Operation Security Understand the core of Operations Security












































lecture_4-5.ppt
- Количество слайдов: 57
 Operation Security
Operation Security
 Understand the core of Operations Security (OPSEC) Define & identify targets and threats Establish countermeasures Identify the Critical Information Commandments Decipher the value of information Objective
Understand the core of Operations Security (OPSEC) Define & identify targets and threats Establish countermeasures Identify the Critical Information Commandments Decipher the value of information Objective
 What is Operation Security…? Have you ever taken precautions against Someone… …breaking into your house while you’re on vacation? …stealing your purse? …stealing packages from your car while your shopping? …fraudulently using your credit card? Then you have used OPSEC!
What is Operation Security…? Have you ever taken precautions against Someone… …breaking into your house while you’re on vacation? …stealing your purse? …stealing packages from your car while your shopping? …fraudulently using your credit card? Then you have used OPSEC!
 OPSEC is a risk management instrument that enables a manager or commander to view an operation or activity from the perspective of an adversary. It is a process of identifying, analyzing and controlling critical information. What is Operation Security …?
OPSEC is a risk management instrument that enables a manager or commander to view an operation or activity from the perspective of an adversary. It is a process of identifying, analyzing and controlling critical information. What is Operation Security …?
 Identify Critical Information Analyze Threats Discover Vulnerabilities Assess Risks Develop Countermeasures What is Operation Security …?
Identify Critical Information Analyze Threats Discover Vulnerabilities Assess Risks Develop Countermeasures What is Operation Security …?
 Identify Critical Information: Credit card numbers, travel dates, itineraries, passwords, patterns, changes in patterns, inspection results, information base systems, etc.. Analyze Threat: Adversaries, Intelligence agencies – Open source information, corporate/state sponsored spies, eavesdropping, photographing, etc… What is Operation Security …?
Identify Critical Information: Credit card numbers, travel dates, itineraries, passwords, patterns, changes in patterns, inspection results, information base systems, etc.. Analyze Threat: Adversaries, Intelligence agencies – Open source information, corporate/state sponsored spies, eavesdropping, photographing, etc… What is Operation Security …?
 Discover Vulnerabilities: Flow of information, operations, timing of events, how an adversary would acquire the information, etc… How would the loss of such data impact the organization? Assess Risks: Estimated loss $ x impact of risk x likelihood of risk = $ Does the solution outweigh the loss? What is Operation Security …?
Discover Vulnerabilities: Flow of information, operations, timing of events, how an adversary would acquire the information, etc… How would the loss of such data impact the organization? Assess Risks: Estimated loss $ x impact of risk x likelihood of risk = $ Does the solution outweigh the loss? What is Operation Security …?
 Develop Countermeasures: are based on the vulnerabilities and inherent risks. Are dictated by cost, timing, feasibility, and imagination of involved personnel. Simplicity, straightforwardness, and inexpensiveness are key to the most effective countermeasure solutions. OPSEC is a DIFFERENT WAY of SEEING What is Operation Security …?
Develop Countermeasures: are based on the vulnerabilities and inherent risks. Are dictated by cost, timing, feasibility, and imagination of involved personnel. Simplicity, straightforwardness, and inexpensiveness are key to the most effective countermeasure solutions. OPSEC is a DIFFERENT WAY of SEEING What is Operation Security …?
 Critical Information Commandments… Must protect the information that the adversary needs to accomplish his mission. Will not try to protect everything. Consider who thy adversaries are and what information they require to inflict harm to you. Consult all sources of information to determine what your enemies know about you. Once you has determined what information is critical, determine if that information is associated with your activities.
Critical Information Commandments… Must protect the information that the adversary needs to accomplish his mission. Will not try to protect everything. Consider who thy adversaries are and what information they require to inflict harm to you. Consult all sources of information to determine what your enemies know about you. Once you has determined what information is critical, determine if that information is associated with your activities.

 Malicious Software
Malicious Software
 Viruses and Other Malicious Content computer viruses have got a lot of publicity one of a family of malicious software effects usually obvious have figured in news reports, fiction, movies (often exaggerated) getting more attention than deserve are a concern though
Viruses and Other Malicious Content computer viruses have got a lot of publicity one of a family of malicious software effects usually obvious have figured in news reports, fiction, movies (often exaggerated) getting more attention than deserve are a concern though
 The Most Common Types Of Program To Be Infected by A Virus exe com vbs mp3 drv bin script files macros
The Most Common Types Of Program To Be Infected by A Virus exe com vbs mp3 drv bin script files macros
 Cryptography and Network Security 14 Malicious Software
Cryptography and Network Security 14 Malicious Software
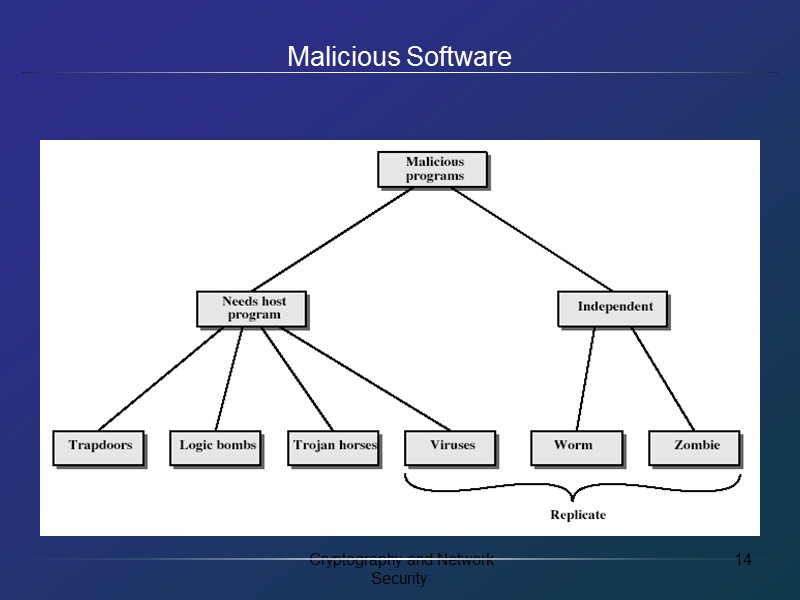
 Trapdoors secret entry point into a program allows those who know access bypassing usual security procedures have been commonly used by developers a threat when left in production programs allowing exploited by attackers very hard to block in O/S requires good s/w development & update
Trapdoors secret entry point into a program allows those who know access bypassing usual security procedures have been commonly used by developers a threat when left in production programs allowing exploited by attackers very hard to block in O/S requires good s/w development & update
 Logic Bomb one of oldest types of malicious software code embedded in legitimate program activated when specified conditions met eg presence/absence of some file particular date/time particular user when triggered typically damage system modify/delete files/disks
Logic Bomb one of oldest types of malicious software code embedded in legitimate program activated when specified conditions met eg presence/absence of some file particular date/time particular user when triggered typically damage system modify/delete files/disks
 Trojan Horse program with hidden side-effects which is usually superficially attractive eg game, s/w upgrade etc when run performs some additional tasks allows attacker to indirectly gain access they do not have directly often used to propagate a virus/worm or install a backdoor or simply to destroy data
Trojan Horse program with hidden side-effects which is usually superficially attractive eg game, s/w upgrade etc when run performs some additional tasks allows attacker to indirectly gain access they do not have directly often used to propagate a virus/worm or install a backdoor or simply to destroy data
 Zombie program which secretly takes over another networked computer then uses it to indirectly launch attacks often used to launch distributed denial of service (DDoS) attacks exploits known flaws in network systems
Zombie program which secretly takes over another networked computer then uses it to indirectly launch attacks often used to launch distributed denial of service (DDoS) attacks exploits known flaws in network systems
 Viruses a piece of self-replicating code attached to some other code cf biological virus both propagates itself & carries a payload carries code to make copies of itself as well as code to perform some covert task
Viruses a piece of self-replicating code attached to some other code cf biological virus both propagates itself & carries a payload carries code to make copies of itself as well as code to perform some covert task
 Virus Operation virus phases: dormant – waiting on trigger event propagation – replicating to programs/disks triggering – by event to execute payload execution – of payload details usually machine/OS specific exploiting features/weaknesses
Virus Operation virus phases: dormant – waiting on trigger event propagation – replicating to programs/disks triggering – by event to execute payload execution – of payload details usually machine/OS specific exploiting features/weaknesses
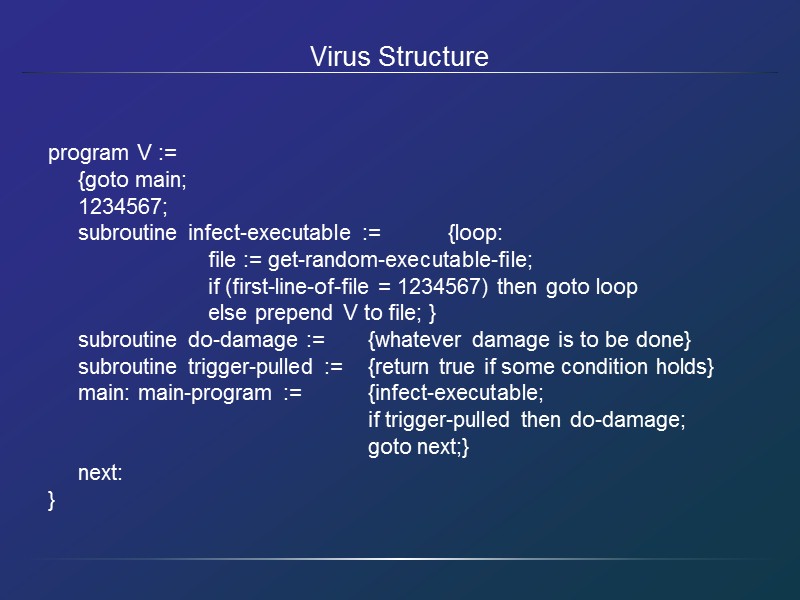
 Virus Structure program V := {goto main; 1234567; subroutine infect-executable := {loop: file := get-random-executable-file; if (first-line-of-file = 1234567) then goto loop else prepend V to file; } subroutine do-damage := {whatever damage is to be done} subroutine trigger-pulled := {return true if some condition holds} main: main-program := {infect-executable; if trigger-pulled then do-damage; goto next;} next: }
Virus Structure program V := {goto main; 1234567; subroutine infect-executable := {loop: file := get-random-executable-file; if (first-line-of-file = 1234567) then goto loop else prepend V to file; } subroutine do-damage := {whatever damage is to be done} subroutine trigger-pulled := {return true if some condition holds} main: main-program := {infect-executable; if trigger-pulled then do-damage; goto next;} next: }
 Types of Viruses can classify on basis of how they attack parasitic virus memory-resident virus boot sector virus stealth polymorphic virus macro virus
Types of Viruses can classify on basis of how they attack parasitic virus memory-resident virus boot sector virus stealth polymorphic virus macro virus
 Macro Virus macro code attached to some data file interpreted by program using file eg Word/Excel macros esp. using auto command & command macros code is now platform independent is a major source of new viral infections blurs distinction between data and program files making task of detection much harder classic trade-off: "ease of use" vs "security"
Macro Virus macro code attached to some data file interpreted by program using file eg Word/Excel macros esp. using auto command & command macros code is now platform independent is a major source of new viral infections blurs distinction between data and program files making task of detection much harder classic trade-off: "ease of use" vs "security"
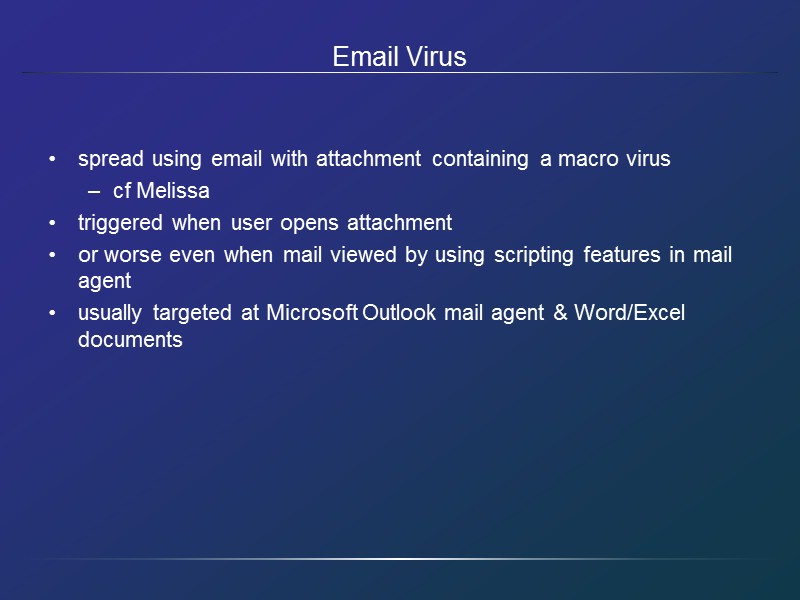
 Email Virus spread using email with attachment containing a macro virus cf Melissa triggered when user opens attachment or worse even when mail viewed by using scripting features in mail agent usually targeted at Microsoft Outlook mail agent & Word/Excel documents
Email Virus spread using email with attachment containing a macro virus cf Melissa triggered when user opens attachment or worse even when mail viewed by using scripting features in mail agent usually targeted at Microsoft Outlook mail agent & Word/Excel documents
 Worms replicating but not infecting program typically spreads over a network cf Morris Internet Worm in 1988 led to creation of CERTs using users distributed privileges or by exploiting system vulnerabilities widely used by hackers to create zombie PC's, subsequently used for further attacks, esp DoS major issue is lack of security of permanently connected systems, esp PC's
Worms replicating but not infecting program typically spreads over a network cf Morris Internet Worm in 1988 led to creation of CERTs using users distributed privileges or by exploiting system vulnerabilities widely used by hackers to create zombie PC's, subsequently used for further attacks, esp DoS major issue is lack of security of permanently connected systems, esp PC's
 Worm Operation worm phases like those of viruses: dormant propagation search for other systems to infect establish connection to target remote system replicate self onto remote system triggering execution
Worm Operation worm phases like those of viruses: dormant propagation search for other systems to infect establish connection to target remote system replicate self onto remote system triggering execution
 Morris Worm best known classic worm released by Robert Morris in 1988 targeted Unix systems using several propagation techniques simple password cracking of local pw file exploit bug in finger daemon exploit debug trapdoor in sendmail daemon if any attack succeeds then replicated self
Morris Worm best known classic worm released by Robert Morris in 1988 targeted Unix systems using several propagation techniques simple password cracking of local pw file exploit bug in finger daemon exploit debug trapdoor in sendmail daemon if any attack succeeds then replicated self
 Recent Worm Attacks new spate of attacks from mid-2001 Code Red exploited bug in MS IIS to penetrate & spread probes random IPs for systems running IIS had trigger time for denial-of-service attack 2nd wave infected 360000 servers in 14 hours Code Red 2 had backdoor installed to allow remote control Nimda used multiple infection mechanisms email, shares, web client, IIS, Code Red 2 backdoor
Recent Worm Attacks new spate of attacks from mid-2001 Code Red exploited bug in MS IIS to penetrate & spread probes random IPs for systems running IIS had trigger time for denial-of-service attack 2nd wave infected 360000 servers in 14 hours Code Red 2 had backdoor installed to allow remote control Nimda used multiple infection mechanisms email, shares, web client, IIS, Code Red 2 backdoor
 Virus Countermeasures viral attacks exploit lack of integrity control on systems to defend need to add such controls typically by one or more of: prevention - block virus infection mechanism detection - of viruses in infected system reaction - restoring system to clean state
Virus Countermeasures viral attacks exploit lack of integrity control on systems to defend need to add such controls typically by one or more of: prevention - block virus infection mechanism detection - of viruses in infected system reaction - restoring system to clean state
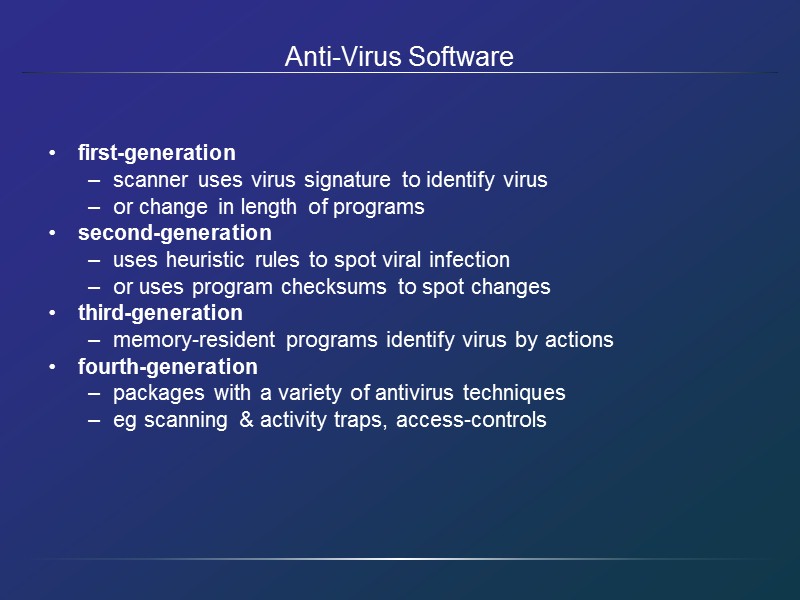
 Anti-Virus Software first-generation scanner uses virus signature to identify virus or change in length of programs second-generation uses heuristic rules to spot viral infection or uses program checksums to spot changes third-generation memory-resident programs identify virus by actions fourth-generation packages with a variety of antivirus techniques eg scanning & activity traps, access-controls
Anti-Virus Software first-generation scanner uses virus signature to identify virus or change in length of programs second-generation uses heuristic rules to spot viral infection or uses program checksums to spot changes third-generation memory-resident programs identify virus by actions fourth-generation packages with a variety of antivirus techniques eg scanning & activity traps, access-controls
 Advanced Anti-Virus Techniques generic decryption use CPU simulator to check program signature & behavior before actually running it digital immune system (IBM) general purpose emulation & virus detection any virus entering org is captured, analyzed, detection/shielding created for it, removed
Advanced Anti-Virus Techniques generic decryption use CPU simulator to check program signature & behavior before actually running it digital immune system (IBM) general purpose emulation & virus detection any virus entering org is captured, analyzed, detection/shielding created for it, removed
 Behavior-Blocking Software integrated with host O/S monitors program behavior in real-time eg file access, disk format, executable mods, system settings changes, network access for possibly malicious actions if detected can block, terminate, or seek ok has advantage over scanners but malicious code runs before detection
Behavior-Blocking Software integrated with host O/S monitors program behavior in real-time eg file access, disk format, executable mods, system settings changes, network access for possibly malicious actions if detected can block, terminate, or seek ok has advantage over scanners but malicious code runs before detection
 Summary have considered: various malicious programs trapdoor, logic bomb, trojan horse, zombie viruses worms countermeasures
Summary have considered: various malicious programs trapdoor, logic bomb, trojan horse, zombie viruses worms countermeasures

 Cryptography Cryptography is the study of Secret (crypto-) writing (-graphy) Concerned with developing algorithms: Conceal the context of some message from all except the sender and recipient (privacy or secrecy), and/or Verify the correctness of a message to the recipient (authentication) Form the basis of many technological solutions to computer and communications security problems
Cryptography Cryptography is the study of Secret (crypto-) writing (-graphy) Concerned with developing algorithms: Conceal the context of some message from all except the sender and recipient (privacy or secrecy), and/or Verify the correctness of a message to the recipient (authentication) Form the basis of many technological solutions to computer and communications security problems
 Basic Concepts Cryptography encompassing the principles and methods of transforming an intelligible message into one that is unintelligible, and then retransforming that message back to its original form Plaintext The original intelligible message Ciphertext The transformed message Message Is treated as a non-negative integer hereafter
Basic Concepts Cryptography encompassing the principles and methods of transforming an intelligible message into one that is unintelligible, and then retransforming that message back to its original form Plaintext The original intelligible message Ciphertext The transformed message Message Is treated as a non-negative integer hereafter
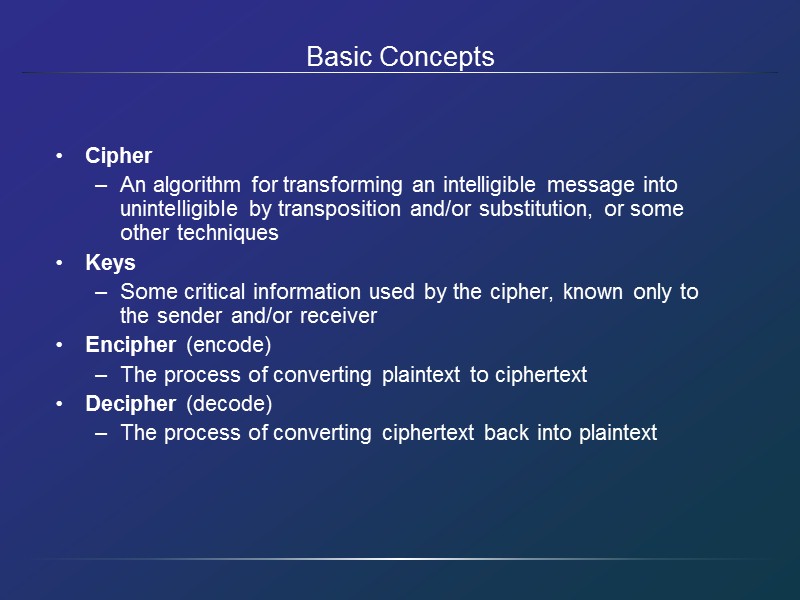
 Basic Concepts Cipher An algorithm for transforming an intelligible message into unintelligible by transposition and/or substitution, or some other techniques Keys Some critical information used by the cipher, known only to the sender and/or receiver Encipher (encode) The process of converting plaintext to ciphertext Decipher (decode) The process of converting ciphertext back into plaintext
Basic Concepts Cipher An algorithm for transforming an intelligible message into unintelligible by transposition and/or substitution, or some other techniques Keys Some critical information used by the cipher, known only to the sender and/or receiver Encipher (encode) The process of converting plaintext to ciphertext Decipher (decode) The process of converting ciphertext back into plaintext
 Basic Concepts cipher an algorithm for encryption and decryption. The exact operation of ciphers is normally controlled by a key — some secret piece of information that customizes how the ciphertext is produced Protocols specify the details of how ciphers (and other cryptographic primitives) are to be used to achieve specific tasks. A suite of protocols, ciphers, key management, user-prescribed actions implemented together as a system constitute a cryptosystem; this is what an end-user interacts with, e.g. PGP
Basic Concepts cipher an algorithm for encryption and decryption. The exact operation of ciphers is normally controlled by a key — some secret piece of information that customizes how the ciphertext is produced Protocols specify the details of how ciphers (and other cryptographic primitives) are to be used to achieve specific tasks. A suite of protocols, ciphers, key management, user-prescribed actions implemented together as a system constitute a cryptosystem; this is what an end-user interacts with, e.g. PGP
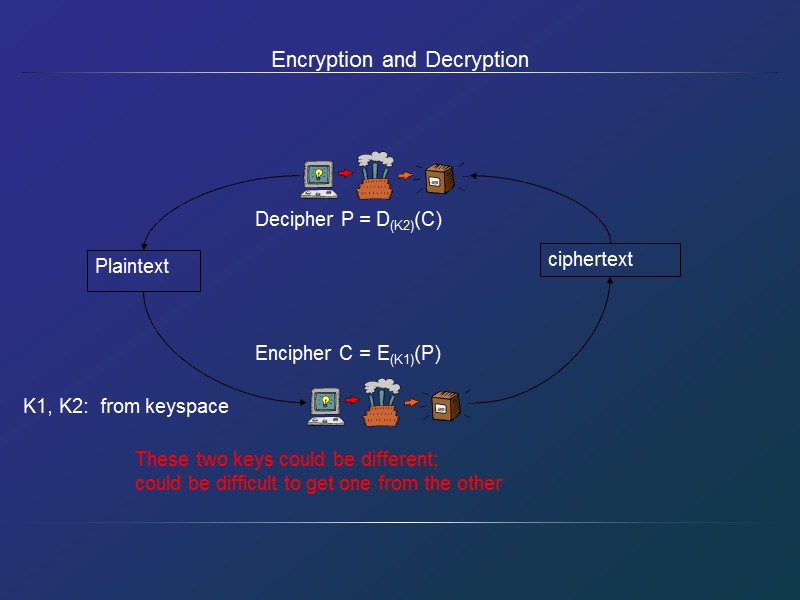
 Encryption and Decryption Plaintext ciphertext Encipher C = E(K1)(P) Decipher P = D(K2)(C) K1, K2: from keyspace These two keys could be different; could be difficult to get one from the other
Encryption and Decryption Plaintext ciphertext Encipher C = E(K1)(P) Decipher P = D(K2)(C) K1, K2: from keyspace These two keys could be different; could be difficult to get one from the other
 What is Security? Two fundamentally different securities Unconditional security No matter how much computer power is available, the cipher cannot be broken Using Shannon’s information theory The entropy of the message I(M) is same as the entropy of the message I(M|C) when known the ciphertext (and possible more) Computational security Given limited computing resources (e.g time needed for calculations is greater than age of universe), the cipher cannot be broken What do we mean “broken”? Proved by some complexity equivalence approach
What is Security? Two fundamentally different securities Unconditional security No matter how much computer power is available, the cipher cannot be broken Using Shannon’s information theory The entropy of the message I(M) is same as the entropy of the message I(M|C) when known the ciphertext (and possible more) Computational security Given limited computing resources (e.g time needed for calculations is greater than age of universe), the cipher cannot be broken What do we mean “broken”? Proved by some complexity equivalence approach

 Public key system
Public key system
 Public Key Encryption Two difficult problems Key distribution under conventional encryption Digital signature Diffie and Hellman, 1976 Astonishing breakthrough One key for encryption and the other related key for decryption It is computationally infeasible to determine the decryption key using only the encryption key and the algorithm
Public Key Encryption Two difficult problems Key distribution under conventional encryption Digital signature Diffie and Hellman, 1976 Astonishing breakthrough One key for encryption and the other related key for decryption It is computationally infeasible to determine the decryption key using only the encryption key and the algorithm
 Public Key Cryptosystem Essential steps of public key cryptosystem Each end generates a pair of keys One for encryption and one for decryption Each system publishes one key, called public key, and the companion key is kept secret It A wants to send message to B Encrypt it using B’s public key When B receives the encrypted message It decrypt it using its own private key
Public Key Cryptosystem Essential steps of public key cryptosystem Each end generates a pair of keys One for encryption and one for decryption Each system publishes one key, called public key, and the companion key is kept secret It A wants to send message to B Encrypt it using B’s public key When B receives the encrypted message It decrypt it using its own private key
 Applications of PKC Encryption/Decryption The sender encrypts the message using the receiver’s public key Q: Why not use the sender’s secret key? Digital signature The sender signs a message by encrypt the message or a transformation of the message using its own private key Key exchange Two sides cooperate to exchange a session key, typically for conventional encryption
Applications of PKC Encryption/Decryption The sender encrypts the message using the receiver’s public key Q: Why not use the sender’s secret key? Digital signature The sender signs a message by encrypt the message or a transformation of the message using its own private key Key exchange Two sides cooperate to exchange a session key, typically for conventional encryption
 Conditions of PKC Computationally easy To generate public and private key pair To encrypt the message using encryption key To decrypt the message using decryption key Computational infeasible To compute the private key using public key To recover the plaintext using ciphertext and public key The encryption and decryption can be applied in either order
Conditions of PKC Computationally easy To generate public and private key pair To encrypt the message using encryption key To decrypt the message using decryption key Computational infeasible To compute the private key using public key To recover the plaintext using ciphertext and public key The encryption and decryption can be applied in either order
 One Way Function PKC boils down to one way function Maps a domain into a range with unique inverse The calculation of the function is easy The calculation of the inverse is infeasible Easy The problem can be solved in polynomial time Infeasible The effort to solve it grows faster than polynomial time For example: 2n It requires infeasible for all inputs, not just worst case
One Way Function PKC boils down to one way function Maps a domain into a range with unique inverse The calculation of the function is easy The calculation of the inverse is infeasible Easy The problem can be solved in polynomial time Infeasible The effort to solve it grows faster than polynomial time For example: 2n It requires infeasible for all inputs, not just worst case
 Trapdoor One-way Function Trapdoor one way function Maps a domain into a range with unique inverse Y=fk(X) The calculation of the function is easy The calculation of the inverse is infeasible if the key is not known The calculation of the inverse is easy if the key is known
Trapdoor One-way Function Trapdoor one way function Maps a domain into a range with unique inverse Y=fk(X) The calculation of the function is easy The calculation of the inverse is infeasible if the key is not known The calculation of the inverse is easy if the key is known
 Possible Attacks Brute force Use large keys Trade-off: speed (not linearly depend on key size) Confined to small data encryption: signature, key management Compute the private key from public key Not proven that is not feasible for most protocols! Probable message attack Encrypt all possible messages using encryption key Compare with the ciphertext to find the matched one! If data is small, feasible, regardless of key size of PKC
Possible Attacks Brute force Use large keys Trade-off: speed (not linearly depend on key size) Confined to small data encryption: signature, key management Compute the private key from public key Not proven that is not feasible for most protocols! Probable message attack Encrypt all possible messages using encryption key Compare with the ciphertext to find the matched one! If data is small, feasible, regardless of key size of PKC
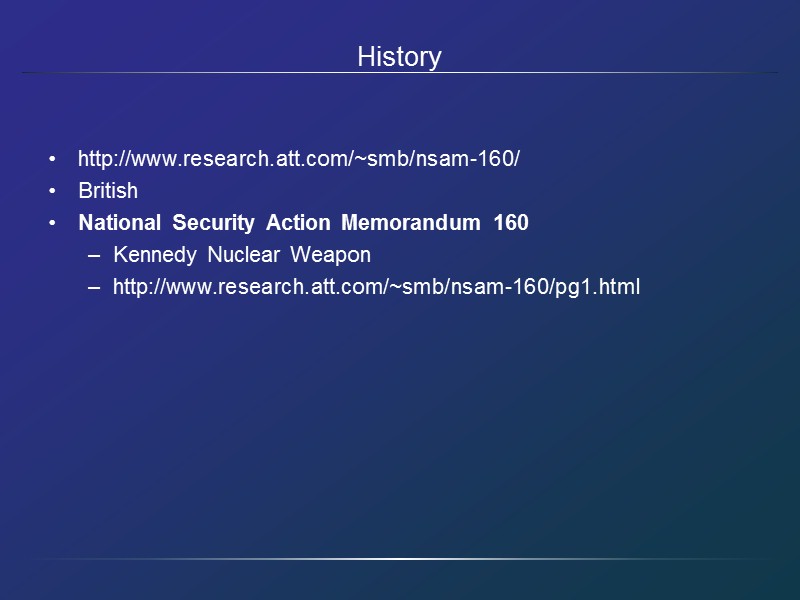
 History http://www.research.att.com/~smb/nsam-160/ British National Security Action Memorandum 160 Kennedy Nuclear Weapon http://www.research.att.com/~smb/nsam-160/pg1.html
History http://www.research.att.com/~smb/nsam-160/ British National Security Action Memorandum 160 Kennedy Nuclear Weapon http://www.research.att.com/~smb/nsam-160/pg1.html
 RSA Algorithm R. Rivest, A. Shamir, L. Adleman (1977) James Ellis came up with the idea in 1970, and proved that it was theoretically possible. In 1973, Clifford Cocks a British mathematician invented a variant on RSA; a few months later, Malcom Williamson invented a Diffie-Hellman analog Only revealed till 1997 Patent expired on September 20, 2000. Block cipher using integers 0~n-1 Thus block size k is less than log2n Algorithm: Encryption: C=Me mod n Decryption: M=Cd mod n Both sender and the receiver know n
RSA Algorithm R. Rivest, A. Shamir, L. Adleman (1977) James Ellis came up with the idea in 1970, and proved that it was theoretically possible. In 1973, Clifford Cocks a British mathematician invented a variant on RSA; a few months later, Malcom Williamson invented a Diffie-Hellman analog Only revealed till 1997 Patent expired on September 20, 2000. Block cipher using integers 0~n-1 Thus block size k is less than log2n Algorithm: Encryption: C=Me mod n Decryption: M=Cd mod n Both sender and the receiver know n
 RSA (public key encryption) Alice wants Bob to send her a message. She: selects two (large) primes p, q, TOP SECRET, computes n = pq and (n) = (p-1)(q-1), (n) also TOP SECRET, selects an integer e, 1 < e < (n), such that gcd(e, (n)) = 1, computes d, such that de 1 (mod (n)), d also TOP SECRET, gives public key (e, n), keeps private key (d, n).
RSA (public key encryption) Alice wants Bob to send her a message. She: selects two (large) primes p, q, TOP SECRET, computes n = pq and (n) = (p-1)(q-1), (n) also TOP SECRET, selects an integer e, 1 < e < (n), such that gcd(e, (n)) = 1, computes d, such that de 1 (mod (n)), d also TOP SECRET, gives public key (e, n), keeps private key (d, n).
 Requirements Possible to find e and d such that M=Mde mod n for all message M Easy to conduct encryption and decryption Infeasible to compute d Given n and e
Requirements Possible to find e and d such that M=Mde mod n for all message M Easy to conduct encryption and decryption Infeasible to compute d Given n and e
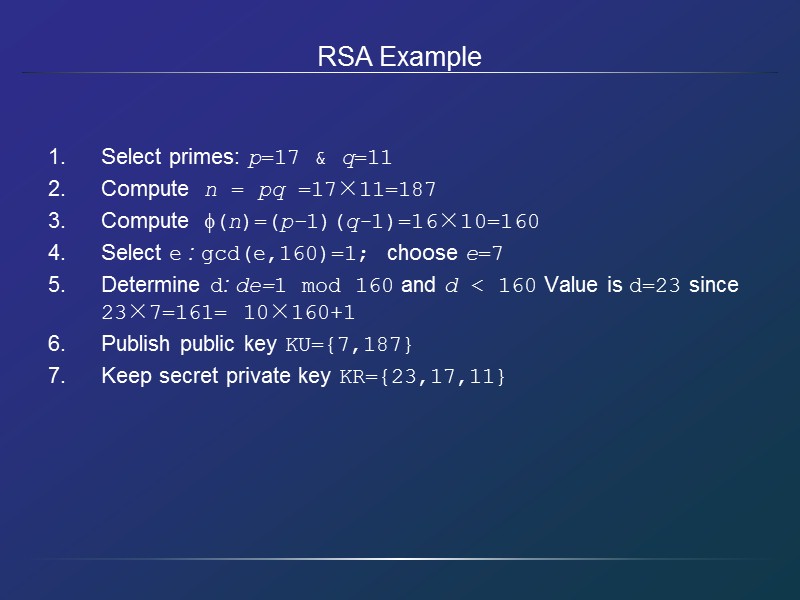
 RSA Example Select primes: p=17 & q=11 Compute n = pq =17×11=187 Compute (n)=(p–1)(q-1)=16×10=160 Select e : gcd(e,160)=1; choose e=7 Determine d: de=1 mod 160 and d < 160 Value is d=23 since 23×7=161= 10×160+1 Publish public key KU={7,187} Keep secret private key KR={23,17,11}
RSA Example Select primes: p=17 & q=11 Compute n = pq =17×11=187 Compute (n)=(p–1)(q-1)=16×10=160 Select e : gcd(e,160)=1; choose e=7 Determine d: de=1 mod 160 and d < 160 Value is d=23 since 23×7=161= 10×160+1 Publish public key KU={7,187} Keep secret private key KR={23,17,11}
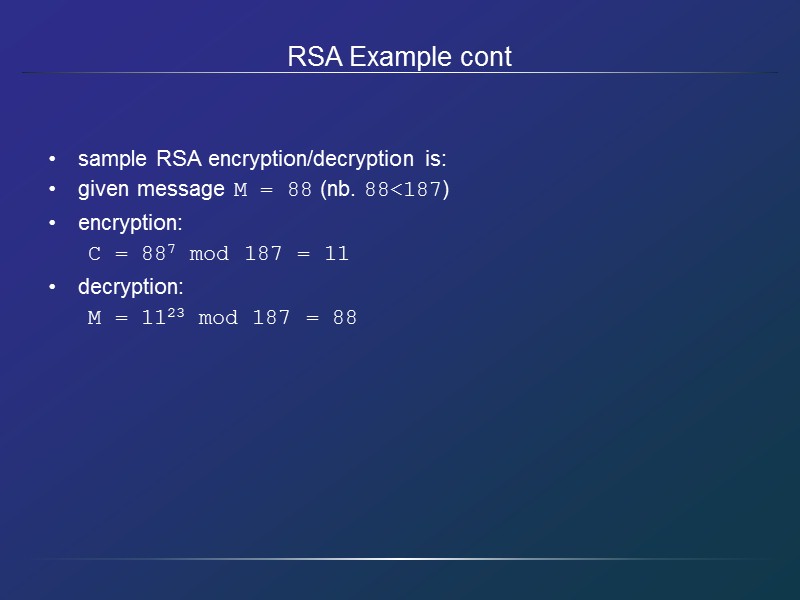
 RSA Example cont sample RSA encryption/decryption is: given message M = 88 (nb. 88<187) encryption: C = 887 mod 187 = 11 decryption: M = 1123 mod 187 = 88
RSA Example cont sample RSA encryption/decryption is: given message M = 88 (nb. 88<187) encryption: C = 887 mod 187 = 11 decryption: M = 1123 mod 187 = 88
 Q & A Questions ?
Q & A Questions ?
 End
End

