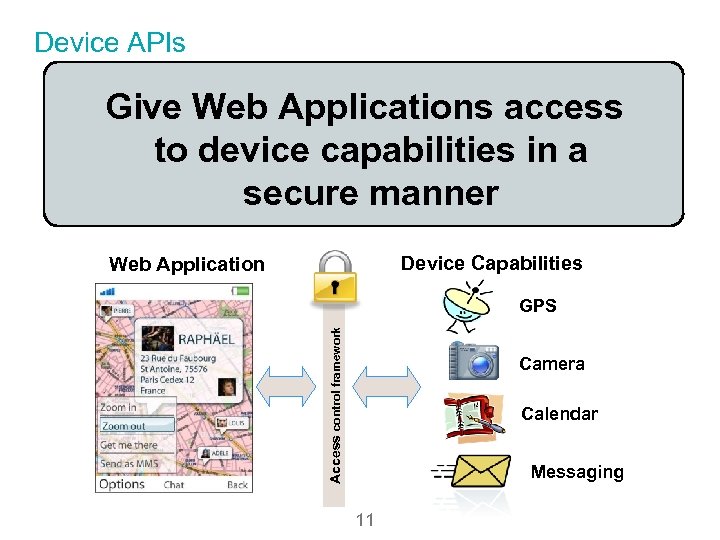 Device APIs Give Web Applications access to device capabilities in a secure manner Device Capabilities Web Application Access control framework GPS Camera Calendar Messaging 11
Device APIs Give Web Applications access to device capabilities in a secure manner Device Capabilities Web Application Access control framework GPS Camera Calendar Messaging 11
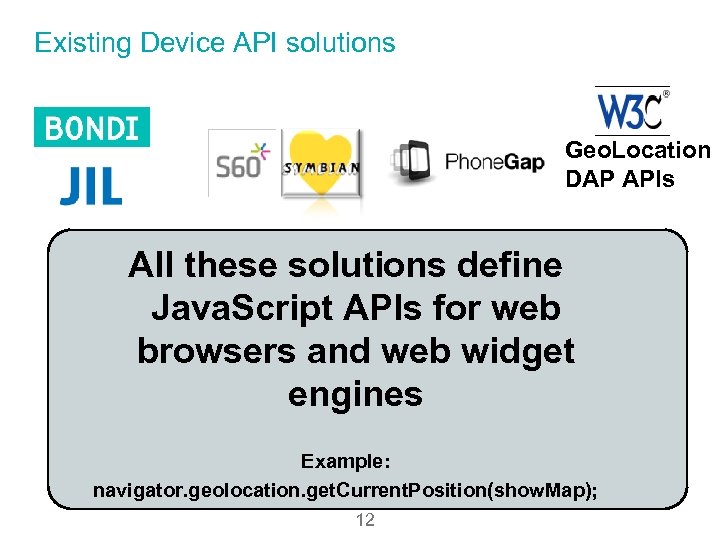 Existing Device API solutions Geo. Location DAP APIs All these solutions define Java. Script APIs for web browsers and web widget engines Example: navigator. geolocation. get. Current. Position(show. Map); 12
Existing Device API solutions Geo. Location DAP APIs All these solutions define Java. Script APIs for web browsers and web widget engines Example: navigator. geolocation. get. Current. Position(show. Map); 12
 Security is a tricky beast! 13
Security is a tricky beast! 13
 One approach is control by some trusted authority 14
One approach is control by some trusted authority 14
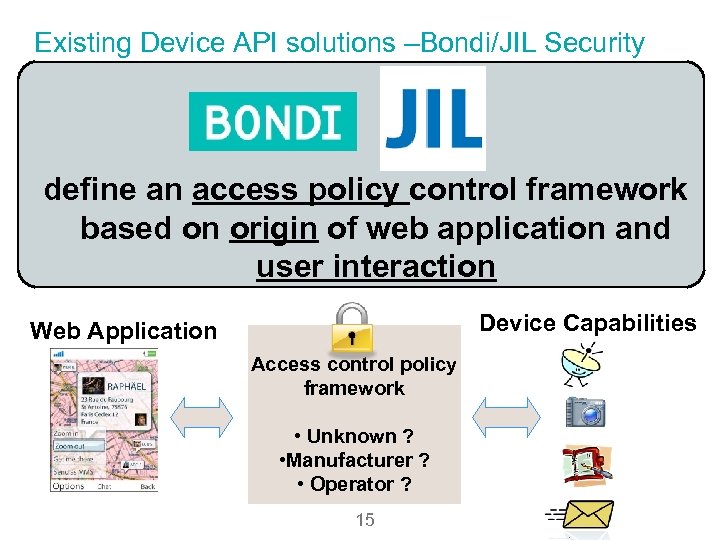 Existing Device API solutions –Bondi/JIL Security define an access policy control framework based on origin of web application and user interaction Device Capabilities Web Application Access control policy framework • Unknown ? • Manufacturer ? • Operator ? 15
Existing Device API solutions –Bondi/JIL Security define an access policy control framework based on origin of web application and user interaction Device Capabilities Web Application Access control policy framework • Unknown ? • Manufacturer ? • Operator ? 15
 Existing Device API solutions – Bondi/JIL policy security model Control by a configured access policy Examples: • “A Widget whose signature chains to operator root certificate can read and write from the PIM databases” • “A Widget downloaded from weather. com can access geolocation coordinates if the user says it’s OK” 16
Existing Device API solutions – Bondi/JIL policy security model Control by a configured access policy Examples: • “A Widget whose signature chains to operator root certificate can read and write from the PIM databases” • “A Widget downloaded from weather. com can access geolocation coordinates if the user says it’s OK” 16
 Another approach is full user control (and responsibility) 17
Another approach is full user control (and responsibility) 17
 Security – implicit user consent examples Full user control • user must press camera shutter • user must state granularity of location • user must inspect message and press “send” • 18
Security – implicit user consent examples Full user control • user must press camera shutter • user must state granularity of location • user must inspect message and press “send” • 18
 Device APIs – work in progress Device API and Policy (DAP) WG • Main SDO for Device APIs • SEMC active – support for W 3 C DAP is our main strategic direction for device APIs • Other members; Nokia, Vodafone, Google, Opera, Orange, AT&T, Telefonica, OMTP, Aplix, Intel…. . . • W 3 C DAP Website 19
Device APIs – work in progress Device API and Policy (DAP) WG • Main SDO for Device APIs • SEMC active – support for W 3 C DAP is our main strategic direction for device APIs • Other members; Nokia, Vodafone, Google, Opera, Orange, AT&T, Telefonica, OMTP, Aplix, Intel…. . . • W 3 C DAP Website 19
 Device API and Policy WG So far Java. Script interfaces defined Contacts File Writer File Directories System Calendar Media Capture System information and Sensors 20 Messaging Gallery
Device API and Policy WG So far Java. Script interfaces defined Contacts File Writer File Directories System Calendar Media Capture System information and Sensors 20 Messaging Gallery
 Device API and Policy WG In addition an optional generic policy based access control framework is being worked on 21
Device API and Policy WG In addition an optional generic policy based access control framework is being worked on 21
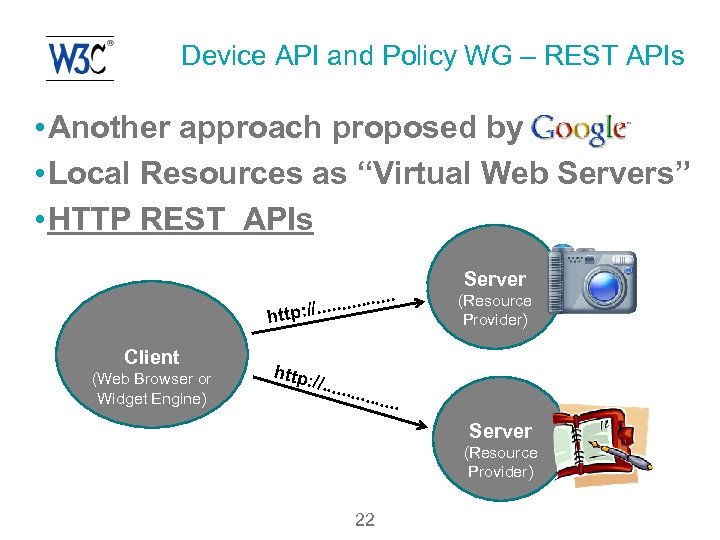 Device API and Policy WG – REST APIs • Another approach proposed by • Local Resources as “Virtual Web Servers” • HTTP REST APIs. . . tp: //. . ht Client (Web Browser or Widget Engine) http: //. . . Server (Resource Provider) 22
Device API and Policy WG – REST APIs • Another approach proposed by • Local Resources as “Virtual Web Servers” • HTTP REST APIs. . . tp: //. . ht Client (Web Browser or Widget Engine) http: //. . . Server (Resource Provider) 22
 Device API and Policy WG – REST APIs • APIs as URIs: • Example: http: //localhost/dap/contacts/create. json? . . . &name=Mr. %20 Robert%20 Smith%20 Jr &nicknames=Bob • Access through standard HTTP methods GET, POST, PUT, DELETE • More reading Rest Introduction 23
Device API and Policy WG – REST APIs • APIs as URIs: • Example: http: //localhost/dap/contacts/create. json? . . . &name=Mr. %20 Robert%20 Smith%20 Jr &nicknames=Bob • Access through standard HTTP methods GET, POST, PUT, DELETE • More reading Rest Introduction 23
 Device API and Policy WG – REST APIs • HTTP REST API advantages ØLanguage independent ØA resource can be situated "anywhere“ v. In mobile device, in PC, in accessory, in server… ØA resource can be accessed from “anywhere” ØLeverage on existing HTTP access control mechanisms 24
Device API and Policy WG – REST APIs • HTTP REST API advantages ØLanguage independent ØA resource can be situated "anywhere“ v. In mobile device, in PC, in accessory, in server… ØA resource can be accessed from “anywhere” ØLeverage on existing HTTP access control mechanisms 24
 SEMC - access to local resources through in-device web server Web Application Internet Device JS libraries to hide complex REST-coding Browser Any native API can be bound to a web API REST Device APIs New web APIs by upgrading in-device server Access Control In-device Web Server 25 Native Device APIs
SEMC - access to local resources through in-device web server Web Application Internet Device JS libraries to hide complex REST-coding Browser Any native API can be bound to a web API REST Device APIs New web APIs by upgrading in-device server Access Control In-device Web Server 25 Native Device APIs
 Device API and Policy WG – Powerbox • Powerbox • Proposed by , SEMC and Mozilla Labs • Supports discovery and interaction with resources independent of where these resources are hosted or how they are produced • Security and Privacy purely user controlled 26
Device API and Policy WG – Powerbox • Powerbox • Proposed by , SEMC and Mozilla Labs • Supports discovery and interaction with resources independent of where these resources are hosted or how they are produced • Security and Privacy purely user controlled 26
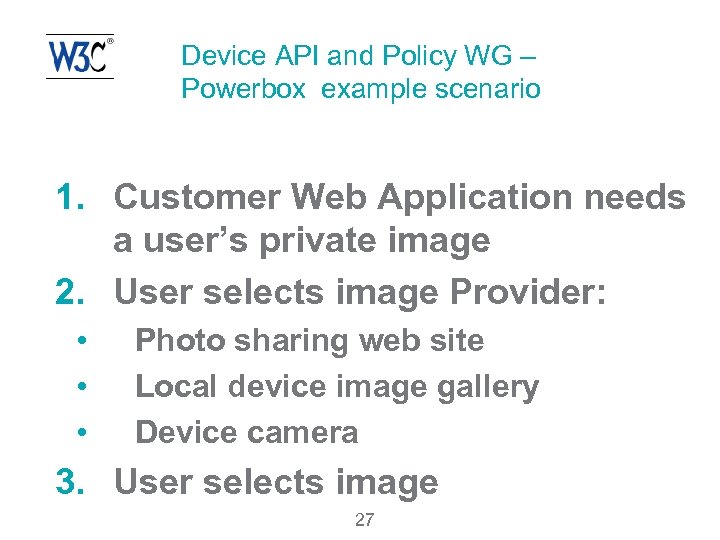 Device API and Policy WG – Powerbox example scenario 1. Customer Web Application needs a user’s private image 2. User selects image Provider: • • • Photo sharing web site Local device image gallery Device camera 3. User selects image 27
Device API and Policy WG – Powerbox example scenario 1. Customer Web Application needs a user’s private image 2. User selects image Provider: • • • Photo sharing web site Local device image gallery Device camera 3. User selects image 27
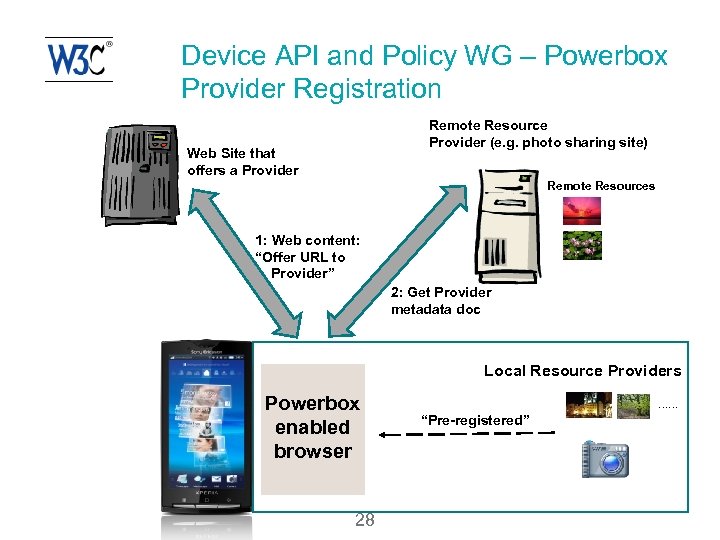 Device API and Policy WG – Powerbox Provider Registration Remote Resource Provider (e. g. photo sharing site) Web Site that offers a Provider Remote Resources 1: Web content: “Offer URL to Provider” 2: Get Provider metadata doc Local Resource Providers Powerbox enabled browser 28 …… “Pre-registered”
Device API and Policy WG – Powerbox Provider Registration Remote Resource Provider (e. g. photo sharing site) Web Site that offers a Provider Remote Resources 1: Web content: “Offer URL to Provider” 2: Get Provider metadata doc Local Resource Providers Powerbox enabled browser 28 …… “Pre-registered”
 Device API and Policy WG – Powerbox User selects remote Provider Remote Resource Provider (e. g. photo sharing site) Customer Web Site Remote Resources 1: Web Application: “Request image” 2: User selects Remote Resource Provider 3: Powerbox sends introduction request to Provider 4: Provider returns web page that lets user choose image 5: Provider provides link to selected image Powerbox enabled browser 29
Device API and Policy WG – Powerbox User selects remote Provider Remote Resource Provider (e. g. photo sharing site) Customer Web Site Remote Resources 1: Web Application: “Request image” 2: User selects Remote Resource Provider 3: Powerbox sends introduction request to Provider 4: Provider returns web page that lets user choose image 5: Provider provides link to selected image Powerbox enabled browser 29
 Device API and Policy WG – Powerbox User selects device gallery Provider Customer 1: Web Application: “Request image” Local Resource Providers Powerbox enabled browser 30 2: User selects device gallery Provider 3: Powerbox sends introduction request to local gallery Provider 4: Provider lets user choose image 5: Provider provides link to selected image
Device API and Policy WG – Powerbox User selects device gallery Provider Customer 1: Web Application: “Request image” Local Resource Providers Powerbox enabled browser 30 2: User selects device gallery Provider 3: Powerbox sends introduction request to local gallery Provider 4: Provider lets user choose image 5: Provider provides link to selected image
 Device API and Policy WG – Powerbox User selects device camera Provider Customer 1: Web Application: “Request image” Local Resource Providers Powerbox enabled browser 31 2: User selects device camera Provider 3: Powerbox sends introduction request to local camera Provider 4: Provider activates camera 5: User takes a picture 6: Link to image provided
Device API and Policy WG – Powerbox User selects device camera Provider Customer 1: Web Application: “Request image” Local Resource Providers Powerbox enabled browser 31 2: User selects device camera Provider 3: Powerbox sends introduction request to local camera Provider 4: Provider activates camera 5: User takes a picture 6: Link to image provided
 Conclusion 32
Conclusion 32
 Use resources hosted anywhere 33
Use resources hosted anywhere 33
 • We need: ØResource discovery ØUser directed resource selection ØStandardized APIs (HTTP – REST) ØAccess and privacy control 34
• We need: ØResource discovery ØUser directed resource selection ØStandardized APIs (HTTP – REST) ØAccess and privacy control 34
 Thank you ! 35
Thank you ! 35


