Overview of Network Security Davydenko Pavel Presentation































overview_of_network_security.ppt
- Размер: 1.6 Mегабайта
- Количество слайдов: 56
Описание презентации Overview of Network Security Davydenko Pavel Presentation по слайдам
 Overview of Network Security Davydenko Pavel
Overview of Network Security Davydenko Pavel
 Presentation Content • What is Internet? • What do we need to protect? • Threat Motivation • Attack Types • Security Objectives • Security mechanisms • References
Presentation Content • What is Internet? • What do we need to protect? • Threat Motivation • Attack Types • Security Objectives • Security mechanisms • References
 What is Internet? • The Internet is a worldwide IP network, that links collection of different networks from various sources, governmental, educational and commercial.
What is Internet? • The Internet is a worldwide IP network, that links collection of different networks from various sources, governmental, educational and commercial.
 What do we need to protect • Data • Resources • Reputation
What do we need to protect • Data • Resources • Reputation
 Threat Motivation • Spy • Joyride • Ignorance • Score Keeper • Revenge • Greed • Terrorist
Threat Motivation • Spy • Joyride • Ignorance • Score Keeper • Revenge • Greed • Terrorist
 Types of Attacks • Passive • Active – Denial of Services – Social Engineering
Types of Attacks • Passive • Active – Denial of Services – Social Engineering
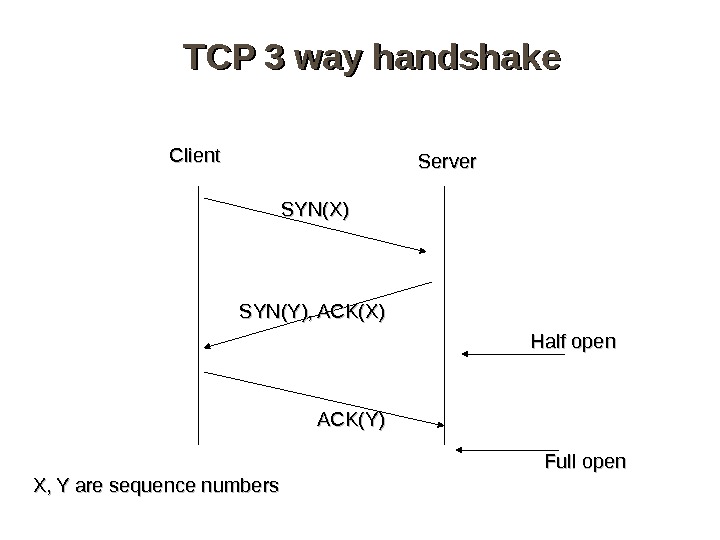
 TCP 3 way handshake Server SYN(X) SYN(Y), ACK(X) ACK(Y)Client X, Y are sequence numbers Half open Full open
TCP 3 way handshake Server SYN(X) SYN(Y), ACK(X) ACK(Y)Client X, Y are sequence numbers Half open Full open
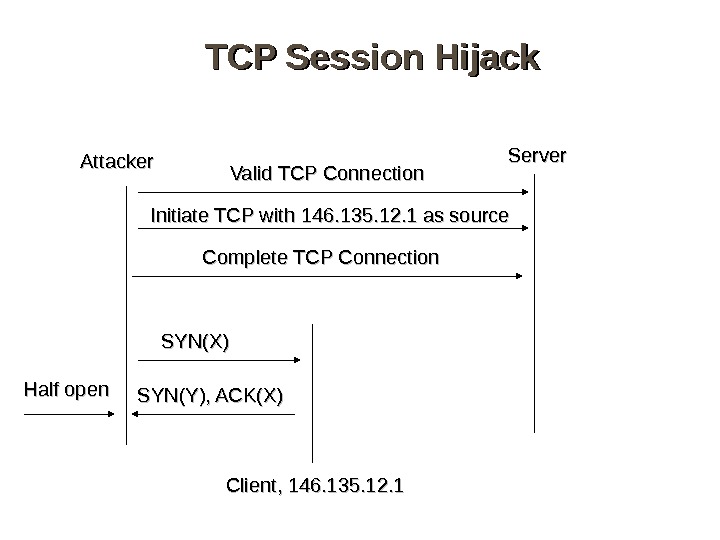
 TCP Session Hijack Server SYN(X) SYN(Y), ACK(X)Attacker Client, 146. 135. 12. 1 Half open Valid TCP Connection Initiate TCP with 146. 135. 12. 1 as source Complete TCP Connection
TCP Session Hijack Server SYN(X) SYN(Y), ACK(X)Attacker Client, 146. 135. 12. 1 Half open Valid TCP Connection Initiate TCP with 146. 135. 12. 1 as source Complete TCP Connection
 Security Objectives • Identification • Authentication • Authorization • Access Control • Data Integrity • Confidentiality • Non-repudiation
Security Objectives • Identification • Authentication • Authorization • Access Control • Data Integrity • Confidentiality • Non-repudiation
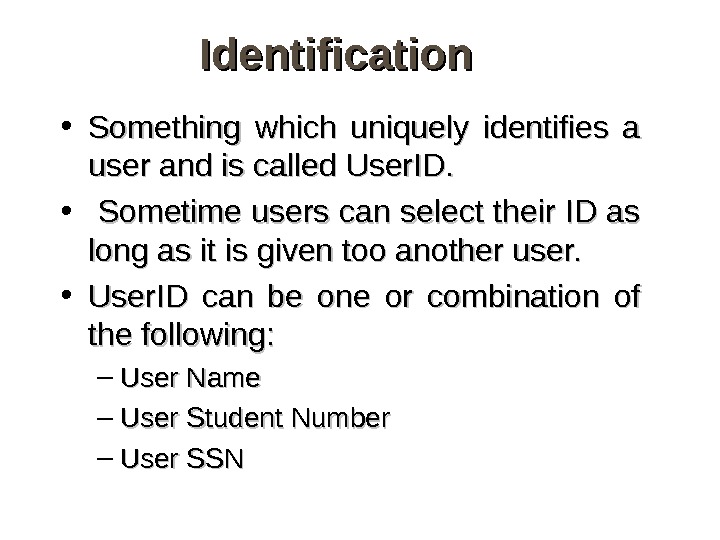
 Identification • Something which uniquely identifies a user and is called User. ID. • Sometime users can select their ID as long as it is given too another user. • User. ID can be one or combination of the following: – User Name – User Student Number – User SSN
Identification • Something which uniquely identifies a user and is called User. ID. • Sometime users can select their ID as long as it is given too another user. • User. ID can be one or combination of the following: – User Name – User Student Number – User SSN
 Authentication • The process of verifying the identity of a user • Typically based on – Something user knows • Password – Something user have • Key, smart card, disk, or other device – Something user is • fingerprint, voice, or retinal scans
Authentication • The process of verifying the identity of a user • Typically based on – Something user knows • Password – Something user have • Key, smart card, disk, or other device – Something user is • fingerprint, voice, or retinal scans
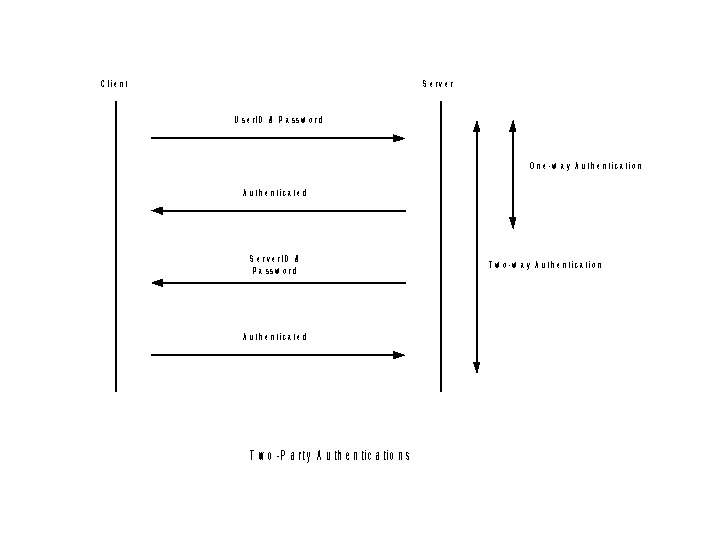
 Authentication Cont. • Authentication procedure – Two-Party Authentication • One-Way Authentication • Two-Way Authentication – Third-Party Authentication • Kerberos • X. 509 – Single Sign ON • User can access several network resources by logging on once to a security system.
Authentication Cont. • Authentication procedure – Two-Party Authentication • One-Way Authentication • Two-Way Authentication – Third-Party Authentication • Kerberos • X. 509 – Single Sign ON • User can access several network resources by logging on once to a security system.
 C l i e n t U s e r I D & P a s s w o r d S e r v e r I D & P a s s w o r d A u t h e n t i c a t e d S e r v e r O n e — w a y A u t h e n t i c a t i o n T w o — P a r t y A u t h e n t i c a t i o n s
C l i e n t U s e r I D & P a s s w o r d S e r v e r I D & P a s s w o r d A u t h e n t i c a t e d S e r v e r O n e — w a y A u t h e n t i c a t i o n T w o — P a r t y A u t h e n t i c a t i o n s
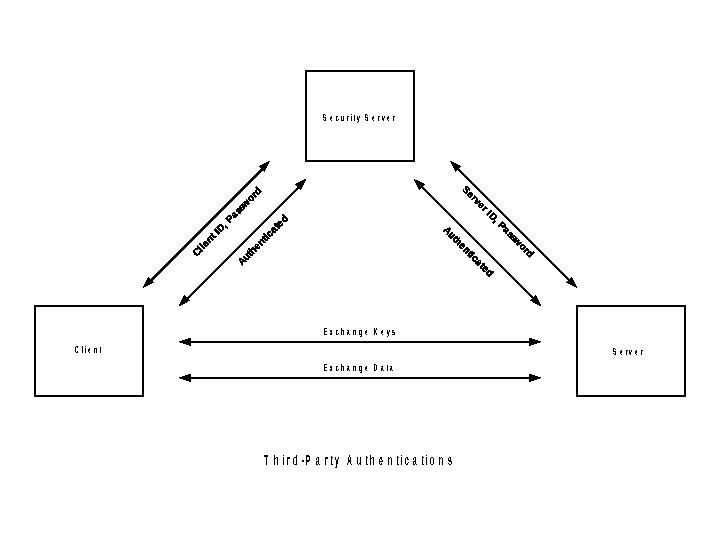
 E x c h a n g e K e y s E x c h a n g e D a t a C l i e n t. S e r v e r S e c u r i t y S e r v e r T h i r d — P a r t y A u t h e n t i c a t i o n s
E x c h a n g e K e y s E x c h a n g e D a t a C l i e n t. S e r v e r S e c u r i t y S e r v e r T h i r d — P a r t y A u t h e n t i c a t i o n s
 Authorization • The process of assigning access right to user
Authorization • The process of assigning access right to user
 Access Control • The process of enforcing access right • and is based on following three entities – Subject • is entity that can access an object – Object • is entity to which access can be controlled – Access Right • defines the ways in which a subject can access an object.
Access Control • The process of enforcing access right • and is based on following three entities – Subject • is entity that can access an object – Object • is entity to which access can be controlled – Access Right • defines the ways in which a subject can access an object.
 Access Control Cont. • Access Control is divided into two – Discretionary Access Control (DAC) • The owner of the object is responsible for setting the access right. – Mandatory Access Control (MAC) • The system defines access right based on how the subject and object are classified.
Access Control Cont. • Access Control is divided into two – Discretionary Access Control (DAC) • The owner of the object is responsible for setting the access right. – Mandatory Access Control (MAC) • The system defines access right based on how the subject and object are classified.
 Data Integrity. • Assurance that the data that arrives is the same as when it was sent.
Data Integrity. • Assurance that the data that arrives is the same as when it was sent.
 Confidentiality • Assurance that sensitive information is not visible to an eavesdropper. This is usually achieved using encryption.
Confidentiality • Assurance that sensitive information is not visible to an eavesdropper. This is usually achieved using encryption.
 Non-repudiation • Assurance that any transaction that takes place can subsequently be proved to have taken place. Both the sender and the receiver agree that the exchange took place.
Non-repudiation • Assurance that any transaction that takes place can subsequently be proved to have taken place. Both the sender and the receiver agree that the exchange took place.
 Security Mechanisms • Web Security • Cryptographic techniques • Internet Firewalls
Security Mechanisms • Web Security • Cryptographic techniques • Internet Firewalls
 Web Security • Basic Authentication • Secure Socket Layer (SSL)
Web Security • Basic Authentication • Secure Socket Layer (SSL)
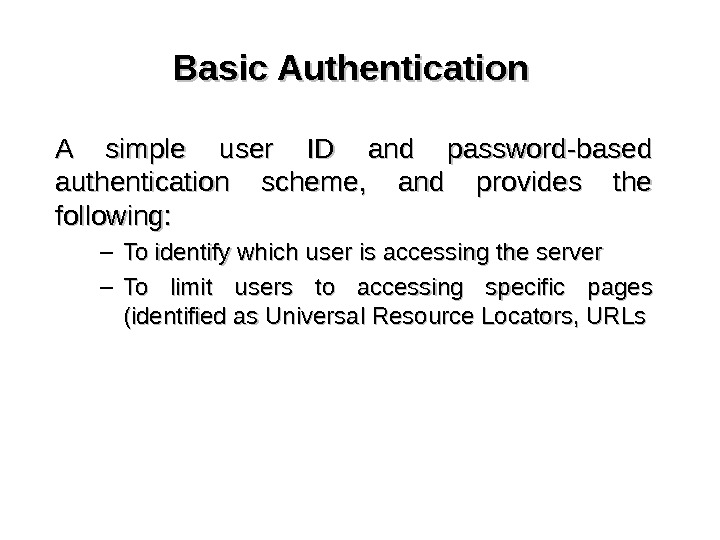
 Basic Authentication A simple user ID and password-based authentication scheme, and provides the following: – To identify which user is accessing the server – To limit users to accessing specific pages (identified as Universal Resource Locators, URLs
Basic Authentication A simple user ID and password-based authentication scheme, and provides the following: – To identify which user is accessing the server – To limit users to accessing specific pages (identified as Universal Resource Locators, URLs
 03/18/16 ms ms 2424 SECURE SOCKET LAYER (SSL) • Netscape Inc. originally created the SSL protocol, but now it is implemented in World Wide Web browsers and servers from many vendors. SSL provides the following — Confidentiality through an encrypted connection based on symmetric keys — Authentication using public key identification and verification — Connection reliability through integrity checking • There are two parts to SSL standard, as follows: The SSL Handshake is a protocol for initial authentication and transfer of encryption keys. The SSL Record protocol is a protocol for transferring encrypted data
03/18/16 ms ms 2424 SECURE SOCKET LAYER (SSL) • Netscape Inc. originally created the SSL protocol, but now it is implemented in World Wide Web browsers and servers from many vendors. SSL provides the following — Confidentiality through an encrypted connection based on symmetric keys — Authentication using public key identification and verification — Connection reliability through integrity checking • There are two parts to SSL standard, as follows: The SSL Handshake is a protocol for initial authentication and transfer of encryption keys. The SSL Record protocol is a protocol for transferring encrypted data
 Secure Socket Layer Cont. . The client sends a «hello» message to the Web server, and the server responds with a copy of its digital certificate. The client decrypts the server’s public key using the well-known public key of the Certificate Authority such as Veri. Sign. The client generates two random numbers that will be used for symmetric key encryption, one number for the receiving channel and one for the sending channel. These keys are encrypted using the server’s public key and then transmitted to the server. The client issues a challenge (some text encrypted with the send key) to the server using the send symmetric key and waits for a response from the server that is using the receive symmetric key. Optional, server authenticates client Data is exchanged across the secure channel.
Secure Socket Layer Cont. . The client sends a «hello» message to the Web server, and the server responds with a copy of its digital certificate. The client decrypts the server’s public key using the well-known public key of the Certificate Authority such as Veri. Sign. The client generates two random numbers that will be used for symmetric key encryption, one number for the receiving channel and one for the sending channel. These keys are encrypted using the server’s public key and then transmitted to the server. The client issues a challenge (some text encrypted with the send key) to the server using the send symmetric key and waits for a response from the server that is using the receive symmetric key. Optional, server authenticates client Data is exchanged across the secure channel.
 Cryptographic Techniques • Secret Key Algorithm • Public Key Algorithm • Secure Hash Function • Digital Signature • Certificate Authority
Cryptographic Techniques • Secret Key Algorithm • Public Key Algorithm • Secure Hash Function • Digital Signature • Certificate Authority
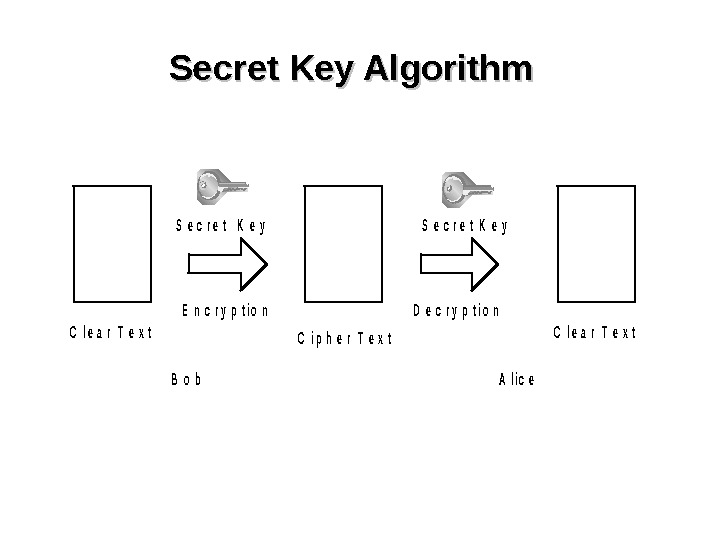
 Secret Key Algorithm. C l e a r T e x t S e c r e t K e y B o b. A l i c e E n c r y p t i o n S e c r e t K e y D e c r y p t i o n C l e a r T e x t. C i p h e r T e x t
Secret Key Algorithm. C l e a r T e x t S e c r e t K e y B o b. A l i c e E n c r y p t i o n S e c r e t K e y D e c r y p t i o n C l e a r T e x t. C i p h e r T e x t
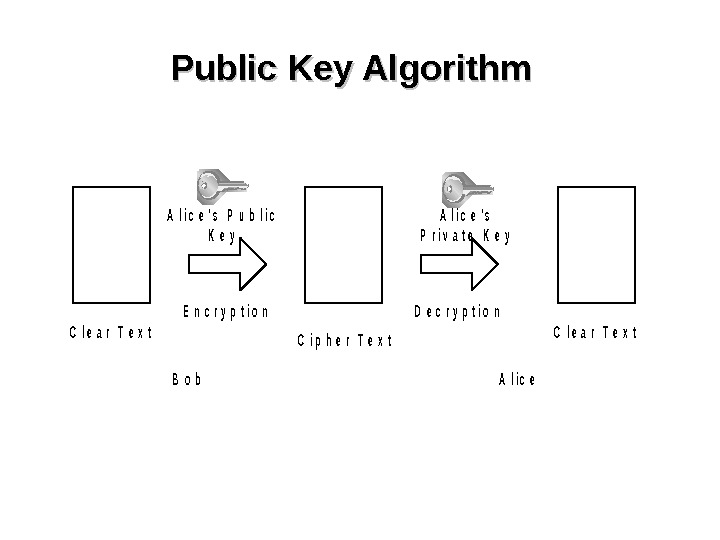
 Public Key Algorithm. C l e a r T e x t A l i c e ‘ s P u b l i c K e y B o b. A l i c e E n c r y p t i o n A l i c e ‘ s P r i v a t e K e y D e c r y p t i o n C l e a r T e x t. C i p h e r T e x t
Public Key Algorithm. C l e a r T e x t A l i c e ‘ s P u b l i c K e y B o b. A l i c e E n c r y p t i o n A l i c e ‘ s P r i v a t e K e y D e c r y p t i o n C l e a r T e x t. C i p h e r T e x t
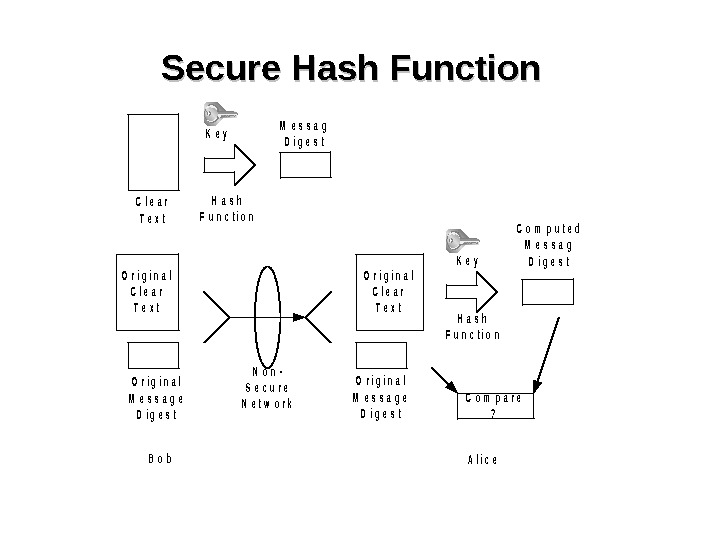
 Secure Hash Function. C l e a r T e x t K e y B o b. A l i c e O r i g i n a l C l e a r T e x t H a s h F u n c t i o n M e s s a g D i g e s t H a s h F u n c t i o n C o m p u t e d M e s s a g D i g e s t. K e y O r i g i n a l M e s s a g e D i g e s t C o m p a r e ? N o n — S e c u r e N e t w o r k
Secure Hash Function. C l e a r T e x t K e y B o b. A l i c e O r i g i n a l C l e a r T e x t H a s h F u n c t i o n M e s s a g D i g e s t H a s h F u n c t i o n C o m p u t e d M e s s a g D i g e s t. K e y O r i g i n a l M e s s a g e D i g e s t C o m p a r e ? N o n — S e c u r e N e t w o r k
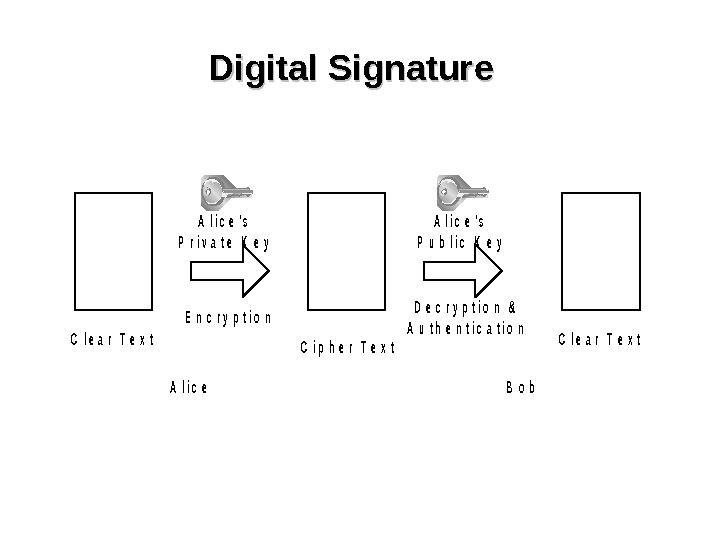
 Digital Signature. C l e a r T e x t A l i c e ‘ s P r i v a t e K e y A l i c e. B o b E n c r y p t i o n A l i c e ‘ s P u b l i c K e y D e c r y p t i o n & A u t h e n t i c a t i o n C l e a r T e x t. C i p h e r T e x t
Digital Signature. C l e a r T e x t A l i c e ‘ s P r i v a t e K e y A l i c e. B o b E n c r y p t i o n A l i c e ‘ s P u b l i c K e y D e c r y p t i o n & A u t h e n t i c a t i o n C l e a r T e x t. C i p h e r T e x t
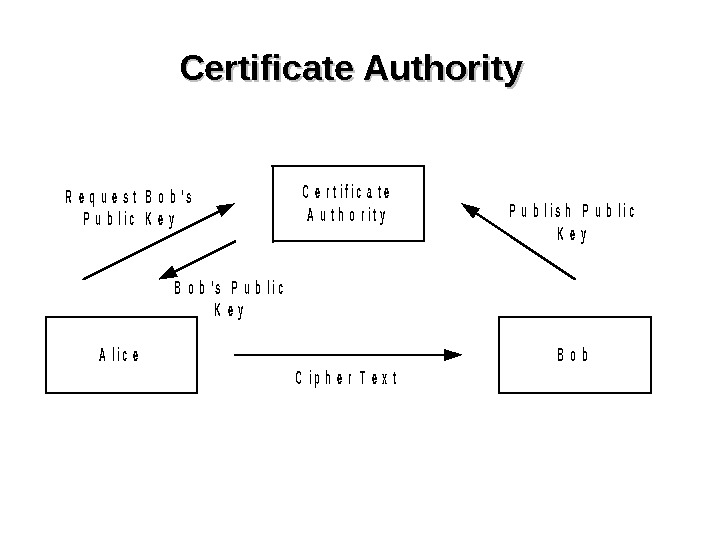
 Certificate Authority. A l i c e. B o b C e r t i f i c a t e A u t h o r i t y. P u b l i s h P u b l i c K e y R e q u e s t B o b ‘ s P u b l i c K e y B o b ‘ s P u b l i c K e y C i p h e r T e x t
Certificate Authority. A l i c e. B o b C e r t i f i c a t e A u t h o r i t y. P u b l i s h P u b l i c K e y R e q u e s t B o b ‘ s P u b l i c K e y B o b ‘ s P u b l i c K e y C i p h e r T e x t
 X. 509 Certificate • Is a ITU-T Recommendation. . • Specifies the authentication service for X. 500 directories • X. 500 specifies the directory services. • Version 1 was published in 1988. • Version 2 was published in 1993. • Version 3 was proposed in 1994 and approved in 1997. • Binds the subject (user’s) name and the user’s public key.
X. 509 Certificate • Is a ITU-T Recommendation. . • Specifies the authentication service for X. 500 directories • X. 500 specifies the directory services. • Version 1 was published in 1988. • Version 2 was published in 1993. • Version 3 was proposed in 1994 and approved in 1997. • Binds the subject (user’s) name and the user’s public key.
 X. 509 Certificate (cont. . ) • X 09 certificate consists of the following fields: – Version – Serial Number – Algorithm Identifier – Issuer name – Validity period – Subject name – Subject public key information – Issuer unique identifier (Version 2 & 3 only) – Subject unique identifier (Version 2 & 3 only) – Extensions (Version 3 only) – Signature
X. 509 Certificate (cont. . ) • X 09 certificate consists of the following fields: – Version – Serial Number – Algorithm Identifier – Issuer name – Validity period – Subject name – Subject public key information – Issuer unique identifier (Version 2 & 3 only) – Subject unique identifier (Version 2 & 3 only) – Extensions (Version 3 only) – Signature
 X. 509 Certificate (Cont. . ) • Version 1 – Basic • Version 2 – Adds unique identifier to prevent reuse of X. 500 • Version 3 – Adds extension to carry additional information and some of them are • Distinguish different certificates • Alternative to X. 500 name • Limit on further certification by subject • Policy and Usage
X. 509 Certificate (Cont. . ) • Version 1 – Basic • Version 2 – Adds unique identifier to prevent reuse of X. 500 • Version 3 – Adds extension to carry additional information and some of them are • Distinguish different certificates • Alternative to X. 500 name • Limit on further certification by subject • Policy and Usage
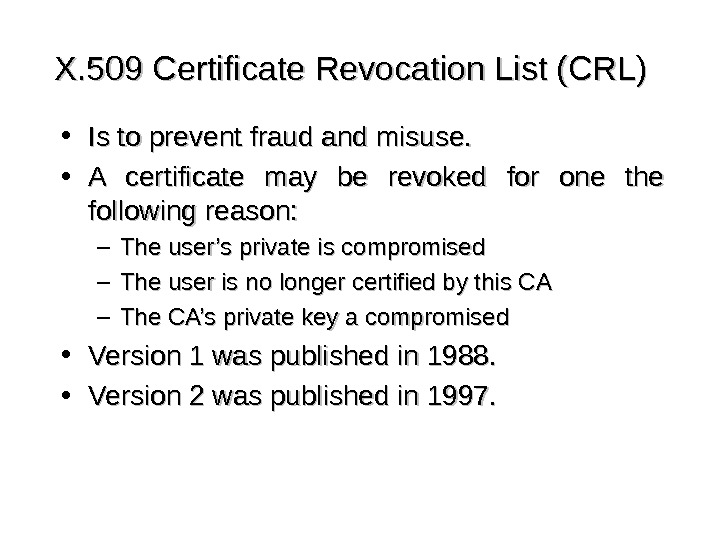
 X. 509 Certificate Revocation List (CRL) • Is to prevent fraud and misuse. • A certificate may be revoked for one the following reason: – The user’s private is compromised – The user is no longer certified by this CA – The CA’s private key a compromised • Version 1 was published in 1988. • Version 2 was published in 1997.
X. 509 Certificate Revocation List (CRL) • Is to prevent fraud and misuse. • A certificate may be revoked for one the following reason: – The user’s private is compromised – The user is no longer certified by this CA – The CA’s private key a compromised • Version 1 was published in 1988. • Version 2 was published in 1997.
 X. 509 CRL (cont. . ) • X 09 CRL consists of the following fields: – Version – Serial Number – Revocation Date – Algorithm Identifier – Issuer name – Last update – Next update – Extensions (Version 2 only) – Signature
X. 509 CRL (cont. . ) • X 09 CRL consists of the following fields: – Version – Serial Number – Revocation Date – Algorithm Identifier – Issuer name – Last update – Next update – Extensions (Version 2 only) – Signature
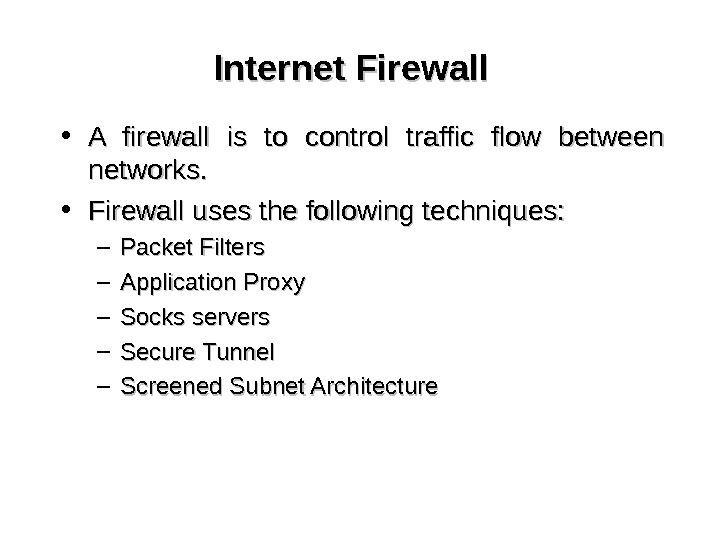
 Internet Firewall • A firewall is to control traffic flow between networks. • Firewall uses the following techniques: – Packet Filters – Application Proxy – Socks servers – Secure Tunnel – Screened Subnet Architecture
Internet Firewall • A firewall is to control traffic flow between networks. • Firewall uses the following techniques: – Packet Filters – Application Proxy – Socks servers – Secure Tunnel – Screened Subnet Architecture
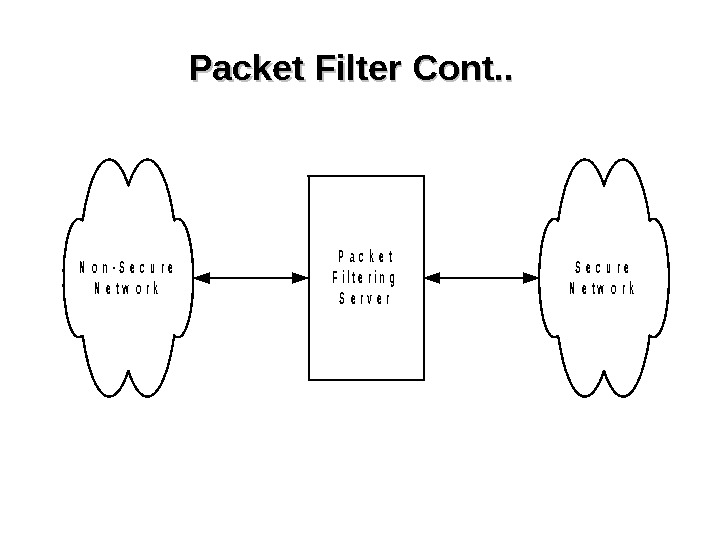
 Packet Filtering • Most commonly used firewall technique • Operates at IP level • Checks each IP packet against the filter rules before passing (or not passing) it on to its destination. • Very fast than other firewall techniques • Hard to configure
Packet Filtering • Most commonly used firewall technique • Operates at IP level • Checks each IP packet against the filter rules before passing (or not passing) it on to its destination. • Very fast than other firewall techniques • Hard to configure
 Packet Filter Cont. . P a c k e t F i l t e r i n g S e r v e r N o n — S e c u r e N e t w o r k
Packet Filter Cont. . P a c k e t F i l t e r i n g S e r v e r N o n — S e c u r e N e t w o r k
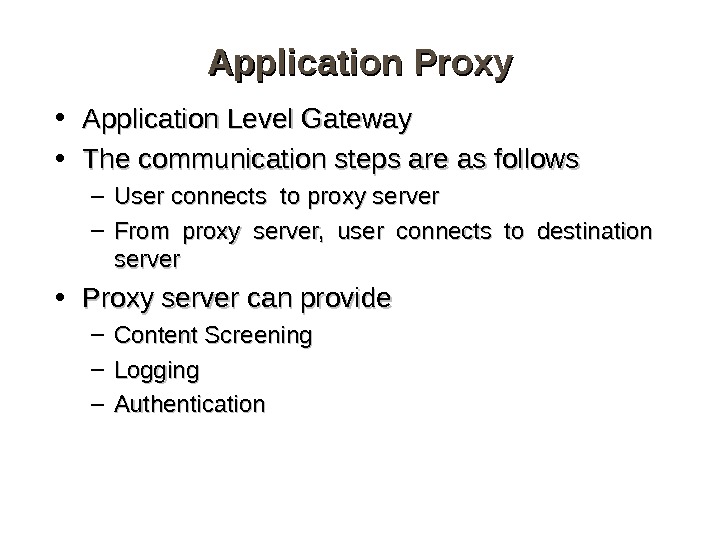
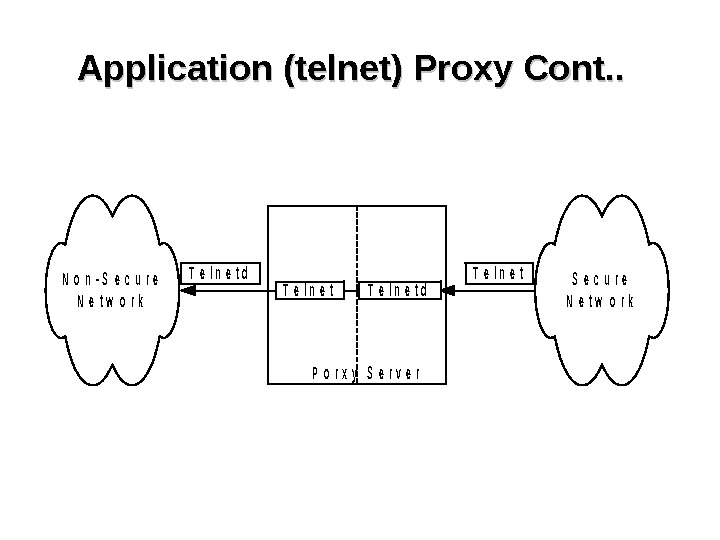
 Application Proxy • Application Level Gateway • The communication steps are as follows – User connects to proxy server – From proxy server, user connects to destination server • Proxy server can provide – Content Screening – Logging – Authentication
Application Proxy • Application Level Gateway • The communication steps are as follows – User connects to proxy server – From proxy server, user connects to destination server • Proxy server can provide – Content Screening – Logging – Authentication
 Application (telnet) Proxy Cont. . N o n — S e c u r e N e t w o r k T e l n e t d P o r x y S e r v e r T e l n e t d
Application (telnet) Proxy Cont. . N o n — S e c u r e N e t w o r k T e l n e t d P o r x y S e r v e r T e l n e t d
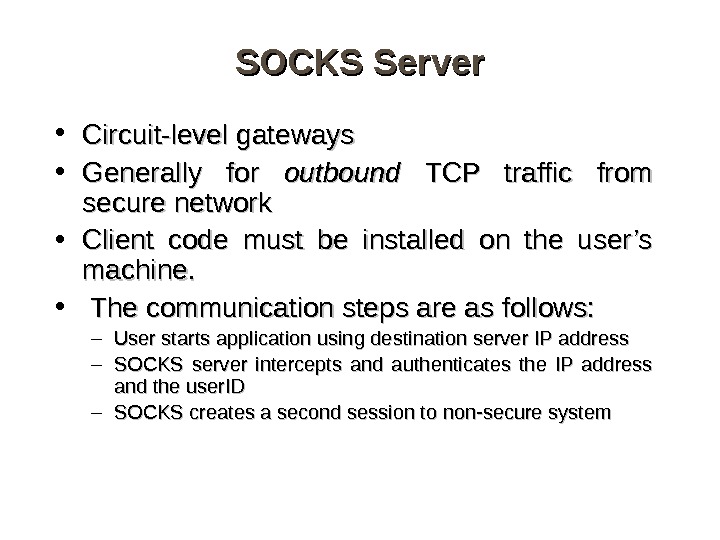
 SOCKS Server • Circuit-level gateways • Generally for outbound TCP traffic from secure network • Client code must be installed on the user’s machine. • The communication steps are as follows: – User starts application using destination server IP address – SOCKS server intercepts and authenticates the IP address and the user. ID – SOCKS creates a second session to non-secure system
SOCKS Server • Circuit-level gateways • Generally for outbound TCP traffic from secure network • Client code must be installed on the user’s machine. • The communication steps are as follows: – User starts application using destination server IP address – SOCKS server intercepts and authenticates the IP address and the user. ID – SOCKS creates a second session to non-secure system
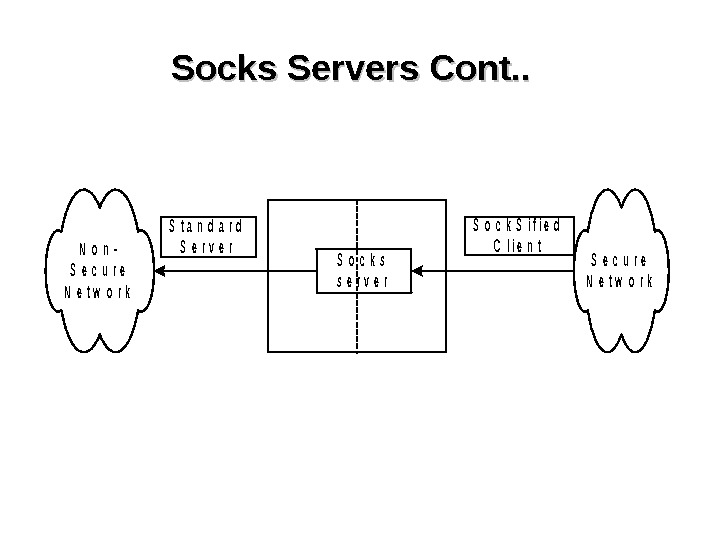
 Socks Servers Cont. . N o n — S e c u r e N e t w o r k S o c k S i f i e d C l i e n t S t a n d a r d S e r v e r S o c k s s e r v e r
Socks Servers Cont. . N o n — S e c u r e N e t w o r k S o c k S i f i e d C l i e n t S t a n d a r d S e r v e r S o c k s s e r v e r
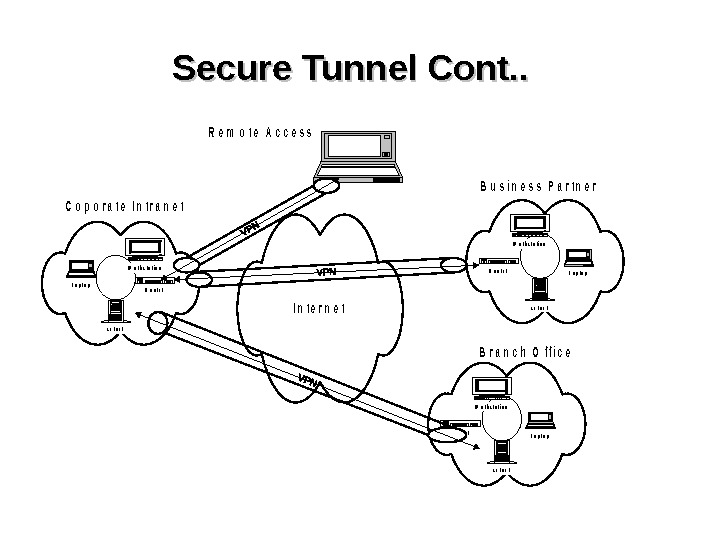
 Secure Tunnel Cont. . W o r k s t a t i o n L a p t o p s e r v e r R o u t e r I n t e r n e t W o r k s t a t i o n L a p t o p s e r v e r R o u t e r C o p o r a t e I n t r a n e t B u s i n e s s P a r t n e r B r a n c h O f f i c e R e m o t e A c c e s s
Secure Tunnel Cont. . W o r k s t a t i o n L a p t o p s e r v e r R o u t e r I n t e r n e t W o r k s t a t i o n L a p t o p s e r v e r R o u t e r C o p o r a t e I n t r a n e t B u s i n e s s P a r t n e r B r a n c h O f f i c e R e m o t e A c c e s s
 Secure IP Tunnel • A secure channel between the secure network and an external trusted server through a non-secure network (e. g. , Internet) • Encrypts the data between the Firewall and the external trusted host • Also identifies of the session partners and the messages authenticity
Secure IP Tunnel • A secure channel between the secure network and an external trusted server through a non-secure network (e. g. , Internet) • Encrypts the data between the Firewall and the external trusted host • Also identifies of the session partners and the messages authenticity
 VPN Solutions • IP Security (IPSec) • Layer 2 Tunnel Protocol (L 2 TP) • Virtual Circuits • Multi Protocol Label Switching (MPLS)
VPN Solutions • IP Security (IPSec) • Layer 2 Tunnel Protocol (L 2 TP) • Virtual Circuits • Multi Protocol Label Switching (MPLS)
 IPSec Solution • IPSec is an Internet standard for ensuring secure private communication over IP networks, and it was developed by IPSec working group of IETF • IPSec implements network layer security
IPSec Solution • IPSec is an Internet standard for ensuring secure private communication over IP networks, and it was developed by IPSec working group of IETF • IPSec implements network layer security
 Principle of IPSec protocols • Authentication Header (AH) – Provides data origin authentication, data integrity and replay protection • Encapsulating Security Payload (ESP) – Provides data confidentiality, data origin authentication, data integrity and replay protection • Internet Security Association and Key Management Protocol (ISAKMP) or Internet Key Exchange (IKE) – Provides a method for automatically setting up security association and managing their cryptographic key. • Security Association (SA) – Provides all the relevant information that communicating systems need to execute the IPSec protocols.
Principle of IPSec protocols • Authentication Header (AH) – Provides data origin authentication, data integrity and replay protection • Encapsulating Security Payload (ESP) – Provides data confidentiality, data origin authentication, data integrity and replay protection • Internet Security Association and Key Management Protocol (ISAKMP) or Internet Key Exchange (IKE) – Provides a method for automatically setting up security association and managing their cryptographic key. • Security Association (SA) – Provides all the relevant information that communicating systems need to execute the IPSec protocols.
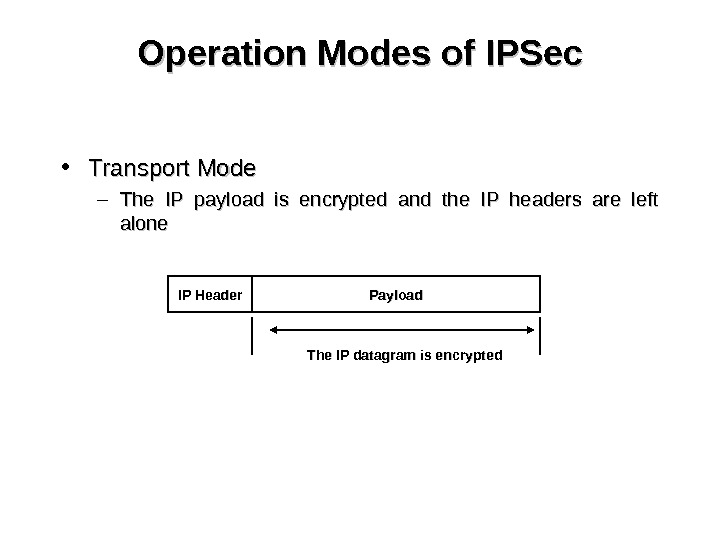
 Operation Modes of IPSec • Transport Mode – The IP payload is encrypted and the IP headers are left alone IP Header Payload The IP datagram is encrypted
Operation Modes of IPSec • Transport Mode – The IP payload is encrypted and the IP headers are left alone IP Header Payload The IP datagram is encrypted
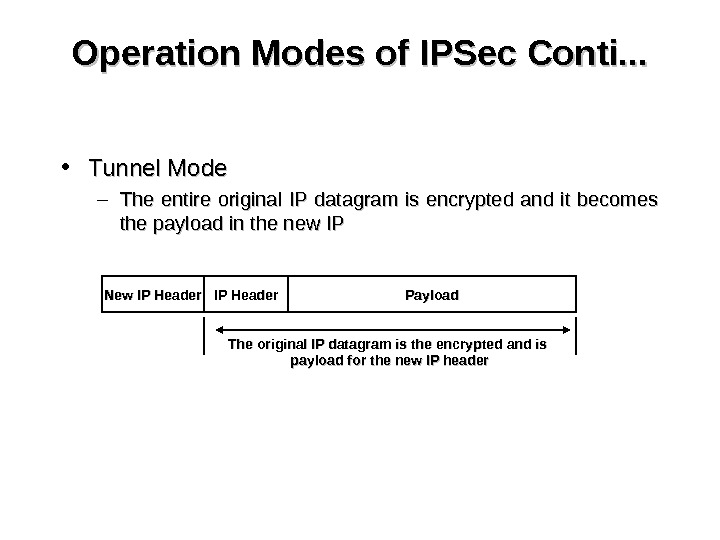
 Operation Modes of IPSec Conti. . . • Tunnel Mode – The entire original IP datagram is encrypted and it becomes the payload in the new IP New IP Header Payload The original IP datagram is the encrypted and is payload for the new IP header
Operation Modes of IPSec Conti. . . • Tunnel Mode – The entire original IP datagram is encrypted and it becomes the payload in the new IP New IP Header Payload The original IP datagram is the encrypted and is payload for the new IP header
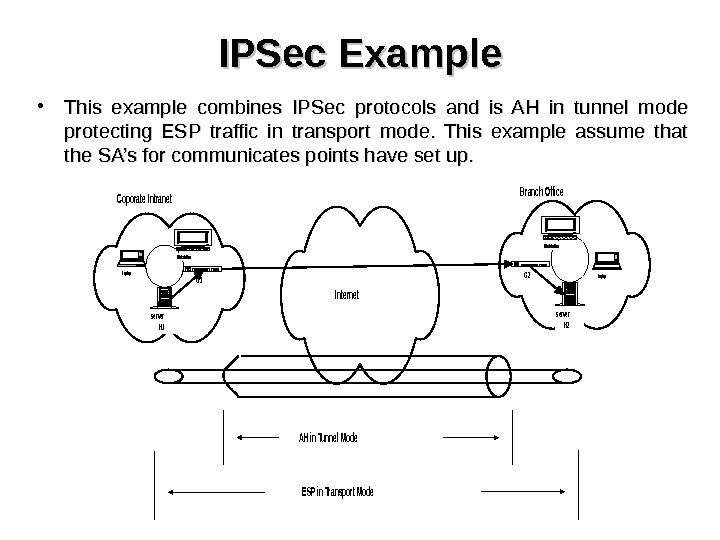
 IPSec Example • This example combines IPSec protocols and is AH in tunnel mode protecting ESP traffic in transport mode. This example assume that the SA’s for communicates points have set up. Workstation Laptop server H 1 G 1 Internet Coporate Intranet Workstation Laptop server H 2 G 2 Branch Office AH in Tunnel Mode ESP in Transport Mode
IPSec Example • This example combines IPSec protocols and is AH in tunnel mode protecting ESP traffic in transport mode. This example assume that the SA’s for communicates points have set up. Workstation Laptop server H 1 G 1 Internet Coporate Intranet Workstation Laptop server H 2 G 2 Branch Office AH in Tunnel Mode ESP in Transport Mode
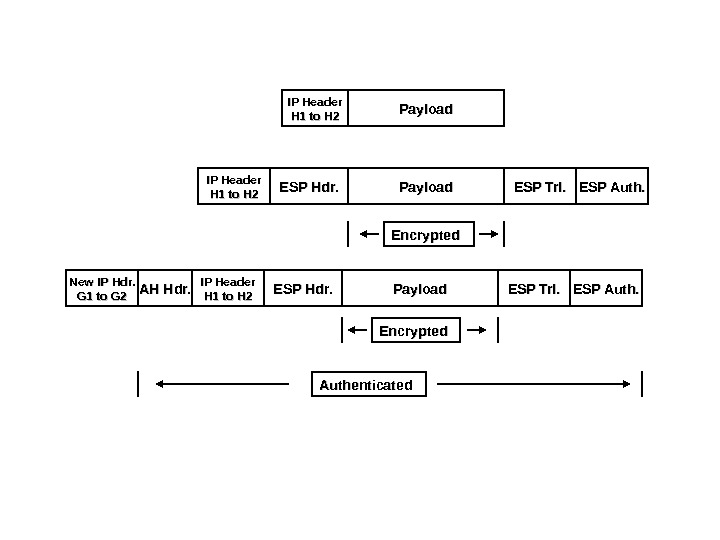
 IP Header H 1 to H 2 Payload New IP Hdr. G 1 to G 2 IP Header H 1 to H 2 H 1 to H 2 Payload ESP Hdr. ESP Trl. ESP Auth. AH Hdr. Encrypted Authenticated
IP Header H 1 to H 2 Payload New IP Hdr. G 1 to G 2 IP Header H 1 to H 2 H 1 to H 2 Payload ESP Hdr. ESP Trl. ESP Auth. AH Hdr. Encrypted Authenticated
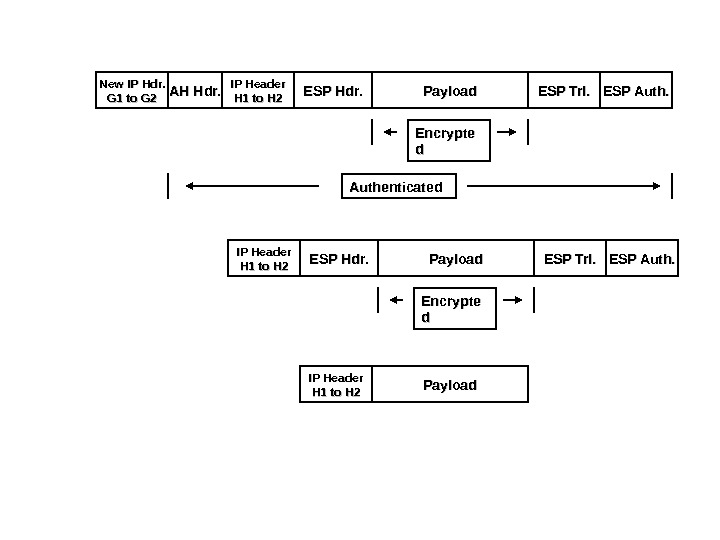
 New IP Hdr. G 1 to G 2 IP Header H 1 to H 2 Payload ESP Hdr. ESP Trl. ESP Auth. AH Hdr. Encrypte dd Authenticated IP Header H 1 to H 2 Payload ESP Hdr. ESP Trl. ESP Auth. Encrypte dd IP Header H 1 to H 2 Payload
New IP Hdr. G 1 to G 2 IP Header H 1 to H 2 Payload ESP Hdr. ESP Trl. ESP Auth. AH Hdr. Encrypte dd Authenticated IP Header H 1 to H 2 Payload ESP Hdr. ESP Trl. ESP Auth. Encrypte dd IP Header H 1 to H 2 Payload
 Screened Subnet Architecture Cont. . D N o n — S e c u r e N e t w o r k P a c k e t F i l t e r i n g T e l e n t P r o x y S e r v e r S o c k s S e r v e r H T T P P r o x y S e r v e r F T P P r o x y S e r v e r S c r e e n e d S u b n e t D e m i l i t a r i z e d Z o n e ( D M Z )
Screened Subnet Architecture Cont. . D N o n — S e c u r e N e t w o r k P a c k e t F i l t e r i n g T e l e n t P r o x y S e r v e r S o c k s S e r v e r H T T P P r o x y S e r v e r F T P P r o x y S e r v e r S c r e e n e d S u b n e t D e m i l i t a r i z e d Z o n e ( D M Z )
 Screened Subnet Architecture • The DMZ (perimeter network) is set up between the secure and non-secure networks • It is accessible from both networks and contains machines that act as gateways for specific applications
Screened Subnet Architecture • The DMZ (perimeter network) is set up between the secure and non-secure networks • It is accessible from both networks and contains machines that act as gateways for specific applications
 Firewall Conclusion • Not the complete answer • The fox is inside the henhouse • Host security + User education • Cannot control back door traffic • any dial-in access • Management problems • Cannot fully protect against new viruses • Antivirus on each host Machine • Needs to be correctly configured • The security policy must be enforced
Firewall Conclusion • Not the complete answer • The fox is inside the henhouse • Host security + User education • Cannot control back door traffic • any dial-in access • Management problems • Cannot fully protect against new viruses • Antivirus on each host Machine • Needs to be correctly configured • The security policy must be enforced

