04191e757edd758d8f370b3546c95d5b.ppt
- Количество слайдов: 21
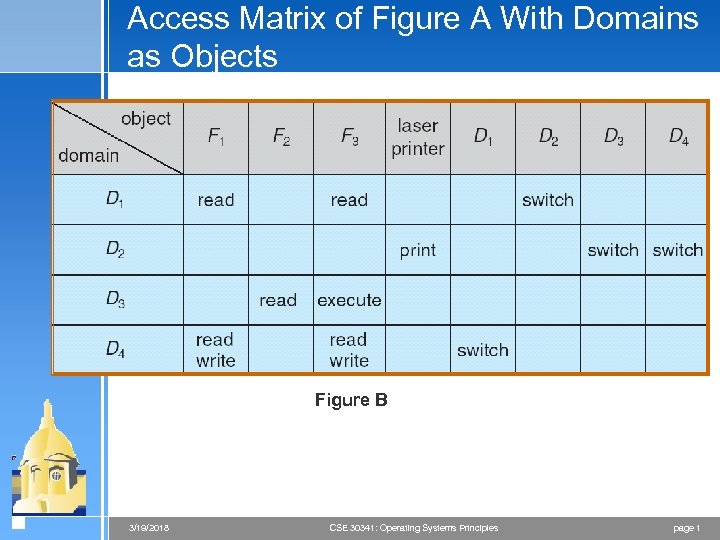 Access Matrix of Figure A With Domains as Objects Figure B 3/19/2018 CSE 30341: Operating Systems Principles page 1
Access Matrix of Figure A With Domains as Objects Figure B 3/19/2018 CSE 30341: Operating Systems Principles page 1
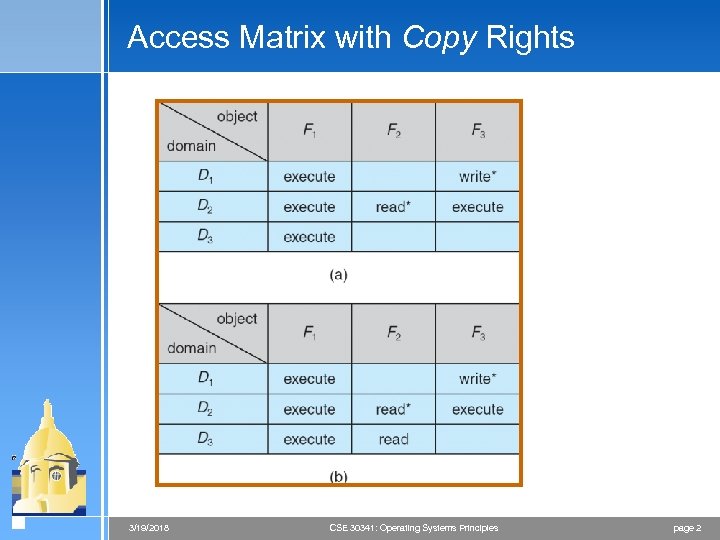 Access Matrix with Copy Rights 3/19/2018 CSE 30341: Operating Systems Principles page 2
Access Matrix with Copy Rights 3/19/2018 CSE 30341: Operating Systems Principles page 2
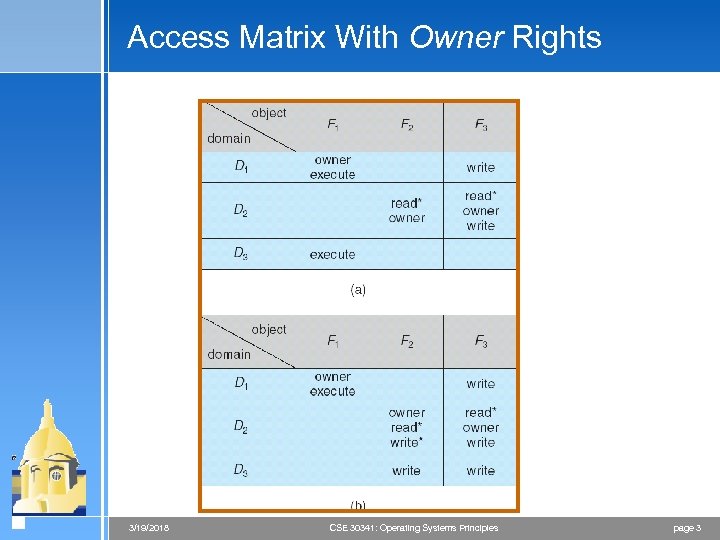 Access Matrix With Owner Rights 3/19/2018 CSE 30341: Operating Systems Principles page 3
Access Matrix With Owner Rights 3/19/2018 CSE 30341: Operating Systems Principles page 3
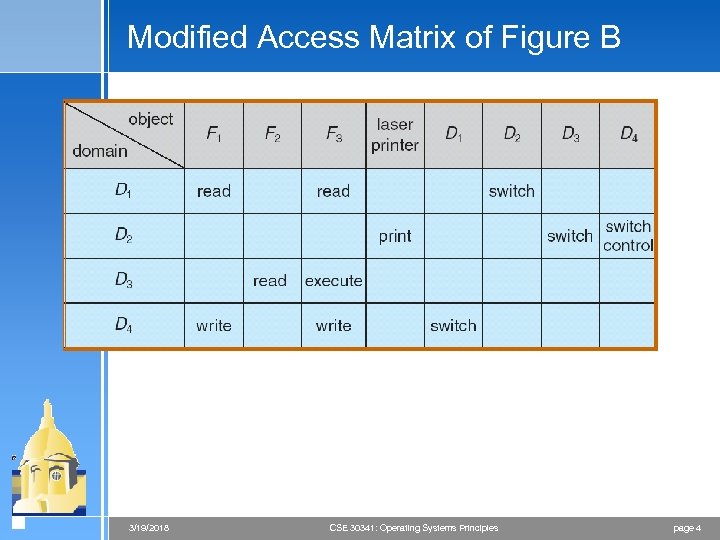 Modified Access Matrix of Figure B 3/19/2018 CSE 30341: Operating Systems Principles page 4
Modified Access Matrix of Figure B 3/19/2018 CSE 30341: Operating Systems Principles page 4
 Revocation of Access Rights 4 Access List – Delete access rights from access list. < Simple < Immediate 4 Capability List – Scheme required to locate capability in the system before capability can be revoked. < Reacquisition < Back-pointers < Indirection < Keys 3/19/2018 CSE 30341: Operating Systems Principles page 5
Revocation of Access Rights 4 Access List – Delete access rights from access list. < Simple < Immediate 4 Capability List – Scheme required to locate capability in the system before capability can be revoked. < Reacquisition < Back-pointers < Indirection < Keys 3/19/2018 CSE 30341: Operating Systems Principles page 5
 Language-Based Protection 4 Specification of protection in a programming language allows the high-level description of policies for the allocation and use of resources. 4 Language implementation can provide software for protection enforcement when automatic hardwaresupported checking is unavailable. 4 Interpret protection specifications to generate calls on whatever protection system is provided by the hardware and the operating system. 3/19/2018 CSE 30341: Operating Systems Principles page 6
Language-Based Protection 4 Specification of protection in a programming language allows the high-level description of policies for the allocation and use of resources. 4 Language implementation can provide software for protection enforcement when automatic hardwaresupported checking is unavailable. 4 Interpret protection specifications to generate calls on whatever protection system is provided by the hardware and the operating system. 3/19/2018 CSE 30341: Operating Systems Principles page 6
 Protection in Java 2 4 Protection is handled by the Java Virtual Machine (JVM) 4 A class is assigned a protection domain when it is loaded by the JVM. 4 The protection domain indicates what operations the class can (and cannot) perform. 4 If a library method is invoked that performs a privileged operation, the stack is inspected to ensure the operation can be performed by the library. 3/19/2018 CSE 30341: Operating Systems Principles page 7
Protection in Java 2 4 Protection is handled by the Java Virtual Machine (JVM) 4 A class is assigned a protection domain when it is loaded by the JVM. 4 The protection domain indicates what operations the class can (and cannot) perform. 4 If a library method is invoked that performs a privileged operation, the stack is inspected to ensure the operation can be performed by the library. 3/19/2018 CSE 30341: Operating Systems Principles page 7
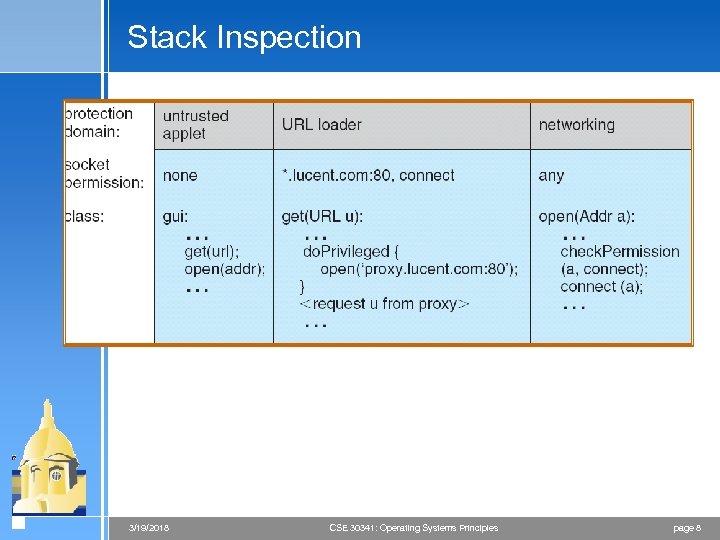 Stack Inspection 3/19/2018 CSE 30341: Operating Systems Principles page 8
Stack Inspection 3/19/2018 CSE 30341: Operating Systems Principles page 8
 Chapter 15: The Security Problem 4 Security must consider external environment of the system, and protect the system resources 4 Intruders (crackers) attempt to breach security 4 Threat is potential security violation 4 Attack is attempt to breach security 4 Attack can be accidental or malicious 4 Easier to protect against accidental than malicious misuse 4 Important to understand the role of OS 4 Trusted computing base: Security depends on understanding components that are assumed to be trusted. OS could be part of TCB 3/19/2018 CSE 30341: Operating Systems Principles page 9
Chapter 15: The Security Problem 4 Security must consider external environment of the system, and protect the system resources 4 Intruders (crackers) attempt to breach security 4 Threat is potential security violation 4 Attack is attempt to breach security 4 Attack can be accidental or malicious 4 Easier to protect against accidental than malicious misuse 4 Important to understand the role of OS 4 Trusted computing base: Security depends on understanding components that are assumed to be trusted. OS could be part of TCB 3/19/2018 CSE 30341: Operating Systems Principles page 9
 Security Violations 4 Categories < Breach of confidentiality - Unauthorized access < Breach of integrity - Unauthorized data modification < Breach of availability - Unavailable data < Theft of service < Denial of service 4 Methods < Masquerading (breach authentication) < Replay attack =Message modification < Man-in-the-middle attack < Session hijacking 3/19/2018 CSE 30341: Operating Systems Principles page 10
Security Violations 4 Categories < Breach of confidentiality - Unauthorized access < Breach of integrity - Unauthorized data modification < Breach of availability - Unavailable data < Theft of service < Denial of service 4 Methods < Masquerading (breach authentication) < Replay attack =Message modification < Man-in-the-middle attack < Session hijacking 3/19/2018 CSE 30341: Operating Systems Principles page 10
 Program Threats 4 Trojan Horse < Code segment that misuses its environment < Exploits mechanisms for allowing programs written by users to be executed by other users < Spyware, pop-up browser windows, covert channels 4 Trap Door < Specific user identifier or password that circumvents normal security procedures < Could be included in a compiler 4 Logic Bomb < Program that initiates a security incident under certain circumstances 4 Stack and Buffer Overflow < Exploits a bug in a program (overflow either the stack or memory buffers) 3/19/2018 CSE 30341: Operating Systems Principles page 11
Program Threats 4 Trojan Horse < Code segment that misuses its environment < Exploits mechanisms for allowing programs written by users to be executed by other users < Spyware, pop-up browser windows, covert channels 4 Trap Door < Specific user identifier or password that circumvents normal security procedures < Could be included in a compiler 4 Logic Bomb < Program that initiates a security incident under certain circumstances 4 Stack and Buffer Overflow < Exploits a bug in a program (overflow either the stack or memory buffers) 3/19/2018 CSE 30341: Operating Systems Principles page 11
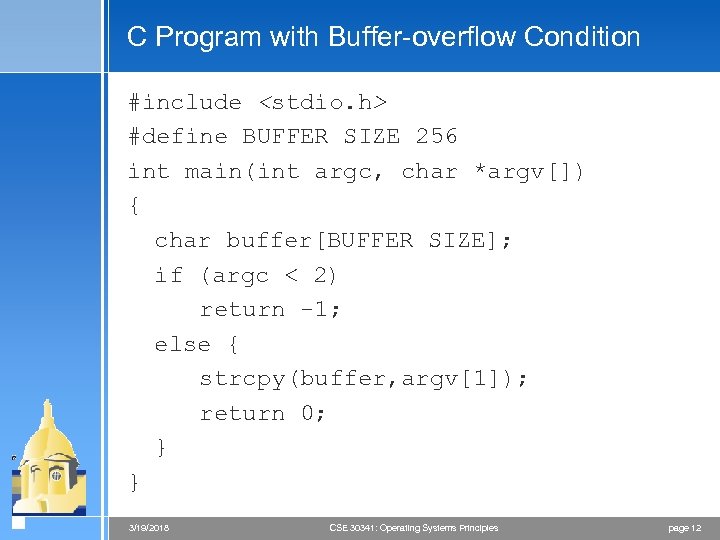 C Program with Buffer-overflow Condition #include
C Program with Buffer-overflow Condition #include
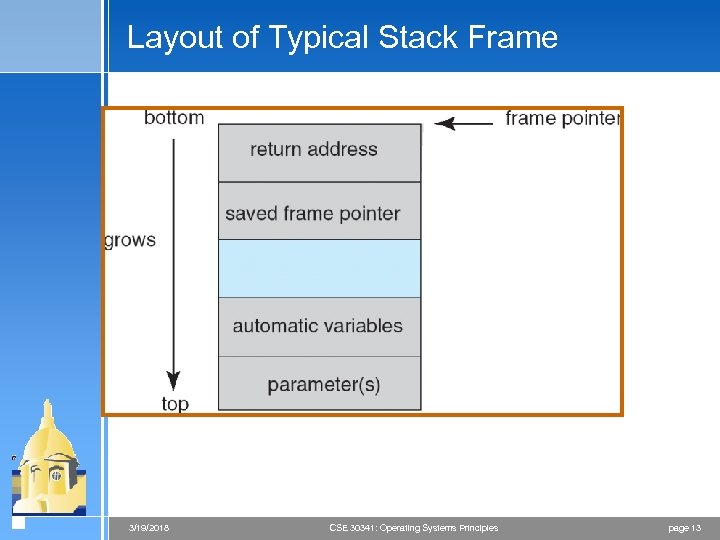 Layout of Typical Stack Frame 3/19/2018 CSE 30341: Operating Systems Principles page 13
Layout of Typical Stack Frame 3/19/2018 CSE 30341: Operating Systems Principles page 13
![Modified Shell Code #include <stdio. h> int main(int argc, char *argv[]) { execvp(“/bin/sh”, ”/bin/sh”, Modified Shell Code #include <stdio. h> int main(int argc, char *argv[]) { execvp(“/bin/sh”, ”/bin/sh”,](https://present5.com/presentation/04191e757edd758d8f370b3546c95d5b/image-14.jpg) Modified Shell Code #include
Modified Shell Code #include
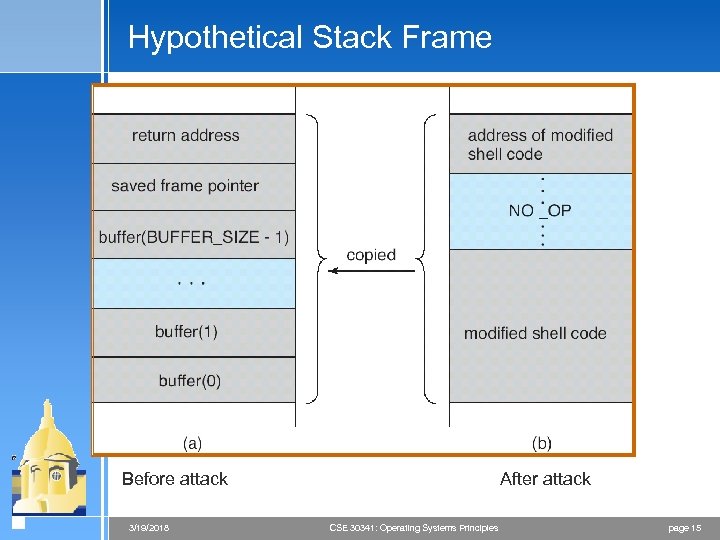 Hypothetical Stack Frame After attack Before attack 3/19/2018 CSE 30341: Operating Systems Principles page 15
Hypothetical Stack Frame After attack Before attack 3/19/2018 CSE 30341: Operating Systems Principles page 15
 Program Threats (Cont. ) 4 Viruses < Code fragment embedded in legitimate program < Very specific to CPU architecture, operating system, applications < Usually borne via email or as a macro =Visual Basic Macro to reformat hard drive Sub Auto. Open() Dim o. FS Set o. FS = Create. Object(’’Scripting. File. System. Object’’) vs = Shell(’’c: command. com /k format c: ’’, vb. Hide) End Sub 3/19/2018 CSE 30341: Operating Systems Principles page 16
Program Threats (Cont. ) 4 Viruses < Code fragment embedded in legitimate program < Very specific to CPU architecture, operating system, applications < Usually borne via email or as a macro =Visual Basic Macro to reformat hard drive Sub Auto. Open() Dim o. FS Set o. FS = Create. Object(’’Scripting. File. System. Object’’) vs = Shell(’’c: command. com /k format c: ’’, vb. Hide) End Sub 3/19/2018 CSE 30341: Operating Systems Principles page 16
 Program Threats (Cont. ) 4 Virus dropper inserts virus onto the system 4 Many categories of viruses, literally many thousands of viruses < File < Boot < Macro < Source code < Polymorphic < Encrypted < Stealth < Tunneling < Multipartite < Armored 3/19/2018 CSE 30341: Operating Systems Principles page 17
Program Threats (Cont. ) 4 Virus dropper inserts virus onto the system 4 Many categories of viruses, literally many thousands of viruses < File < Boot < Macro < Source code < Polymorphic < Encrypted < Stealth < Tunneling < Multipartite < Armored 3/19/2018 CSE 30341: Operating Systems Principles page 17
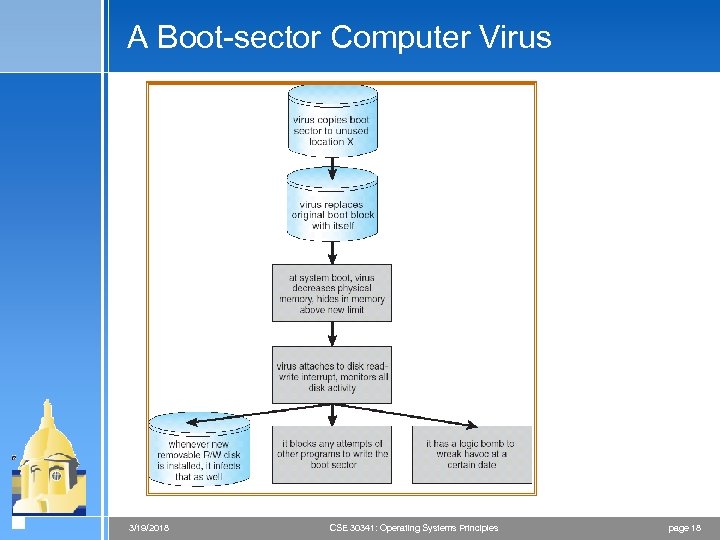 A Boot-sector Computer Virus 3/19/2018 CSE 30341: Operating Systems Principles page 18
A Boot-sector Computer Virus 3/19/2018 CSE 30341: Operating Systems Principles page 18
 System and Network Threats 4 Worms – use spawn mechanism; standalone program 4 Internet worm < Exploited UNIX networking features (remote access) and bugs in finger and sendmail programs < Grappling hook program uploaded main worm program 4 Port scanning < Automated attempt to connect to a range of ports on one or a range of IP addresses 4 Denial of Service < Overload the targeted computer preventing it from doing any useful work < Distributed denial-of-service (DDOS) come from multiple sites at once 3/19/2018 CSE 30341: Operating Systems Principles page 19
System and Network Threats 4 Worms – use spawn mechanism; standalone program 4 Internet worm < Exploited UNIX networking features (remote access) and bugs in finger and sendmail programs < Grappling hook program uploaded main worm program 4 Port scanning < Automated attempt to connect to a range of ports on one or a range of IP addresses 4 Denial of Service < Overload the targeted computer preventing it from doing any useful work < Distributed denial-of-service (DDOS) come from multiple sites at once 3/19/2018 CSE 30341: Operating Systems Principles page 19
 Computer Security Classifications 4 U. S. Department of Defense outlines four divisions of computer security: A, B, C, and D. 4 D – Minimal security. 4 C – Provides discretionary protection through auditing. Divided into C 1 and C 2. C 1 identifies cooperating users with the same level of protection. C 2 allows user-level access control. 4 B – All the properties of C, however each object may have unique sensitivity labels. Divided into B 1, B 2, and B 3. 4 A – Uses formal design and verification techniques to ensure security. 3/19/2018 CSE 30341: Operating Systems Principles page 20
Computer Security Classifications 4 U. S. Department of Defense outlines four divisions of computer security: A, B, C, and D. 4 D – Minimal security. 4 C – Provides discretionary protection through auditing. Divided into C 1 and C 2. C 1 identifies cooperating users with the same level of protection. C 2 allows user-level access control. 4 B – All the properties of C, however each object may have unique sensitivity labels. Divided into B 1, B 2, and B 3. 4 A – Uses formal design and verification techniques to ensure security. 3/19/2018 CSE 30341: Operating Systems Principles page 20
 Example: Windows XP 4 Security is based on user accounts < Each user has unique security ID < Login to ID creates security access token =Includes security ID for user, for user’s groups, and special privileges =Every process gets copy of token =System checks token to determine if access allowed or denied 4 Uses a subject model to ensure access security. A subject tracks and manages permissions for each program that a user runs 4 Each object in Windows XP has a security attribute defined by a security descriptor < For example, a file has a security descriptor that indicates the access permissions for all users 3/19/2018 CSE 30341: Operating Systems Principles page 21
Example: Windows XP 4 Security is based on user accounts < Each user has unique security ID < Login to ID creates security access token =Includes security ID for user, for user’s groups, and special privileges =Every process gets copy of token =System checks token to determine if access allowed or denied 4 Uses a subject model to ensure access security. A subject tracks and manages permissions for each program that a user runs 4 Each object in Windows XP has a security attribute defined by a security descriptor < For example, a file has a security descriptor that indicates the access permissions for all users 3/19/2018 CSE 30341: Operating Systems Principles page 21
