4333ec34d0572e3aa18c3a930e1ba2f6.ppt
- Количество слайдов: 78
 Site Access Control Grid Middleware 3 David Groep, lecture series 2005 -2006
Site Access Control Grid Middleware 3 David Groep, lecture series 2005 -2006
 Grid Middleware III Outline n Authorisation Framework § § § n Credential Mapping and local policies § § § n SAML and XACML Scheduling and batch systems § n unix domain for jobs account mapping across clusters (LDAP, or NSS-JR) workspace service and virtualisation Policy languages § n Policies, policy combination and enforcement PDP, PIP and PEP LCAS, Grid. Site, Java. Trust. Manager getting into the mess: preserving priorities? Network and firewall issues 2
Grid Middleware III Outline n Authorisation Framework § § § n Credential Mapping and local policies § § § n SAML and XACML Scheduling and batch systems § n unix domain for jobs account mapping across clusters (LDAP, or NSS-JR) workspace service and virtualisation Policy languages § n Policies, policy combination and enforcement PDP, PIP and PEP LCAS, Grid. Site, Java. Trust. Manager getting into the mess: preserving priorities? Network and firewall issues 2
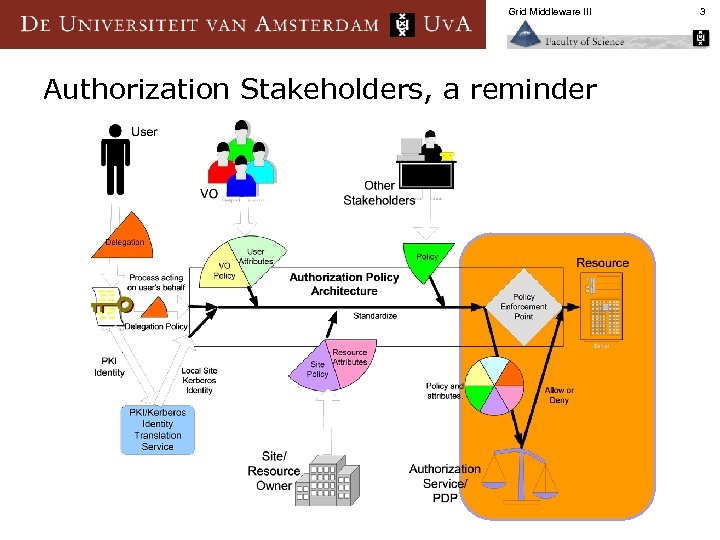 Grid Middleware III Authorization Stakeholders, a reminder 3
Grid Middleware III Authorization Stakeholders, a reminder 3
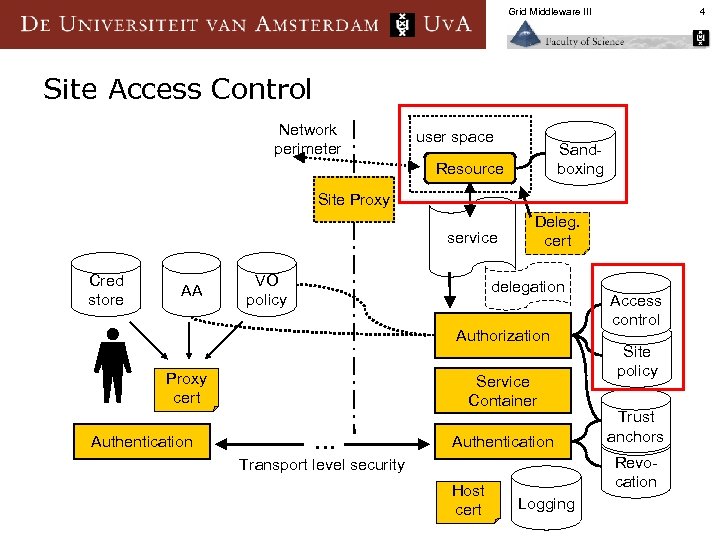 Grid Middleware III 4 Site Access Control Network perimeter user space Sandboxing Resource Site Proxy service Cred store AA VO policy Deleg. cert delegation Authorization Proxy cert Authentication Service Container . . . Authentication Site policy Trust anchors Revocation Transport level security Host cert Access control Logging
Grid Middleware III 4 Site Access Control Network perimeter user space Sandboxing Resource Site Proxy service Cred store AA VO policy Deleg. cert delegation Authorization Proxy cert Authentication Service Container . . . Authentication Site policy Trust anchors Revocation Transport level security Host cert Access control Logging
 Grid Middleware III What Problems should we solve n Fit ‘external’ users into existing infrastructure § n enforce (local) security policies § n fork jobs, batch queuing systems, disks & mass stores, … e. g. a panic button, blacklisting of users ensure that global (VO) policies are satisfied locally § in as far as possible, given local mechanisms 5
Grid Middleware III What Problems should we solve n Fit ‘external’ users into existing infrastructure § n enforce (local) security policies § n fork jobs, batch queuing systems, disks & mass stores, … e. g. a panic button, blacklisting of users ensure that global (VO) policies are satisfied locally § in as far as possible, given local mechanisms 5
 Grid Middleware III What To Do? 1. 2. 3. collect policies that need to be enforced collect the information on which to base the decision make the decision 6
Grid Middleware III What To Do? 1. 2. 3. collect policies that need to be enforced collect the information on which to base the decision make the decision 6
 Grid Middleware III Distinct pieces in the process flow n Authentication n Authorization § § n results in a yes/no decision possibly with obligations Service access § For legacy job execution services (Unix, Win 32), need an execution environment with a system credential: Credential Mapping needed (site-local, to preserve autonomy) § For hosted services execute the service request, taking into account service-specific access controls (such as ACLs for file catalogue access) 7
Grid Middleware III Distinct pieces in the process flow n Authentication n Authorization § § n results in a yes/no decision possibly with obligations Service access § For legacy job execution services (Unix, Win 32), need an execution environment with a system credential: Credential Mapping needed (site-local, to preserve autonomy) § For hosted services execute the service request, taking into account service-specific access controls (such as ACLs for file catalogue access) 7
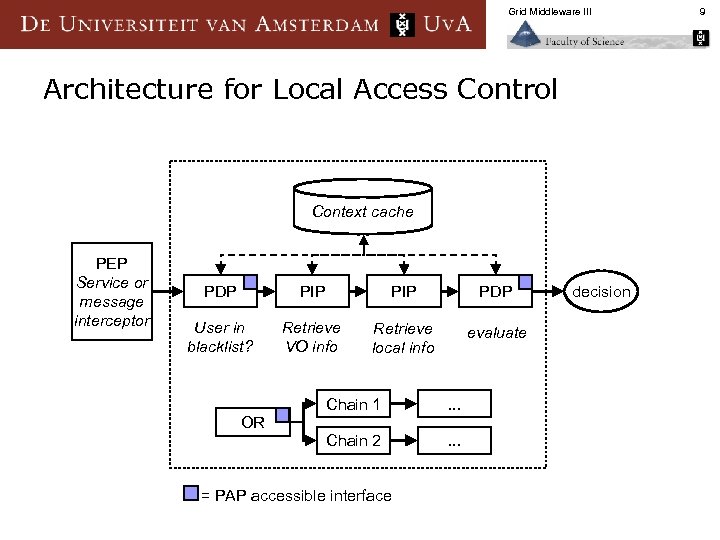 Grid Middleware III Architecture for Local Access Control Context cache PEP Service or message interceptor PDP PIP PDP User in blacklist? Retrieve VO info Retrieve local info evaluate Chain 1 . . . Chain 2 . . . OR = PAP accessible interface decision 9
Grid Middleware III Architecture for Local Access Control Context cache PEP Service or message interceptor PDP PIP PDP User in blacklist? Retrieve VO info Retrieve local info evaluate Chain 1 . . . Chain 2 . . . OR = PAP accessible interface decision 9
 Grid Middleware III Authorization Framework components n Policy Decision Point (PDP) makes a binary “yes/no” decision § based on a policy, that can be nested § n Policy Information Point (PIP) extract information from sources, needed to provide the assertions for making the decision § Policies can be ‘hybrid’ § § n “SAML with obligations”, where the policy evaluates to Yes/No, but a Yes carries specific obligations for the PEP to enforce (such as an account mapping) Policy Enforcement Point (PEP) § enforce the yes/no decision of a PDP 10
Grid Middleware III Authorization Framework components n Policy Decision Point (PDP) makes a binary “yes/no” decision § based on a policy, that can be nested § n Policy Information Point (PIP) extract information from sources, needed to provide the assertions for making the decision § Policies can be ‘hybrid’ § § n “SAML with obligations”, where the policy evaluates to Yes/No, but a Yes carries specific obligations for the PEP to enforce (such as an account mapping) Policy Enforcement Point (PEP) § enforce the yes/no decision of a PDP 10
 Grid Middleware III A ‘perfectly’ integrated model 1. Collect policies and assertions through PIPs § § § 2. attributes pushed by the client, e. g. VOMS-enabled proxies attributed retrieved via a pull mode (Shib-style, e. g. via WAYF) policies that constrain usage (restricted delegation) site-local policies resource-local policies Assert their authenticity and validity § § incoming policies and assertions should be signed (authentic) not expired and recognised by the deciding party (valid) 3. Evaluate all these policies together in a (single) PDP 4. Possibly, return obligations for e. g. unix system integration 11
Grid Middleware III A ‘perfectly’ integrated model 1. Collect policies and assertions through PIPs § § § 2. attributes pushed by the client, e. g. VOMS-enabled proxies attributed retrieved via a pull mode (Shib-style, e. g. via WAYF) policies that constrain usage (restricted delegation) site-local policies resource-local policies Assert their authenticity and validity § § incoming policies and assertions should be signed (authentic) not expired and recognised by the deciding party (valid) 3. Evaluate all these policies together in a (single) PDP 4. Possibly, return obligations for e. g. unix system integration 11
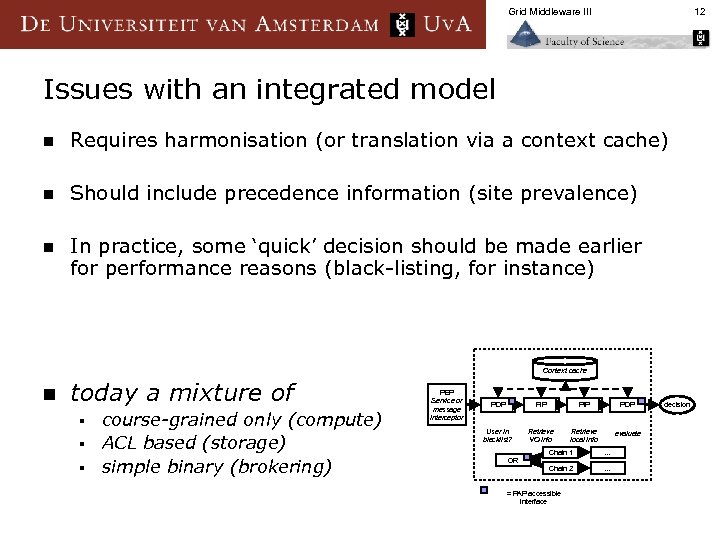 Grid Middleware III 12 Issues with an integrated model n Requires harmonisation (or translation via a context cache) n Should include precedence information (site prevalence) n In practice, some ‘quick’ decision should be made earlier for performance reasons (black-listing, for instance) Context cache n today a mixture of course-grained only (compute) § ACL based (storage) § simple binary (brokering) § PEP Service or message interceptor PDP PIP PDP User in blacklist? Retrieve VO info Retrieve local info evaluate OR Chain 1 . . . Chain 2 . . . = PAP accessible interface decision
Grid Middleware III 12 Issues with an integrated model n Requires harmonisation (or translation via a context cache) n Should include precedence information (site prevalence) n In practice, some ‘quick’ decision should be made earlier for performance reasons (black-listing, for instance) Context cache n today a mixture of course-grained only (compute) § ACL based (storage) § simple binary (brokering) § PEP Service or message interceptor PDP PIP PDP User in blacklist? Retrieve VO info Retrieve local info evaluate OR Chain 1 . . . Chain 2 . . . = PAP accessible interface decision
 Grid Middleware III Issues with the model (2) n Auth. Z cannot always be cleanly separated from the service n Example: data access to the service ‘read file’ can be allowed, but access to any specific file restricted by ACLs on the file § so the Auth. Z front-end should either ‘snoop’ into the service and use the ACLs § or the business logic should do the Auth. Z (again) § see access control to services slide later 13
Grid Middleware III Issues with the model (2) n Auth. Z cannot always be cleanly separated from the service n Example: data access to the service ‘read file’ can be allowed, but access to any specific file restricted by ACLs on the file § so the Auth. Z front-end should either ‘snoop’ into the service and use the ACLs § or the business logic should do the Auth. Z (again) § see access control to services slide later 13
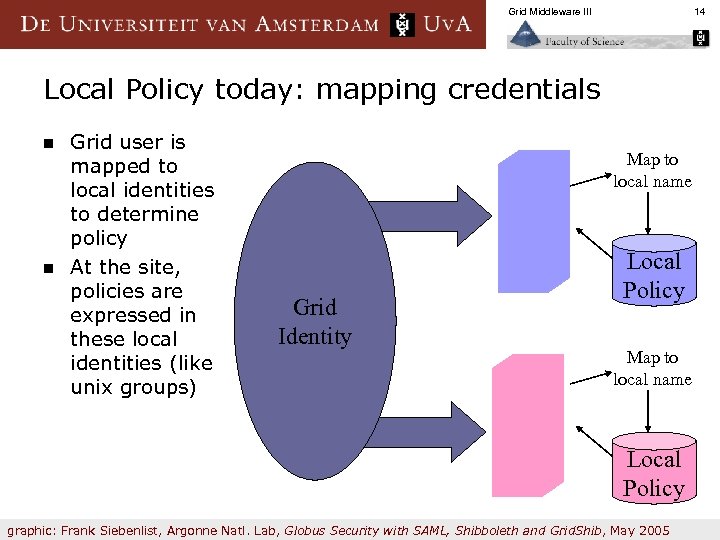 Grid Middleware III 14 Local Policy today: mapping credentials n n Grid user is mapped to local identities to determine policy At the site, policies are expressed in these local identities (like unix groups) Map to local name Grid Identity Local Policy Map to local name Local Policy graphic: Frank Siebenlist, Argonne Natl. Lab, Globus Security with SAML, Shibboleth and Grid. Shib, May 2005
Grid Middleware III 14 Local Policy today: mapping credentials n n Grid user is mapped to local identities to determine policy At the site, policies are expressed in these local identities (like unix groups) Map to local name Grid Identity Local Policy Map to local name Local Policy graphic: Frank Siebenlist, Argonne Natl. Lab, Globus Security with SAML, Shibboleth and Grid. Shib, May 2005
 Grid Middleware III Implementations today n n All separate auth. N and auth. Z most separate mapping from auth. Z where necessary, e. g. for databases and legacy execution § in most general sense, it is a handle for local policy § Faced with two worlds: Java and native (C) § Need a solution for both, but no unification yet § n Examples: C world: LCAS & LCMAPS (so this talk misses out on Prima, GUMS, g. Plazma, …) § Java: GT 4 Authorization Framework (so this talk misses out on Generic AAA, PERMIS, …) § n papers on the others are in the bundle! 15
Grid Middleware III Implementations today n n All separate auth. N and auth. Z most separate mapping from auth. Z where necessary, e. g. for databases and legacy execution § in most general sense, it is a handle for local policy § Faced with two worlds: Java and native (C) § Need a solution for both, but no unification yet § n Examples: C world: LCAS & LCMAPS (so this talk misses out on Prima, GUMS, g. Plazma, …) § Java: GT 4 Authorization Framework (so this talk misses out on Generic AAA, PERMIS, …) § n papers on the others are in the bundle! 15
 Grid Middleware III The C World: job submission and Grid. FTP n LCAS authorization based on credentials and job information (RSL) § returns a yes/no answer § pluggable framework of PDPs, using dlopen(3) system § n LCMAPS credential mapping based on user credential and additional handle information § enforcement within the process space needed § n n GUMS: access based on a site-local database of grid-to-local creds g. Plazma: gid and uid assignments for ACLs on storage 17
Grid Middleware III The C World: job submission and Grid. FTP n LCAS authorization based on credentials and job information (RSL) § returns a yes/no answer § pluggable framework of PDPs, using dlopen(3) system § n LCMAPS credential mapping based on user credential and additional handle information § enforcement within the process space needed § n n GUMS: access based on a site-local database of grid-to-local creds g. Plazma: gid and uid assignments for ACLs on storage 17
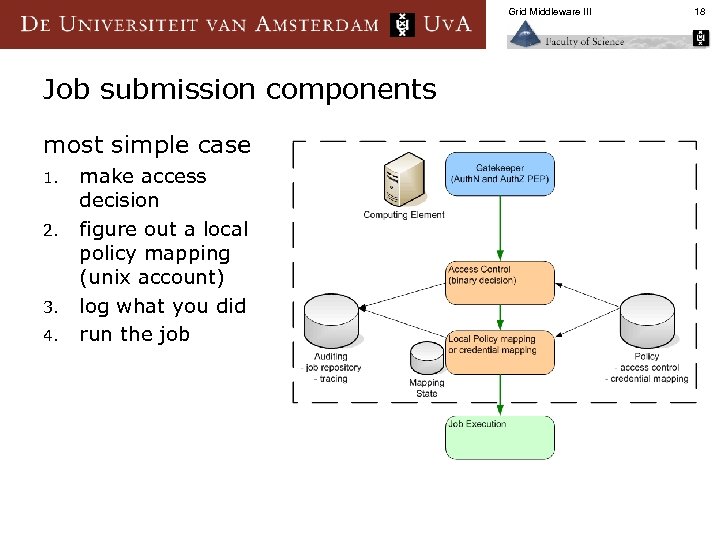 Grid Middleware III Job submission components most simple case 1. 2. 3. 4. make access decision figure out a local policy mapping (unix account) log what you did run the job 18
Grid Middleware III Job submission components most simple case 1. 2. 3. 4. make access decision figure out a local policy mapping (unix account) log what you did run the job 18
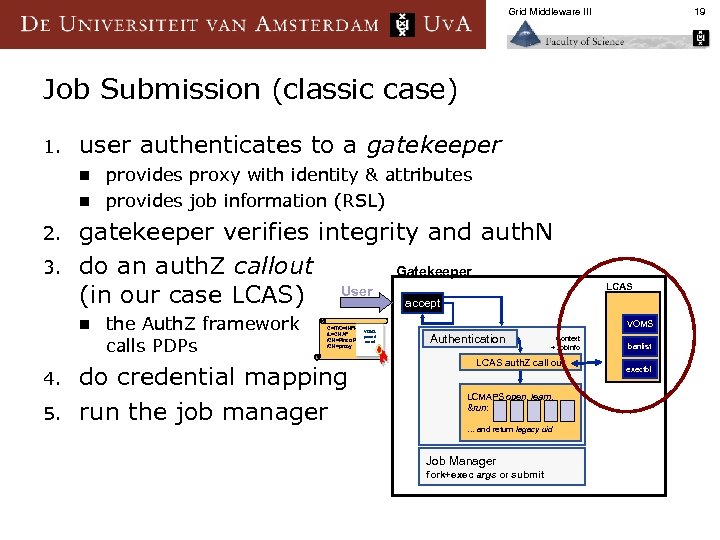 Grid Middleware III 19 Job Submission (classic case) 1. user authenticates to a gatekeeper provides proxy with identity & attributes n provides job information (RSL) n 2. 3. gatekeeper verifies integrity and auth. N do an auth. Z callout Gatekeeper User (in our case LCAS) accept n 4. 5. the Auth. Z framework calls PDPs C=IT/O=INFN VOMS /L=CNAF pseud /CN=Pinco Pallao-cert /CN=proxy do credential mapping run the job manager LCAS VOMS Authentication Context + Job. Info LCAS auth. Z call out LCMAPS open, learn, &run: … and return legacy uid Job Manager fork+exec args or submit banlist exectbl
Grid Middleware III 19 Job Submission (classic case) 1. user authenticates to a gatekeeper provides proxy with identity & attributes n provides job information (RSL) n 2. 3. gatekeeper verifies integrity and auth. N do an auth. Z callout Gatekeeper User (in our case LCAS) accept n 4. 5. the Auth. Z framework calls PDPs C=IT/O=INFN VOMS /L=CNAF pseud /CN=Pinco Pallao-cert /CN=proxy do credential mapping run the job manager LCAS VOMS Authentication Context + Job. Info LCAS auth. Z call out LCMAPS open, learn, &run: … and return legacy uid Job Manager fork+exec args or submit banlist exectbl
 Grid Middleware III Policy Decision modules Typical PDPs n Blacklist and whitelist n VOMS attributes (group/role based access) n Proxy lifetime constraints n Checking quality of authentication tokens (OIDs) n timeslots As many of these PDPs are (still) local, the grid is missing the ‘big red button’ … 20
Grid Middleware III Policy Decision modules Typical PDPs n Blacklist and whitelist n VOMS attributes (group/role based access) n Proxy lifetime constraints n Checking quality of authentication tokens (OIDs) n timeslots As many of these PDPs are (still) local, the grid is missing the ‘big red button’ … 20
 Grid Middleware III PDP configuration n A PDP is driven by a policy language § typical choice is XACML 21
Grid Middleware III PDP configuration n A PDP is driven by a policy language § typical choice is XACML 21
 Policy languages Driving the PDP
Policy languages Driving the PDP
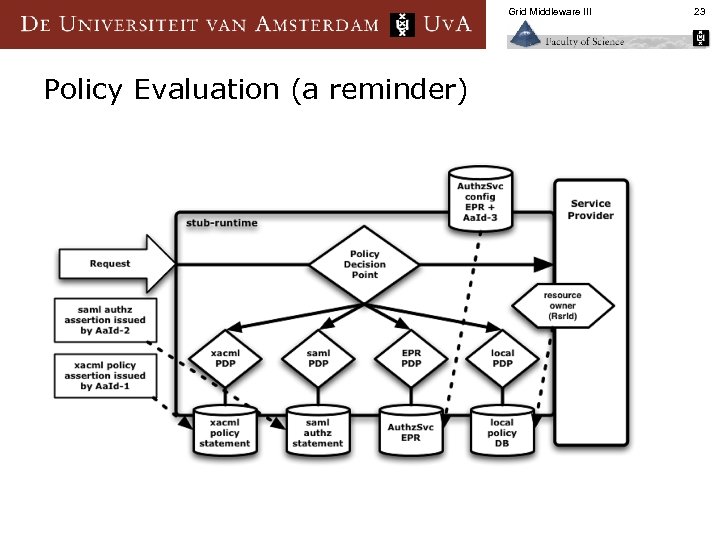 Grid Middleware III Policy Evaluation (a reminder) 23
Grid Middleware III Policy Evaluation (a reminder) 23
 Grid Middleware III Policy Languages n Home-grown languages § n XACML § § § n structured “Subject, Resource, Action” triplets supports logical constructs (and, or) also includes a retrieve/push operation** SAML § § n infinite number out there … assertion mark-up, but can also be used to express policies** not typically used as such (XACML has a preference in the community, since it is more expressive for ACLs) GACL (Grid ACL) § § § semantically a subset of XACML can be translated back and forth comprehensible for sysadmins 24
Grid Middleware III Policy Languages n Home-grown languages § n XACML § § § n structured “Subject, Resource, Action” triplets supports logical constructs (and, or) also includes a retrieve/push operation** SAML § § n infinite number out there … assertion mark-up, but can also be used to express policies** not typically used as such (XACML has a preference in the community, since it is more expressive for ACLs) GACL (Grid ACL) § § § semantically a subset of XACML can be translated back and forth comprehensible for sysadmins 24
 Grid Middleware III SAML – conveying assertions n Security Assertion Mark-up Language XML format for exchanging assertions over the wire § a message exchange protocol: how to ask and get assertions § OASIS standard § in itself, SAML does not define the integrity of the assertion § SAML assertion itself is typically signed using XML Signature when travelling between untrusted end-points § 25
Grid Middleware III SAML – conveying assertions n Security Assertion Mark-up Language XML format for exchanging assertions over the wire § a message exchange protocol: how to ask and get assertions § OASIS standard § in itself, SAML does not define the integrity of the assertion § SAML assertion itself is typically signed using XML Signature when travelling between untrusted end-points § 25
 Grid Middleware III SAML assertion types n n n Authentication Assertion Attribute Assertion Authorisation Decision 26
Grid Middleware III SAML assertion types n n n Authentication Assertion Attribute Assertion Authorisation Decision 26
 Grid Middleware III All assertions have some common information n Issuer and issuance timestamp Assertion ID Subject § § n “Conditions” under which assertion is valid § § n Name plus the security domain Optional subject confirmation, e. g. public key SAML clients must reject assertions containing unsupported conditions Special kind of condition: assertion validity period Additional “advice” § E. g. , to explain how the assertion was made 27
Grid Middleware III All assertions have some common information n Issuer and issuance timestamp Assertion ID Subject § § n “Conditions” under which assertion is valid § § n Name plus the security domain Optional subject confirmation, e. g. public key SAML clients must reject assertions containing unsupported conditions Special kind of condition: assertion validity period Additional “advice” § E. g. , to explain how the assertion was made 27
 Grid Middleware III Attribute Assertion n An issuing authority asserts that: subject S § is associated with attributes A, B, … § with values “a”, “b”, “c”… § n Typically this would be gotten from an LDAP repository “john. doe” in “example. com” § is associated with attribute “Department” § with value “Human Resources” § 28
Grid Middleware III Attribute Assertion n An issuing authority asserts that: subject S § is associated with attributes A, B, … § with values “a”, “b”, “c”… § n Typically this would be gotten from an LDAP repository “john. doe” in “example. com” § is associated with attribute “Department” § with value “Human Resources” § 28
 Grid Middleware III SAML Attribute Assertion
Grid Middleware III SAML Attribute Assertion
 Grid Middleware III Auth. Z Decision Assertion n An issuing authority decides whether to grant the request: by subject S § for access type A § to resource R § given evidence E § n n The subject could be a human or a program The resource could be a web page or a web service, for example 30
Grid Middleware III Auth. Z Decision Assertion n An issuing authority decides whether to grant the request: by subject S § for access type A § to resource R § given evidence E § n n The subject could be a human or a program The resource could be a web page or a web service, for example 30
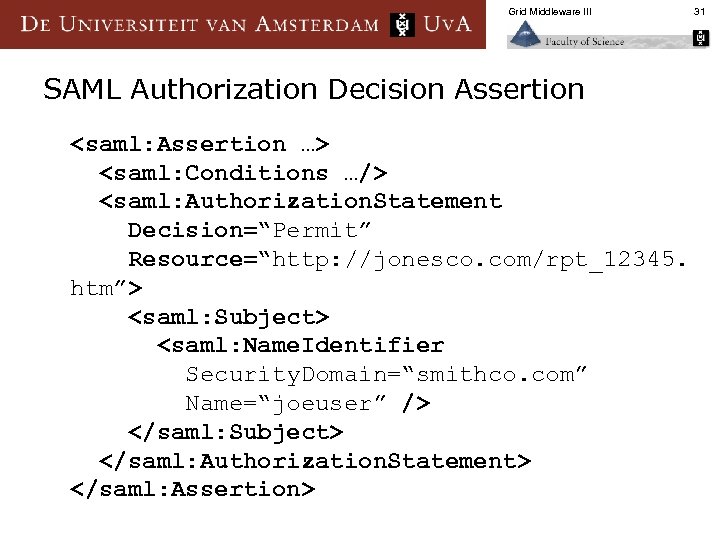 Grid Middleware III SAML Authorization Decision Assertion
Grid Middleware III SAML Authorization Decision Assertion
 Grid Middleware III XACML: access control n XACML well suited to express local policies can interoperate with incoming SAML assertions by translation § works on triplet § (subject, resource, action) – RULE –> (decision [, obligation]) 32
Grid Middleware III XACML: access control n XACML well suited to express local policies can interoperate with incoming SAML assertions by translation § works on triplet § (subject, resource, action) – RULE –> (decision [, obligation]) 32
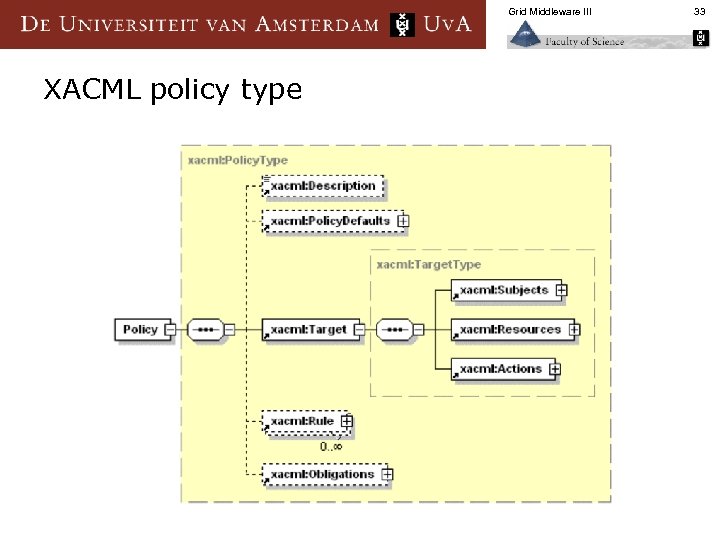 Grid Middleware III XACML policy type 33
Grid Middleware III XACML policy type 33
 Grid Middleware III XACML rules n a (set of) conditions that evaluate the incoming triples and result in a decision 34
Grid Middleware III XACML rules n a (set of) conditions that evaluate the incoming triples and result in a decision 34
n
 Grid Middleware III XACML policy: login from 9 AM to 5 PM
Grid Middleware III XACML policy: login from 9 AM to 5 PM
 Grid Middleware III Simpler policy languages n n XACML is too expressive to be understood by people so lots of graphical editors (not so handy for large-scale adminstration) § translators from and to simpler languages § n Example: GACL, the Grid ACL language 37
Grid Middleware III Simpler policy languages n n XACML is too expressive to be understood by people so lots of graphical editors (not so handy for large-scale adminstration) § translators from and to simpler languages § n Example: GACL, the Grid ACL language 37
 Credential mapping and virtual workspaces
Credential mapping and virtual workspaces
 Grid Middleware III Credential Mapping For legacy jobs, need to privision an environment n Unix account persistent (grid-mapfile) § group account (looses tracability/accountability) § dynamic assignment pool-accounts § pool-accounts with expiration (**) § n Virtual machines 40
Grid Middleware III Credential Mapping For legacy jobs, need to privision an environment n Unix account persistent (grid-mapfile) § group account (looses tracability/accountability) § dynamic assignment pool-accounts § pool-accounts with expiration (**) § n Virtual machines 40
 Grid Middleware III grid-mapfile n n static mapping between grid user and local uid cannot support multiple-VO membership § n or user needs a new identity for each VO combines auth. Z and mapping 41
Grid Middleware III grid-mapfile n n static mapping between grid user and local uid cannot support multiple-VO membership § n or user needs a new identity for each VO combines auth. Z and mapping 41
 Grid Middleware III poolaccounts n minimal modification to the gridmap-file code § § § n same file format uses a state directory where DNs are associated with unix accounts (using hard links, as they are atomic across NFS) account mapping to “. pool” -> pool 000, pool 001, pool 002, … when the account mapping is requested look in a state directory if this DN has an account mapping 2. if so, return this mapping 3. otherwise, pick next unused account from the pool and make a hardlink between DN and accountname file 4. return that mapping 1. § periodic clean up of the gridmapdir is possible § but dangerous, as jobs may still be running or files left 42
Grid Middleware III poolaccounts n minimal modification to the gridmap-file code § § § n same file format uses a state directory where DNs are associated with unix accounts (using hard links, as they are atomic across NFS) account mapping to “. pool” -> pool 000, pool 001, pool 002, … when the account mapping is requested look in a state directory if this DN has an account mapping 2. if so, return this mapping 3. otherwise, pick next unused account from the pool and make a hardlink between DN and accountname file 4. return that mapping 1. § periodic clean up of the gridmapdir is possible § but dangerous, as jobs may still be running or files left 42
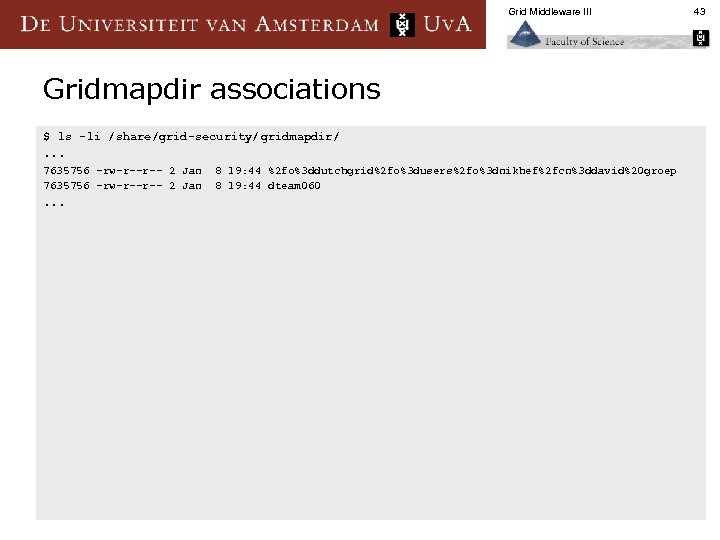 Grid Middleware III Gridmapdir associations $ ls -li /share/grid-security/gridmapdir/. . . 7635756 –rw-r--r-- 2 Jan 7635756 -rw-r--r-- 2 Jan . . . 8 19: 44 %2 fo%3 ddutchgrid%2 fo%3 dusers%2 fo%3 dnikhef%2 fcn%3 ddavid%20 groep 8 19: 44 dteam 060 43
Grid Middleware III Gridmapdir associations $ ls -li /share/grid-security/gridmapdir/. . . 7635756 –rw-r--r-- 2 Jan 7635756 -rw-r--r-- 2 Jan . . . 8 19: 44 %2 fo%3 ddutchgrid%2 fo%3 dusers%2 fo%3 dnikhef%2 fcn%3 ddavid%20 groep 8 19: 44 dteam 060 43
 Grid Middleware III LCMAPS n There are many ways to collect credentials in a site § § n n n Backward compatible with existing systems (grid-mapfile) Support for multiple VOs per user (and thus multiple UNIX groups) Mimimum system administration § § n /etc/passwd, NIS+, LDAP, Hesiod, My. SQL need a extensible, pluggable framework Poolaccounts Pool”groups” Boundary conditions § § Has to run in privileged mode Has to run in process space of incoming connection (for fork jobs) 44
Grid Middleware III LCMAPS n There are many ways to collect credentials in a site § § n n n Backward compatible with existing systems (grid-mapfile) Support for multiple VOs per user (and thus multiple UNIX groups) Mimimum system administration § § n /etc/passwd, NIS+, LDAP, Hesiod, My. SQL need a extensible, pluggable framework Poolaccounts Pool”groups” Boundary conditions § § Has to run in privileged mode Has to run in process space of incoming connection (for fork jobs) 44
 Grid Middleware III LCMAPS – functionality view n n Unix mapping based on VOMS groups, roles Supports pool groups as well as pool accounts Granularity set by the site administrator (see example) Primary group set to first VOMS group § § n for accounting purposes for use by schedulers in setting priority Identity set before job gets to batch system § § § accounting based on batch system data needs specific USER id for each job submitted traceability of system/network activity inside the job or ~wrapper limit impact of a compromised identity (so as not to hurt production) 45
Grid Middleware III LCMAPS – functionality view n n Unix mapping based on VOMS groups, roles Supports pool groups as well as pool accounts Granularity set by the site administrator (see example) Primary group set to first VOMS group § § n for accounting purposes for use by schedulers in setting priority Identity set before job gets to batch system § § § accounting based on batch system data needs specific USER id for each job submitted traceability of system/network activity inside the job or ~wrapper limit impact of a compromised identity (so as not to hurt production) 45
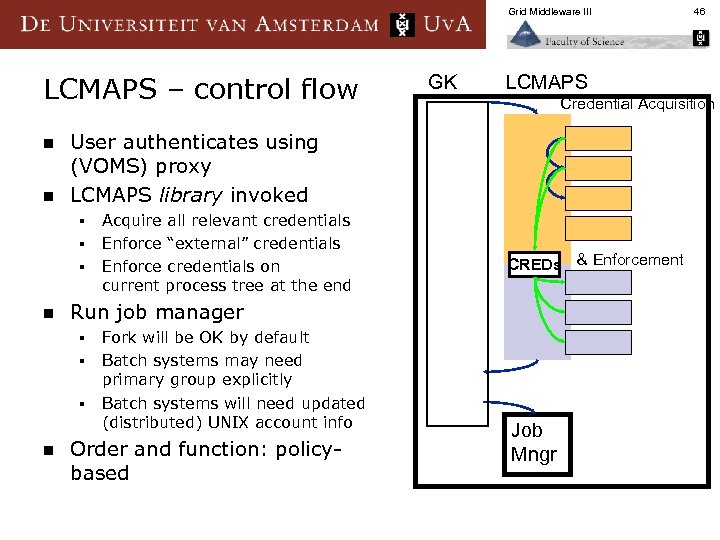 Grid Middleware III LCMAPS – control flow n n § § Credential Acquisition Acquire all relevant credentials Enforce “external” credentials Enforce credentials on current process tree at the end CREDs & Enforcement Run job manager § § § n LCMAPS User authenticates using (VOMS) proxy LCMAPS library invoked § n GK Fork will be OK by default Batch systems may need primary group explicitly Batch systems will need updated (distributed) UNIX account info Order and function: policybased 46 Job Mngr
Grid Middleware III LCMAPS – control flow n n § § Credential Acquisition Acquire all relevant credentials Enforce “external” credentials Enforce credentials on current process tree at the end CREDs & Enforcement Run job manager § § § n LCMAPS User authenticates using (VOMS) proxy LCMAPS library invoked § n GK Fork will be OK by default Batch systems may need primary group explicitly Batch systems will need updated (distributed) UNIX account info Order and function: policybased 46 Job Mngr
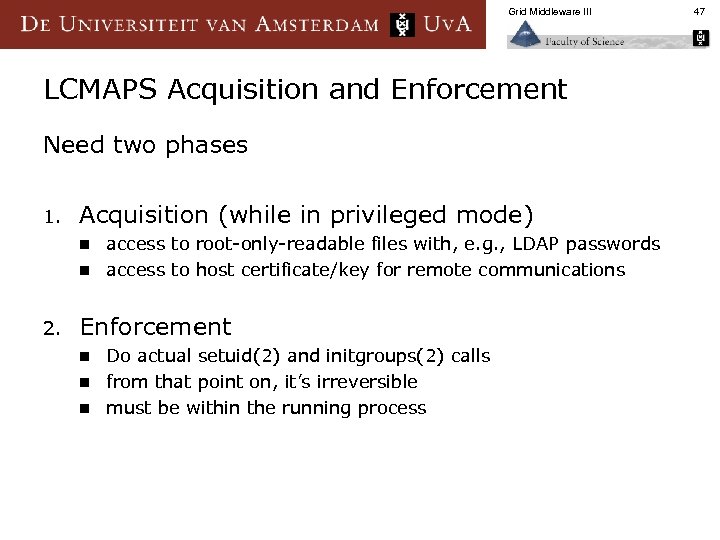 Grid Middleware III LCMAPS Acquisition and Enforcement Need two phases 1. Acquisition (while in privileged mode) access to root-only-readable files with, e. g. , LDAP passwords n access to host certificate/key for remote communications n 2. Enforcement Do actual setuid(2) and initgroups(2) calls n from that point on, it’s irreversible n must be within the running process n 47
Grid Middleware III LCMAPS Acquisition and Enforcement Need two phases 1. Acquisition (while in privileged mode) access to root-only-readable files with, e. g. , LDAP passwords n access to host certificate/key for remote communications n 2. Enforcement Do actual setuid(2) and initgroups(2) calls n from that point on, it’s irreversible n must be within the running process n 47
 Grid Middleware III LCMAPS – modules n Modules represent atomic functionality n VOMS extract VOMS credentials from the proxy (A) Pool. Accounts from username assign unique uid (A) Pool. Groups from (VOMS) groupname assign unique gid (A) Local. Account from username assign local existing unique uid (A) Local. Groups from (VOMS) groupname assign local existing gid (A) VOMS Pool. Accounts from (VOMS) username assign unique uid (A) AFS/Krb 5 get token based on user DN info (A) n n n n n POSIX process setuid() and setegid() (E) POSIX LDAP update distributed user database (E) Krb 5 run job via k 5 cert (E) … 48
Grid Middleware III LCMAPS – modules n Modules represent atomic functionality n VOMS extract VOMS credentials from the proxy (A) Pool. Accounts from username assign unique uid (A) Pool. Groups from (VOMS) groupname assign unique gid (A) Local. Account from username assign local existing unique uid (A) Local. Groups from (VOMS) groupname assign local existing gid (A) VOMS Pool. Accounts from (VOMS) username assign unique uid (A) AFS/Krb 5 get token based on user DN info (A) n n n n n POSIX process setuid() and setegid() (E) POSIX LDAP update distributed user database (E) Krb 5 run job via k 5 cert (E) … 48
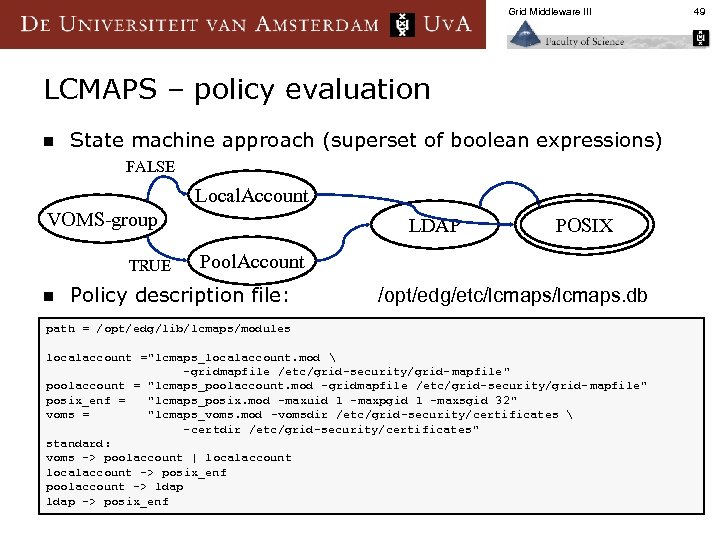 Grid Middleware III LCMAPS – policy evaluation n State machine approach (superset of boolean expressions) FALSE Local. Account VOMS-group TRUE n LDAP POSIX Pool. Account Policy description file: /opt/edg/etc/lcmaps. db path = /opt/edg/lib/lcmaps/modules localaccount ="lcmaps_localaccount. mod -gridmapfile /etc/grid-security/grid- mapfile" poolaccount = "lcmaps_poolaccount. mod -gridmapfile /etc/grid-security/grid- mapfile" posix_enf = "lcmaps_posix. mod -maxuid 1 -maxpgid 1 -maxsgid 32" voms = "lcmaps_voms. mod -vomsdir /etc/grid-security/certificates -certdir /etc/grid-security/certificates" standard: voms -> poolaccount | localaccount -> posix_enf poolaccount -> ldap -> posix_enf 49
Grid Middleware III LCMAPS – policy evaluation n State machine approach (superset of boolean expressions) FALSE Local. Account VOMS-group TRUE n LDAP POSIX Pool. Account Policy description file: /opt/edg/etc/lcmaps. db path = /opt/edg/lib/lcmaps/modules localaccount ="lcmaps_localaccount. mod -gridmapfile /etc/grid-security/grid- mapfile" poolaccount = "lcmaps_poolaccount. mod -gridmapfile /etc/grid-security/grid- mapfile" posix_enf = "lcmaps_posix. mod -maxuid 1 -maxpgid 1 -maxsgid 32" voms = "lcmaps_voms. mod -vomsdir /etc/grid-security/certificates -certdir /etc/grid-security/certificates" standard: voms -> poolaccount | localaccount -> posix_enf poolaccount -> ldap -> posix_enf 49
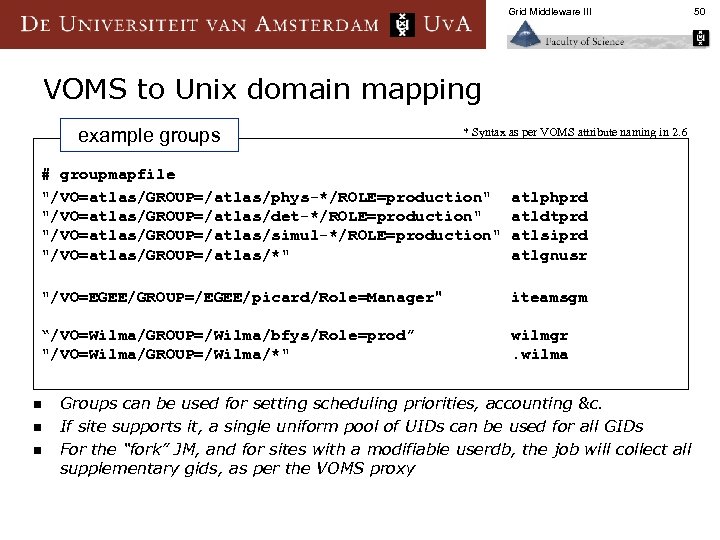 Grid Middleware III VOMS to Unix domain mapping example groups * Syntax as per VOMS attribute naming in 2. 6 # groupmapfile "/VO=atlas/GROUP=/atlas/phys-*/ROLE=production" "/VO=atlas/GROUP=/atlas/det-*/ROLE=production" "/VO=atlas/GROUP=/atlas/simul-*/ROLE=production" "/VO=atlas/GROUP=/atlas/*" atlphprd atldtprd atlsiprd atlgnusr "/VO=EGEE/GROUP=/EGEE/picard/Role=Manager" iteamsgm “/VO=Wilma/GROUP=/Wilma/bfys/Role=prod” "/VO=Wilma/GROUP=/Wilma/*" wilmgr. wilma n n n Groups can be used for setting scheduling priorities, accounting &c. If site supports it, a single uniform pool of UIDs can be used for all GIDs For the “fork” JM, and for sites with a modifiable userdb, the job will collect all supplementary gids, as per the VOMS proxy 50
Grid Middleware III VOMS to Unix domain mapping example groups * Syntax as per VOMS attribute naming in 2. 6 # groupmapfile "/VO=atlas/GROUP=/atlas/phys-*/ROLE=production" "/VO=atlas/GROUP=/atlas/det-*/ROLE=production" "/VO=atlas/GROUP=/atlas/simul-*/ROLE=production" "/VO=atlas/GROUP=/atlas/*" atlphprd atldtprd atlsiprd atlgnusr "/VO=EGEE/GROUP=/EGEE/picard/Role=Manager" iteamsgm “/VO=Wilma/GROUP=/Wilma/bfys/Role=prod” "/VO=Wilma/GROUP=/Wilma/*" wilmgr. wilma n n n Groups can be used for setting scheduling priorities, accounting &c. If site supports it, a single uniform pool of UIDs can be used for all GIDs For the “fork” JM, and for sites with a modifiable userdb, the job will collect all supplementary gids, as per the VOMS proxy 50
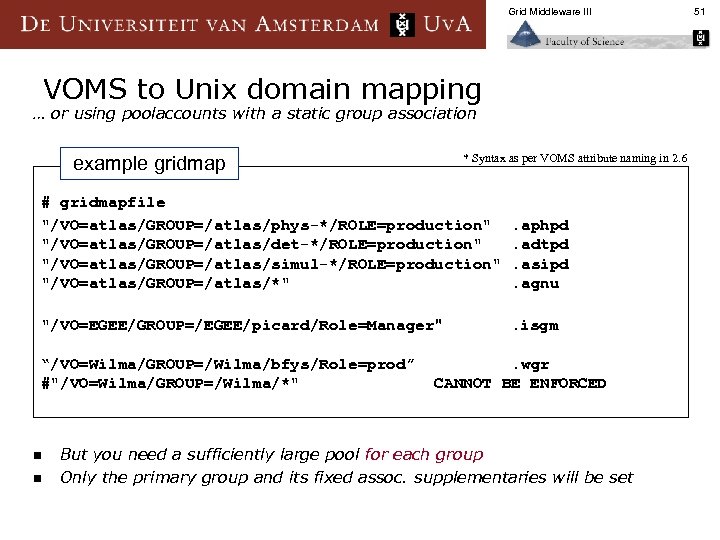 Grid Middleware III VOMS to Unix domain mapping … or using poolaccounts with a static group association * Syntax as per VOMS attribute naming in 2. 6 example gridmap # gridmapfile "/VO=atlas/GROUP=/atlas/phys-*/ROLE=production" "/VO=atlas/GROUP=/atlas/det-*/ROLE=production" "/VO=atlas/GROUP=/atlas/simul-*/ROLE=production" "/VO=atlas/GROUP=/atlas/*" . aphpd. adtpd. asipd. agnu "/VO=EGEE/GROUP=/EGEE/picard/Role=Manager" . isgm “/VO=Wilma/GROUP=/Wilma/bfys/Role=prod” #"/VO=Wilma/GROUP=/Wilma/*" n n . wgr CANNOT BE ENFORCED But you need a sufficiently large pool for each group Only the primary group and its fixed assoc. supplementaries will be set 51
Grid Middleware III VOMS to Unix domain mapping … or using poolaccounts with a static group association * Syntax as per VOMS attribute naming in 2. 6 example gridmap # gridmapfile "/VO=atlas/GROUP=/atlas/phys-*/ROLE=production" "/VO=atlas/GROUP=/atlas/det-*/ROLE=production" "/VO=atlas/GROUP=/atlas/simul-*/ROLE=production" "/VO=atlas/GROUP=/atlas/*" . aphpd. adtpd. asipd. agnu "/VO=EGEE/GROUP=/EGEE/picard/Role=Manager" . isgm “/VO=Wilma/GROUP=/Wilma/bfys/Role=prod” #"/VO=Wilma/GROUP=/Wilma/*" n n . wgr CANNOT BE ENFORCED But you need a sufficiently large pool for each group Only the primary group and its fixed assoc. supplementaries will be set 51
 Grid Middleware III LCMAPS – caveats n n Unix mapping based on VOMS groups, roles, and capabilities Possibly pool groups as well as pool accounts Granularity set by the site administrator (see example following) Primary group set to first VOMS group – accounting n More than one VO/group per grid user allowed [but…] Each VOMS unique FQAN listed translates into 1 Unix group id Each user-FQAN combination translates into 1 Unix user id n New mechanisms could mitigate issues: n n groups-on-demand, support granularity at any level § Central user directory support (nss_LDAP, pam-ldap) Not ready – and priorities have not been assigned to this yet. § 52
Grid Middleware III LCMAPS – caveats n n Unix mapping based on VOMS groups, roles, and capabilities Possibly pool groups as well as pool accounts Granularity set by the site administrator (see example following) Primary group set to first VOMS group – accounting n More than one VO/group per grid user allowed [but…] Each VOMS unique FQAN listed translates into 1 Unix group id Each user-FQAN combination translates into 1 Unix user id n New mechanisms could mitigate issues: n n groups-on-demand, support granularity at any level § Central user directory support (nss_LDAP, pam-ldap) Not ready – and priorities have not been assigned to this yet. § 52
 Grid Middleware III Work Space Service On the road towards virtualized resources: Work Space Service n Managed accounts § § n n enable life cycle management controlled account management (VO can request/release) “special” Qo. S requests Use to request credentials (groups) with specific prios? future: provision a virtual machine WS-RF style GT 4 service § uses LCMAPS as a back-end for account leasing http: //www. mcs. anl. gov/workspace/ 53
Grid Middleware III Work Space Service On the road towards virtualized resources: Work Space Service n Managed accounts § § n n enable life cycle management controlled account management (VO can request/release) “special” Qo. S requests Use to request credentials (groups) with specific prios? future: provision a virtual machine WS-RF style GT 4 service § uses LCMAPS as a back-end for account leasing http: //www. mcs. anl. gov/workspace/ 53
 Grid Middleware III Workspaces and accounts n n Unix account is ‘just’ a specific kind of workspace ought to be provides like one 54
Grid Middleware III Workspaces and accounts n n Unix account is ‘just’ a specific kind of workspace ought to be provides like one 54
 Grid Middleware III Work Space Service Work by Kate Keahey, et al. , ANL n provision workspaces before the job starts static account mappings: grid-mapfile § with poolaccounts (using LCMAPS) § provisioning of workspace using VM technology § § n provides abstraction of resources option for a ‘feel at home’ environment for applications if VM technology can deliver enough performance parts of this now part of a GT 4 tech preview 55
Grid Middleware III Work Space Service Work by Kate Keahey, et al. , ANL n provision workspaces before the job starts static account mappings: grid-mapfile § with poolaccounts (using LCMAPS) § provisioning of workspace using VM technology § § n provides abstraction of resources option for a ‘feel at home’ environment for applications if VM technology can deliver enough performance parts of this now part of a GT 4 tech preview 55
 Grid Middleware III LCMAPS usage with the WSS 56
Grid Middleware III LCMAPS usage with the WSS 56
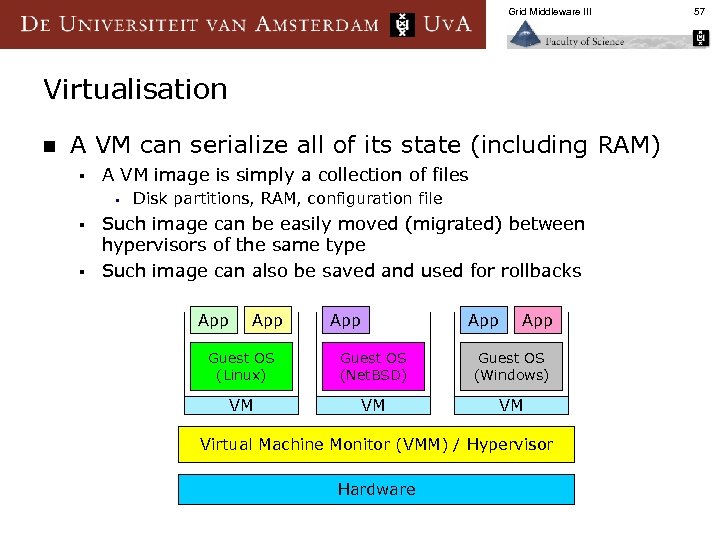 Grid Middleware III Virtualisation n A VM can serialize all of its state (including RAM) § A VM image is simply a collection of files § Disk partitions, RAM, configuration file Such image can be easily moved (migrated) between hypervisors of the same type § Such image can also be saved and used for rollbacks § App App App Guest OS (Linux) Guest OS (Net. BSD) Guest OS (Windows) VM VM VM Virtual Machine Monitor (VMM) / Hypervisor Hardware 57
Grid Middleware III Virtualisation n A VM can serialize all of its state (including RAM) § A VM image is simply a collection of files § Disk partitions, RAM, configuration file Such image can be easily moved (migrated) between hypervisors of the same type § Such image can also be saved and used for rollbacks § App App App Guest OS (Linux) Guest OS (Net. BSD) Guest OS (Windows) VM VM VM Virtual Machine Monitor (VMM) / Hypervisor Hardware 57
 Grid Middleware III Types of virtualisation n Depending on the layer you virtualize you will end up with a different VM API: language VMs (JVM) § ISA: system VMs (VMware) § n Different types of system virtual machines § Full virtualization (VMware) § § Para-virtualization (Xen, UML, Denali) § § n Run multiple unmodified guest OSs Run multiple guest OSs ported to a special architecture Single OS image (Vserver) What is the cost of using VMs? § Paper by Kate Keahey et al. “From Sandbox to Playground: Dynamic Virtual Environments in the Grid”, Grid 2004 from: Kate Keahey’s PPAM 2005 talk 58
Grid Middleware III Types of virtualisation n Depending on the layer you virtualize you will end up with a different VM API: language VMs (JVM) § ISA: system VMs (VMware) § n Different types of system virtual machines § Full virtualization (VMware) § § Para-virtualization (Xen, UML, Denali) § § n Run multiple unmodified guest OSs Run multiple guest OSs ported to a special architecture Single OS image (Vserver) What is the cost of using VMs? § Paper by Kate Keahey et al. “From Sandbox to Playground: Dynamic Virtual Environments in the Grid”, Grid 2004 from: Kate Keahey’s PPAM 2005 talk 58
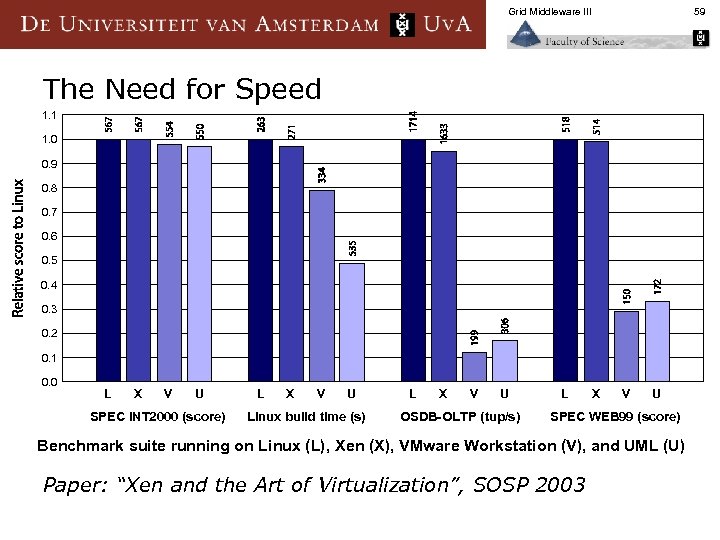 Grid Middleware III 59 The Need for Speed 1. 1 1. 0 0. 9 0. 8 0. 7 0. 6 0. 5 0. 4 0. 3 0. 2 0. 1 0. 0 L X V U SPEC INT 2000 (score) L X V U Linux build time (s) L X V U OSDB-OLTP (tup/s) L X V U SPEC WEB 99 (score) Benchmark suite running on Linux (L), Xen (X), VMware Workstation (V), and UML (U) Paper: “Xen and the Art of Virtualization”, SOSP 2003
Grid Middleware III 59 The Need for Speed 1. 1 1. 0 0. 9 0. 8 0. 7 0. 6 0. 5 0. 4 0. 3 0. 2 0. 1 0. 0 L X V U SPEC INT 2000 (score) L X V U Linux build time (s) L X V U OSDB-OLTP (tup/s) L X V U SPEC WEB 99 (score) Benchmark suite running on Linux (L), Xen (X), VMware Workstation (V), and UML (U) Paper: “Xen and the Art of Virtualization”, SOSP 2003
 Grid Middleware III What Makes VMs Great n Summary of VM properties: § Good isolation properties § § Excellent enforcement potential § § VM images (include RAM), can be copied The ability to pause and resume computations § n Library signature, OS, maybe even 64/32 -bit architectures Serialization property § § Details depend on implementation Customizable software configuration § § Generally enhanced security, audit forensics Allow migration How do we make VMs available over the network and manage them so as to leverage this potential? § Challenges: security, enforcement, protocols from: Kate Keahey’s PPAM 2005 talk 60
Grid Middleware III What Makes VMs Great n Summary of VM properties: § Good isolation properties § § Excellent enforcement potential § § VM images (include RAM), can be copied The ability to pause and resume computations § n Library signature, OS, maybe even 64/32 -bit architectures Serialization property § § Details depend on implementation Customizable software configuration § § Generally enhanced security, audit forensics Allow migration How do we make VMs available over the network and manage them so as to leverage this potential? § Challenges: security, enforcement, protocols from: Kate Keahey’s PPAM 2005 talk 60
 Grid Middleware III What are Virtual Workspaces? n Virtual Workspaces: environments that can be made available dynamically the Grid § n Examples: § § n well-defined properties in terms of environment definition and resource usage enforcement A physical cluster booted to a desired configuration (e. g. Cluster on Demand) A Grid 3 node dynamically configured using Pacman A cluster partition configured with a hypervisor A VM representing an OSG configuration enforcing memory and CPU usage Workspaces can be implemented using a variety of technologies § VMs are the most promising from: Kate Keahey’s PPAM 2005 talk 61
Grid Middleware III What are Virtual Workspaces? n Virtual Workspaces: environments that can be made available dynamically the Grid § n Examples: § § n well-defined properties in terms of environment definition and resource usage enforcement A physical cluster booted to a desired configuration (e. g. Cluster on Demand) A Grid 3 node dynamically configured using Pacman A cluster partition configured with a hypervisor A VM representing an OSG configuration enforcing memory and CPU usage Workspaces can be implemented using a variety of technologies § VMs are the most promising from: Kate Keahey’s PPAM 2005 talk 61
 Grid Middleware III Virtual Workspace n Environment Aspect (workspace meta-data) § Information/state that outlives its deployment § § § n Resource allocation request (deployment time) § Flexibly negotiated within desired constraints § § § See GGF WS-Agreement standard Memory, disk, networking, etc. § n Generic information (name, time to live) Attested software partition information: OS, “OSG configuration”, “application installation”, etc. Services: ssh, GRAM, pre-configured job See GGF JSDL standard On deployment the actual resource allocation information becomes available for inspection Atomic workspaces and virtual clusters § Clusters are simply aggregate workspaces from: Kate Keahey’s PPAM 2005 talk 62
Grid Middleware III Virtual Workspace n Environment Aspect (workspace meta-data) § Information/state that outlives its deployment § § § n Resource allocation request (deployment time) § Flexibly negotiated within desired constraints § § § See GGF WS-Agreement standard Memory, disk, networking, etc. § n Generic information (name, time to live) Attested software partition information: OS, “OSG configuration”, “application installation”, etc. Services: ssh, GRAM, pre-configured job See GGF JSDL standard On deployment the actual resource allocation information becomes available for inspection Atomic workspaces and virtual clusters § Clusters are simply aggregate workspaces from: Kate Keahey’s PPAM 2005 talk 62
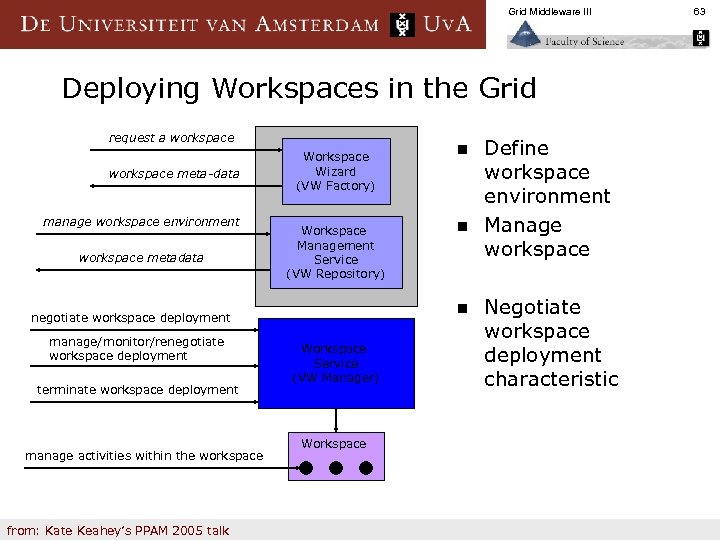 Grid Middleware III Deploying Workspaces in the Grid request a workspace meta-data manage workspace environment workspace metadata Workspace Wizard (VW Factory) Workspace Management Service (VW Repository) terminate workspace deployment manage activities within the workspace from: Kate Keahey’s PPAM 2005 talk n n negotiate workspace deployment manage/monitor/renegotiate workspace deployment n Workspace Service (VW Manager) Workspace Define workspace environment Manage workspace Negotiate workspace deployment characteristic 63
Grid Middleware III Deploying Workspaces in the Grid request a workspace meta-data manage workspace environment workspace metadata Workspace Wizard (VW Factory) Workspace Management Service (VW Repository) terminate workspace deployment manage activities within the workspace from: Kate Keahey’s PPAM 2005 talk n n negotiate workspace deployment manage/monitor/renegotiate workspace deployment n Workspace Service (VW Manager) Workspace Define workspace environment Manage workspace Negotiate workspace deployment characteristic 63
 Grid Middleware III Current Implementation n Current prototype using Globus Toolkit 4 § n Workspace Wizard § § n Leveraging standard Grid Service features Returns workspace meta-data Very rudimentary implementation Workspace Service § § Create: takes workspace meta-data and a deployment descriptor Manage: § § § Destroy § n renegotiate resource allocation Also traditional Grid Service management: TTL, etc. Different options: pause, shutdown or destroy First tech preview release expected later this month from: Kate Keahey’s PPAM 2005 talk 64
Grid Middleware III Current Implementation n Current prototype using Globus Toolkit 4 § n Workspace Wizard § § n Leveraging standard Grid Service features Returns workspace meta-data Very rudimentary implementation Workspace Service § § Create: takes workspace meta-data and a deployment descriptor Manage: § § § Destroy § n renegotiate resource allocation Also traditional Grid Service management: TTL, etc. Different options: pause, shutdown or destroy First tech preview release expected later this month from: Kate Keahey’s PPAM 2005 talk 64
 Grid Middleware III How dynamic is the deployment? n Automatic § § § n Protocol-based Moving towards better articulation of migration Renegotiation of resource allocation How fast is this deployment? § Deployment of workspace for EMBOSS suite: § § § n Manual: ~45 minutes Based on pre-configured Vmware VMs: ~6 minutes Based on pre-configured Xen VM: < 1 second How much overhead does workspace deployment add over what we have today? from: Kate Keahey’s PPAM 2005 talk 65
Grid Middleware III How dynamic is the deployment? n Automatic § § § n Protocol-based Moving towards better articulation of migration Renegotiation of resource allocation How fast is this deployment? § Deployment of workspace for EMBOSS suite: § § § n Manual: ~45 minutes Based on pre-configured Vmware VMs: ~6 minutes Based on pre-configured Xen VM: < 1 second How much overhead does workspace deployment add over what we have today? from: Kate Keahey’s PPAM 2005 talk 65
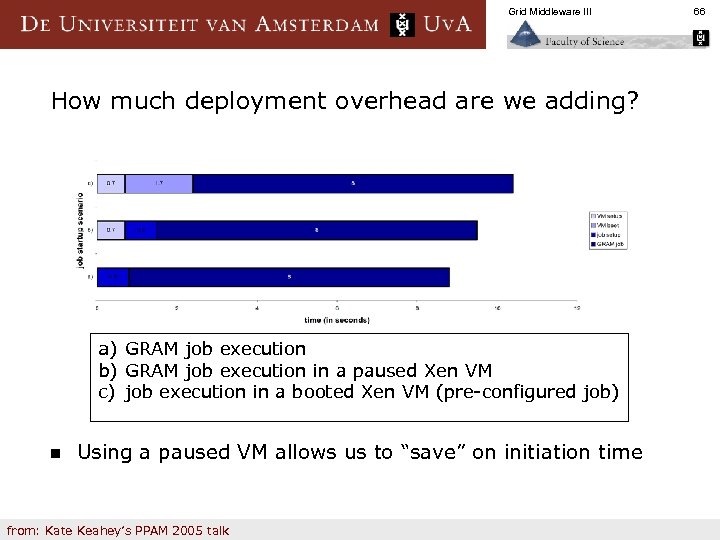 Grid Middleware III How much deployment overhead are we adding? a) GRAM job execution b) GRAM job execution in a paused Xen VM c) job execution in a booted Xen VM (pre-configured job) n Using a paused VM allows us to “save” on initiation time from: Kate Keahey’s PPAM 2005 talk 66
Grid Middleware III How much deployment overhead are we adding? a) GRAM job execution b) GRAM job execution in a paused Xen VM c) job execution in a booted Xen VM (pre-configured job) n Using a paused VM allows us to “save” on initiation time from: Kate Keahey’s PPAM 2005 talk 66
 Grid Middleware III Virtual Grids? n In principle, VM technology opens the possibility for virtual grids, built as overlay networks § n for full virtualisation need a VPN between the VMs as well but policy and deployment issues remain § regulatory and system sanity requirements for hosting providers to know who is running where 67
Grid Middleware III Virtual Grids? n In principle, VM technology opens the possibility for virtual grids, built as overlay networks § n for full virtualisation need a VPN between the VMs as well but policy and deployment issues remain § regulatory and system sanity requirements for hosting providers to know who is running where 67
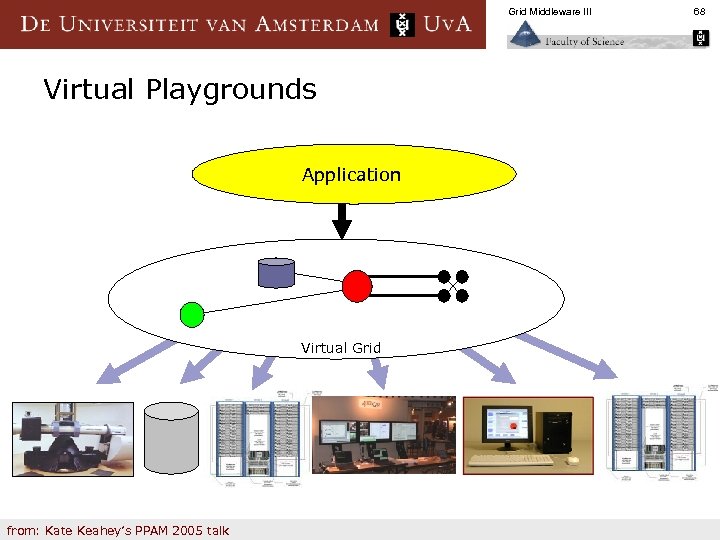 Grid Middleware III Virtual Playgrounds Application Virtual Grid from: Kate Keahey’s PPAM 2005 talk 68
Grid Middleware III Virtual Playgrounds Application Virtual Grid from: Kate Keahey’s PPAM 2005 talk 68
 Access Control to Services Fine grained control within the integrated framework
Access Control to Services Fine grained control within the integrated framework
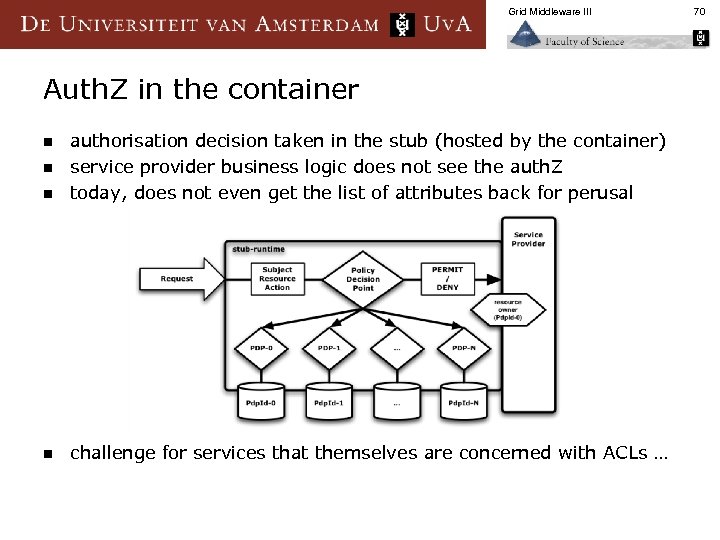 Grid Middleware III Auth. Z in the container n authorisation decision taken in the stub (hosted by the container) service provider business logic does not see the auth. Z today, does not even get the list of attributes back for perusal n challenge for services that themselves are concerned with ACLs … n n 70
Grid Middleware III Auth. Z in the container n authorisation decision taken in the stub (hosted by the container) service provider business logic does not see the auth. Z today, does not even get the list of attributes back for perusal n challenge for services that themselves are concerned with ACLs … n n 70
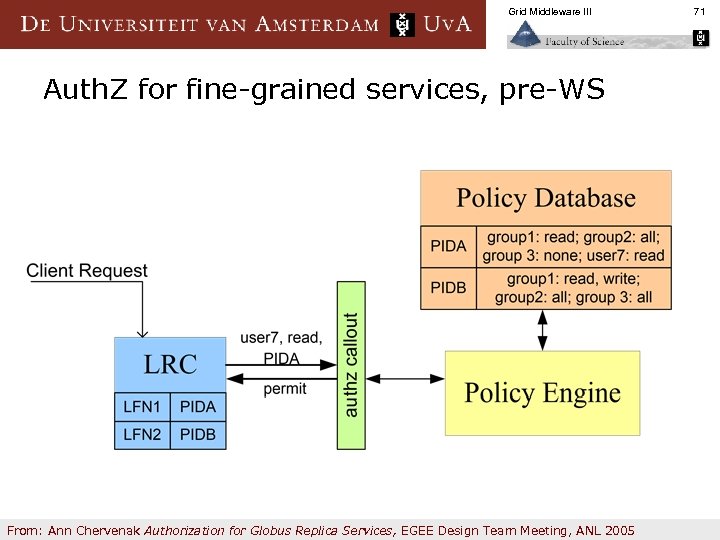 Grid Middleware III Auth. Z for fine-grained services, pre-WS From: Ann Chervenak Authorization for Globus Replica Services, EGEE Design Team Meeting, ANL 2005 71
Grid Middleware III Auth. Z for fine-grained services, pre-WS From: Ann Chervenak Authorization for Globus Replica Services, EGEE Design Team Meeting, ANL 2005 71
 Grid Middleware III Policy Identifiers and Policy Engines n Associate entries in the RLS with one or more policy identifiers § E. g. , policy identifier could represent an ACL n When a client attempts to create, update or access an RLS entry, the authorization framework invokes a policy engine n Policy engine understands how to enforce the policy associated with each policy ID n Assumption is that there will be a relatively small number of unique policies § Typically, data organized as datasets or collections, with permissions on all objects the same From: Ann Chervenak Authorization for Globus Replica Services, EGEE Design Team Meeting, ANL 2005 72
Grid Middleware III Policy Identifiers and Policy Engines n Associate entries in the RLS with one or more policy identifiers § E. g. , policy identifier could represent an ACL n When a client attempts to create, update or access an RLS entry, the authorization framework invokes a policy engine n Policy engine understands how to enforce the policy associated with each policy ID n Assumption is that there will be a relatively small number of unique policies § Typically, data organized as datasets or collections, with permissions on all objects the same From: Ann Chervenak Authorization for Globus Replica Services, EGEE Design Team Meeting, ANL 2005 72
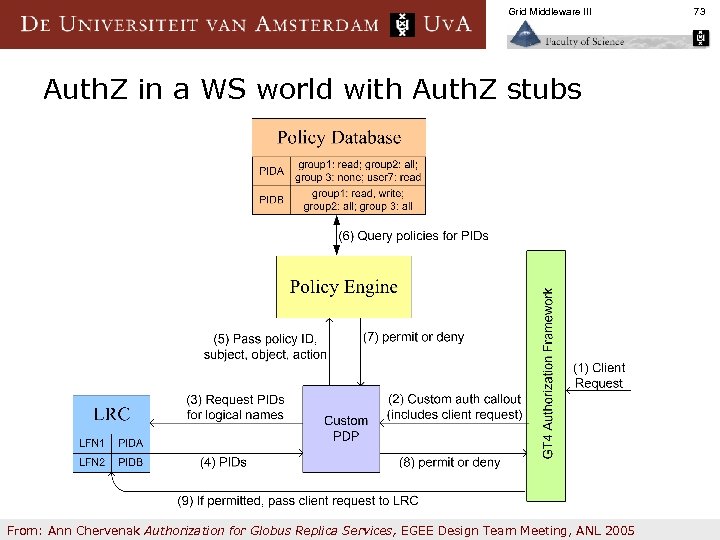 Grid Middleware III Auth. Z in a WS world with Auth. Z stubs From: Ann Chervenak Authorization for Globus Replica Services, EGEE Design Team Meeting, ANL 2005 73
Grid Middleware III Auth. Z in a WS world with Auth. Z stubs From: Ann Chervenak Authorization for Globus Replica Services, EGEE Design Team Meeting, ANL 2005 73
 Grid Middleware III WS-RF Version n n n n The client request (1) is handled at the container level, where a custom authorization callout is performed. The authorization callout passes the entire client request to a custom Policy Decision Point (PDP) (2). Then the PDP queries the LRC (3) to obtain the policy identifiers associated with the request. LRC returns list of unique policy identifiers to the PDP (4). PDP passes the client information, requested operations, policy IDs and objects of the request to policy engine (5). Policy engine queries associated policy database (6) to obtain the policies associated with policy identifiers. The policy engine makes decisions to permit or deny the request and returns these decisions to the PDP (7). The permit/deny decisions are passed to the custom authorization framework (8). For permitted operations, the authorization framework passes the client request to the LRC for execution (9). From: Ann Chervenak Authorization for Globus Replica Services, EGEE Design Team Meeting, ANL 2005 74
Grid Middleware III WS-RF Version n n n n The client request (1) is handled at the container level, where a custom authorization callout is performed. The authorization callout passes the entire client request to a custom Policy Decision Point (PDP) (2). Then the PDP queries the LRC (3) to obtain the policy identifiers associated with the request. LRC returns list of unique policy identifiers to the PDP (4). PDP passes the client information, requested operations, policy IDs and objects of the request to policy engine (5). Policy engine queries associated policy database (6) to obtain the policies associated with policy identifiers. The policy engine makes decisions to permit or deny the request and returns these decisions to the PDP (7). The permit/deny decisions are passed to the custom authorization framework (8). For permitted operations, the authorization framework passes the client request to the LRC for execution (9). From: Ann Chervenak Authorization for Globus Replica Services, EGEE Design Team Meeting, ANL 2005 74
 Network Access Provisioning connectivity
Network Access Provisioning connectivity
 Grid Middleware III Firewalls and NAT n n Traditional site network protection has been centred around the concept of firewalls some sites also adopt NAT wrongly advertised as being a security solution § or because of supposed ‘lack of address space’ § in fact, it is still used as it is the path of least resistance … § n firewalls and NAT are the most common obstacles to grid computing many protocols are not firewall friendly (like Grid. FTP); or § require inbound connectivity to the farm (service containers) § 76
Grid Middleware III Firewalls and NAT n n Traditional site network protection has been centred around the concept of firewalls some sites also adopt NAT wrongly advertised as being a security solution § or because of supposed ‘lack of address space’ § in fact, it is still used as it is the path of least resistance … § n firewalls and NAT are the most common obstacles to grid computing many protocols are not firewall friendly (like Grid. FTP); or § require inbound connectivity to the farm (service containers) § 76
 Grid Middleware III Firewall connectivity ‘white’ solutions n explicit application-level solutions outbound connectivity only via external proxy boxes § move to transport over port 80 (http) and hope for dumb firewalls that are not packet-inspecting Jabber, R-GMA MON boxes, proprietary solutions § n explicit solutions connectivity provisioning & grid-aware firewalls/routers § similar to provisioning network links in a point 2 point setup like lambda provisioning EGEE DCS, GGF Firewall Issues RG work, … § 77
Grid Middleware III Firewall connectivity ‘white’ solutions n explicit application-level solutions outbound connectivity only via external proxy boxes § move to transport over port 80 (http) and hope for dumb firewalls that are not packet-inspecting Jabber, R-GMA MON boxes, proprietary solutions § n explicit solutions connectivity provisioning & grid-aware firewalls/routers § similar to provisioning network links in a point 2 point setup like lambda provisioning EGEE DCS, GGF Firewall Issues RG work, … § 77
 Grid Middleware III Firewall avoidance, the ‘black’ methods n implicit brokering trap program syscalls and route the traffic at the user level § dynamically select the systems that allow incoming traffic § or interpose a connection broker Condor Generic Connection Broker, Sonny’s work, … § n tcp splicing with two co-operating applications, transmit TCP packet serials out-of-band, synch them up, and try to fool the firewall § may take a long time, but it doesn’t break to the protocol § it is a dedicated abuse of the protocol that admins may detect and consider a crack. IBIS Java toolkit § 78
Grid Middleware III Firewall avoidance, the ‘black’ methods n implicit brokering trap program syscalls and route the traffic at the user level § dynamically select the systems that allow incoming traffic § or interpose a connection broker Condor Generic Connection Broker, Sonny’s work, … § n tcp splicing with two co-operating applications, transmit TCP packet serials out-of-band, synch them up, and try to fool the firewall § may take a long time, but it doesn’t break to the protocol § it is a dedicated abuse of the protocol that admins may detect and consider a crack. IBIS Java toolkit § 78
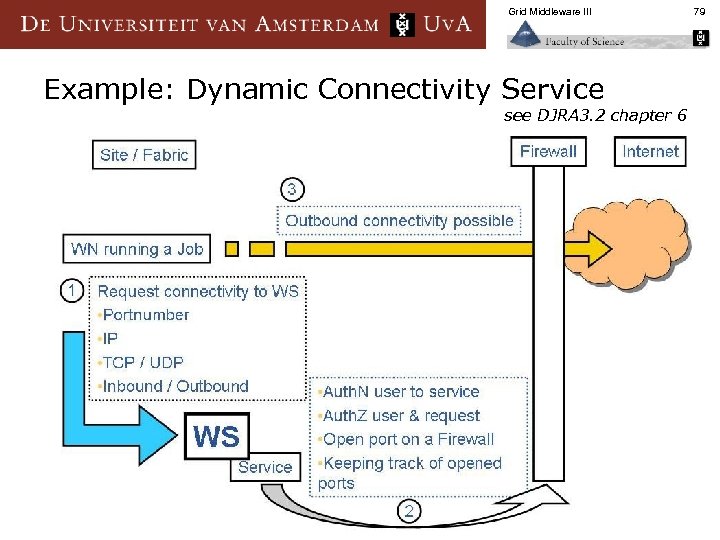 Grid Middleware III Example: Dynamic Connectivity Service see DJRA 3. 2 chapter 6 79
Grid Middleware III Example: Dynamic Connectivity Service see DJRA 3. 2 chapter 6 79
 Next: once you’ve got access … Compute and brokering services
Next: once you’ve got access … Compute and brokering services


